Detecting Actors Activity with Threat Intel
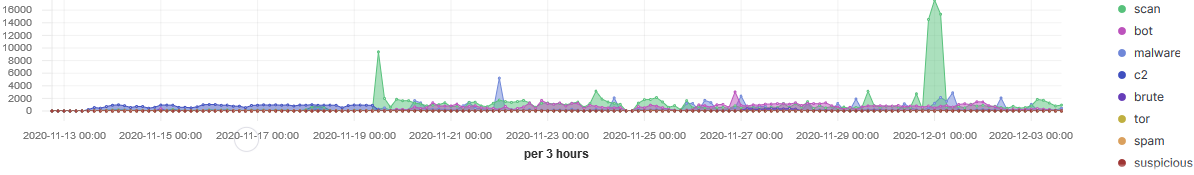
Over the past three weeks I have applied threat intel to all the inbound traffic going to my honeypot and the stats have shown some interesting trends. The top 20 TCP ports targeted have been between 1-50 and top 20 UDP 7-11211. During this period, the sensor recorded over 301K indicators matching threat intel from known actors.
A Look at the Top 3 IPs
The port the most targeted over that period has been the Telnet (TCP/23) service with over 97% of the traffic.
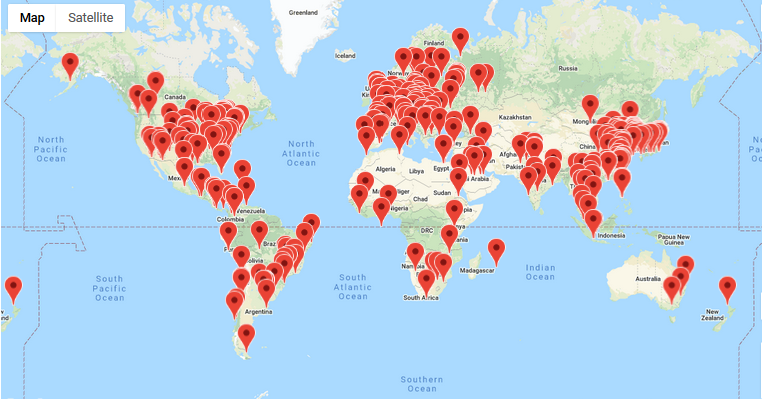
As a security practitioner, I have stopped using Telnet years ago (a honeypot being the exception). To find out how widespread Telnet is available, a query for this service on Shodan[4] shows there are still thousand of host showing this port as open and/or active. This map from Censys [8] illustrate a list of 2090422 hosts matched the search query where Telnet was open. Censys only shows the first 500 locations on the map.
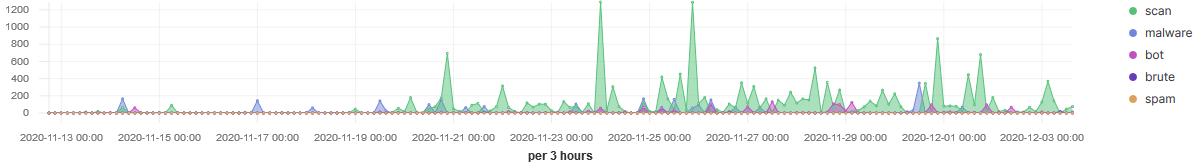
IP 207.244.234.226 launched a large scan on the 30 Nov (12:00-06:00) lasting for 6 hours actively scanning various TCP ports multiple times (46836 records). However, IP 88.214.24.77 has been a lot more consistent over time, scanning mostly TCP ports between 1000-1100 illustrated below:
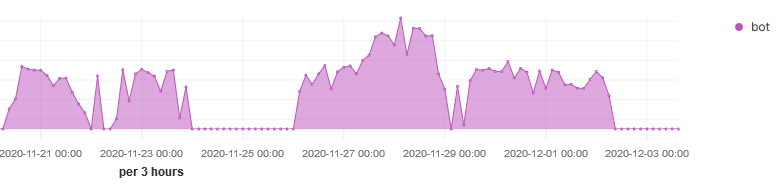
The third IP 5.182.210.95 has been scanning a single port over the past few and it is MemoryCache (UDP/11211). This source was first report in DShield on the 14 Nov 2020 with a last report today. The reports in DShield are mostly against LDAP (UDP/389) and only one record for 11211.
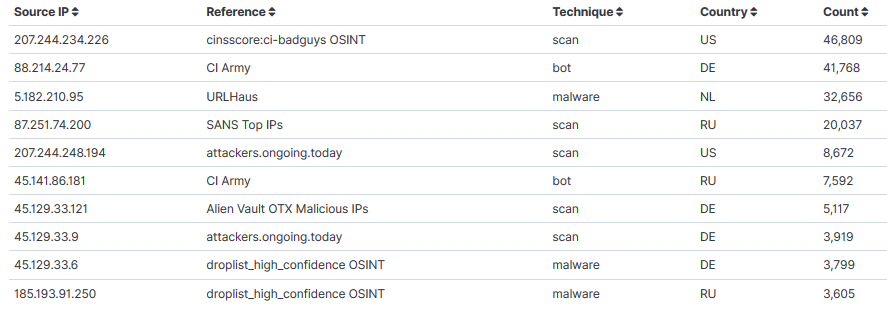
Last, this is the list of top 10 IPs with Intel source, techniques and total.
Two freely and widely available intel platform Anomali Staxx[1] after registration is available for download and installed locally (has API) and AlienVault[2] can be accessed via API and is widely supported.
[1] https://www.anomali.com/resources/staxx
[2] https://otx.alienvault.com/
[3] https://isc.sans.edu/port.html?port=23
[4] https://www.shodan.io/search?query=telnet
[5] https://isc.sans.edu/ipinfo.html?ip=207.244.234.226
[6] https://isc.sans.edu/ipinfo.html?ip=88.214.24.77
[7] https://isc.sans.edu/ipinfo.html?ip=5.182.210.95
[8] https://censys.io/ipv4/map?q=protocols%3A+("23%2Ftelnet")
-----------
Guy Bruneau IPSS Inc.
My Handler Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu


Comments