Couple of interesting Covid-19 related stats
It is nothing new that Covid-19 forced many organizations around the world to quickly adopt the “work from home” model, which in turn resulted in an increased number of machines offering remote access services and protocols accessible from the internet[1,2].
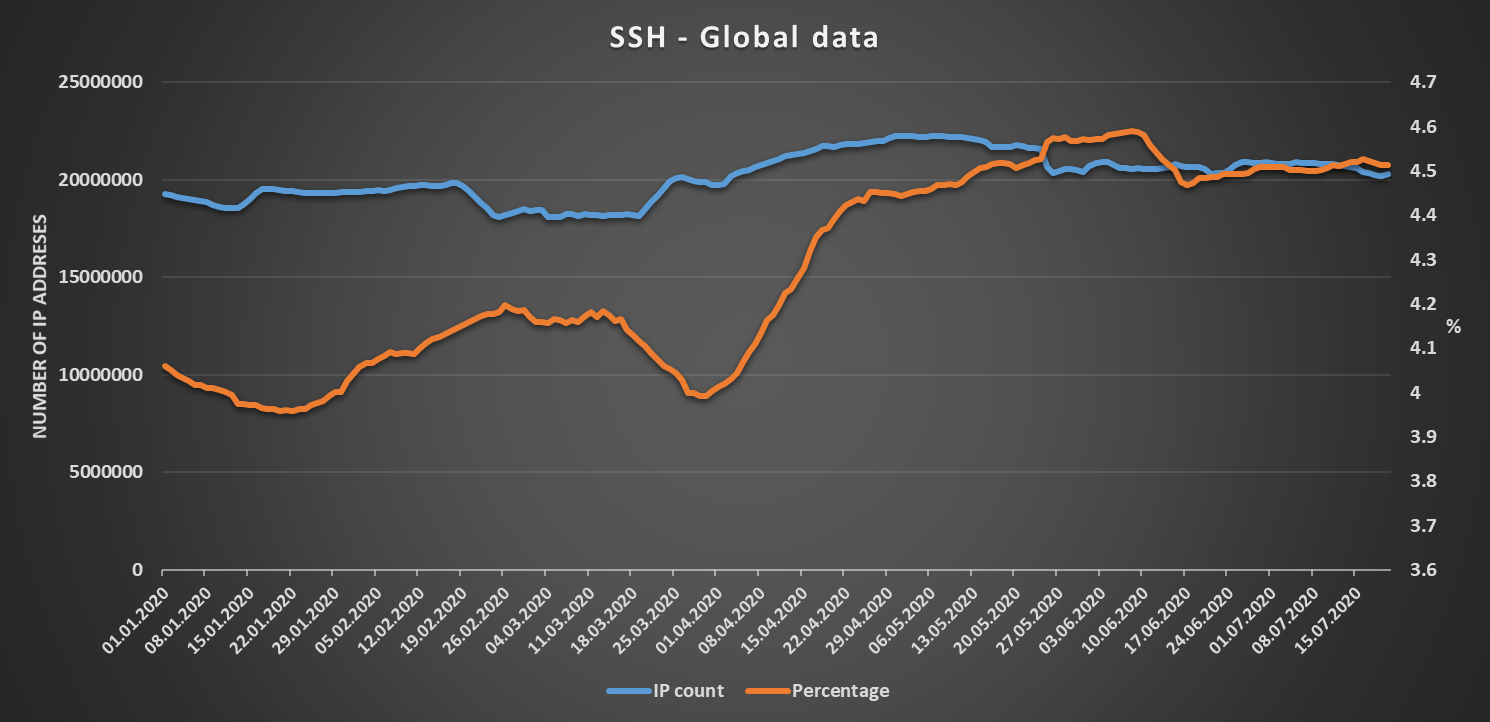
While this is true, going over data gathered from Shodan over this year I noticed that an interesting correlation exists in some cases between the number of machines with accessible protocols for remote access and regionally implemented restrictions on free movement. I call it “interesting” because although one might expect such a correlation to exist, one would probably expect it to always be strongly positive, i.e. that with increased restrictions on free movement would come a significant increase in the number of machines with SSH, Telnet, RDP, VNC, etc. accessible from the internet, followed by a significant decrease following lifting of the restrictions.
