Testing for opened ports with firewalk technique
by Manuel Humberto Santander Pelaez (Version: 1)
There is an interesting way of knowing what kind of filters are placed in the gateway of a specific host. It is called firewalk and it is based on IP TTL expiration. The algorithm goes as follows:
- The entire route is determined using any of the traceroute techniques available
- A packet is sent with the TTL equal to the distance to the target
- If the packet times out, it is resent with the TTL equal to the distance to the target minus one.
- If an ICMP type 11 code 0 (Time-to-Live exceeded) is received, the packet was forwarded and so the port is not blocked.
- If no response is received, the port is blocked on the gateway.
Let?s see this with a real example. Consider the following network diagram:
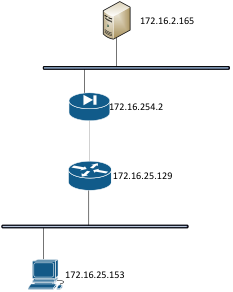
Firewalking happens with the following steps:
- Traceroute packets are sent to determine the gateway with decremental TTL:
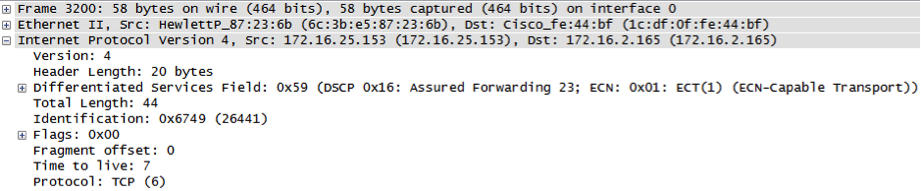
....
2. An ICMP Time Exceeded message is received from the default gateway for the TTL=2 and TTL=1 packet, which means there are two gateways between origin and destination and TTL=3 is the distance to the destination
.png)
