Sporadic scans for "server-info.action", possibly looking for Confluence Server and Data Center Vulnerability CVE-2023-22515
I noticed many scans for "/server-info.action" showing up in our "First Seen URLs" report. This URL didn't ring a bell at first but may be associated with CVE-2023-22515, a recent vulnerability in Confluence Server and Data Center.
Atlassian published an advisory describing this vulnerability on October 4th [1]. The vulnerability is a broken access control vulnerability. Initially exploited against a small number of sites, exploit code is now widely available. The trivial exploit will allow an unauthenticated user to create an admin account. For example, a request to exploit this issue may look like:
POST /setup/setupadministrator.action HTTP/1.1
Host: [target host]
Accept: */*
Connection: keep-alive
X-Atlassian-Token: no-check
Content-Length: 131
Content-Type: application/x-www-form-urlencoded
username=test&fullName=test&email=test&password=test&confirm=test
However, this isn't the only URL that is available for exploitation. Rapid7 first noted, and Atlassian later confirmed, that the vulnerability may also be exploited via the "/server-info.action" endpoint [2].
Today, I noticed that we did see some probes for the "server-info.action" URL in addition to the "setupadministrator.action" URL.
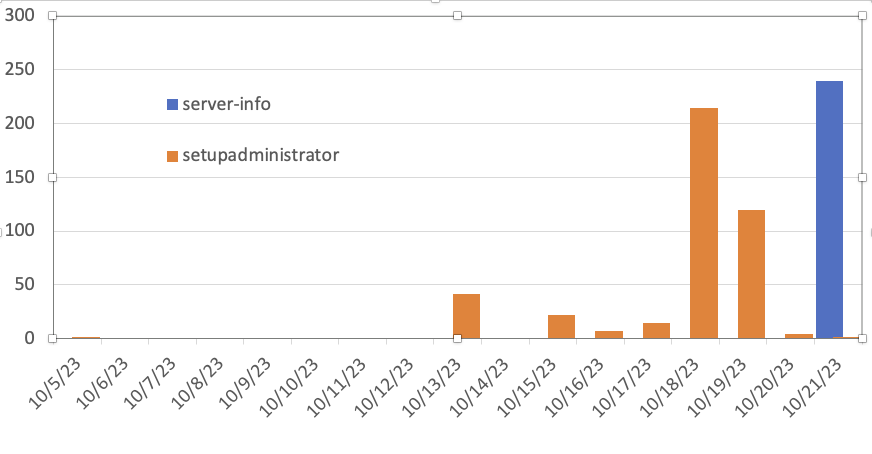
Please ensure that any filter you use covers both URLs and, even better, do not allow access to any Atlassian product from the open internet.
[1] https://confluence.atlassian.com/security/cve-2023-22515-privilege-escalation-vulnerability-in-confluence-data-center-and-server-1295682276.html
[2] https://www.rapid7.com/blog/post/2023/10/04/etr-cve-2023-22515-zero-day-privilege-escalation-in-confluence-server-and-data-center/
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|

Comments