AV Cleaned Maldoc
An anonymous reader reported an unusual malicious Office document.
This is oledump's output for this file:
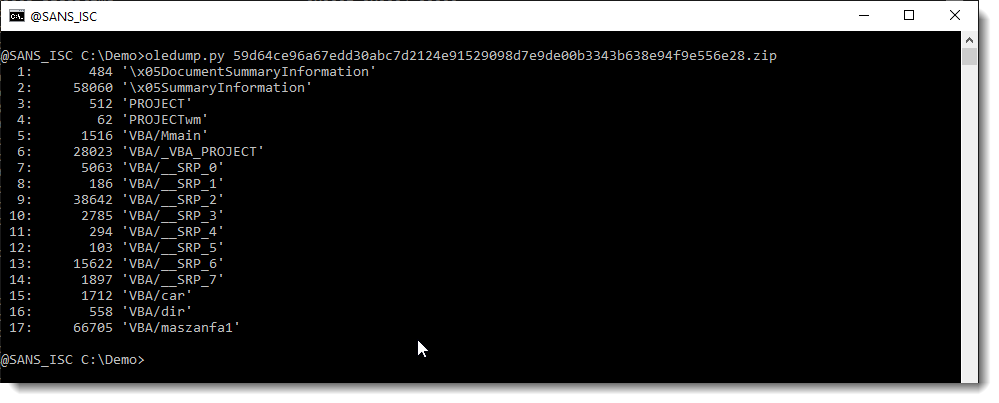
Although there is a VBA storage and all the usual streams associated with VBA macros, oledump does not display macro indicators (M or m).
In such cases, I always use option -i like this:
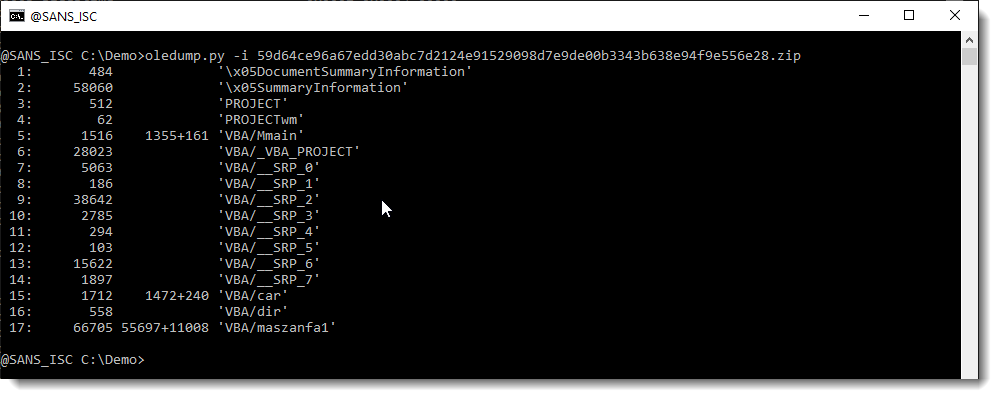
When you use option -i (--info) without options -s, an extra column is added to the overview of streams. For all VBA module streams, a value like c+s will be displayed in that column. c stands for compiled code and s for source code.
For example, for stream 5, we have value 1355+161: this means that the first 1355 bytes of this stream contain compiled VBA code, and the following 161 bytes contain compressed VBA source code. Remark that the sum of 1355 and 161 is 1516, e.g. the size of the stream.
So now we know that stream 5, 15 and 17 are VBA modules, but that there's something unusual with them (otherwise we would see a macro indicator: M or m).
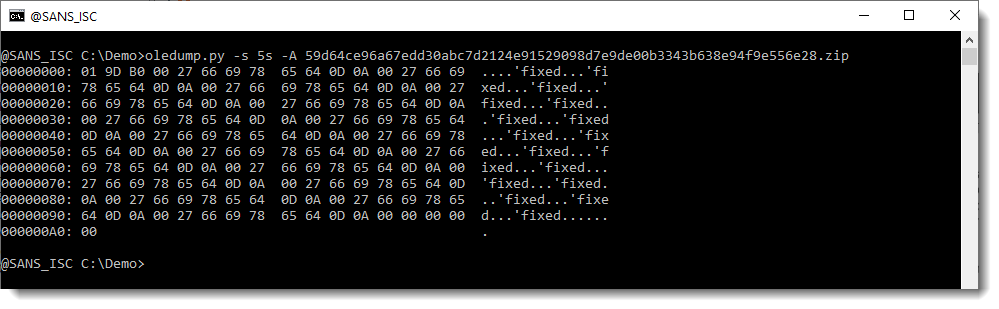
Let's take a look at the content of stream 5: I use option -A to output a run-length compressed hexadecimal/ASCII dump. If there are repeating rows in the hexadecimal/ASCII dump, they will be counted and removed:
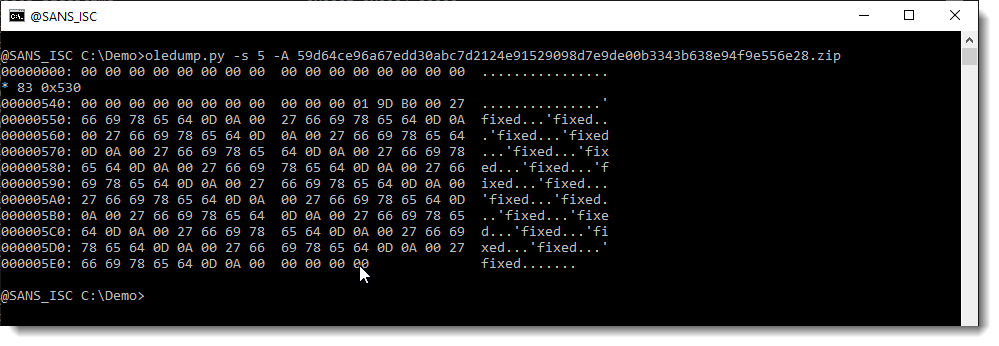
The first row is all NULL bytes (00), and the following 83 rows too. And then we have some binary data with a repeating ASCII string: 'fixed.
