Look Alike Accounts Used in Ukraine Donation Scam impersonating Olena Zelenska
Earlier, I saw the following account being flagged on Twitter:
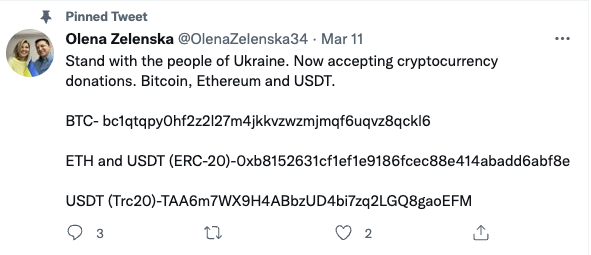
The account attempts to impersonate Olena Zelenska, the first lady of Ukraine. Mrs. Zelenska has a legitimate, private account (https://twitter.com/OlenaZelenska34). So what is the difference between:
https://twitter.com/OlenaZelenska34 and
https://twitter.com/OlenaZeIenska34 ?
If you look closely: The fake account uses an upper case I (I) instead of the lower case L (l). The characters are visually identical. So no fancy Unicode is required for this. Luckily, at least the bitcoin address has not yet received any funds. I flagged the fake account, but it appears to be still available so far.
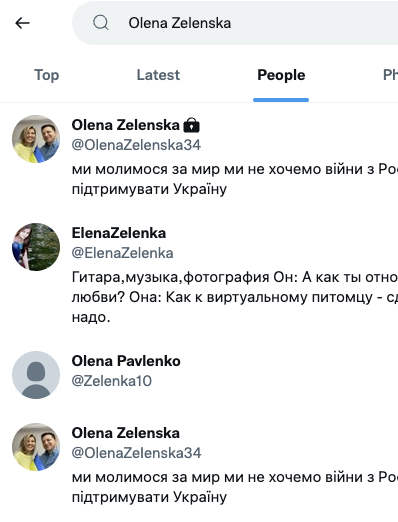
Like the email scam we saw earlier, cryptocurrency donations have been popular even for legitimate causes in this war. Be very careful. For Twitter: Even legitimate and verified accounts have been taken over in the past. You need to be a bit like an excellent old journalist and only trust information that you receive from different independent and trusted sources. It took me a moment to figure out which one was fake in the above example. There are plenty of other look-alike accounts. Some appear to be from people who have similar names. Others consider themselves "Fan Accounts" and clearly state that they are not affiliated with the actual person. The fake account currently shows as #4 if you search for "Olena Zelenska" on Twitter.
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
Apple Updates Everything: MacOS 12.3, XCode 13.3, tvOS 15.4, watchOS 8.5, iPadOS 15.4 and more
Apple today released one of its massive "surprise" updates for all of its operating systems. This includes updates for Safari as well as stand-alone security updates for older operating systems like macOS Big Sur and Catalina. As so often, this also includes feature updates for the respective operating systems.
It should be noted that Python 2 was removed from MacOS 12.3. This may still be needed by some third-party applications and you should check with the respective vendor for plans to update to Python 3. Python 2 support officially ended January 1st, 2020, but many applications still need it.
Kernel extensions used by Dropbox Desktop Application and Microsoft OneDrive have also been removed (however, these tools may still work).
And finally, PostScript files can no longer be viewed inline.
