Wireshark: Specifying a Protocol Stack Layer in Display Filters
The release of Wireshark 4.0.0 brings many new features, especially for the display filter syntax.
Specifying a protocol stack layer is one of the new syntax features. But let me first explain what the problem is, and then we can talk about the solution that the new syntax brings
Take the following packet capture, it shows failed attempts to establish a TCP connection: 192.168.10.10 sends a TCP SYN packet to 192.168.10.1, and this is followed by a "reply", 192.168.10.1 sending an ICMP packet (Destination unreachable) to 192.168.10.10. This happens 3 times (because the TCP stack tries 2 retransmissions and then gives up).
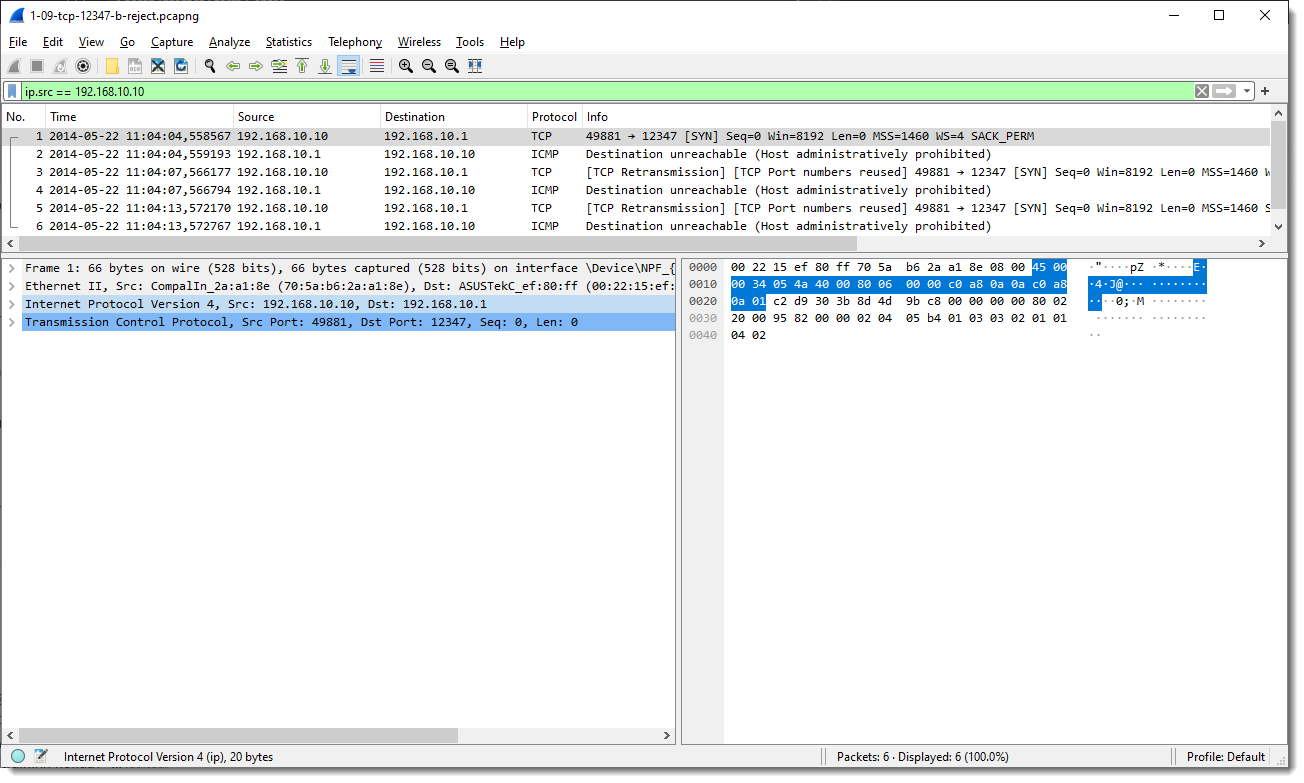
I use the following display filter: ip.src == 192.168.10.10
So I only want to see packets that come from 192.168.10.10. But although that display filter is applied, I still see the ICMP packets coming from 192.168.10.1.
