Google Paid Ads for Fake Tesla Websites
In recent media events, Tesla has demoed progressively more sophisticated versions of its Optimus robots. The sales pitch is pretty simple: "Current AI" is fun, but what we really need is not something to create more funny kitten pictures. We need AI to load and empty dishwashers, fold laundry, and mow lawns. But the robot has not been for sale yet, and there is no firm release date.
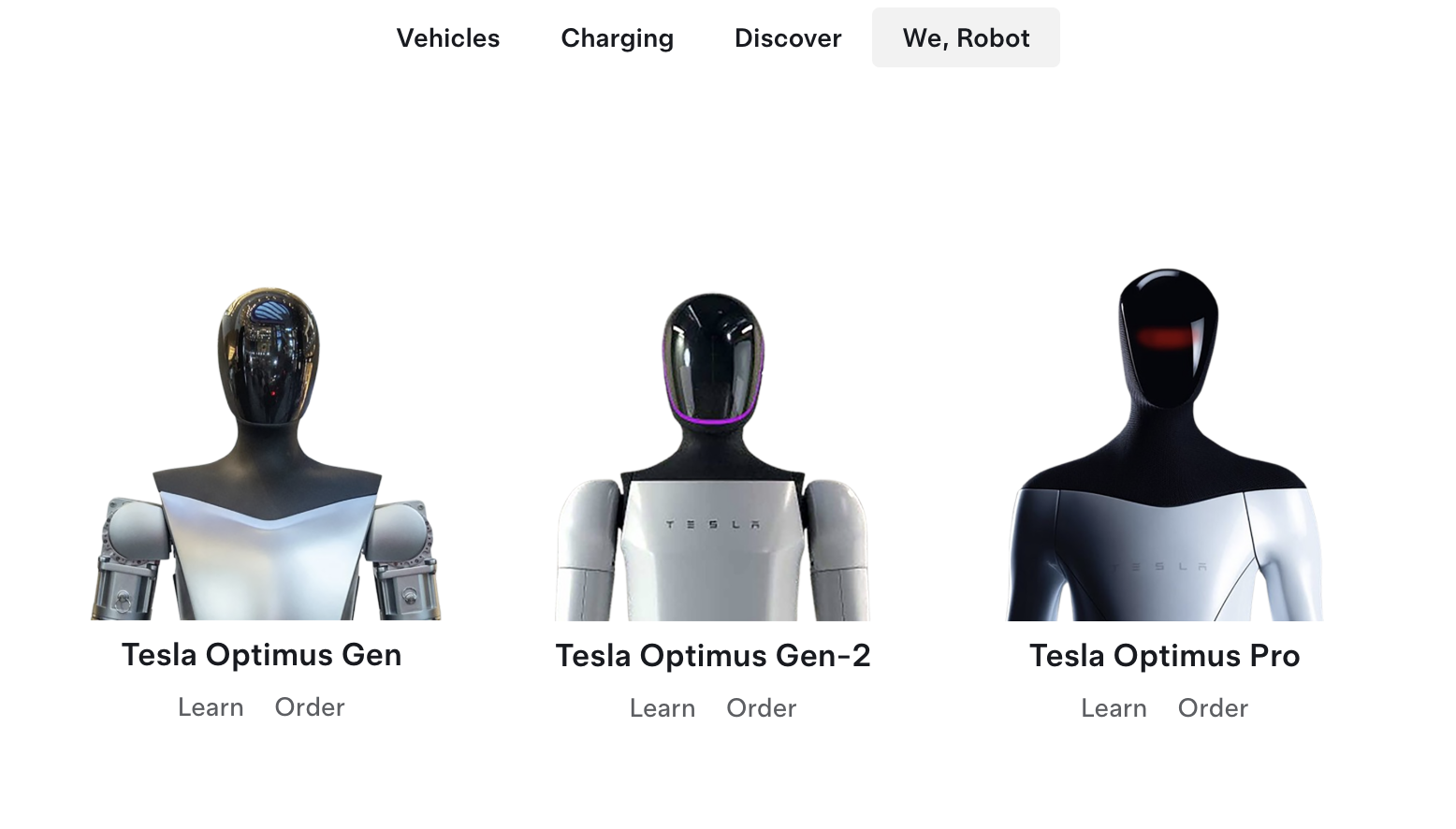
In the past, Tesla has accepted preorders for future products, asking for a deposit, which in some cases was even refundable. But aside from an April Fool's posting announcing such a presale, as far as I can tell, no presale has been offered by Tesla.
