Deceptive Advertisements: What they do and where they come from
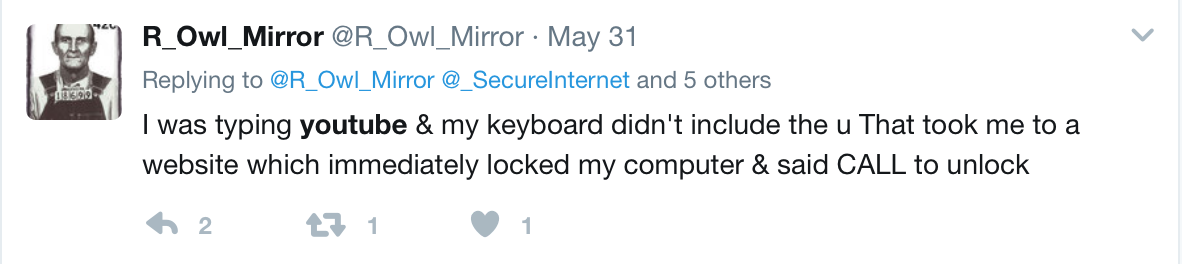
About a week ago, a reader asked for help with a nasty typo squatting incident:
The site, “yotube.com”, at the time redirected to fake tech support sites. These sites typically pop up a message alerting the user of a made-up problem and offer a phone number for tech support.
Investigating the site, I found ads, all of which can be characterized as deceptive. In addition to offering tech support, some of the ads offered video players for download or even suggested that the user has to log in to the site, offering a made up login form. If a user clicks on these ads, the user is sent to a number of different redirects. For example:
For example: (URL parameters removed to make this more readable)
hxxp://inclk.com/adServe/feedclick (URL the ad linked to)
hxxp://p185689.inclk.com/adServe/adClick
hxxp://wkee.reddhon.com/d7477cb3-70f0-4861-a578-a5b6ef73a167
hxxp://www.rainbow-networks.com/RBN3seB
hxxp://critical-system-failure8466.97pn76810224.error-notification-3.club/ (fake tech support page)
hxxp://inclk.com/adServe/banners
hxxp://inclk.com/adServe/banners/findBanner
hxxp://service.skybrock.com/serving/
hxxp://cdn.glisteningapples.pro/lp/
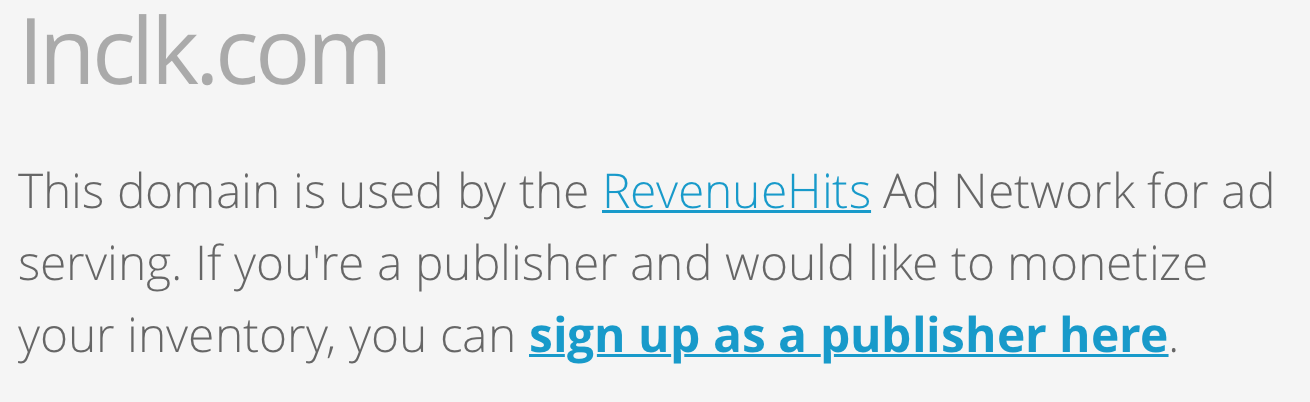
At the time, the ads were hosted at “inclk.com.” Inclk.com is a URL used by RevenueHits, an ad network.