Why is that? Because the ICMP packets embed the IP packets that caused the error:
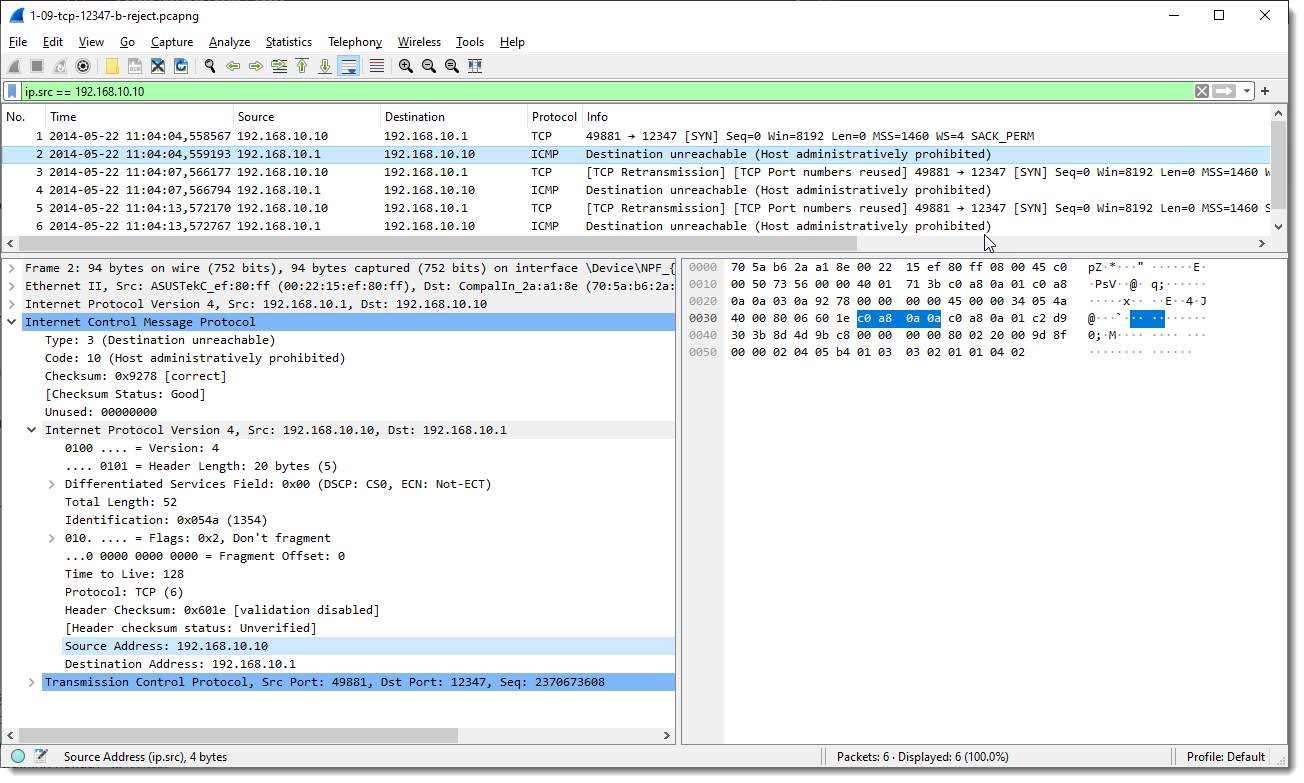
So these ICMP packets have 2 ip.src fields: one for the outher IP packet and one for the IP packet contained in the ICMP packet (that is contained in the outher IP packet).
And that is why the display filter is showing all packets. It shows the TCP SYN packets because ip.src matches 192.168.10.10, and it shows the ICMP packets because they contain a field ip.src that also matches 192.168.10.10.
The solution brought with the new syntax, is that one can specify explicitly the protocol stack layer that should be matched, like this: ip.src#layer. Where layer is a number.
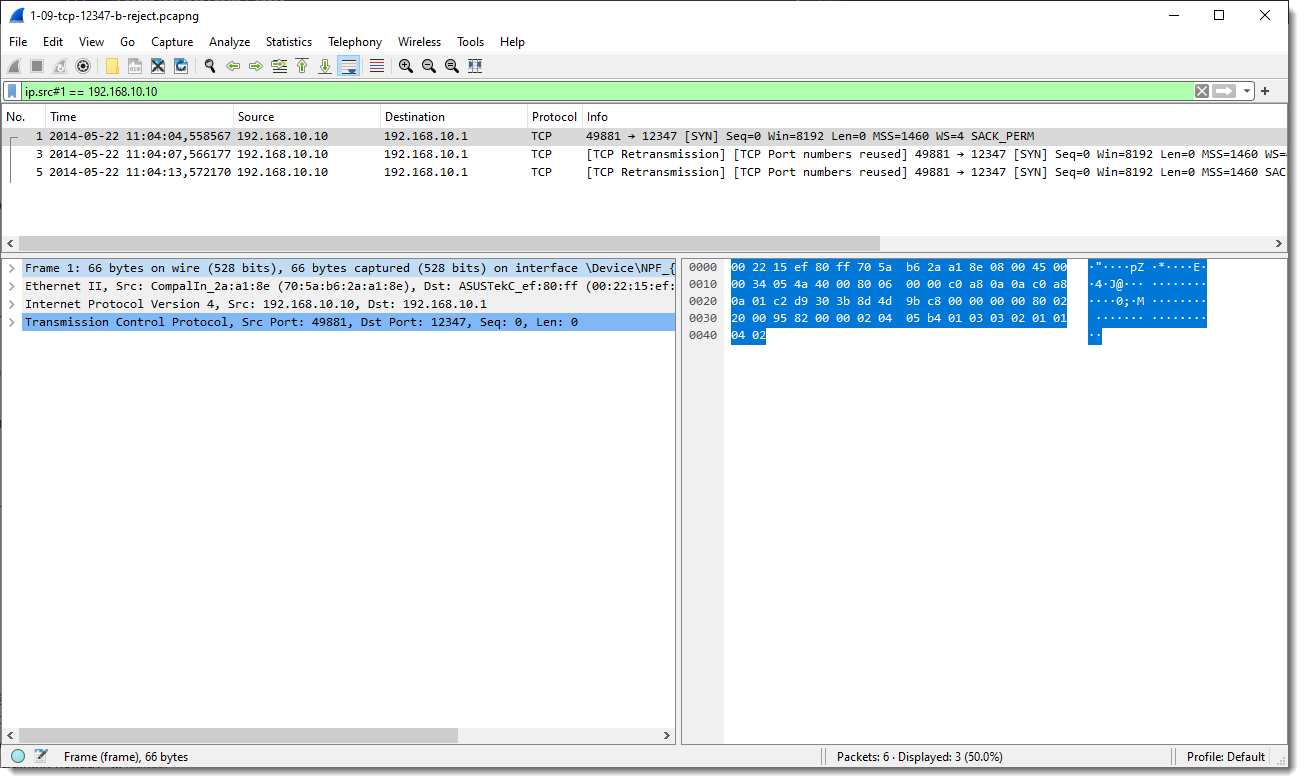
Display filter "ip.src#1 == 192.168.10.10" filters out all IP packets on the first layer that match ip.src == 192.168.10.10.
