Uncovering Shenanigans in an IP Address Block via Hurricane Electric's BGP Toolkit (II)
Today’s diary revisits hunting for dodgy domains via Hurricane Electric's BGP Toolkit [1]. This was previously done in an earlier diary [2], and I plan to do this occasionally to share potential or identified threats so that readers can be aware of them.
I selected the IP address block of 209.58.160.0/20 this time, partly also due to a significant number of hits on my DShield sensor from this IP address block. An entry immediately caught my attention, and stood out due to the recent Akamai outage as mentioned by Johannes [3]. With reference to Figure 1, there was a site “akammai.com” lurking amongst the plethora of many other websites that was hosted on the same IP address.
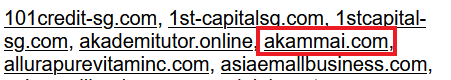
Figure 1: “akammai.com” Hosted on 209.58.163[.]95
A closer inspection on the site showed a “Hello world” post, and did not display any other noticeable features (as shown in Figure 2).
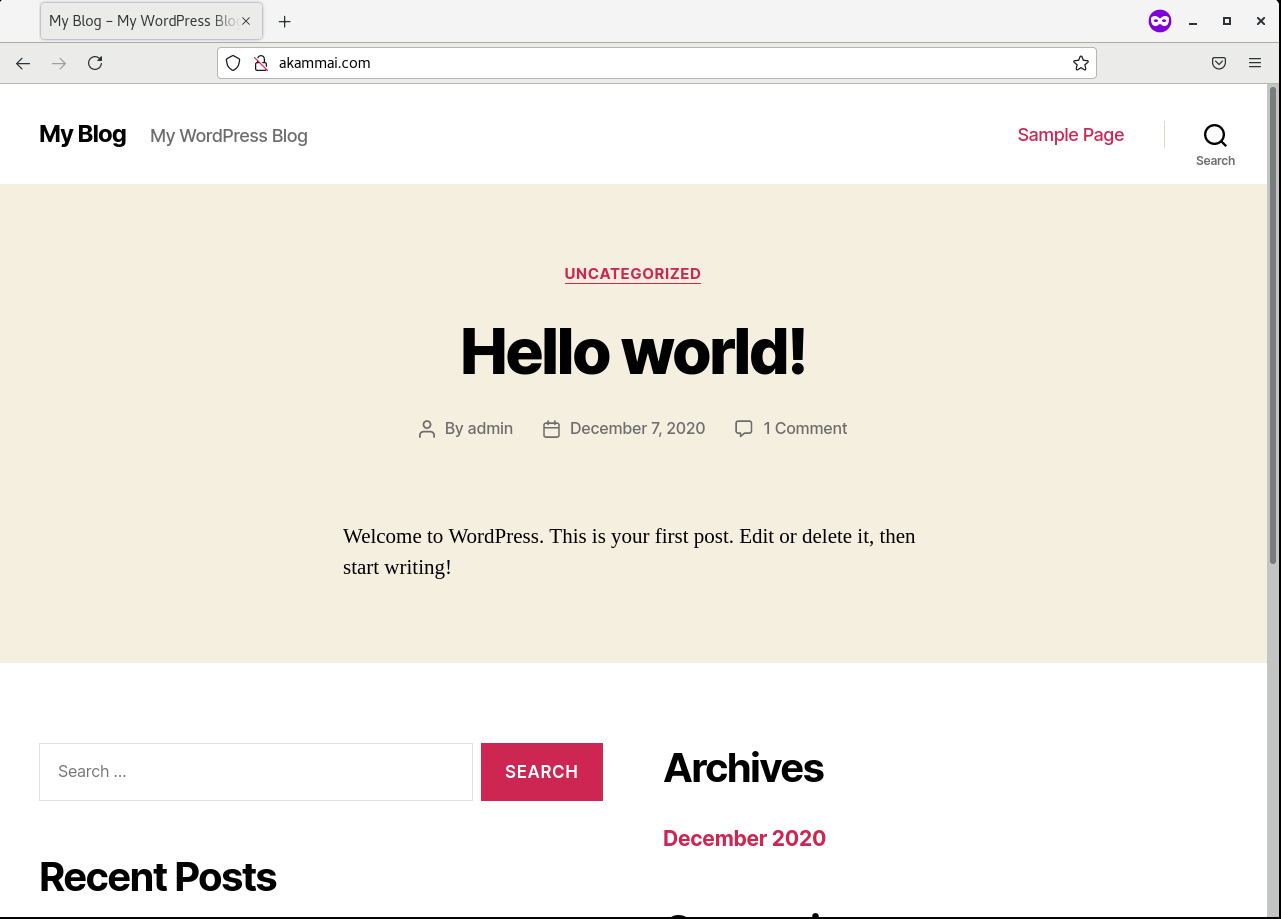
Figure 2: Screenshot of “akammai.com”
As of now, the site appears to be pretty harmless. However, the domain name is quite close to the actual Akamai domain name (akamai.com). Depending on the true owner of the domain name “akammai.com”, the site could very well be repurposed and used by cybercriminals or red teams for their phishing campaigns. This is especially so due to the recent Akamai outage, or perhaps in a future unforeseen outage related to Akamai. It would be worthwhile to be wary of such domain names, particularly more so if they do not have any relation to the original site but yet bear such a close resemblance.
Indicators of Compromise (IOCs):
hxxp://akammai[.]com
209.58.163[.]95
References:
[1] https://bgp.he.net/
[2] https://isc.sans.edu/diary/27456
[3] https://isc.sans.edu/diary/27660
-----------
Yee Ching Tok, ISC Handler
Personal Site
Twitter


Comments