That is not always the case however and given the inherent risk associated with allowing unrestricted access to these services from an untrusted external network, I thought it might be interesting to take a short look at recent developments in the number of IPs exposing SSH, RDP and Telnet to the internet in couple of different countries.
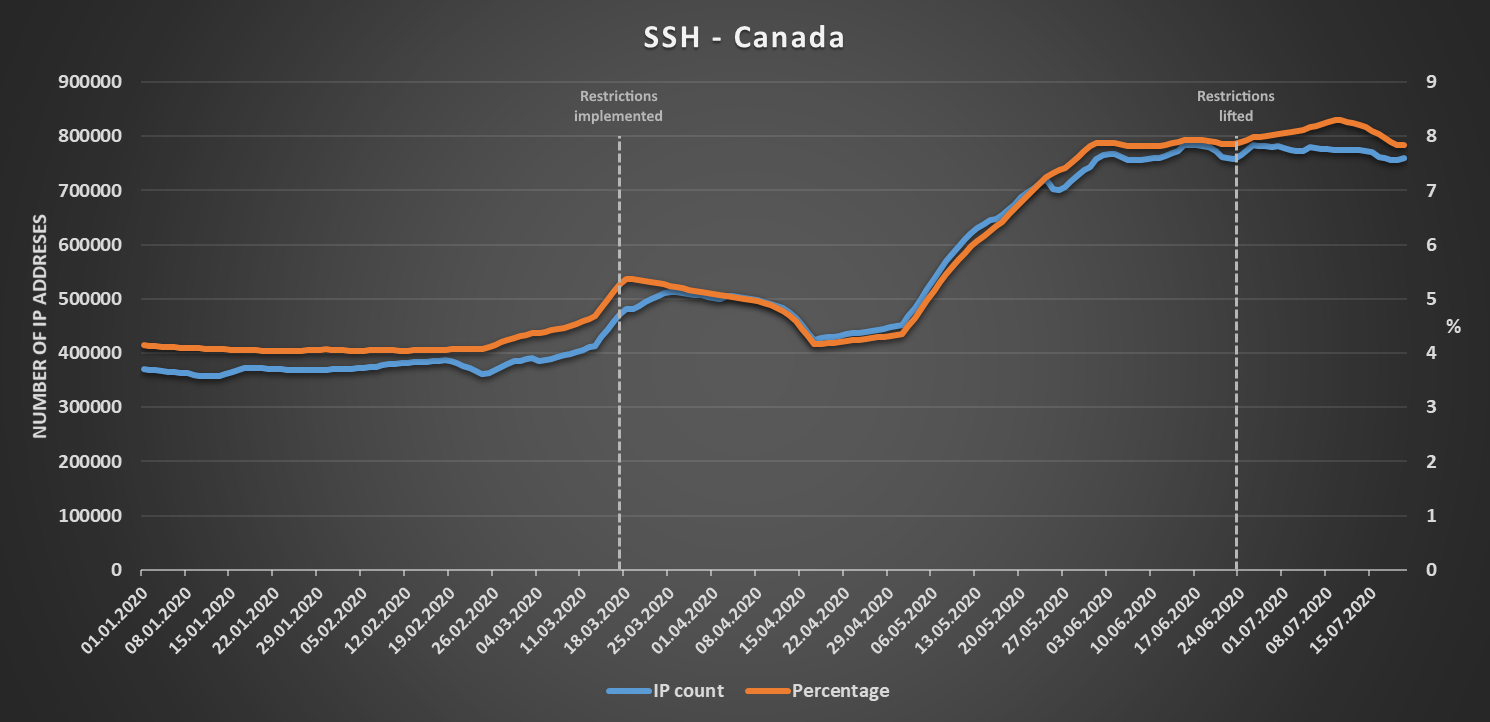
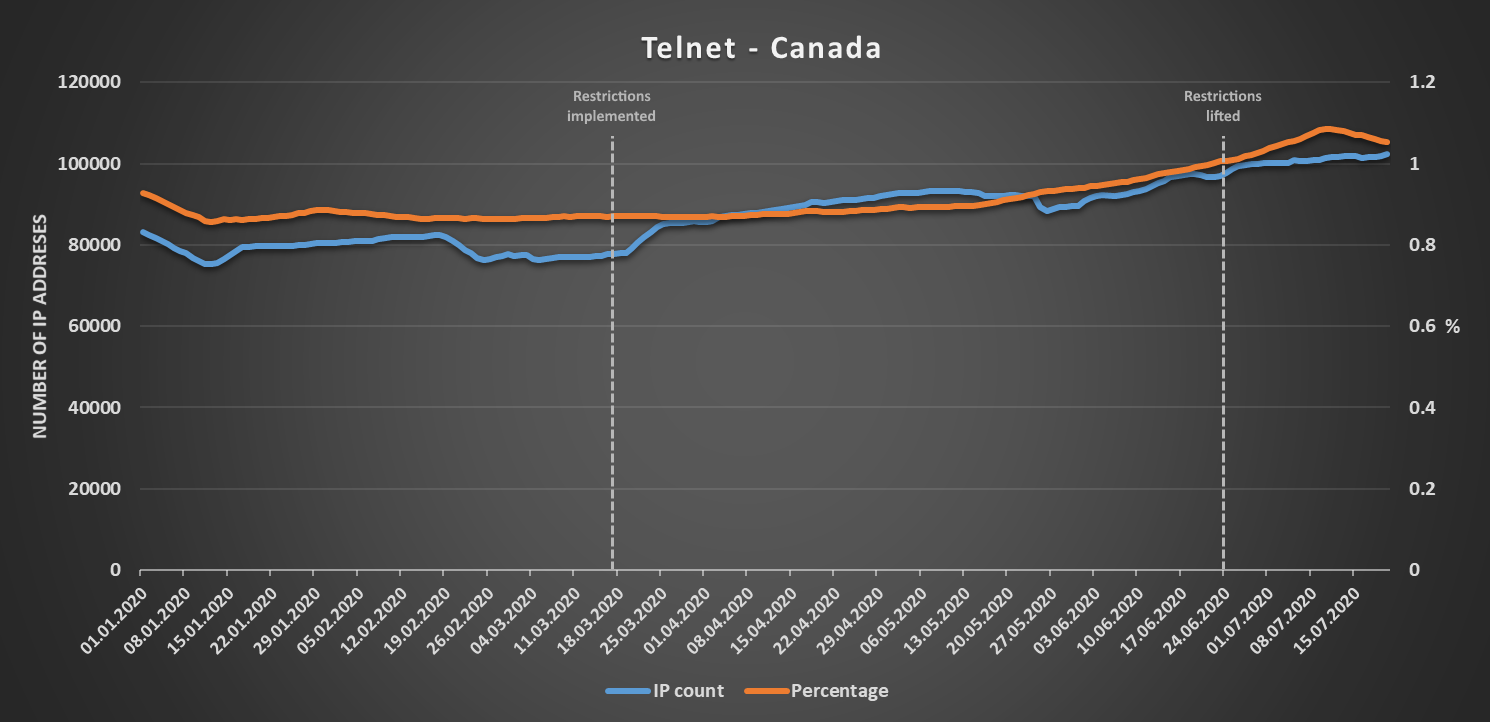
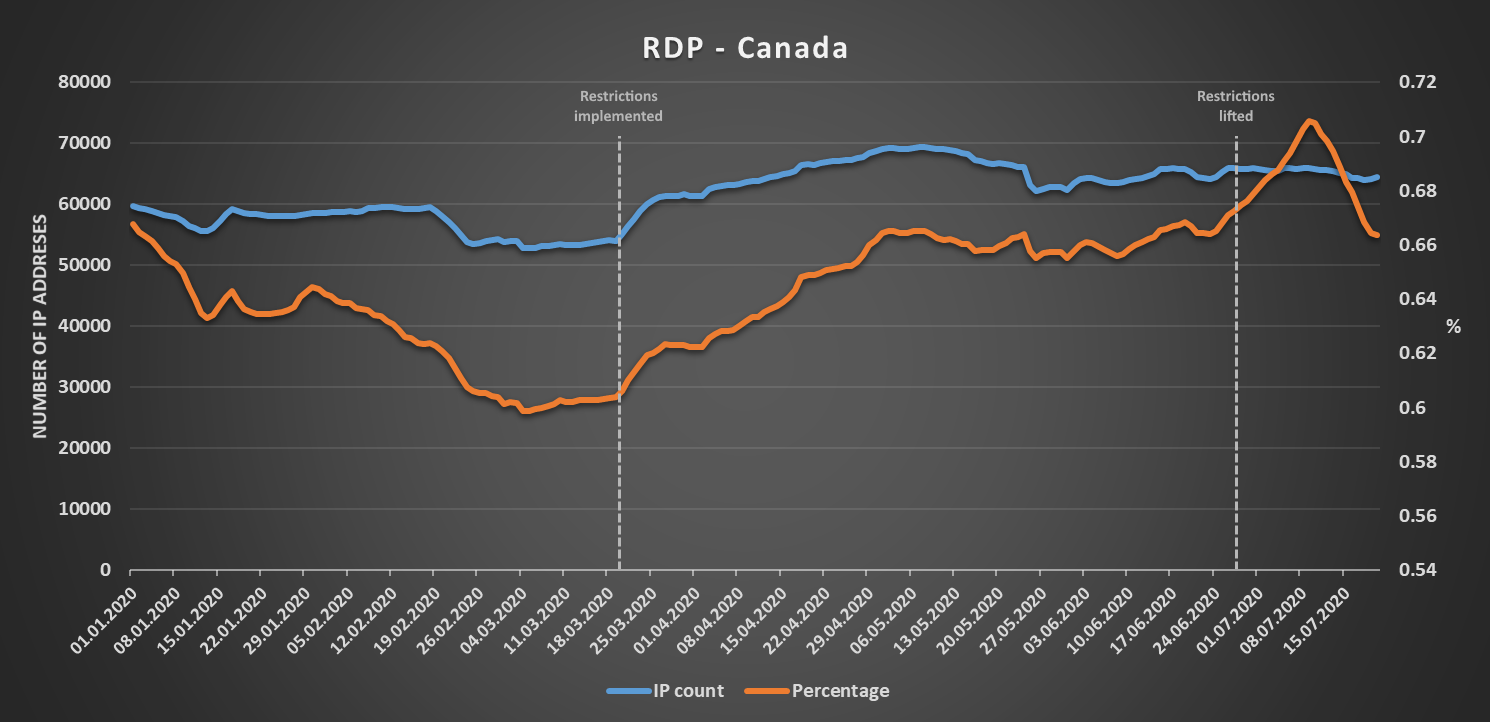
A good example of a country where the “expected” increase in numbers may be seen would be Canada. There, both the number of IP addresses and the corresponding percentage of IPs allocated to ISPs in the country both saw a significant increase between the time restrictions on free movement were implemented and the time they were lifted (a large thanks goes to my colleague @inarumlova for providing me with the relevant dates for almost 60 different countries). Since then, the numbers have stayed fairly high however, with only a small drop in the number of IPs with exposed RDP.