For more details, see Apple's security update page: https://support.apple.com/en-us/HT201222
and the developer release notes for macOS: https://developer.apple.com/documentation/macos-release-notes/macos-12_3-release-notes
[I may tweak the table below a bit more. But wanted to get this out to give some initial guidance. Feedback welcome. ]
| Catalina | BigSur | Monterey | tvOS | iOS/iPadOS | watchOS | ||
|---|---|---|---|---|---|---|---|
| CVE-2022-22631 [important] AppleGraphicsControl An out-of-bounds write issue was addressed with improved bounds checking. An application may be able to gain elevated privileges | |||||||
| x | x | x | |||||
| CVE-2022-22648 [important] AppleScript This issue was addressed with improved checks. An application may be able to read restricted memory | |||||||
| x | x | x | |||||
| CVE-2022-22627 [important] AppleScript An out-of-bounds read was addressed with improved bounds checking. Processing a maliciously crafted AppleScript binary may result in unexpected application termination or disclosure of process memory | |||||||
| x | x | x | |||||
| CVE-2022-22626 [important] AppleScript An out-of-bounds read was addressed with improved bounds checking. Processing a maliciously crafted AppleScript binary may result in unexpected application termination or disclosure of process memory | |||||||
| x | x | x | |||||
| CVE-2022-22625 [important] AppleScript An out-of-bounds read was addressed with improved input validation. Processing a maliciously crafted AppleScript binary may result in unexpected application termination or disclosure of process memory | |||||||
| x | x | x | |||||
| CVE-2022-22597 [critical] AppleScript A memory corruption issue was addressed with improved validation. Processing a maliciously crafted file may lead to arbitrary code execution | |||||||
| x | x | x | |||||
| CVE-2022-22616 [important] Safari Downloads This issue was addressed with improved checks. A maliciously crafted ZIP archive may bypass Gatekeeper checks | |||||||
| x | x | x | |||||
| CVE-2022-22661 [important] Intel Graphics Driver A type confusion issue was addressed with improved state handling. An application may be able to execute arbitrary code with kernel privileges | |||||||
| x | x | x | |||||
| CVE-2022-22613 [important] Kernel An out-of-bounds write issue was addressed with improved bounds checking. An application may be able to execute arbitrary code with kernel privileges | |||||||
| x | x | x | x | x | x | ||
| CVE-2022-22615 [important] Kernel A use after free issue was addressed with improved memory management. An application may be able to execute arbitrary code with kernel privileges | |||||||
| x | x | x | x | x | x | ||
| CVE-2022-22614 [important] Kernel A use after free issue was addressed with improved memory management. An application may be able to execute arbitrary code with kernel privileges | |||||||
| x | x | x | x | x | x | ||
| CVE-2022-22638 [important] Kernel A null pointer dereference was addressed with improved validation. An attacker in a privileged position may be able to perform a denial of service attack | |||||||
| x | x | x | x | x | x | ||
| CVE-2022-22647 [critical] Login Window This issue was addressed with improved checks. A person with access to a Mac may be able to bypass Login Window | |||||||
| x | x | x | |||||
| CVE-2022-22656 [other] LoginWindow An authentication issue was addressed with improved state management. A local attacker may be able to view the previous logged in user?s desktop from the fast user switching screen | |||||||
| x | x | x | |||||
| CVE-2022-22617 [important] PackageKit A logic issue was addressed with improved state management. An application may be able to gain elevated privileges | |||||||
| x | x | x | |||||
| CVE-2022-22650 [important] QuickTime Player This issue was addressed with improved checks. A plug-in may be able to inherit the application's permissions and access user data | |||||||
| x | x | x | |||||
| WebKit Bugzilla [important] WebKit A logic issue was addressed with improved state management. A malicious website may cause unexpected cross-origin behavior | |||||||
| x | x | x | x | x | x | ||
| CVE-2022-22582 [important] xar A validation issue existed in the handling of symlinks. This issue was addressed with improved validation of symlinks. A local user may be able to write arbitrary files | |||||||
