Netfox Detective: An Alternative Open-Source Packet Analysis Tool
[This is a guest diary by Yee Ching Tok (personal website here (https://poppopretn.com)). Feedback welcome either via comments or our contact page (https://isc.sans.edu/contact.html)]
Various digital forensic artifacts are generated during intrusions and malware infections. Other than analyzing endpoint logs, memory and suspicious binaries, network packet captures offer a trove of information to incident handlers that could help them triage incidents quickly (such as determining if sensitive data had been exfiltrated). Popular tools such as WireShark, Ettercap, NetworkMiner or tcpdump are often used by incident handlers to analyze packet captures. However, there could be situations where a tool is unable to open up packet captures due to its size or being deliberately tampered (perhaps in Capture-the-Flag (CTF) challenges to increase difficulty and complexity). As such, being proficient in multiple alternative tools for packet analysis could come in handy, be it for handling incidents or for CTF challenges.
I recently came across an open-source tool for packet analysis named Netfox Detective [1], developed by the Networked and Embedded Systems Research Group at Brno University of Technology [2]. To showcase some of its features, I mainly used the packet capture created in my previous diary [3]. Firstly, with reference to Figure 1, a workspace needs to be created. As the name implies, the created workspace will contain artifacts such as packet captures or logs that would be analyzed (in this example, I only used network packet captures and did not import any logs).
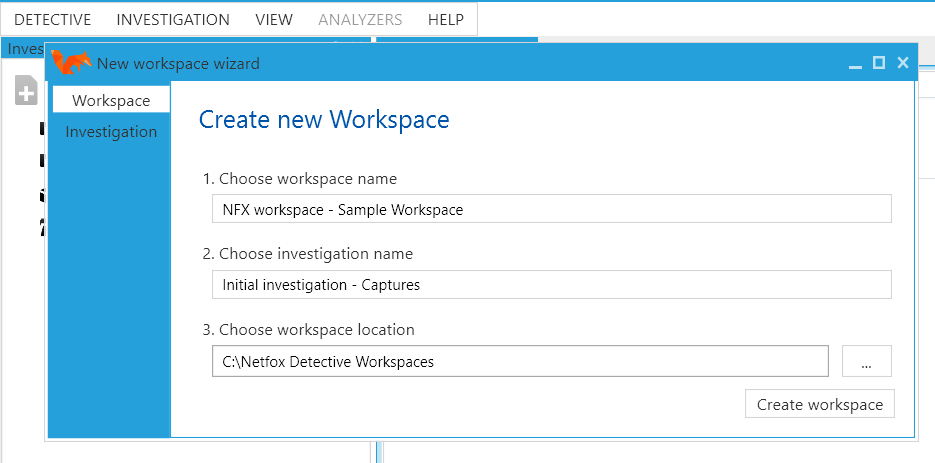
Figure 1: Creation of Workspace for Analysis
Following that, I imported the network packet capture created in my previous diary [3] and Figure 2 shows an overview of the statistics of the packet capture. An interesting observation was that I did not know some packet loss occurred during the capture I made previously. It was also interesting to note that Netfox Detective utilized TCP heuristics that the creators have developed previously and improved on to mitigate corrupted or missing packets so as to collate as many network conversations as possible [4].
