Your Supply Chain Doesn't End At Receiving: How Do You Decommission Network Equipment?
Trying to experiment with cutting edge security tools, without breaking the bank, often leads me to used equipment on eBay. High-end enterprise equipment is usually available at a bargain-basement price. For experiments or use in a home/lab network, I am willing to take the risk to receive the occasional "dud," and I usually can do without the support and other perks that come with equipment purchased full price.

Lately, I have been looking at some of Gigamon's "Gigavue" appliances, which have become available at very affordable prices. After I received the device, I did a quick inventory of its hardware components and configuration. Pretty much immediately, it became apparent that the device was not properly wiped. Sadly, this is a very common occurrence. The configuration of the device led me to the prior owner of the device, which turned out to be a company close to where I live. After contacting them, I returned the device to them to allow them to investigate the failure in their decommissioning procedure. I didn't do much analysis myself of this particular device before returning it. Still, it was kind of interesting how it arrived a few miles from its original home via a surplus equipment seller in a very different part of the country.
But... this left me one Gigamon short. So I did purchase a second one from a different eBay seller. Again, this device arrived "untouched" (but luckily with the default password, which was in particular nice since I couldn't get the serial console to work). Again, this device had an intact configuration, which included pretty much a detailed network map. But this time, I wasn't able to quickly identify the original owner, so I decided to take a quick look at what can be learned from these devices.
As one would expect, these devices are "servers." What differentiates them from regular servers is that the only significant persistent storage is a 2GByte SDCard. I was a bit surprised by this given the "iffy" reputation of SDCards. I have had plenty of them fail over the years and would have expected a bit "more" in a device in this price class. But I guess it does the job. The SDCard is easily removed and imaged.
So far, I haven't gotten around to a full analysis of the image, but the image includes the firmware and at least some of the configuration of the device. Of course, the configuration is also easily explored via the web-based GUI of the command line interface.
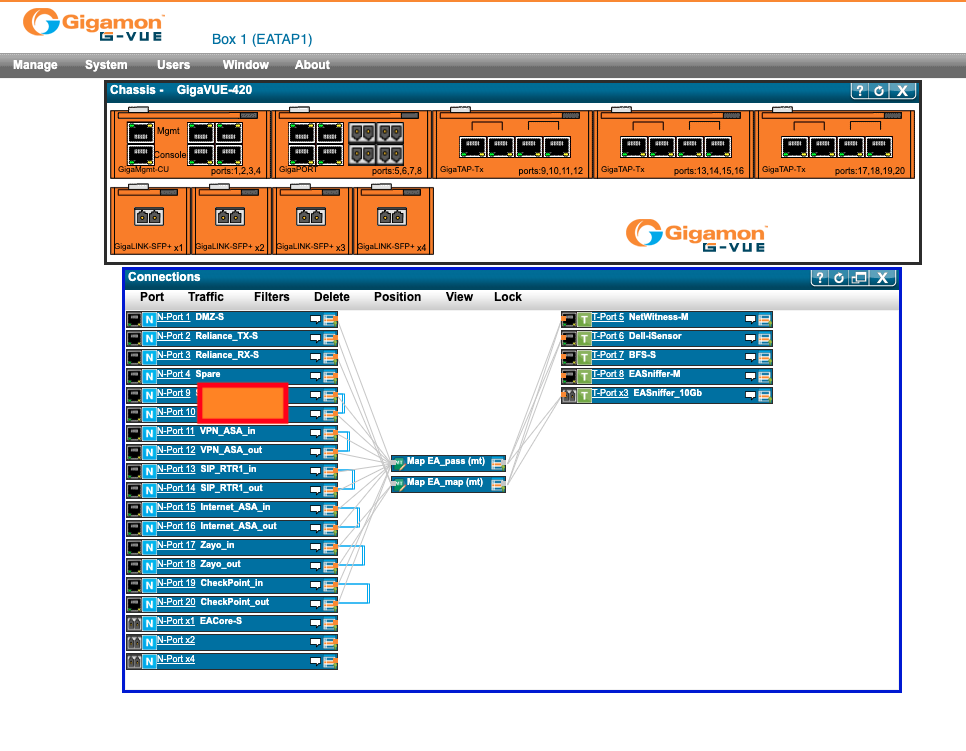
I covered one company name in the image above that may indicate the original owner (but it could also be a link to that company's service. Not clear based on the label used).
In addition to the configuration, I was also able to recover a partial syslog from the device, listing the private IP of the system from which the administrator connected to the system.
Interestingly, the administrator account used (not the default "root" account) was still configured, but the root password was set to the default password. I find it unlikely that just the root password was reset, and the remaining configuration was untouched. Gigamon does provide two commands to possibly wipe the configuration:
- sd_format: This command *should* format the SD card. But it is not clear if it will overwrite/wipe any content.
- reset system factory-default: According to the manual, this will reset the device to factory default.
- Via the serial console, the device can be reset using the "fconfig rstrtac true" command at the boot prompt. This process does not require a password and is used to reset the "root" password. It may not reset the configuration (I will have to try this out once I got the serial console working).
I did not find any customer data / PII on the systems. The risk is probably best classified as "information leakage." An attacker could certainly obtain valuable intelligence from the configuration, maybe even deduct usernames and passwords for other devices.
Lesson learned: A lot of people are talking about "Supply chain security" these days. Your supply chain doesn't end once you receive a piece of equipment. The decommissioning process and any vendors used as part of it should be considered part of the supply chain.
I will follow up on this diary once I have more time to explore some of the settings and options. Let me know if you have attempted this before and have any insight, or if you have similar stories to share.
---
Johannes B. Ullrich, Ph.D., Dean of Research, SANS Technology Institute
Twitter|
| Application Security: Securing Web Apps, APIs, and Microservices | Las Vegas | Sep 22nd - Sep 27th 2025 |


Comments