| x | x | x | |||||
| CVE-2022-22633 [critical] Accelerate Framework A memory corruption issue was addressed with improved state management. Opening a maliciously crafted PDF file may lead to an unexpected application termination or arbitrary code execution | |||||||
| x | x | x | x | ||||
| CVE-2022-22632 [important] Kernel A logic issue was addressed with improved state management. A malicious application may be able to elevate privileges | |||||||
| x | x | x | x | x | |||
| CVE-2022-22599 [other] Siri A person with physical access to a device may be able to use Siri to obtain some location information from the lock screen | |||||||
| x | x | x | x | ||||
| CVE-2022-22669 [important] AMD A use after free issue was addressed with improved memory management. An application may be able to execute arbitrary code with kernel privileges | |||||||
| x | |||||||
| CVE-2022-22665 [important] AppKit A logic issue was addressed with improved validation. A malicious application may be able to gain root privileges | |||||||
| x | |||||||
| CVE-2021-22946 [other] curl Multiple issues were addressed by updating to curl version 7.79.1. Multiple issues in curl | |||||||
| x | |||||||
| CVE-2021-22947 [other] curl Multiple issues were addressed by updating to curl version 7.79.1. Multiple issues in curl | |||||||
| x | |||||||
| CVE-2021-22945 [other] curl Multiple issues were addressed by updating to curl version 7.79.1. Multiple issues in curl | |||||||
| x | |||||||
| CVE-2022-22623 [other] curl Multiple issues were addressed by updating to curl version 7.79.1. Multiple issues in curl | |||||||
| x | |||||||
| CVE-2022-22643 [important] FaceTime This issue was addressed with improved checks. A user may send audio and video in a FaceTime call without knowing that they have done so | |||||||
| x | x | ||||||
| CVE-2022-22611 [critical] ImageIO An out-of-bounds read was addressed with improved input validation. Processing a maliciously crafted image may lead to arbitrary code execution | |||||||
| x | x | x | x | ||||
| CVE-2022-22612 [critical] ImageIO A memory consumption issue was addressed with improved memory handling. Processing a maliciously crafted image may lead to heap corruption | |||||||
| x | x | x | x | ||||
| CVE-2022-22641 [important] IOGPUFamily A use after free issue was addressed with improved memory management. An application may be able to gain elevated privileges | |||||||
| x | x | x | |||||
| CVE-2022-22640 [important] Kernel A memory corruption issue was addressed with improved validation. An application may be able to execute arbitrary code with kernel privileges | |||||||
| x | x | x | x | ||||
| CVE-2021-36976 [other] libarchive Multiple memory corruption issues existed in libarchive. These issues were addressed with improved input validation. Multiple issues in libarchive | |||||||
| x | x | x | |||||
| CVE-2022-22657 [other] GarageBand MIDI A memory initialization issue was addressed with improved memory handling. Opening a maliciously crafted file may lead to unexpected application termination or arbitrary code execution | |||||||
| x | |||||||
| CVE-2022-22664 [other] GarageBand MIDI An out-of-bounds read was addressed with improved bounds checking. Opening a maliciously crafted file may lead to unexpected application termination or arbitrary code execution | |||||||
| x | |||||||
| CVE-2022-22644 [other] NSSpellChecker A privacy issue existed in the handling of Contact cards. This was addressed with improved state management. A malicious application may be able to access information about a user's contacts | |||||||
| x | |||||||
| CVE-2022-22609 [other] Preferences The issue was addressed with additional permissions checks. A malicious application may be able to read other applications' settings | |||||||
| x | x | x | x | ||||
| CVE-2022-22600 [other] Sandbox The issue was addressed with improved permissions logic. A malicious application may be able to bypass certain Privacy preferences | |||||||
| x | x | x | x | ||||
| CVE-2022-22651 [other] SMB An out-of-bounds write issue was addressed with improved bounds checking. A remote attacker may be able to cause unexpected system termination or corrupt kernel memory | |||||||