When I see this, I start to think that this is a malicious Office document that has been cleaned: the malicious code has been removed. Let's check, by taking a look at the compiled code and the VBA code separately. I'll start with the compiled code:
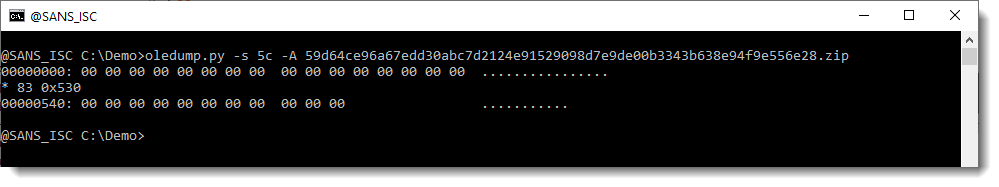
The 1355 bytes of compiled code are all 00: that's not normal.
The source code:
VBA source code is compressed, but doesn't look like this. If you try to decompress the VBA source code with option -v, like we usually do, it will not work. option -v is specific for compressed VBA source code produced by an Office application. If you want to decompress any data (including VBA source code), you have to use option --decompress like this (I'm also using option -d to dump the output):
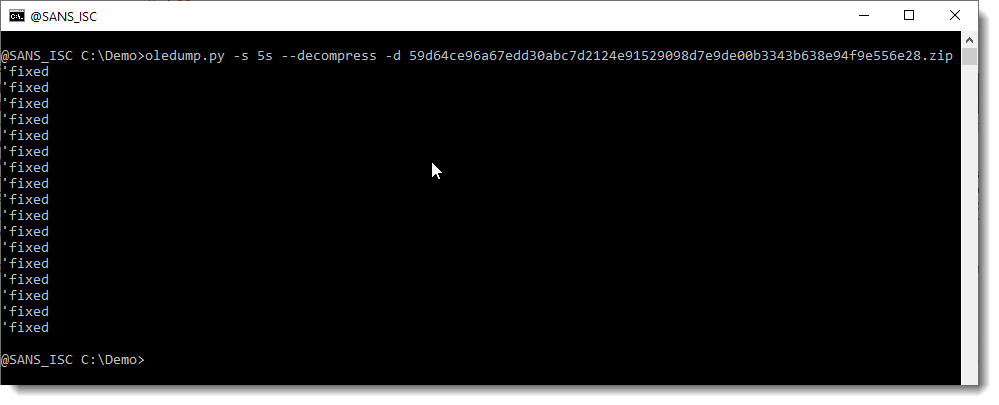
So this is indeed compressed ASCII text: a repetition of the line 'fixed.
But it is not VBA code compressed by an Office application, as it does not start with "Attribute VB_.." (option -v searches for VBA code staring with Attribute VB_...).
So this certainly looks to me like a malicious Office document where the VBA macros have been cleaned by an anti-virus program. But which AV?