However, if you search for "Optimus Tesla preorder" and other similar terms, sites claiming to offer Optimus preorders will be advertised.
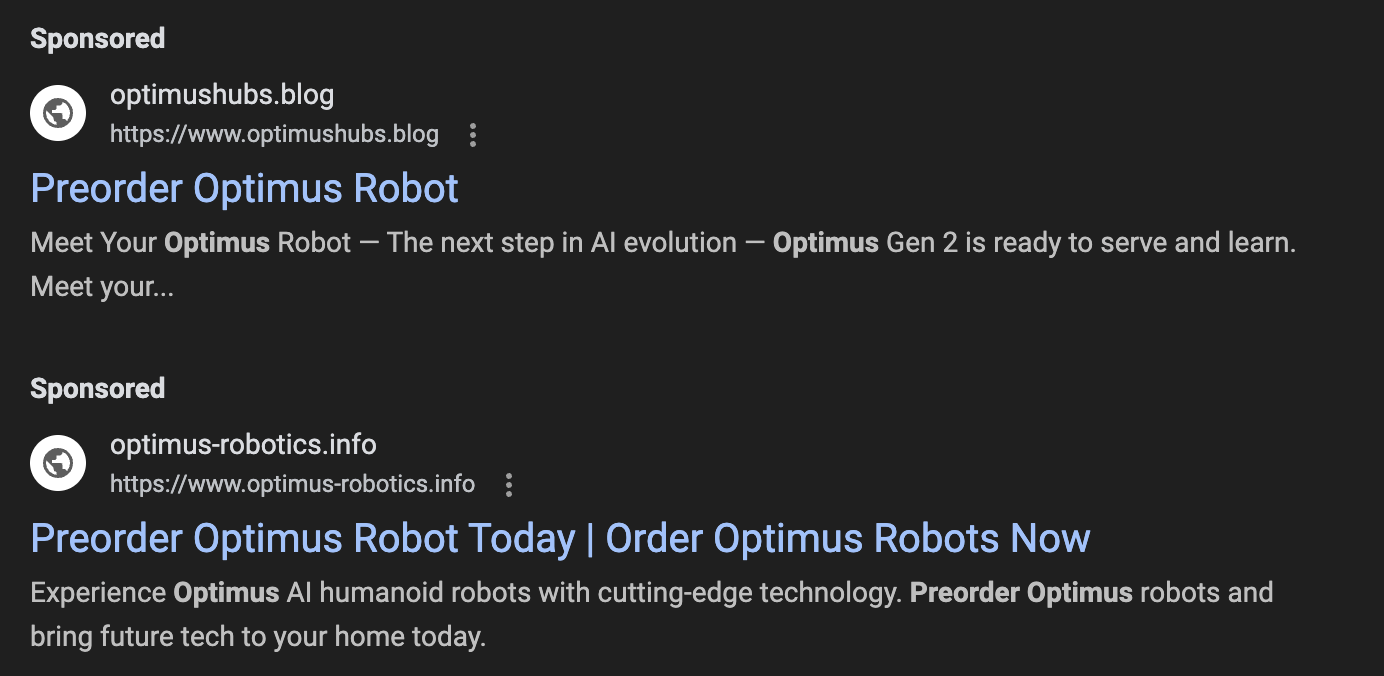
These are sponsored listings. The official Tesla site (without the preorder option) shows below these fake links.
We have often seen sponsored listings like this used to advertise malware. But in this case, I suspect, the goal is simply to steal money from people willing to pay for preorders. The interesting twist is that the theft may remain unnoticed until the customer expects delivery, which may be months or years from now.
