Case Study: Cobalt Strike Server Lives on After Its Domain Is Suspended
Introduction
How do threat actors behind a Cobalt Strike server keep it running after its domain is taken down? If the server is not hosted through the domain registrar, it merely keeps running on the same IP address.
Today's diary is a case study where Cobalt Strike remained active on the same IP address at least one week after its domain was suspended.
Traffic Forensics
On Tuesday 2022-06-28, I generated a Qakbot infection in my lab and saw Cobalt Strike HTTPS traffic on 147.78.47[.]223 over TCP port 443 as shown below.
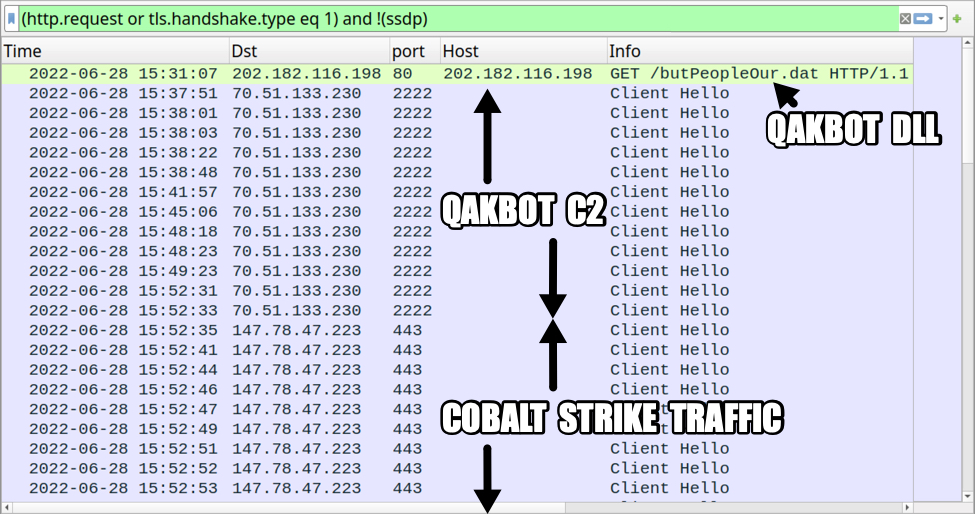
Shown above: Traffic from a Qakbot infection with Cobalt Strike on Tuesday 2022-06-28 filtered in Wireshark.
Examining the certificate in Wireshark reveals it's a Let's Encrypt certificate for moros[.]icu. Let's Encrypt is a legitimate free, automated, and open certificate authority (CA). While used by many valid websites, this service is commonly abused by threat actors, including those behind malicious Cobalt Strike activity.
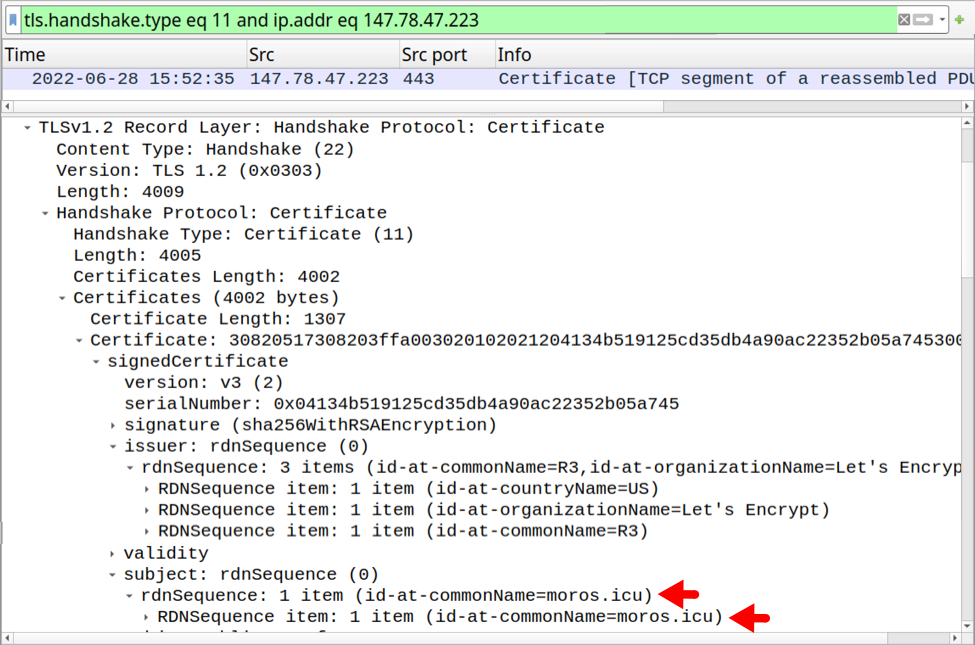
Shown above: Reviewing certificate issuer data associated with Cobalt Strike traffic on 147.78.47[.]223 in Wireshark.
