Old TLS versions - gone, but not forgotten... well, not really "gone" either
With the recent official deprecation of TLS 1.0 and TLS 1.1 by RFC 8996[1], a step, which has long been in preparation and which was preceded by many recommendations to discontinue the use of both protocols (as well as by the removal of support for them from all mainstream web browsers[2]), one might assume that the use of old TLS versions on the internet would have significantly decreased over the last few months. This has however not been the case.
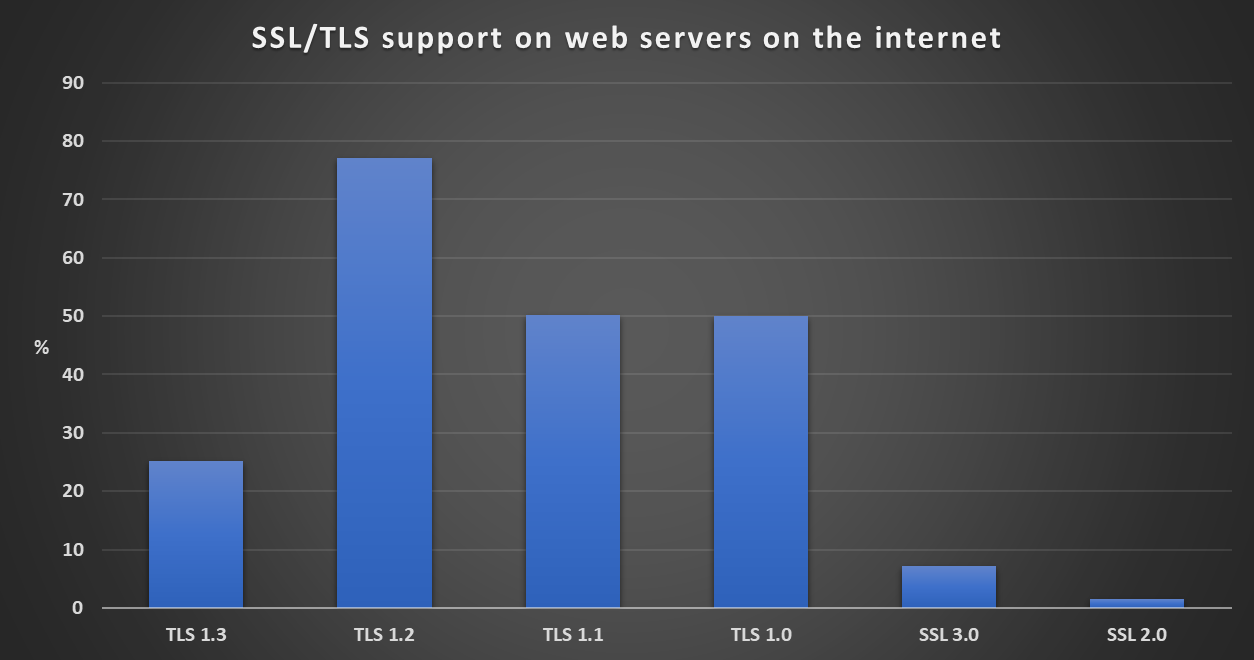
According to Shodan, at the time of writing, TLS 1.0 and TLS 1.1 are still supported by over 50% of web servers on the internet (50.15% and 50.08% respectively). We’ll leave aside the potentially much more problematic 7.2% of web servers that still support SSL 3.0 and 1.6% of servers that support SSL 2.0...