| x | |||||||
| CVE-2022-22639 [important] SoftwareUpdate A logic issue was addressed with improved state management. An application may be able to gain elevated privileges | |||||||
| x | x | ||||||
| CVE-2022-22660 [other] System Preferences This issue was addressed with a new entitlement. An app may be able to spoof system notifications and UI | |||||||
| x | |||||||
| CVE-2022-22621 [other] UIKit This issue was addressed with improved checks. A person with physical access to an iOS device may be able to see sensitive information via keyboard suggestions | |||||||
| x | x | x | x | ||||
| CVE-2021-4136 [other] Vim Multiple issues were addressed by updating Vim. Multiple issues in Vim | |||||||
| x | |||||||
| CVE-2021-4166 [other] Vim Multiple issues were addressed by updating Vim. Multiple issues in Vim | |||||||
| x | |||||||
| CVE-2021-4173 [other] Vim Multiple issues were addressed by updating Vim. Multiple issues in Vim | |||||||
| x | |||||||
| CVE-2021-4187 [other] Vim Multiple issues were addressed by updating Vim. Multiple issues in Vim | |||||||
| x | |||||||
| CVE-2021-4192 [other] Vim Multiple issues were addressed by updating Vim. Multiple issues in Vim | |||||||
| x | |||||||
| CVE-2021-4193 [other] Vim Multiple issues were addressed by updating Vim. Multiple issues in Vim | |||||||
| x | |||||||
| CVE-2021-46059 [other] Vim Multiple issues were addressed by updating Vim. Multiple issues in Vim | |||||||
| x | |||||||
| CVE-2022-0128 [other] Vim Multiple issues were addressed by updating Vim. Multiple issues in Vim | |||||||
| x | |||||||
| CVE-2022-0156 [other] Vim Multiple issues were addressed by updating Vim. Multiple issues in Vim | |||||||
| x | |||||||
| CVE-2022-0158 [other] Vim Multiple issues were addressed by updating Vim. Multiple issues in Vim | |||||||
| x | |||||||
| CVE-2021-30918 [other] VoiceOver A lock screen issue was addressed with improved state management. A user may be able to view restricted content from the lock screen | |||||||
| x | |||||||
| CVE-2022-22668 [important] Wi-Fi A logic issue was addressed with improved restrictions. A malicious application may be able to leak sensitive user information | |||||||
| x | x | ||||||
| CVE-2022-22666 [critical] AppleAVD A memory corruption issue was addressed with improved validation. Processing a maliciously crafted image may lead to heap corruption | |||||||
| x | x | x | |||||
| CVE-2022-22634 [important] AVEVideoEncoder A buffer overflow was addressed with improved bounds checking. A malicious application may be able to execute arbitrary code with kernel privileges | |||||||
| x | x | ||||||
| CVE-2022-22635 [important] AVEVideoEncoder An out-of-bounds write issue was addressed with improved bounds checking. An application may be able to gain elevated privileges | |||||||
| x | x | ||||||
| CVE-2022-22636 [important] AVEVideoEncoder An out-of-bounds write issue was addressed with improved bounds checking. An application may be able to execute arbitrary code with kernel privileges | |||||||
| x | x | ||||||
| CVE-2022-22670 [other] MediaRemote An access issue was addressed with improved access restrictions. A malicious application may be able to identify what other applications a user has installed | |||||||
| x | x | x | |||||
| CVE-2022-22596 [important] Kernel A memory corruption issue was addressed with improved validation. An application may be able to execute arbitrary code with kernel privileges | |||||||
| x | x | ||||||
| CVE-2022-22618 [other] Phone This issue was addressed with improved checks. A user may be able to bypass the Emergency SOS passcode prompt | |||||||
| x | x | ||||||
| CVE-2022-22654 [other] Safari A user interface issue was addressed. Visiting a malicious website may lead to address bar spoofing | |||||||
| x | |||||||
| WebKit Bugzilla 233172
CVE-2022-22624 [critical] WebKit A use after free issue was addressed with improved memory management. Processing maliciously crafted web content may lead to arbitrary code execution | |||||||
| x | |||||||
| CVE-2022-22652 [other] Cellular The GSMA authentication panel could be presented on the lock screen. The issue was resolved by requiring device unlock to interact with the GSMA authentication panel. A person with physical access may be able to view and modify the carrier account information and settings from the lock screen | |||||||