Investigating the Malicious Server
Viewing the certificate from 147.78.47[.]223 in a web browser reveals it was originally issued for moros[.]icu through Let's Encrypt on 2022-06-20 and is no longer valid for that IP.
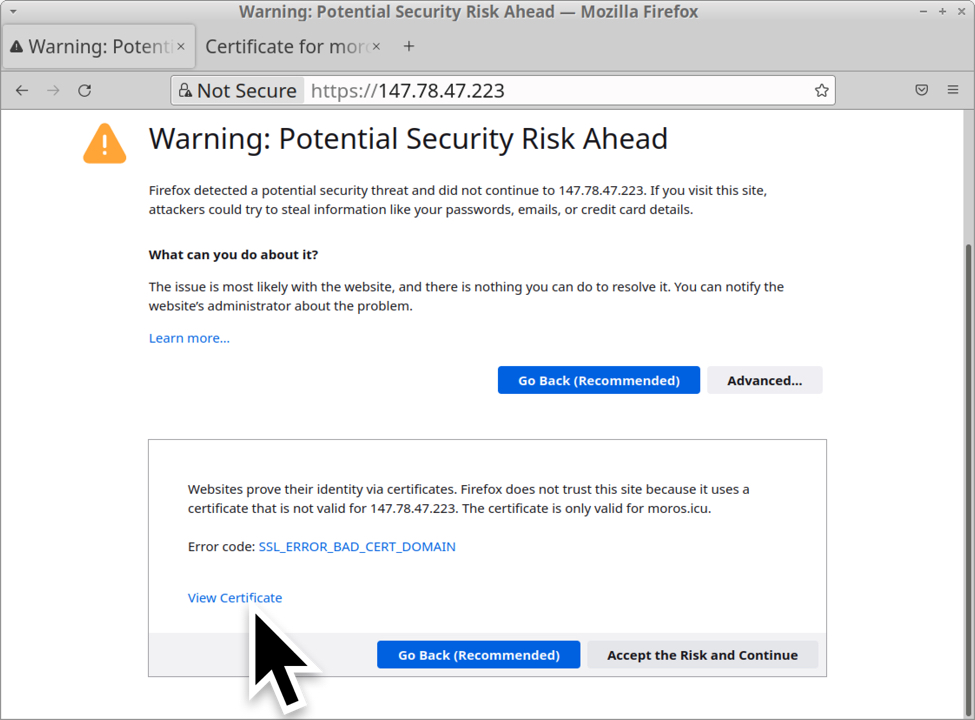
Shown above: Connecting to the Cobalt Strike server using a web browser.