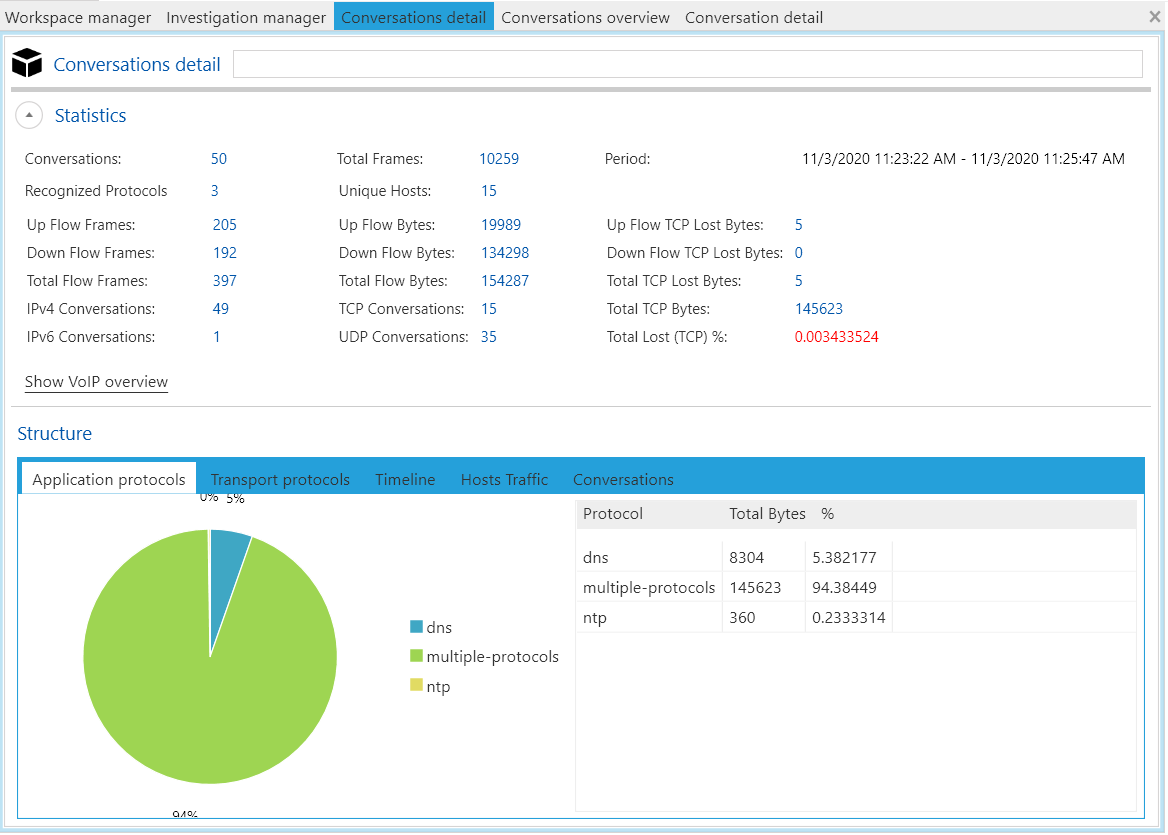
Figure 2: Overview of NAT Slipstreaming Packet Capture
As compared to WireShark where packets are displayed linearly, Netfox Detective has a tabbed view and displays the packets at Layer 3, Layer 4 and Layer 7 (linear option also available by selecting the “Frames” tab). Figure 3 shows the Layer 4 tab being selected and corresponding results being displayed.
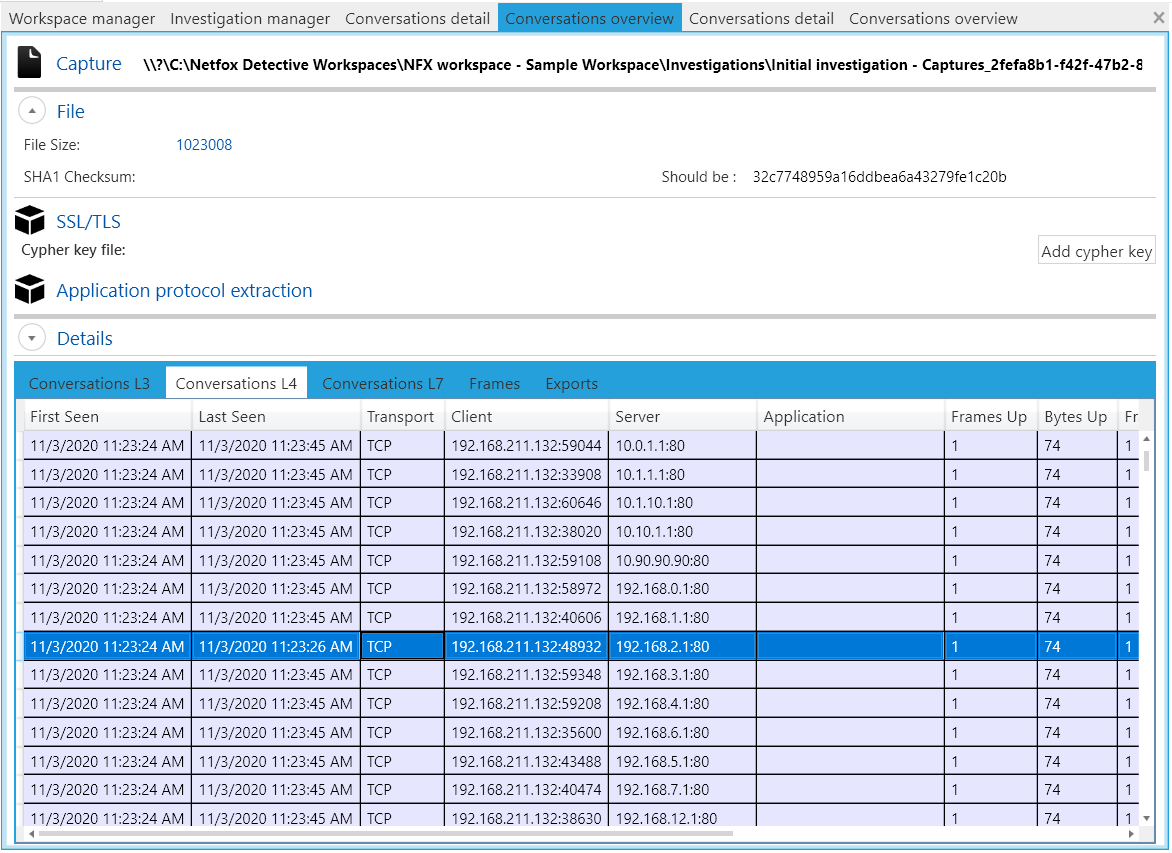
