Challenges of Anti-Phishing Advice, the Google Docs Edition
Coming up with meaningful anti-phishing advice is hard, in part because even the most pragmatic tips cannot be practical in all situations. Scams where the attacker's data-collection form resides at a Google Docs (now Google Drive) are especially difficult to warn users about. After all, the malicious webpage resides at the trusted google.com domain. The effect is especially severe for organizations using Google Apps as a collaboration platform.
Using Google Docs for hosting phishing forms isn't new. F-Secure published several examples of such scams in May 2011; GFI shared additional screenshots in June 2011; Sophos outlined some examples in May 2012.
To understand why such scams aren't going away any time soon, consider the example that came to our attention this month. The malicious email arrived with the subject "Message From I.T Service Helpdesk" and alerted the user, "Your mailbox is almost full."
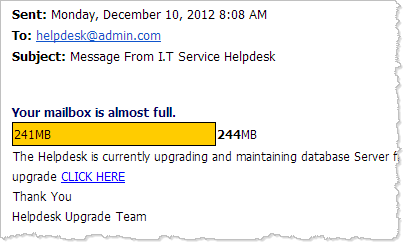
Recipientswho clicked the "CLICK HERE" link were directed to the following "IT HELPDESK SERVICE" page, which prompted for logon credentials that the attacker wanted to capture.
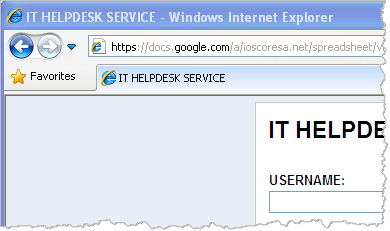
Although the landing page had a very basic look to it, it resided at the domain that most people trust: google.com. The attacker was likely using a compromised Google Apps account of another organization to create a Google Docs spreadsheet and expose its data entry form in the manner shown above.
The use of the Google domain is what lends credence to the phishing scams that make use of Google Docs. The targeted individuals can no longer rely on the advice we often give: Examine the URL bar to confirm that you are at a trustworthy site. This problem is especially severe for individuals whose organizations use Google Aps for email, calendaring and file management needs. In such cases, administrative communications are expected to come through or reside at the google.com domain.
What anti-phishing advice could we offer to potential Google Docs phishing scam victims? There's the more general suggestion of being vigilant and looking out for anomalies, be they an unusual signature line in the email message or an unexpected look-and-feel of the web page. A more specific recommendation might be: Avoid clicking on email links when you need to take important actions that require logging in. Relying on a previously-saved bookmark is safer.
Is that practical advice? Not for all situations. This is what makes anti-phishing advice so challenging to provide.
-- Lenny Zeltser
Lenny Zeltser focuses on safeguarding customers' IT operations at NCR Corp. He also teaches how to analyze malware at SANS Institute. Lenny is active on Twitter and Google+. He also writes a security blog.



Comments
John
Dec 19th 2012
1 decade ago
John
Dec 19th 2012
1 decade ago
Yes, John it's nice that Google has an abuse reporting link.
Pity that they don't actually act on abuse complaints for days... sometimes phishing forms are online for weeks following multiple complaints.
You wouldn't guess it from their web design or mailing address (Romania), but the most responsive and helpful site out there is www.123contactform.com. I typically get a response from a human within 30 minutes. Often, they'll even give you the submitted data.
rich
Dec 19th 2012
1 decade ago
Never enter your password into any form, anywhere, or in response to a message with which you are unfamiliar. If in doubt, initial a telephone call to the help desk (don't trust an incoming call) or at least show the message to a co-worker. For IT, maximizing the use of "integrated windows authentication" and web initial sign-on systems can help tremendously. If you use Google Apps, you might have to do password sync for mobiles and other niche applications, but you should be authenticating users via SAML assertions from a web site in your domain. If you've taught your users that they need to give their password to any popup that asks for it, then that's what they'll do.
rich
Dec 19th 2012
1 decade ago
Rich, difference in service response may be that Google has 300M customers against what seems like 7 billion bad guys.
dsh
Dec 19th 2012
1 decade ago
John
Dec 19th 2012
1 decade ago
1) Generic greeting, i.e. Dear Sir, Dear Madam, etc. If they are really a company you do business with, they’ll have your name.
2) Huh? Any email that makes you go “huh?†is to be considered suspicious. Strange things you have no knowledge of are very often lures. Don’t take the bait. I have seen a great many curious users with infected computers.
3) Some sort of threat, i.e. your account will be suspended/closed, you won’t be able to receive email, your credit card will be billed, your computer will be compromised, etc.
4) To avoid the threat, you must act right now, or at least within the next 24-48 hours.
5) The action involves either clicking on a link, opening an attachment (includes running the program in the attachment), or filling out the form and emailing it back.
berzerke
Dec 19th 2012
1 decade ago
For end users, STOP USING LINKS IN ALL EMAIL.
If the link is 100% required, such as creating a new account. The user is (hopefully...) aware of links coming from that site. Otherwise, assume all links are tainted and navigate manually.
It is not easy advice, but it is the safest approach.
Beau
Dec 19th 2012
1 decade ago