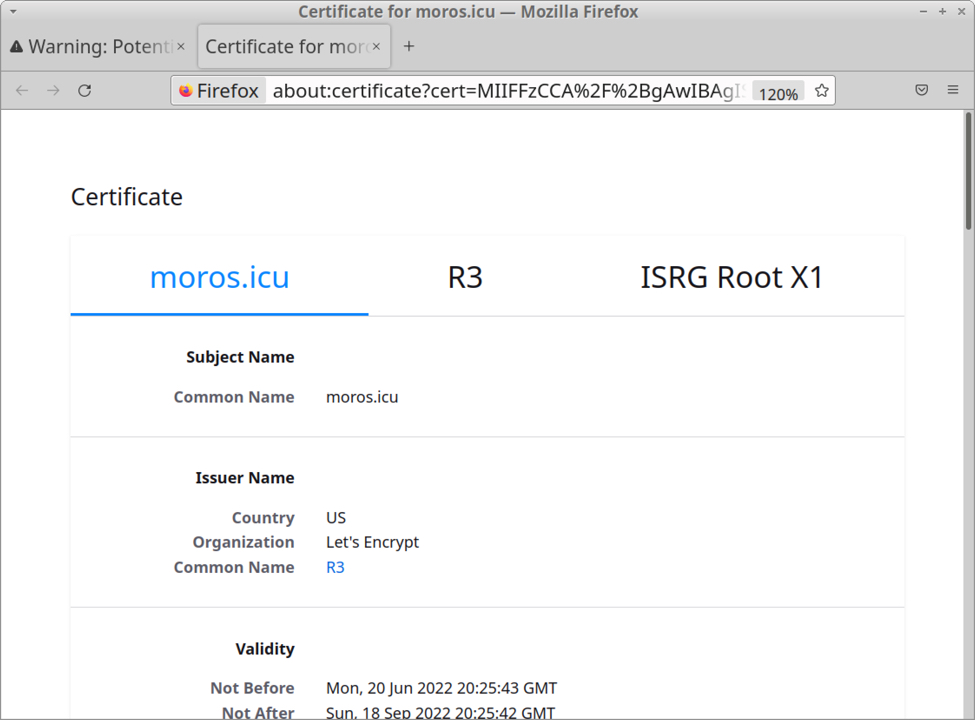
Shown above: Certificate data for moros[.]icu shown in a web browser.
The domain moros[.]icu was reported and suspended less than one day after it was registered through Namecheap, but its server was set up through a legitimate hosting provider at Flyservers. Kudos to @ian_kenefick and Namecheap for quickly taking action and suspending this malicious domain!
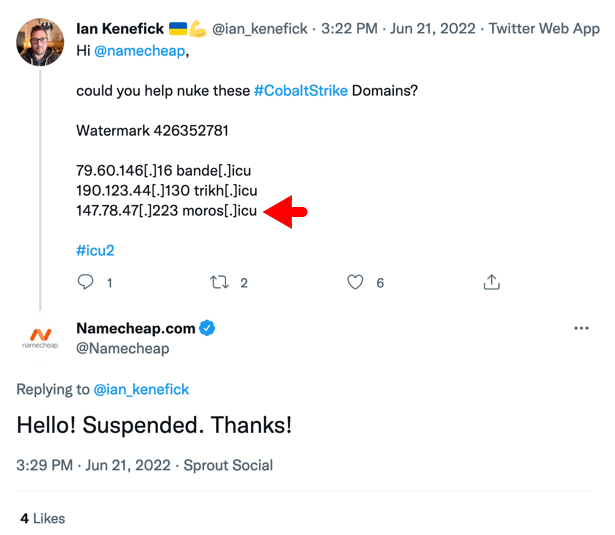
Shown above: Tweets showing moros[.]icu was suspended on 2022-06-21.