Things were a bit more interesting in Austria. There, the number of IPs exposing remote access protocols rose in the time frame when restrictions on free movement were in place (and, in the case of SSH, the numbers fell significantly for a while after the restrictions were lifted), while the percentage of Austrian IP space visible to Shodan, which those IPs represented, steadily decreased.
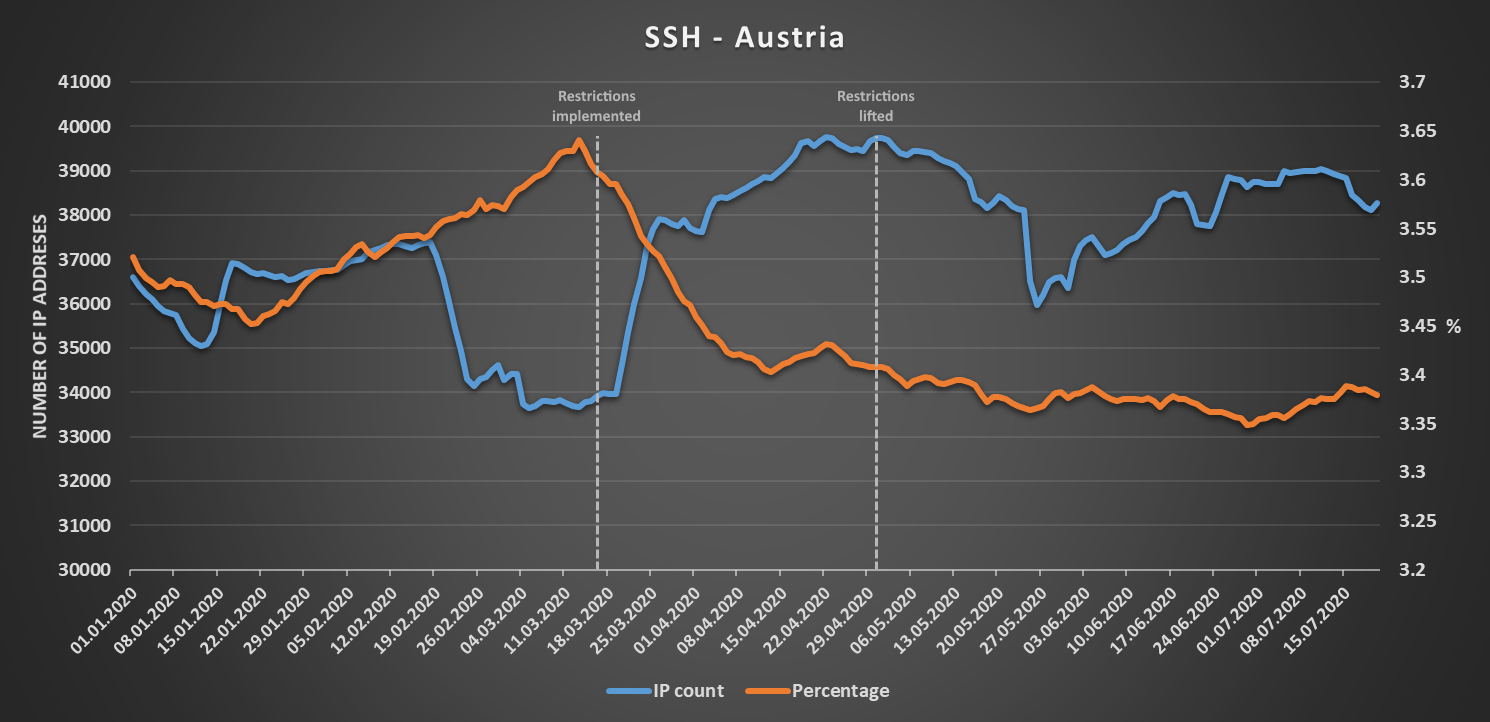
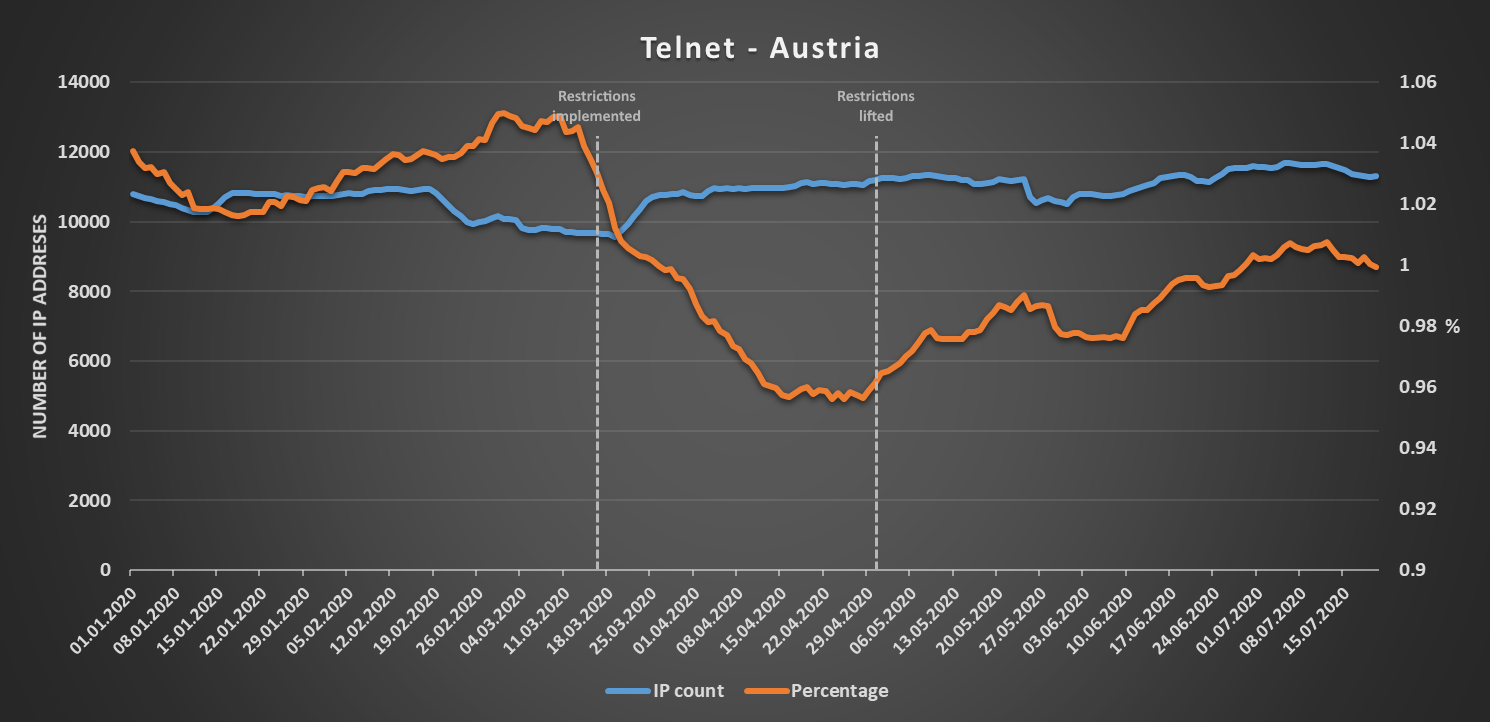