| x | |||||||
| CVE-2022-22598 [other] CoreMedia An issue with app access to camera metadata was addressed with improved logic. An app may be able to learn information about the current camera view before being granted camera access | |||||||
| x | |||||||
| CVE-2022-22642 [other] FaceTime This issue was addressed with improved checks. A user may be able to bypass the Emergency SOS passcode prompt | |||||||
| x | |||||||
| CVE-2022-22667 [important] GPU Drivers A use after free issue was addressed with improved memory management. An application may be able to execute arbitrary code with kernel privileges | |||||||
| x | |||||||
| CVE-2022-22653 [important] iTunes A logic issue was addressed with improved restrictions. A malicious website may be able to access information about the user and their devices | |||||||
| x | |||||||
| CVE-2022-22622 [other] Markup This issue was addressed with improved checks. A person with physical access to an iOS device may be able to see sensitive information via keyboard suggestions | |||||||
| x | |||||||
| CVE-2022-22659 [important] NetworkExtension A logic issue was addressed with improved state management. An attacker in a privileged network position may be able to leak sensitive user information | |||||||
| x | |||||||
| CVE-2022-22671 [important] VoiceOver An authentication issue was addressed with improved state management. A person with physical access to an iOS device may be able to access photos from the lock screen | |||||||
| x | |||||||
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
Curl on Windows
It's about 2 years ago that Xavier wrote a diary entry ("Keep an Eye on Command-Line Browsers") mentioning that curl was now build into Windows.
And since then, we see the occasional malicious script using curl to communicate. Like the one analysed in diary entry "Infostealer in a Batch File".
I sometimes hunt for curl generated traffic (in proxy logs for example) by searching for curl's User Agent String: curl/<version-number>.
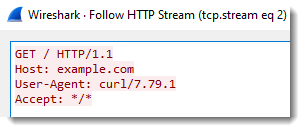
The user agent string does not tell you what operating system it is. So you have to distinguish curl requests from Linux machines and Windows machines with other info, like asset information, or TLS fingerprinting (if HTTPS is used), or looking at other traffic from the same IP, ...
And of course, curl can be configured with another User Agent String, using option -A (--user-agent).
But that is not the case in the BAT file that Xavier analysed. The malicious author uses -H options to add JSON headers, but not to change the user agent string:
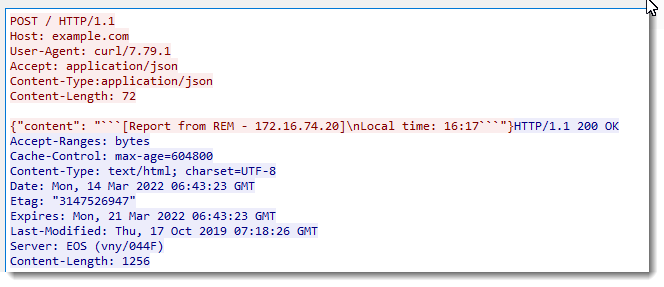
So with this particular malicious script, it's rather easy to detect (especially if you are in a network environment without Linux machines): search for curl UAS.
If you are in a corporate environment, there's something else to know about curl on Windows. Although curl has many proxy options, curl is not able to auto detect proxies. In other words, if you run curl on Windows in a network environment that requires the use of a proxy to access the Internet, curl will not communicate with said proxy, unless it is configured explicitly to use a specific proxy (hostname, IP address, port, ...).
And that is the case with the malicious script Xavier wrote about: there are no proxy options in that script, so when curl is executed, it will issue a DNS request for discord[.]com, and if it gets a reply with an IP address, it will connect directly to that IP address.
Although the automatic detection of proxies has been on curl's TODO list for some years now, it is still not implemented. There have been PRs like this one, but it has not been merged into curl's code base.
This means that if an attacker wants to use curl in your corporate environment with proxies, the attacker needs to know the name/ip address of one proxy in your environment and configure that explicitly via curl's proxy options.
If your proxy requires authentitation, curl is capable to do this. Not only with explicit credentials, but also with single-sign-on. At least on Windows with SSPI.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com


Comments