Pro Russian Attackers Scanning for Sharepoint Servers to Exploit CVE-2023-29357
In June, Microsoft released a patch for CVE-2023-29357, a critical privilege escalation vulnerability for Sharepoint. An exploit for this vulnerability was released in late September [1]. Combined with CVE-2023-24955, a remote code execution vulnerability that was patched in May. The first vulnerability bypasses authentication to enable code execution via the second vulnerability.
Earlier today, I noticed the URL for CVE-2023-2023-29357 show up in our "first seen URL" list. This list notes URLs collected by our honeypots that reached certain thresholds for the first time. Our honeypots saw the first exploit attempts on September 30th, but at the time, they did not reach the threshold yet to be considered significant.
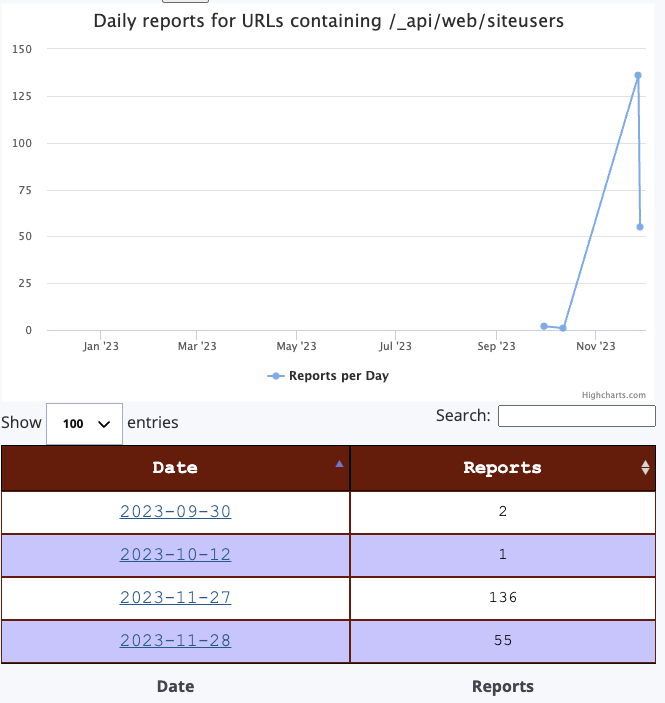
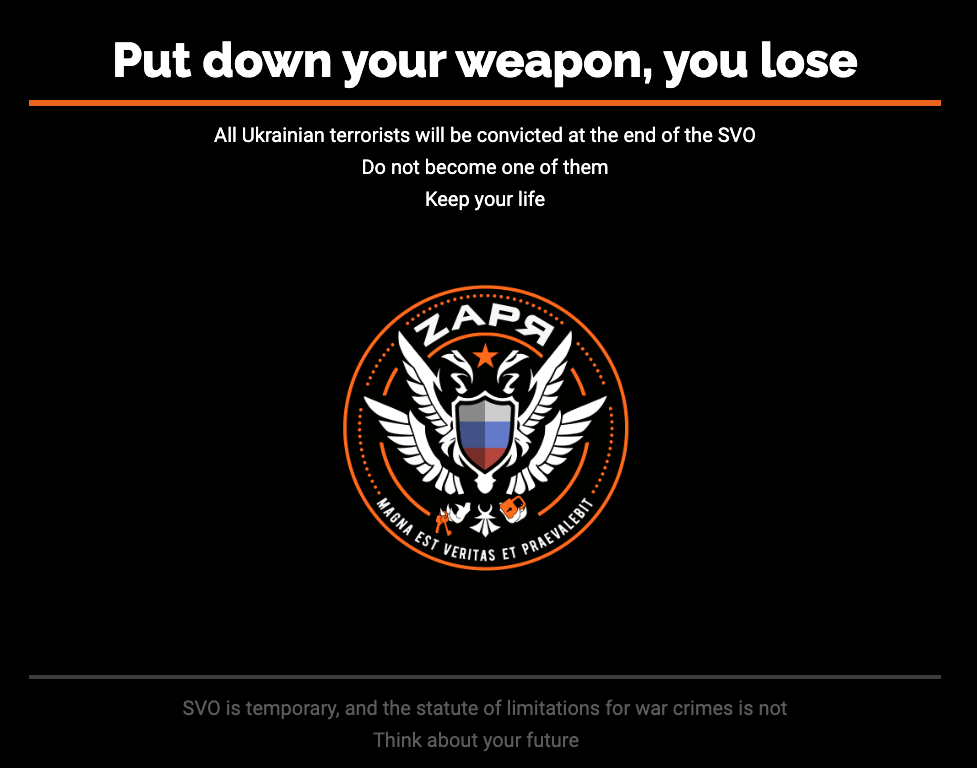
The attacks originate almost exclusively from 212.113.106.100, an IP address that ironically resolved to "rooted-pizzas.aeza.network'. The web server running on this server displays a homepage that indicates that it was compromised and defaced by a pro-Russian group
| Russian Original | English Translation |
 |
 |
The URL being scanned is /_api/web/siteusers. This URL is usually intended to retrieve user information from Sharepoint servers. The exploit will use it to retrieve a list of admin users and then spoof the administrator's identity, taking advantage of the vulnerability.
According to Aeza.net's geolocation feed, the server is located in Vienna and runs Ubuntu according to the server's banner. It is unlikely that the same Sharepoint vulnerability was used to exploit the server.
[1] https://github.com/Chocapikk/CVE-2023-29357
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
| Application Security: Securing Web Apps, APIs, and Microservices | Las Vegas | Sep 22nd - Sep 27th 2025 |


Comments