Don't launch that file Adobe Reader!
Maybe you read my PDF + DOC malicious document diary entry, or maybe even you tested your system with my PDF + DOC test file, and maybe you wondered if you could change Adobe Reader's behavior.
Well, no more "maybes": you can. Years ago, when PDF malware was the most widespread malicious document type, disabling JavaScript in Adobe Reader was a recommendation.
But you can also prevent Adobe Reader from opening embedded files and launching the associated application. Here is the setting in the Trust Manager to do this:
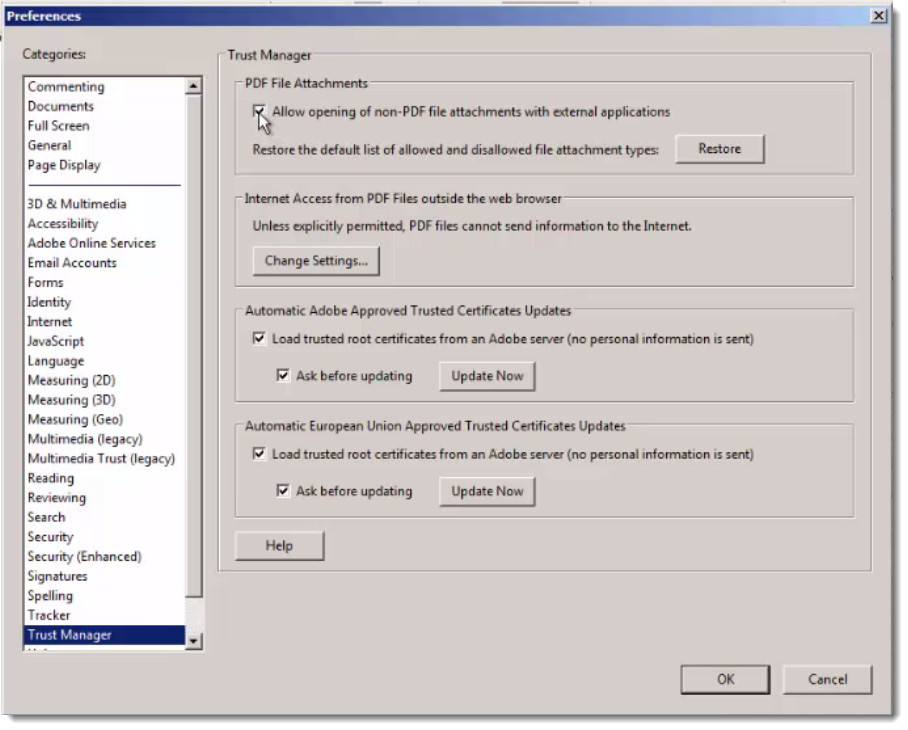
And if PDF attachments are important in your organization, this setting will not prevent attachments from being saved (extracted). Only from being launched from within Adobe Reader.
I also have a video showing the effects of this setting (plus the JavaScript setting).
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com
My YouTube Channel


Comments
The registry settings for that (and a couple of others I change) in v11 are:
HKCU\Software\Adobe\Adobe {Acrobat | Reader}\11.0\Originals\bAllowOpenFile = 0
HKCU\Software\Adobe\Adobe {Acrobat | Reader}\11.0\JSPrefs\bEnableGlobalSecurity = 1
HKCU\Software\Adobe\Adobe {Acrobat | Reader}\11.0\JSPrefs\bEnableJS = 0
Anonymous
Sep 21st 2015
9 years ago
I've seen a bunch of posts from others on the internet saying they had to manually create these registry changes to affect previous versions of Adobe, ergo Reader XI.
Seeing as Adobe Reader DC is located in HKLM\Software\Wow6432Node\Adobe\Acrobat Reader (and not HKCU\Software\Adobe\Acrobat Reader\11.0) how would one go about making these changes for an enterprise organization?
Anonymous
Sep 21st 2015
9 years ago
But if those settings are now located in HKLM with DC versions and newer, then that makes it MUCH easier to push out with a REG file.
Anonymous
Sep 21st 2015
9 years ago
Nice read from NSA
+ Recommendations for Configuring Adobe Acrobat Reader XI in a Windows Environment
http://www.nsa.gov/ia/_files/app/Recommendations_for_Configuring_Adobe_Acrobat_Reader_XI_in_a_Windows_Environment.pdf
Anonymous
Sep 22nd 2015
9 years ago