Offensive Countermeasures against stolen passswords
A while ago I shared a diary on offensive counter measures against stolen Windows hashes. You can review that diary here.
https://isc.sans.edu/forums/diary/Detecting+Mimikatz+Use+On+Your+Network/19311/
This one is for Linux! This fun tweet by @nixcraft showed how an attacker could us Bash terminal commands to move the cursor and disguise the contents of a file.
https://twitter.com/nixcraft/status/644731204533534720
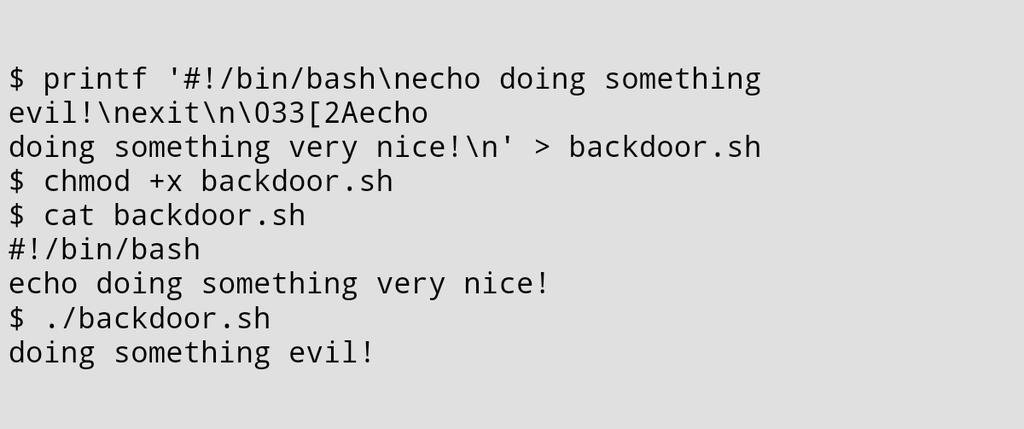
By moving the cursor around and printing over existing lines in the script the attackers hide the evil nature of the file. As @nixcrafts tweet "Hacking like its 1999" implies this has been around for a while, but it is still pretty fun. After reading this tweet it occurred to me that I could use this same technique to protect my /etc/shadow file when an attacker steals a copy of it and/or displays it with cat, tail or some other command that processes terminal cursor movements. Let's give it a try! Here is what at attacker sees when they steal your hashes from your Linux machine...
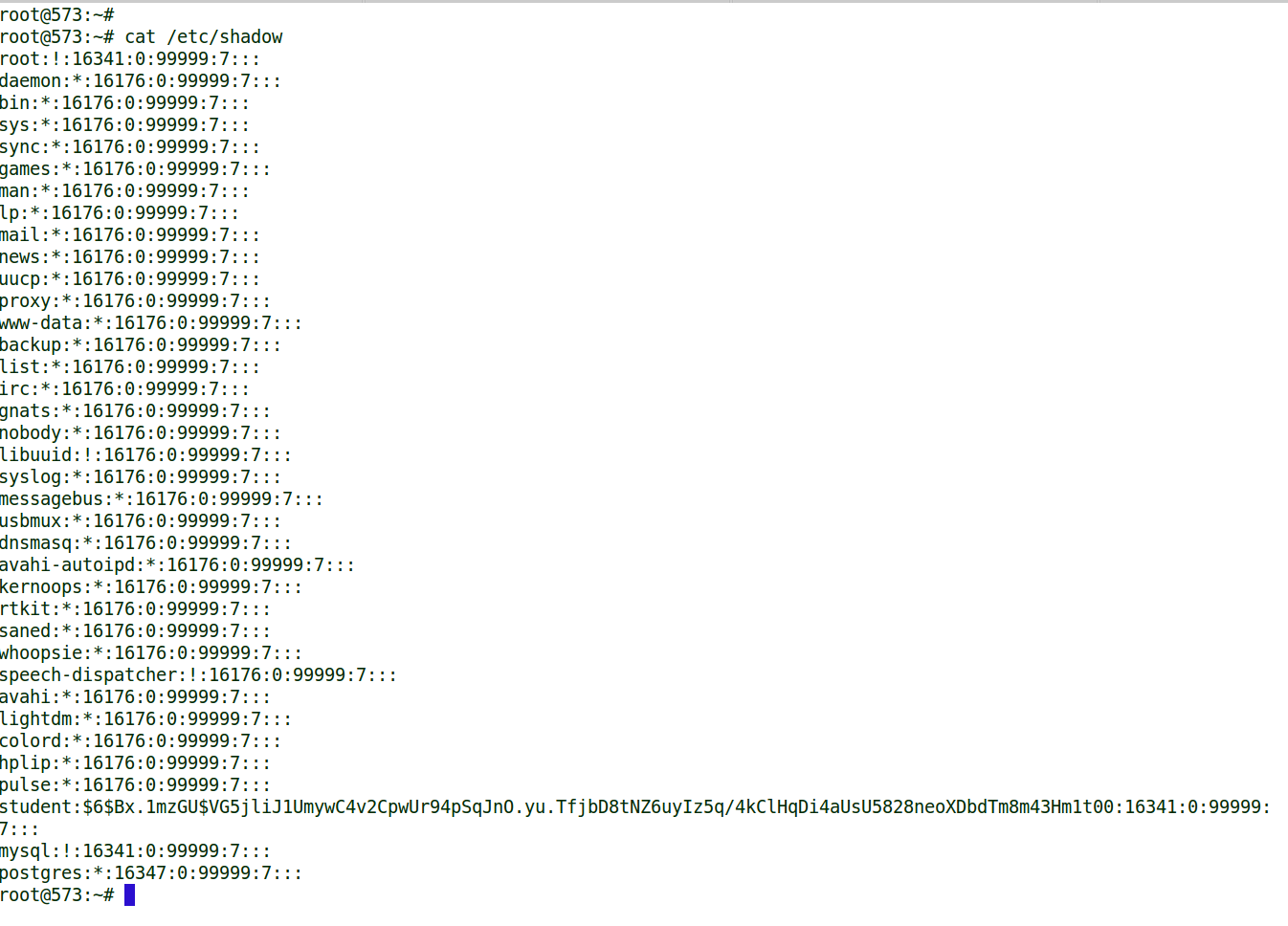
OH NO!! There is the student accounts hash displayed in all its glory for the attacker to steal and crack. Enter Liam Neeson. Liam Neeson is a small python program that inserts terminal cursor movements to disguise your /etc/shadow file. Here is the help options and an example of running the script to protect my etc shadow file.
.png)
So what does an attacker see now that the file is protected by Liam_neeson.py??? This..

Now your password hashes are safe. Notice that the student hash is no longer visible. NOTE TO ALL ATTACKERS: If you do hack a server protected by Liam Neeson the proper response is to erase the shadow file and replace it with a file that simply says "Good Luck".
You can download a copy of Liam_neeson.py from here: https://raw.githubusercontent.com/MarkBaggett/MarkBaggett/master/liam_neeson.py
Would I use this in production? Probably not. Your logins will still work and your system will function properly until you add another user. I don't know what will happen when you try to add a user to the end of that file. It is unlikely that attackers will leave you alone based on this defense. As an attacker it would only spark my interest. BUT the concept is a good one if you are a little more subtle. Look at servers sitting in your DMZ where the users will not change. Then make small subtle changes to the hashes that appear when attackers view the files. Here is an example where I just overwrote a part of the hash with the word "Changed hash".
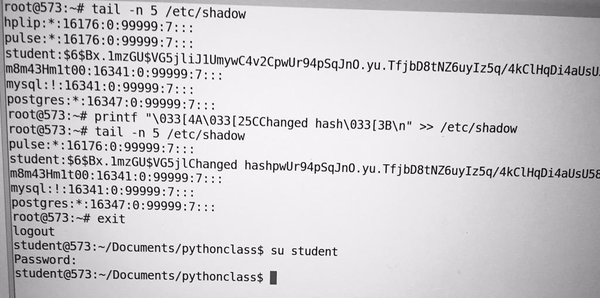
Again this is done with the intention of being obvious so that you can see what it is doing. But, if I just overwrote a portion of the password hash with characters that appear to be part of the password hash then an attacker is likely to steal and try to crack those modified password hashes.
Of course there are obvious limitations. This will only deceive attackers who display the file with a command that interprets the cursor movements. But... defense indepth... every little bit helps.
Check out my Python class and learn how to create tools like this. SEC573 Python for Penetration testers covers topics every defender can use to protect their network. Non-programmers are welcome! We will start with the essentials and teach you to code.
Come check out Python in Orlando Florida, Berlin Germany or Canberra Australia!! For dates and details click here.
https://www.sans.org/course/python-for-pen-testers
Follow me on Twitter at @MarkBaggett (I tweeted about this one a few months ago)


Comments
By default I have LESS="-MM -i -R", but even after unsetting that and running less with its full path I still see the full file contents.
Anonymous
Dec 7th 2015
9 years ago
Anonymous
Dec 7th 2015
9 years ago
Anonymous
Dec 10th 2015
9 years ago