Figure 3: Netfox Detective displaying Layer 4 Network Traffic
Selecting a conversation (highlighted in Figure 3) will add the selection in the “Conversation explorer” pane (highlighted by the red box in Figure 4). Double clicking the entry in “Conversation explorer” will create a new tab “Conversation detail” where a summary of the interaction is displayed (as shown in Figure 4). I found the Packet Sequence Chart to be very useful as it visualized when the various packets were transmitted with respect to their frame size.
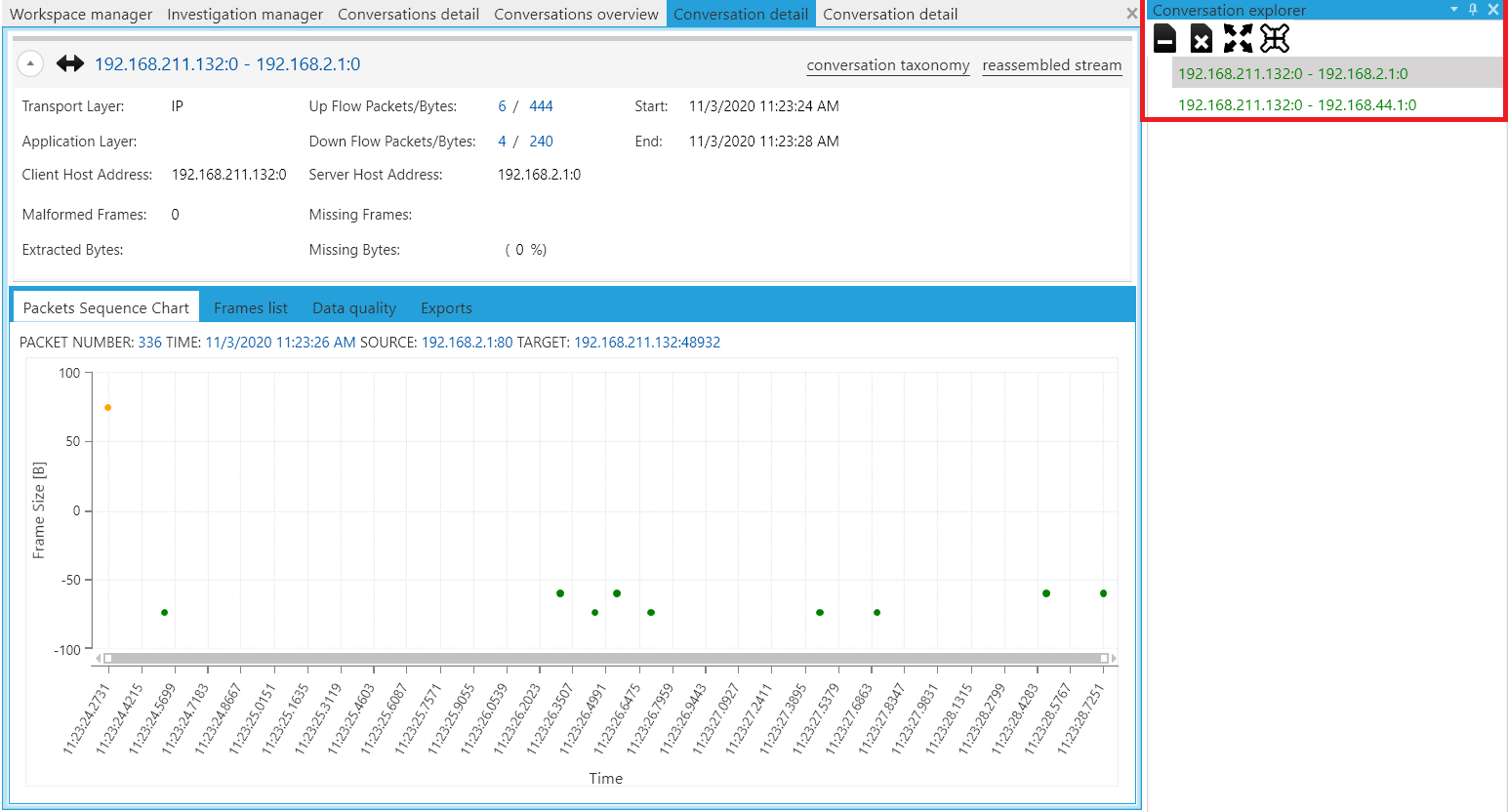
Figure 4: Conversation detail view of 192.168.211.132 and 192.168.2.1
Following that, with reference to Figure 5, I selected frame number 336 for an in-depth look and we can see the ACK and RST flags being reflected in this packet (an expected finding as per the observations of NAT Slipstreaming experiment I done previously).