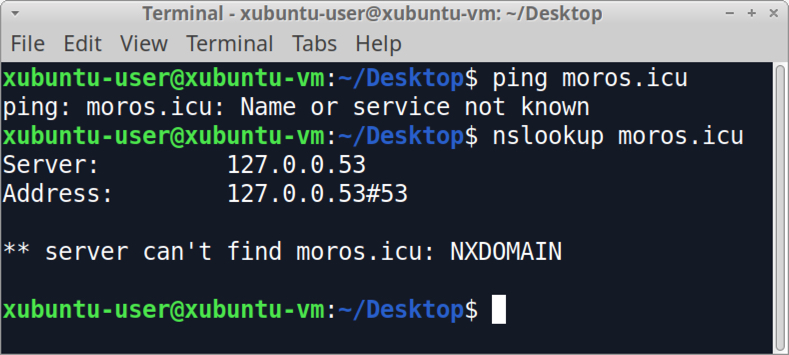
Shown above: My own confirmation that moros[.]icu no longer works.
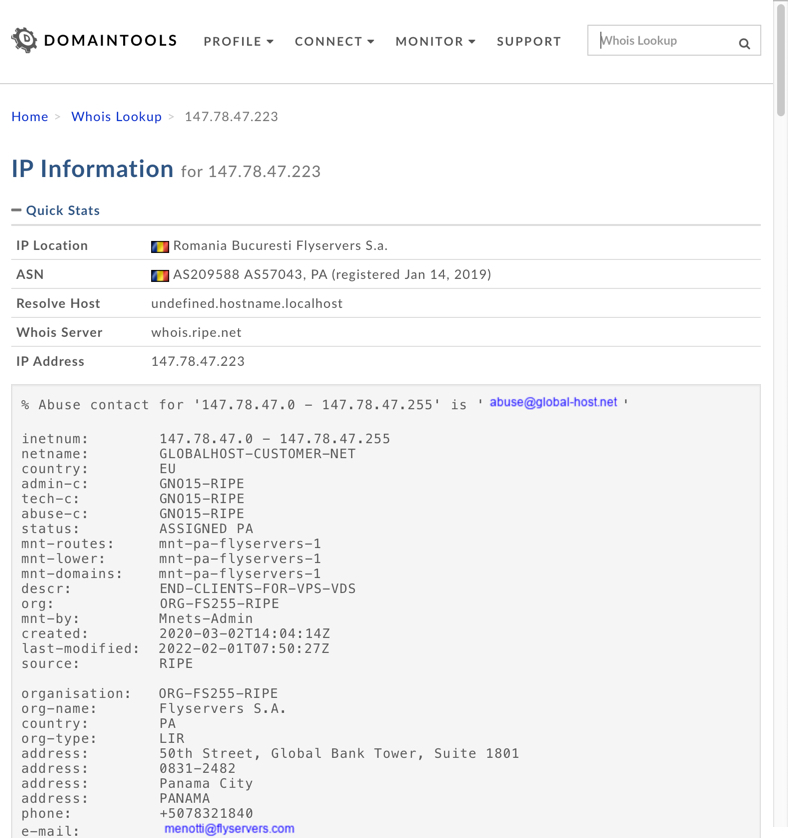
Shown above: Whois lookup for 147.78.47[.]223 using whois.domaintools.com.
The certificate's validity did not matter for Cobalt Strike activity I found on Tuesday 2022-06-28. Since the traffic was generated by malware instead of a web browser, HTTPS still worked.
Flyservers has been a hosting provider since 2001, and it appears to be a legitimate company. I've emailed their abuse address to report the malicious server on 147.78.47[.]223.
Final Words
Threat actors continually abuse legitimate hosting providers and certificate authorities (CAs), presumably through fraudulent accounts. Both free and paid services are incredibly susceptible to criminal abuse. Even Cobalt Strike is a legitimate red team tool commonly abused by various threat actors.
Security professionals can quickly report abuse cases, and service providers can rapidly shut down individual violations. However, threat actors can easily recover, and malware-related servers will continue to be an issue for defenders everywhere.
This case study reveals how criminal activity can circumvent domain takedowns. It also illustrates how time-intensive the associated investigation and corrective actions can be.
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments