A Survey of Scans for GeoServer Vulnerabilities
A little bit over a year ago, I wrote about scans for GeoServer [1][2]. GeoServer is a platform to process geographic data [3]. It makes it easy to share geospatial data in various common standard formats. Recently, new vulnerabilities were discovered in GeoServer, prompting me to look again at what our honeypots pick up [4].
Let's first look at the "big picture": How many scans did we see? The total number of requests for URLs starting with "/geoserver" was 211,143 since the beginning of the year.
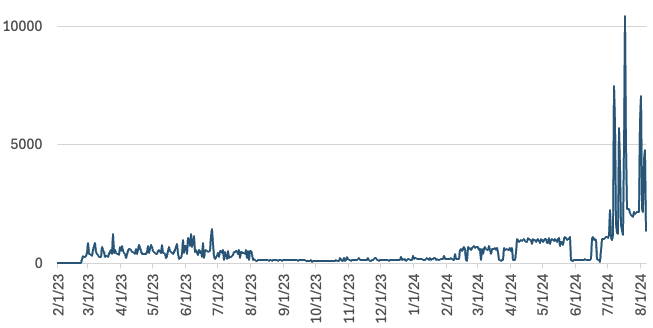
Interest in GeoServer started in 2023. It ceased after August but then came back early this year. After the latest SQL exploit was discovered (July 5th), scans for GeoServer surged.
When I wrote about the GeoServer scans last year, a reader noted that Shadowserver had just started scanning for GeoServer. Indeed, most of the time, all GeoServer scans on particular days can be attributed to researchers. In addition to Shadowserver, Internet Census (associated with BitSight) is scanning for GeoServer instances. Personally, I think this is a good thing. Shadowserver will notify ISPs who host insecure instances, and they will find them before the bad guys.
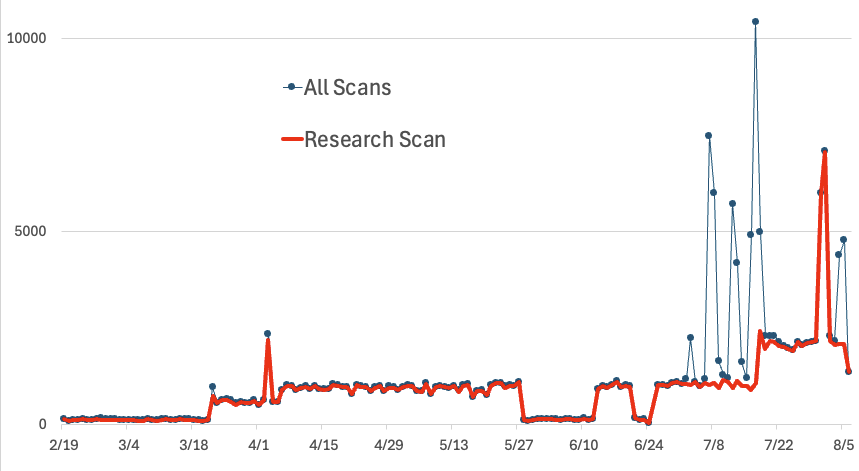
If you are interested, you can retrieve a list of research IPs from our API [5]
Once we remove the scans we identified as "research," these are the top countries from which scans originate:
| Country | Count |
|---|---|
| China | 26,844 |
| South Korea | 2,890 |
| USA | 2,549 |
| Germany | 1,685 |
| Sweden | 1,593 |
| Russia | 1,516 |
| Canada | 1,417 |
| Brazil | 1,137 |
| Hong Kong | 984 |
| Indonesia | 729 |
The most common URLs scanned:
| URL | Count |
|---|---|
| /geoserver/web/ | 37654 |
| /geoserver/web/wicket/bookmarkable/org.geoserver.web.AboutGeoServerPage?lang=en | 4811 |
| /geoserver/wms | 1651 |
| /geoserver | 1432 |
| /geoserver/web/wicket/bookmarkable/org.geoserver.web.AboutGeoServerPage | 333 |
| /geoserver/ | 37 |
| /geoserver/bad397/ | 37 |
| /geoserver/TestWfsPost | 26 |
| /geoserver/web/wicket/bookmarkable/org.geoserver.web.demo.MapPreviewPage | 25 |
| /geoserver/ows | 17 |
"/geoserver/web" is the default "Home Page" of GeoServer. "/geoserver/wms" URLs is what we have seen in the past. Current exploits for CVE-2024-36401 use "/geoserver/wfs". These URLs didn't make the top 10.
[1] https://isc.sans.edu/diary/Geoserver+Attack+Details+More+Cryptominers+against+Unconfigured+WebApps/29936
[2] https://isc.sans.edu/diary/Ongoing+scans+for+Geoserver/29926
[3] https://geoserver.org/
[4] https://medium.com/@knownsec404team/geoserver-sql-injection-vulnerability-analysis-cve-2023-25157-413c1f9818c3
[5] https://isc.sans.edu/api
[6] https://github.com/bigb0x/CVE-2024-36401/blob/main/cve-2024-36401.py
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
| Application Security: Securing Web Apps, APIs, and Microservices | Las Vegas | Sep 22nd - Sep 27th 2025 |


Comments