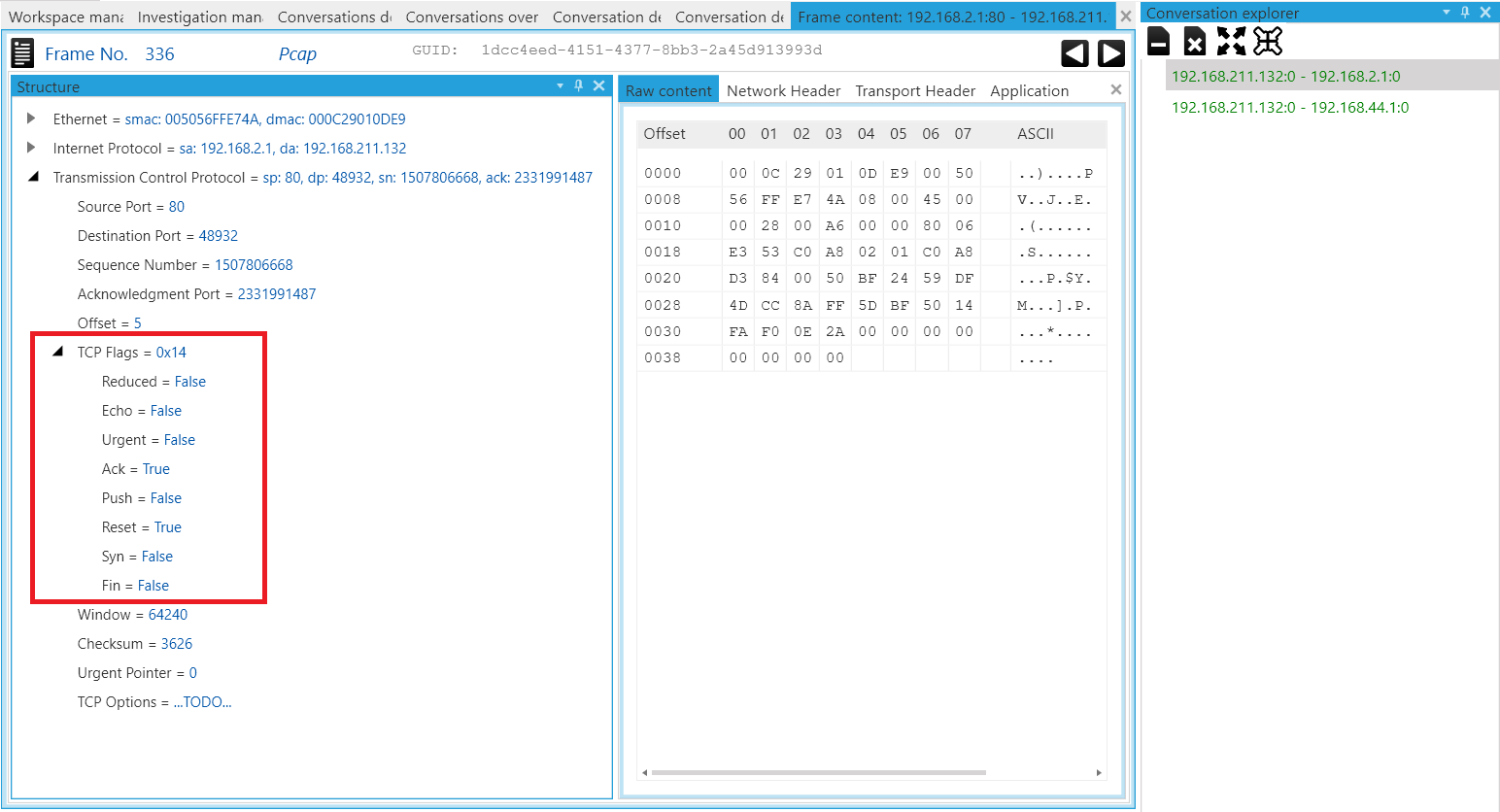
Figure 5: Frame content view of Frame Number 336
There could be instances where analysis of multiple related network packet captures is needed in an incident. Netfox Detective allows multiple packet capture files to be imported into the same workspace (as shown in Figure 6). Over here, I used another packet capture created by Brad Duncan [5] to demonstrate the feature.
