DShield SIEM Docker Updates
Since the last update [5], over the past few months I added several enhancements to DShield SIEM and webhoneypot sensor collection that included an update to the interface to help with DShield sensor analysis. I updated the main dashboard to have all the main analytic tools listed on the left for quick access to all the sub-dashboards.
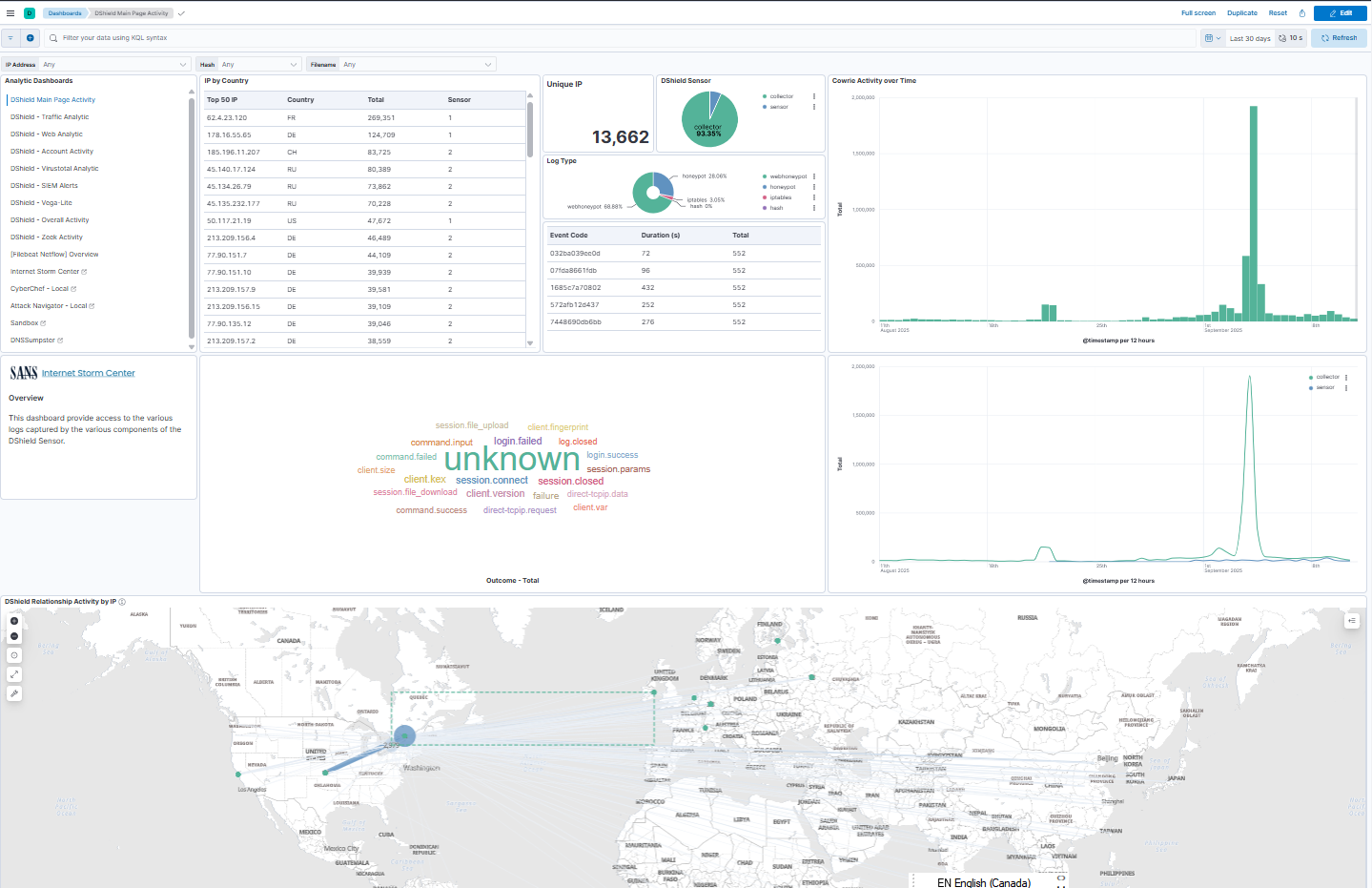
ELK Update
- Removed from the interface the usage of TCP 5601, now just https://IP
- Updated all Elastic packages to version 8.19.3
- Updated the webhoneypot logstash parser based on Mark's update
- Updated the DShield - Web Analytic page to reflect new content
- ELK monitoring with Metricbeat
- 2 Treat Intel feeds (run from ELK server via cronjob)
- Inclusion of ISC web activity detection rules
- Updated cowrie and docker troubleshooting pages [2][3]
- List of previous SANS.edu BACS internships students’ scripts [4]
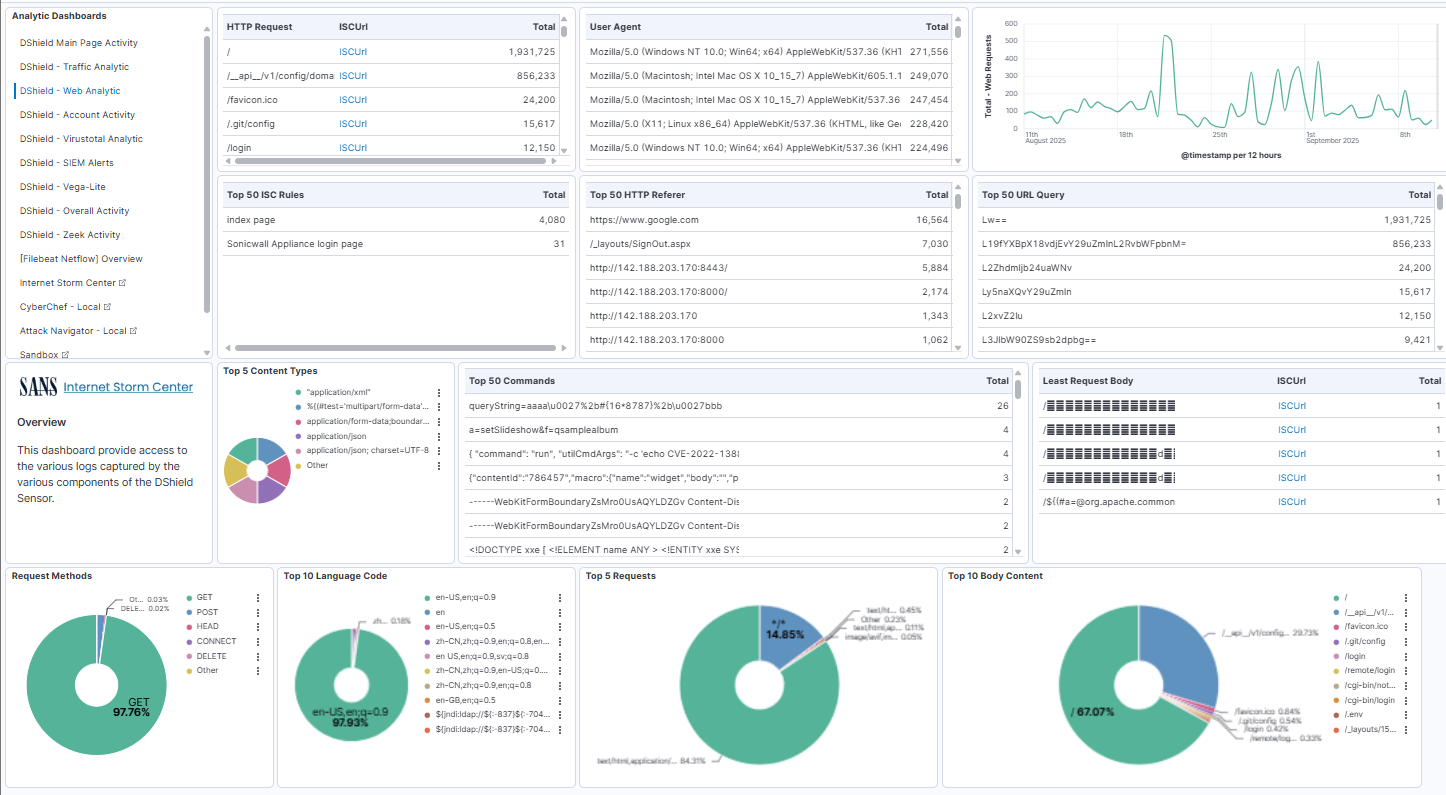
I tested and added two additional applications in the Kibana DShield Main Page Activity to help with analysis. These are installed via docker when installing or updating docker to the current version:
Analysis Tools
- CyberChef
- Mitre ATT&CK - Attack Navigator
How to upgrade to the current version?
- cd DShield-SIEM
- sudo docker compose stop
- git pull --autostash
- sudo docker compose rm -f -v
- sudo docker compose up --build -d
Load new templates into Kibana:
- sudo docker exec -ti filebeat bash
- ./filebeat setup -e
[1] https://github.com/bruneaug/DShield-SIEM/blob/main/README.md
[2] https://github.com/bruneaug/DShield-SIEM/blob/main/Troubleshooting/docker_useful_commands..md
[3] https://github.com/bruneaug/DShield-SIEM/blob/main/Troubleshooting/Troubleshooting_SIEM_and_Sensor.md
[4] https://github.com/bruneaug/DShield-SIEM/blob/main/README.md#dshield-analysis-scripts-and-code-by-students
[5] https://isc.sans.edu/diary/DShield+SIEM+Docker+Updates/31680
[6] https://www.sans.edu/cyber-security-programs/bachelors-degree/
-----------
Guy Bruneau IPSS Inc.
My GitHub Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu
BASE64 Over DNS
On the Stormcast, Johannes talked about BASE64 and DNS used by a backdoor.
I was interested to learn more about this, because DNS labels can only contain letters, digits and a hyphen. If you make a distinction between uppercase and lowercase letters, you have exactly 63 characters to choose from. While BASE64 requires 64 characters (and a 65th character for padding: =).
So how can the backdoor use BASE64 in a label, since RFC 1035 (and updates) does not allow characters +, / and = ?
I did some tests.
I had my dnsresolver.py tool running on a server, configured to answer DNS A requests for label Aa0+/=.
And it just worked:
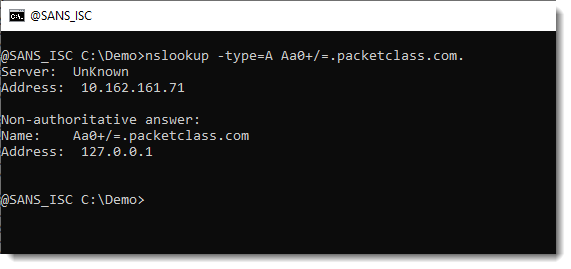
nslookup doesn't check the format of the labels, and neither did the DNS servers that forwarded my queries to my dnsresolver.py tool.
But the Windows APIs that help with resolving hostnames, do care about the format.
For example, the ping tool that uses the Windows API, doesn't work:
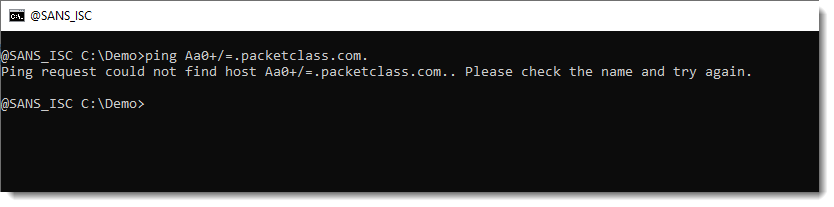
Neither does the DnsApi:
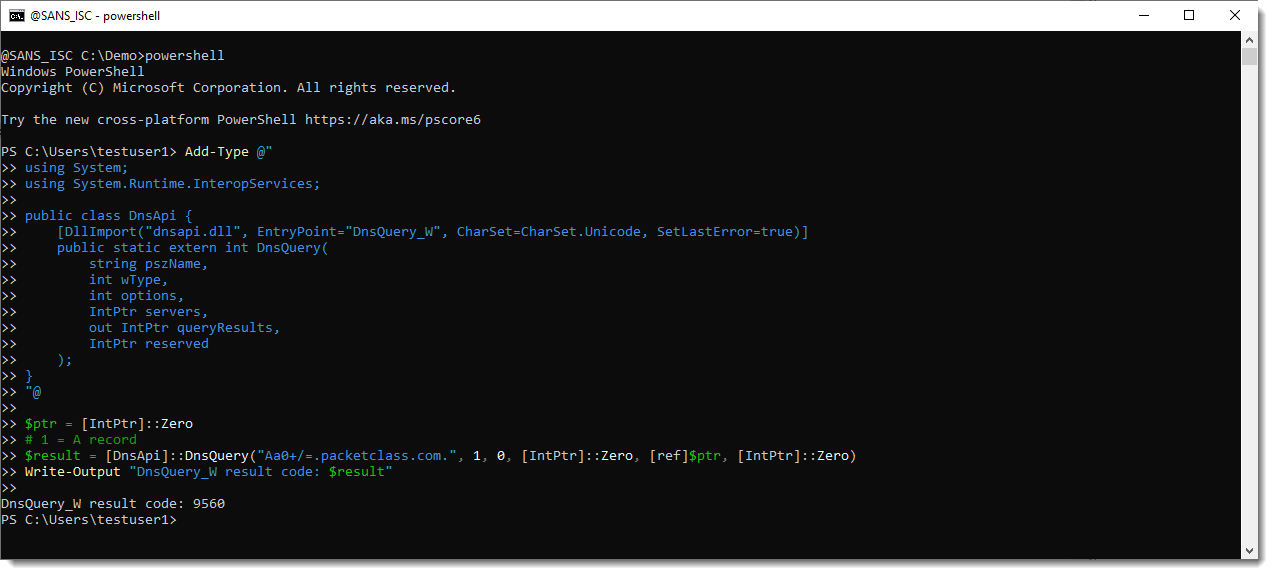
Error 9560 is because of the +, / and = characters I used:
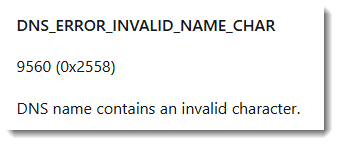
Thus malware can use special characters in DNS labels as a C2 channel, but then it has to talk directly to the DNS server (like nslookup does), it can't use Windows APIs to achieve this.
It might be interesting to check your DNS logs (if you have them) for labels with special characters. It's something I'll investigate and report later.
Didier Stevens
Senior handler
blog.DidierStevens.com


Comments