Knowing where these ads come from, I set up an account with RevenueHits and added ads to a test page. So far, I have only gotten deceptive ads like the following:
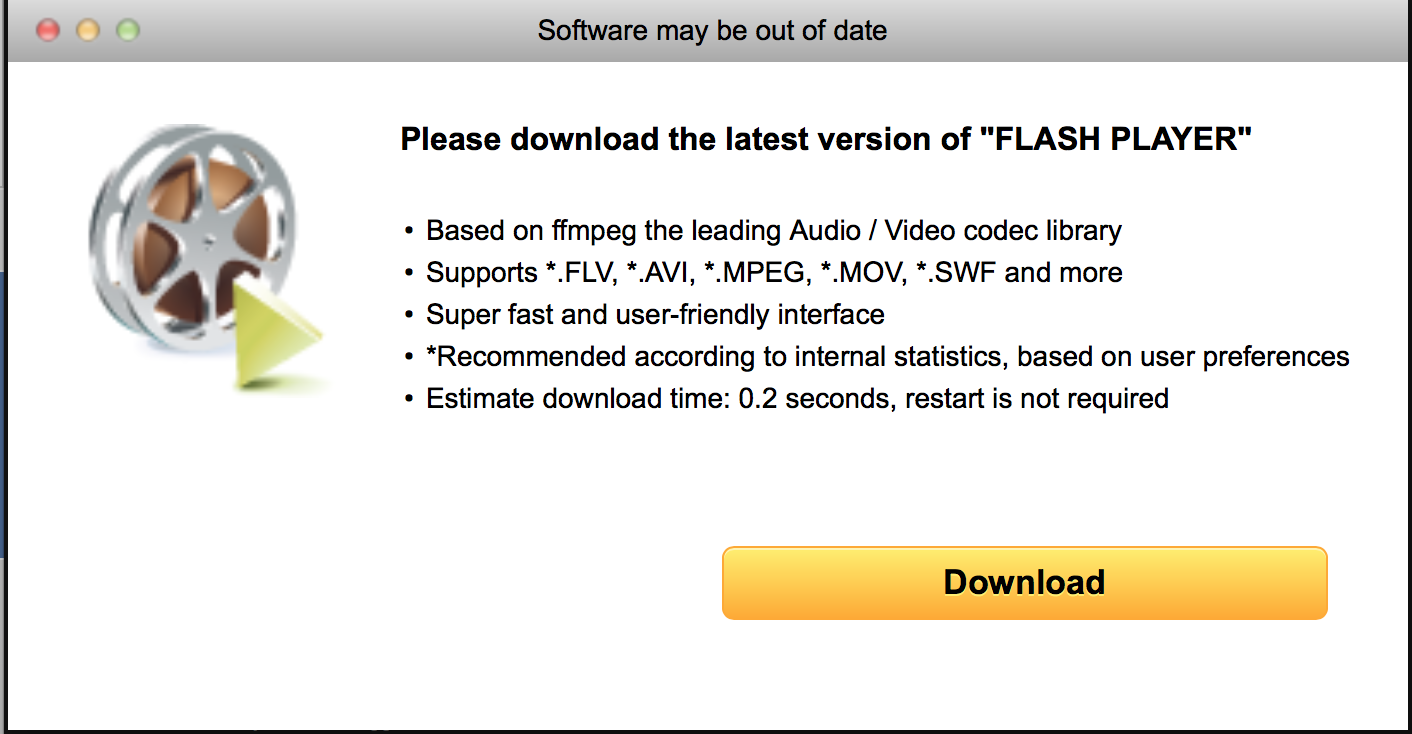
The ads usually claim that a video player is used to view the page, or they suggest that software like a Flash player is out of date and needs to be updated. In one case, it even suggested that I need to log in to view the site and redirected me to a login page, which could be considered phishing.