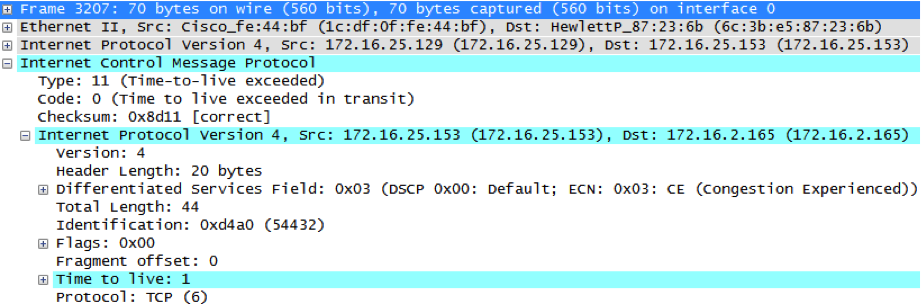
3. Several packets are sent with TTL=3 to the destination varying the destination port. The sequence goes as follows: A first packet is sent with TTL=3. If a timeout occurs, a second packet is sent with TTL=1. If an ICMP type 11 code 0 (Time-to-live exceeded) is received, the gateway is forwarding the packet.
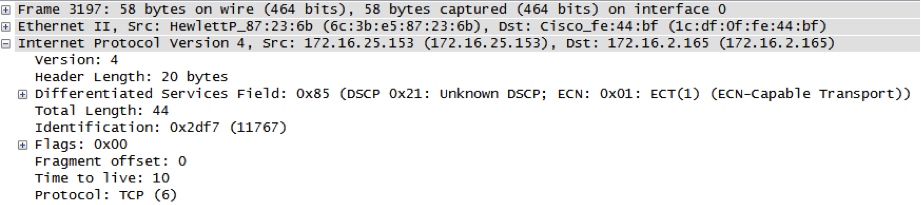
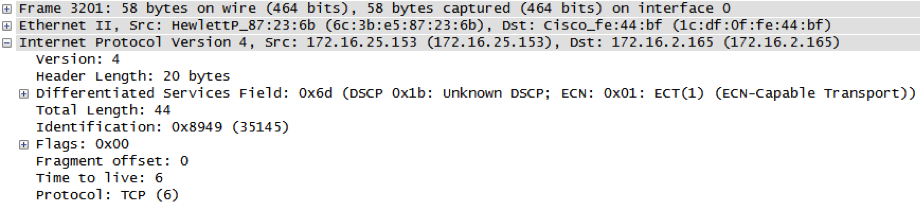
Let?s see the first packet to port 1 and TTL=3:
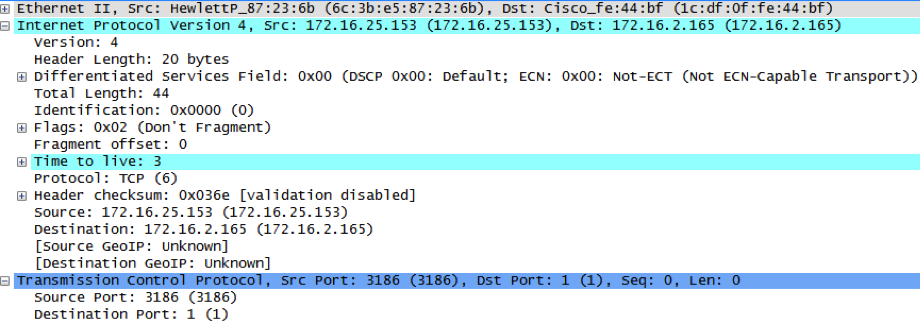
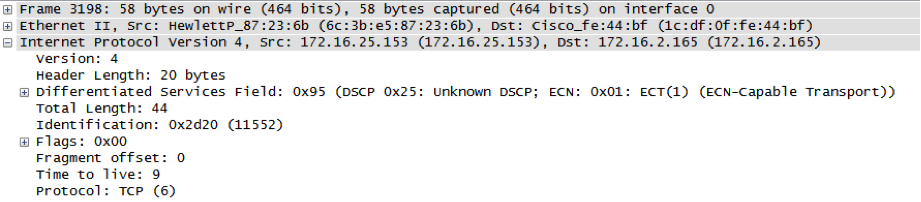
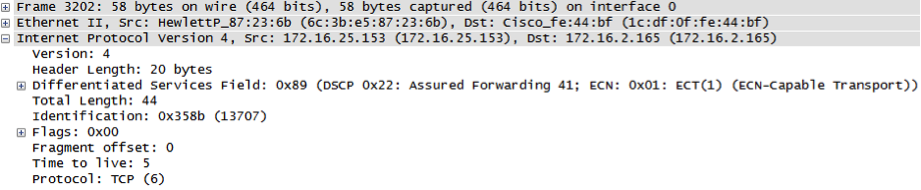
Timeout occurs, so same packet is sent with TTL=2:

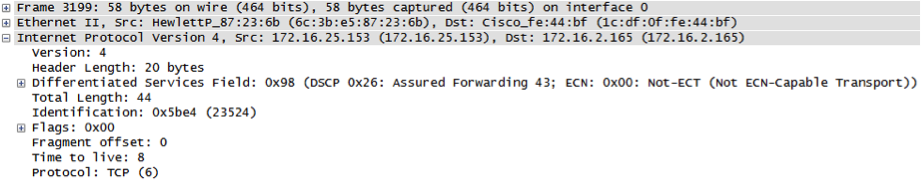
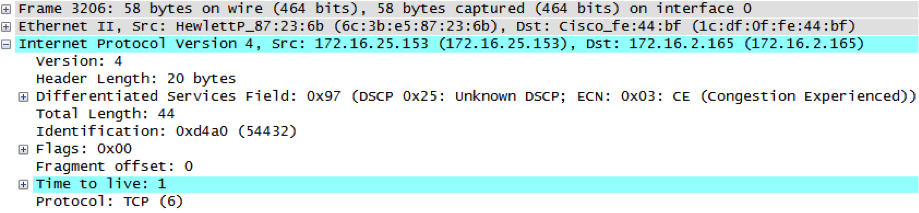
ICMP type 11 code 0 is sent from the gateway routing the destination host, which means the packet was forwarded and the port is opened:
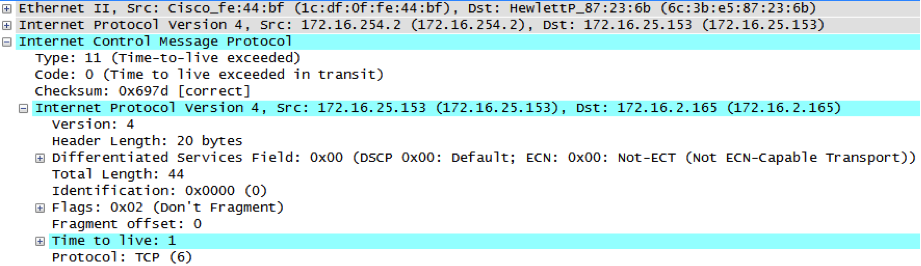
How can we use this technique? Nmap has a firewalk script that can be used. For this example, the following command should be issued:
nmap --script=firewalk --traceroute 172.16.2.165
Manuel Humberto Santander Pelaez
SANS Internet Storm Center - Handler
Twitter:@manuelsantander
Web:http://manuel.santander.name
e-mail: msantand at isc dot sans dot org


Comments