We get a good clue by looking at the compressed data of stream 15:
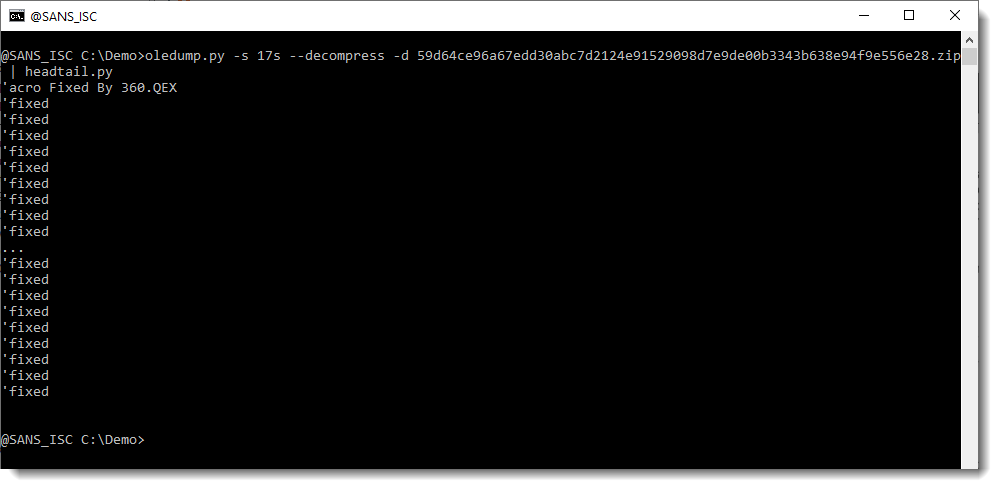
The first line reads: 'macro Fixed By 360.QEX
That's the AV of Qihoo 360: 360 Safeguard. That's very thoughtful of the developers to add a message that helps me identify the AV product that did this.
So the module streams have been wiped: no compiled code and no source code. This maldoc can no longer execute.
But there are some other streams that contain compiled code too, like stream _VBA_PROJECT:
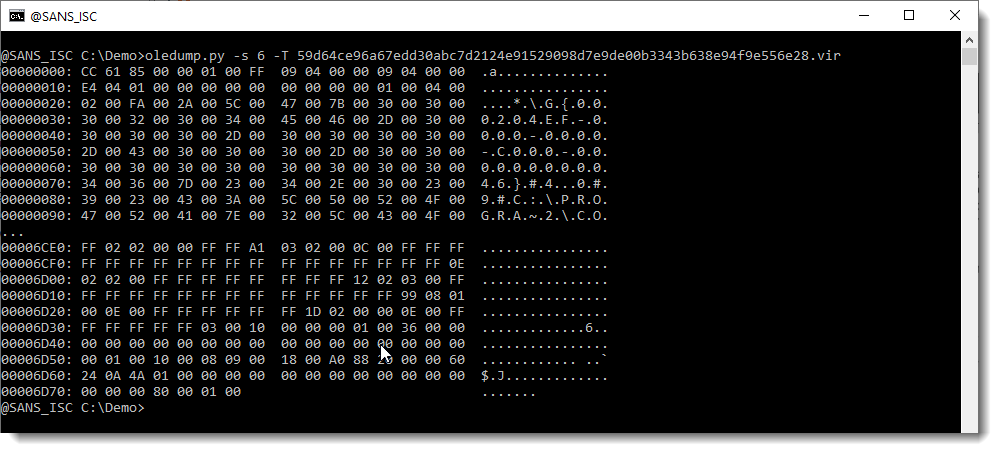
This one has not been cleaned. Let's take a look at the strings inside this stream:
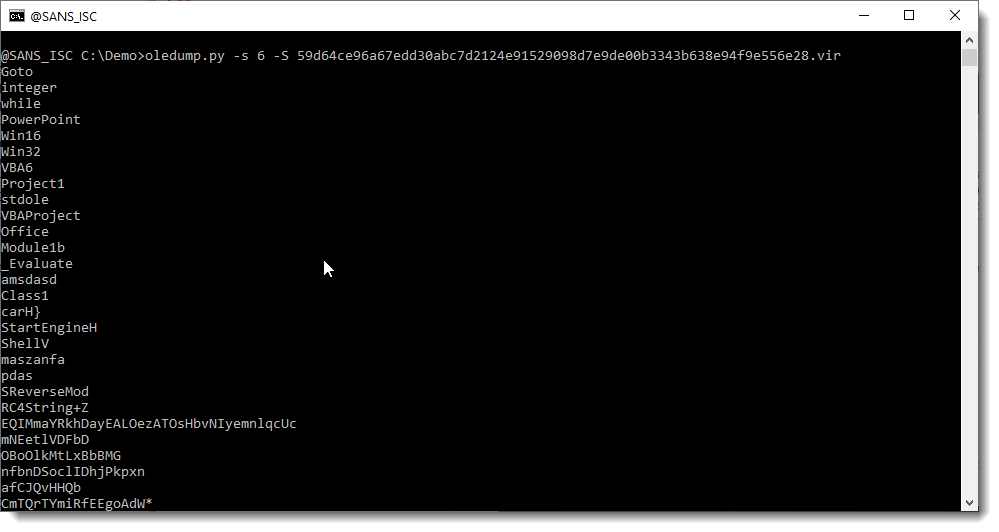
So we have ShellV and different strings that look like BASE64: this is probably a maldoc that executes a PowerShell command.
I tried to find back the original maldoc using the method I described in this diary entry, but I had no success.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com



Comments