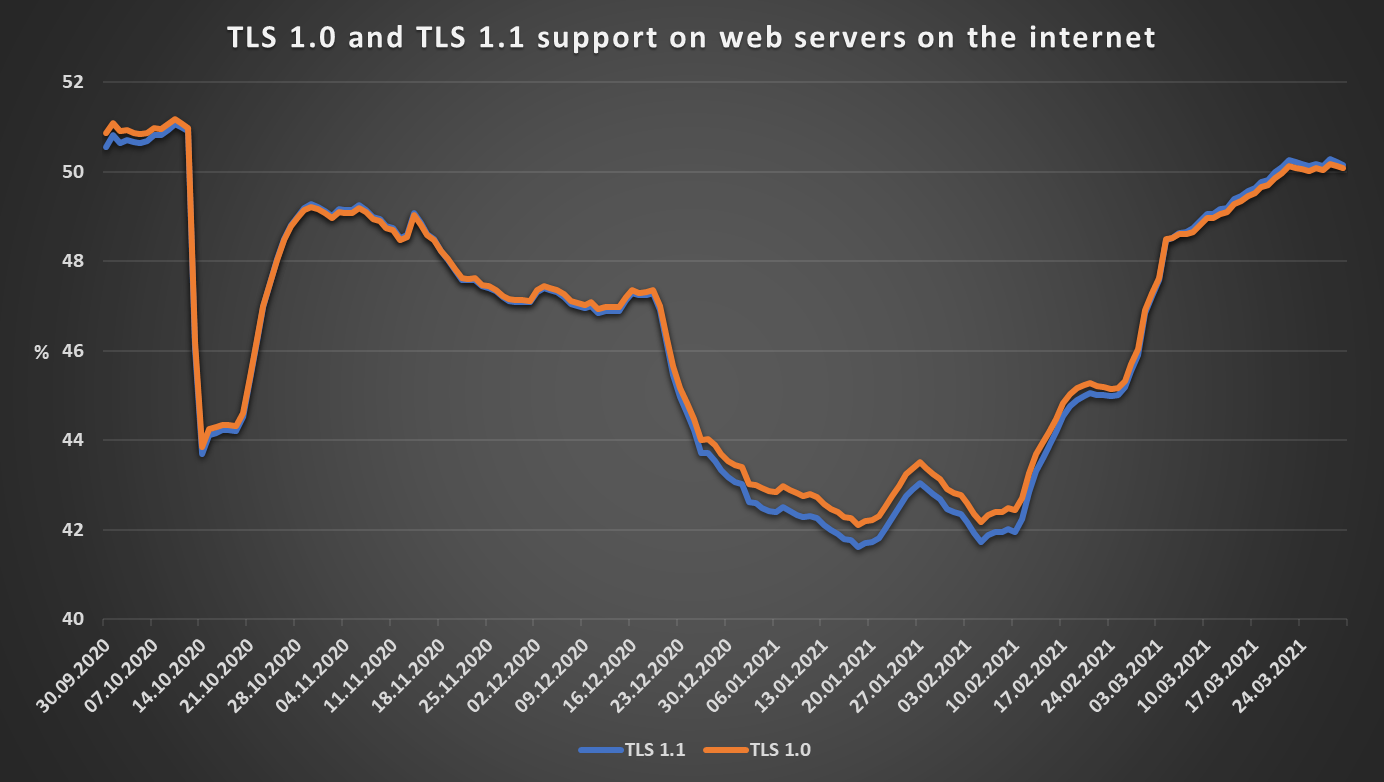
What is interesting about the percentages for TLS 1.0 and TLS 1.1 is that both are almost the same as they were six months ago. As the following chart shows, there appeared to be a fairly significant decrease in support of both protocols between the second half of October 2020 and the end of January 2021, which was however followed by a later sharp increase, after which the percentages plateaued at around the current values.
The still significant support for TLS 1.1 and TLS 1.0 is hardly too big a problem, since, although these protocols can’t be called “secure” by today’s standards, most browsers won’t use them unless specifically configured to do so. The fact that the percentage of publicly accessible web servers, which still support the historical TLS versions, didn’t decrease significantly in the last six months is, however, certainly noteworthy.
To end on a positive note, TLS 1.3 is now supported by over 25% of web servers (25.22% to be specific), as you may have noticed in the first chart. It seems that even if old TLS versions will not leave us any time soon, support for the new and secure version of the protocol is certainly slowly increasing[3].
[1] https://datatracker.ietf.org/doc/rfc8996/?include_text=1
[2] https://en.wikipedia.org/wiki/Transport_Layer_Security#TLS_1.0
[3] https://isc.sans.edu/forums/diary/TLS+13+is+now+supported+by+about+1+in+every+5+HTTPS+servers/26936/



Comments