So far, I have seen these ads lead to three different websites:
- offers-tesla.com (currently active)
- exclusive-tesla.com (now offline)
- prelaunch-tesla.com (now offline)
Other suspect domains:
- private-tesla.com (unreachable)
- corp-tesla.com (redirects to legitimate tesla.com site)
- www-tesla.com (unreachable)
- hyper-tesla.com (unreachable)
- auth.cp-tesla.com (used for account setup by fake site)
The sites display a complete copy of a slightly older design of the Tesla.com website. As far as I can tell, the design does not include a login page. Standard phishing does not appear to be the goal here. Not having a login page may make it easier to hide that no orders are being placed. Customers will not be able to use the fake site to check their order status.
It asks for a $250 non-refundable deposit, which aligns with what Tesla asked for in prior preorder events.
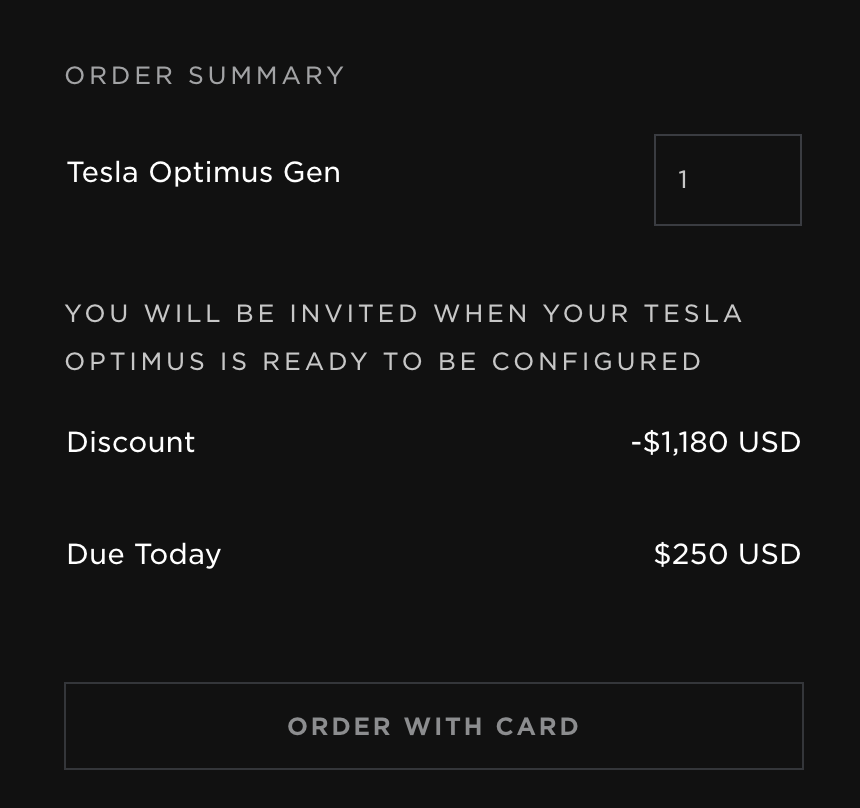
I tried to place an order with a test credit card number, and it was accepted, showing that the credit card was not charged (yet?). Next, I was directed to auth.cp-tesla.com to set up an account. I never received the e-mail confirmation, so I am not sure if my spam filters dropped it or if it is supposed to fail. The original Tesla site uses "auth.tesla.com" for authentication.
Setting up credit card processing for a fake site is likely too complicated, and I assume the site just collects the payment card data to later use the cards on other sites for fraudulent orders or just to resell the payment card data (are there still "Carder" forums? Have not looked at that in a while). So far, the fake sites have only been available for a few days before being shut down. I assume that Tesla monitors these sites and sends takedown requests as they find them.
Preorders are accepted not only for Optimus robots but also for other Tesla products. Interestingly, the data is sent to different sites, not just to the original site. One URL used is https://caribview.info/tesla/. There are a few open directory listings on offers-tesla.com (for example,/api and /js). File dates are from March and May 2025, which is likely around the time the Tesla site was copied. The fake site is hosted behind Cloudflare.
--
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Social Media Links: https://jbu.me


Comments