Changes to SMS Delivery and How it Effects MFA and Phishing
Spam and phishing SMS messages (sometimes called "smishing") have been problematic in recent years. These messages often bypass security controls and are more challenging to identify as malicious by users. Moreover, they can be just simply annoying.
This post does apply to US telecom companies. Let me know how this is being dealt with in other countries.
Here is a simple "stupid" one I just received yesterday
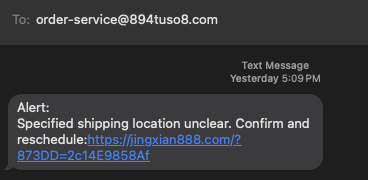
But often, you will now see "smishing" that asks you to reply. For example, an attack I wrote about recently:
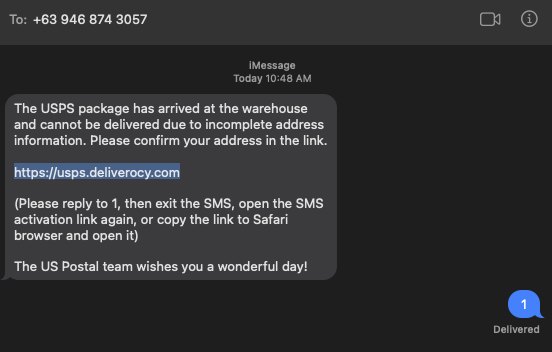
Initially, I figured it might be required to reply to the message to "activate" the phishing page. This would certainly make analysis of these messages more difficult. But the phishing page was accessible even without replying. So there must be another reason for this.
My best guess is that these messages are asking for replies to fool anti-spam techniques put in place by carriers. Over the last few years, carriers in the US have implemented more and more anti-spam measures for SMS. This is partly driven by regulations that initially allowed carriers to filter messages, and now, more and more require them to implement filters. T-Mobile, for example, uses a detailed "code of conduct" to inform customers what T-Mobile considers appropriate behavior.
One distinction in rules like this is using "conversational" messaging compared to informational or promotional messaging. In a conversational exchange, both sides are sending text messages to each other. A reply may be considered part of a "conversation."
In response to these new measures by phone companies, providers of SMS messaging services have also acted to implement related rules for their customers. Twilio, for example, has been blocking outbound SMS messages unless customers provide additional information verifying their identity. This process also passes on some additional costs carriers impose.
However, there is a side effect of this regulation to limit automated SMS messages: 2FA utilizing SMS messaging will be less reliable. You must ensure that the numbers your 2FA messages originate from are appropriately registered. This is necessary if you use a "regular" 10-digit phone number, not a "shortcode." Shortcodes are usually much more expensive and are only used if you send many SMS messages.
It is hard to tell if these measures have reduced Phishing. I believe I see less spam overall, but I still see some, like the message I received yesterday.
One thing you can and should do: Reply to any spam messages with "STOP." The use of this response is tracked and is used to identify non-compliant SMS campaigns automatically. This slightly differs from the "unsubscribe" link in spam emails, which is usually counter-productive. I recently inherited a number that received many automated messages that the prior owner of the number may have subscribed to. After replying with "stop", the number has been quiet.
For example, T-Mobile's code of conduct states:
"Messaging campaigns that yield high opt-out rates may suggest compliance issues with the campaign, content provider, or opt-in list. DCAshould monitor STOP and HELP responses on a campaign basis and should be flagged for monitoring and/or conduct a consent audit shall opt-out rates exceed .5% per messaging campaign blast."
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|

Comments
Steve
Oct 17th 2023
6 months ago
- activating the link, at least in some cases I've noticed that the link doesn't light up to be easily clicked on until you do ...
- so they can tell an active number, assuming there's at lesat a bit of spray and pray.
- probably at least some amount of trying to add them to your known contacts and all on your device, much like email phishing does.
jjminer
Oct 17th 2023
6 months ago