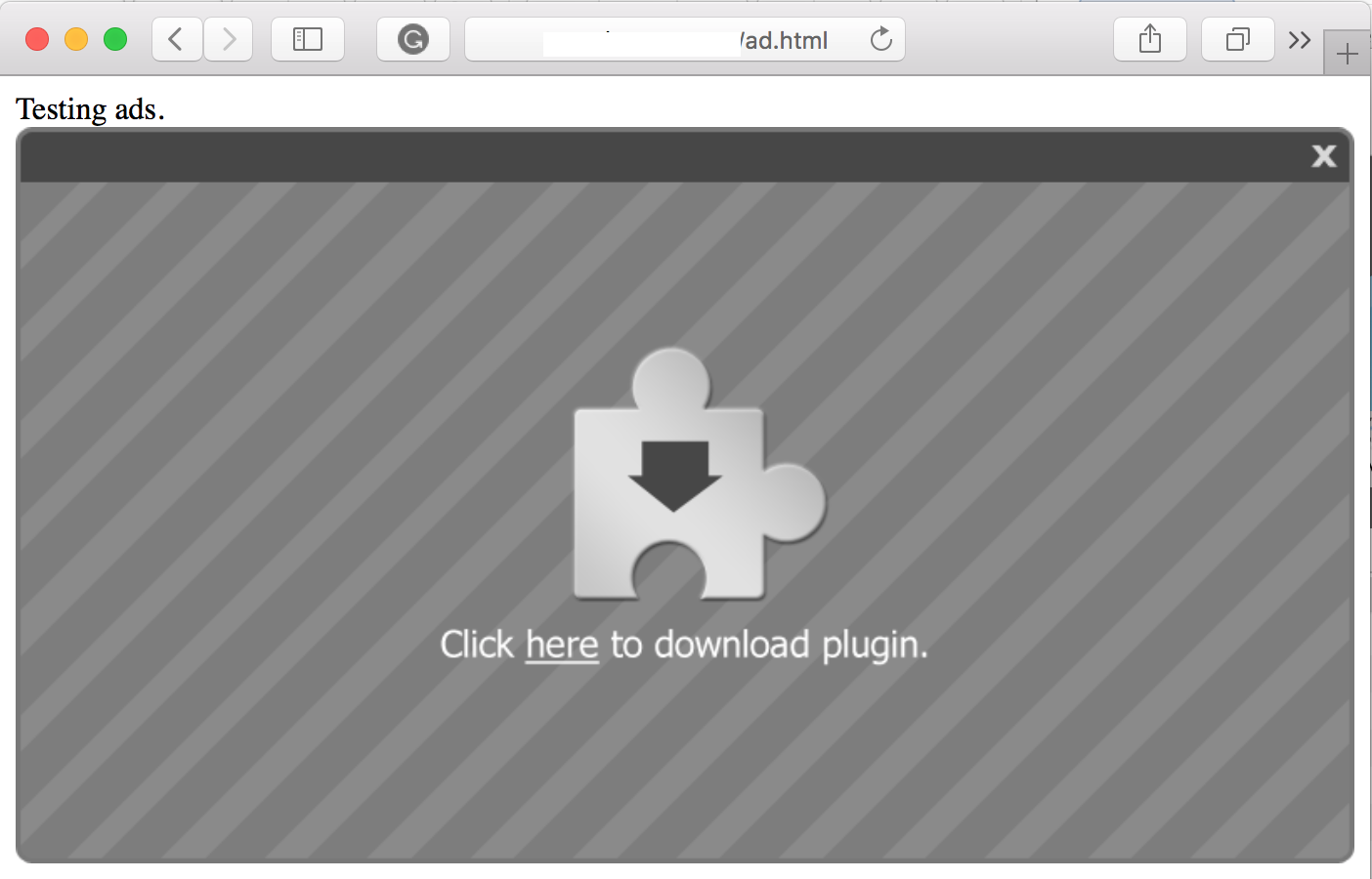
Next, you are offered a download:
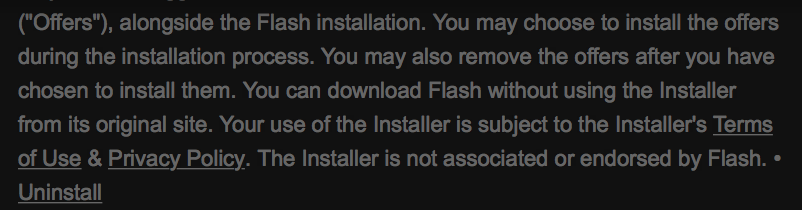
Below this dialog, a hard to read disclaimer is displayed (I left the colors "as is." Click on the image for a full-resolution version):
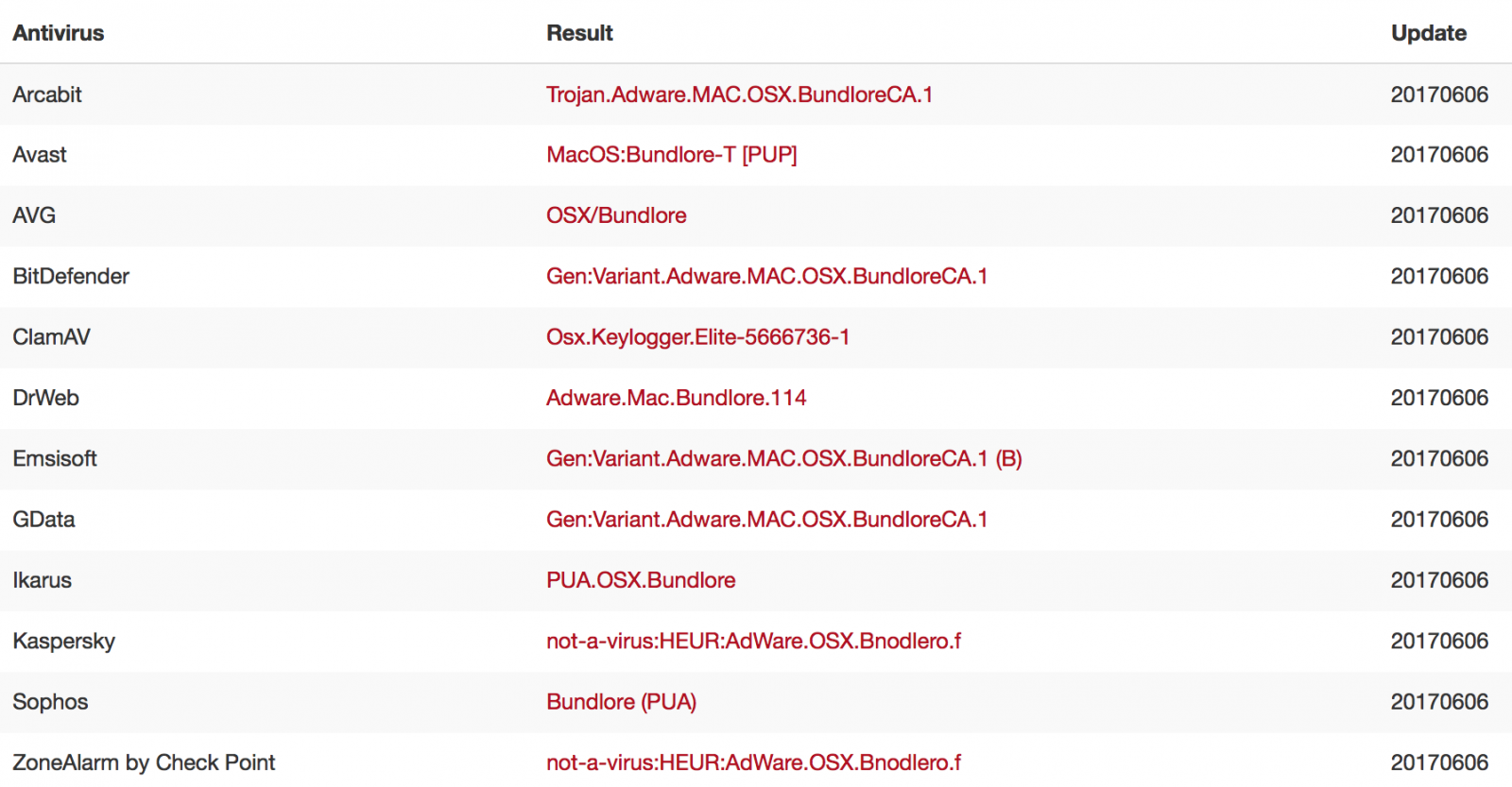
Virustotal identifies the resulting download as "Adware." I didn't install it, but from experience, the installer will install a valid Flash Player in addition to a bunch of adware, often in the form of browser toolbars.
Now, these ads were after all displayed on my page, and I had an account set up with RevenueHits. So I decided to inquire about the deceptive ads I received:
I just started testing revenue hits, and all the ads I receive are downloads of fraudulent media players. Is there a way to filter these ads? Do you have a way to flag ads as inappropriate? thx.
The moment I submitted this request, I received the following (obviously automated) response:
JohannesUllrich
Your account was automatically banned by our system, due to fraudulent traffic sources.
Please notice that once our system mark your traffic as fraud, there is nothing I can do to change it
Please check again all you traffic sources.
Regards
Support team
The ads continued to be displayed on my site. A business day later, I received a manual reply to my initial question:
Hi Johannes
Thank you for reaching out to us.Our Design team is working these days on the diversity of our ads.
We are committed to achieve the highest performance as possible for you. Therefore, the ads you see today are the best performing ones on your traffic.
You can remove some of them from your site but note that it might affect your results.
I still receive exclusively deceptive ads from RevenueHits. However, at least the results are not that bad. RevenueHits would pay me $0.36 for the one "click through" it counted. I haven't set up payment details with them and have no intentions of claiming the prize ;-)
---
Johannes B. Ullrich, Ph.D., Dean of Research, SANS Technology Institute
STI|Twitter|
| Application Security: Securing Web Apps, APIs, and Microservices | Las Vegas | Sep 22nd - Sep 27th 2025 |


Comments
His safari browser had been sent a malware page which could not be exited from. It was easy enough for me to go to settings and dump all Safari history to recover. The 866 number given was listed as a known scammer using a quick google search.
Anonymous
Jun 9th 2017
8 years ago