So that means that only the TCP SYN packets are displayed:
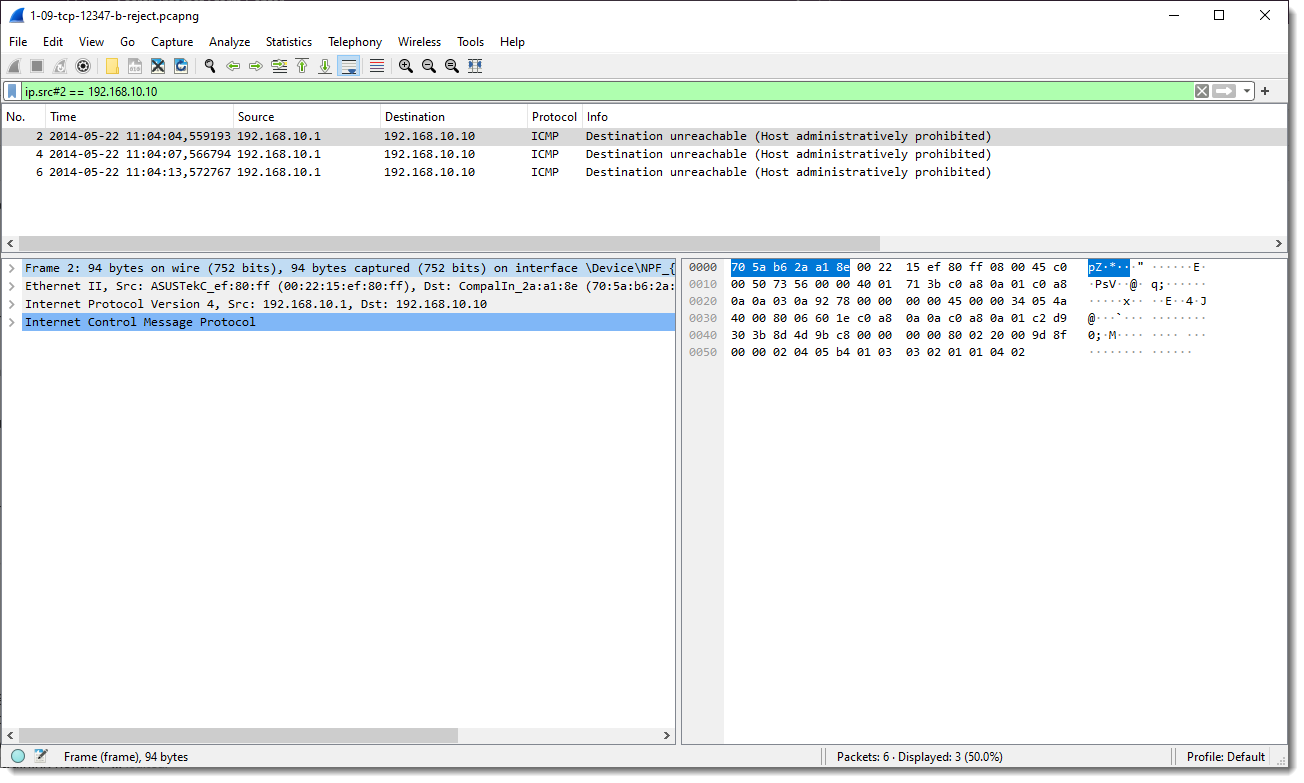
Display filter "ip.src#2 == 192.168.10.10" filters out all IP packets on the second layer that match ip.src == 192.168.10.10.
So that means that only the ICMP packets are displayed:
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com


Comments