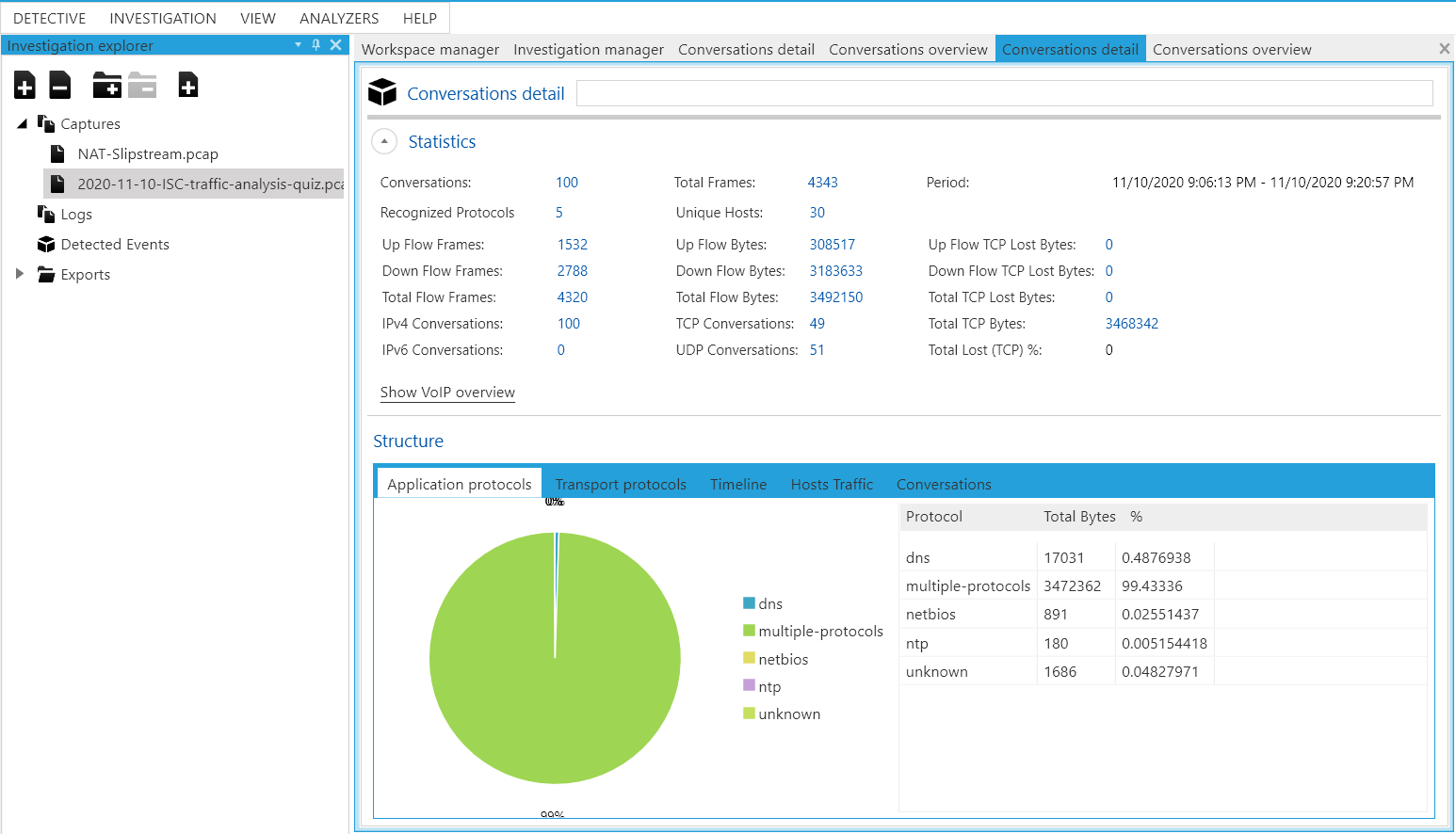
Figure 6: Importing Multiple Packet Capture Files into the Same Workspace
As always, there are strengths and weaknesses in the various tools we use for packet analysis. Netfox Detective can only be installed on Microsoft Windows (Windows Vista SP2 or newer), and supports a smaller subset of protocols as compared to other tools such as WireShark [1]. However, the various tabbed views at Layer 3, 4 and 7, packet visualizations and ability to group related packet captures in a same workspace offers a refreshing perspective for incident handlers to perform their analysis/triage on network packet captures. Moreover, the open-source nature of Netfox Detective allows further enhancements to the tool itself.
For a complete read about Netfox Detective’s design decisions and technical implementations, their published paper is available here [4]. To download Netfox Detective, the information can be found on their GitHub page [1].
[1] https://github.com/nesfit/NetfoxDetective/
[2] https://nesfit.github.io/
[3] https://github.com/poppopretn/ISC-diaries-pcaps/blob/main/2020-11-NAT-Slipstream.zip
[4] https://doi.org/10.1016/j.fsidi.2020.301019
[5] https://www.malware-traffic-analysis.net/2020/11/10/index.html
| Application Security: Securing Web Apps, APIs, and Microservices | Las Vegas | Sep 22nd - Sep 27th 2025 |


Comments