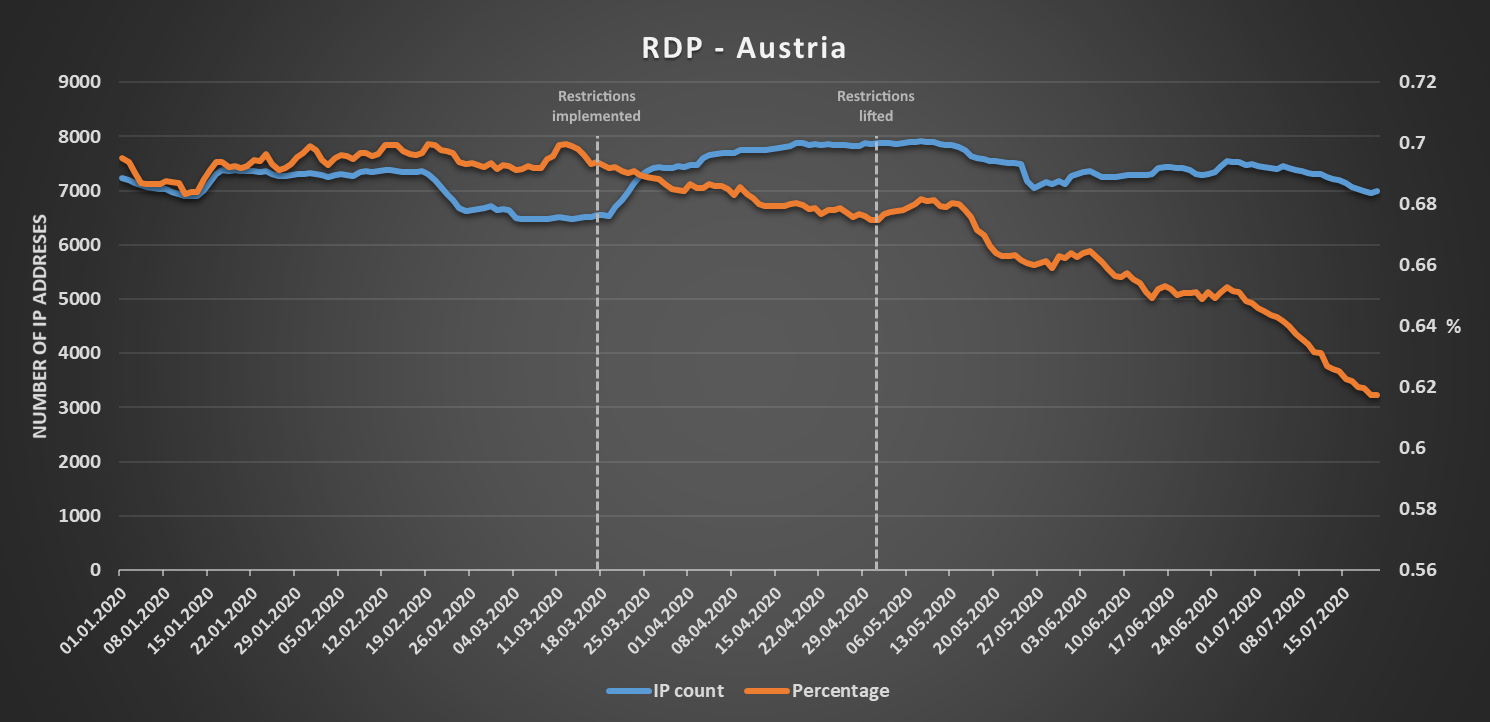
So far, the expectation of a significant increase in the number of IP addresses with exposed remote access protocols during any “lockdown” period held true.
A country where this expectation would prove to be wrong – at least in the case of RDP – would be the United States. This may be because most restrictions on free movement, which were put in place in the US, were enforced only on a regional or at most state level, or perhaps because organizations in the US chose to provide access to the protocols we’re interested in only through VPN connections. This is only a speculation, however. Whatever the reason, although we may see a steady increase for both SSH and Telnet since the beginning of March, the number of IP addresses with exposed RDP first fell significantly at the beginning of the year and then remained more or less constant with only couple of temporary increases visible in data following implementation of the first travel restrictions.
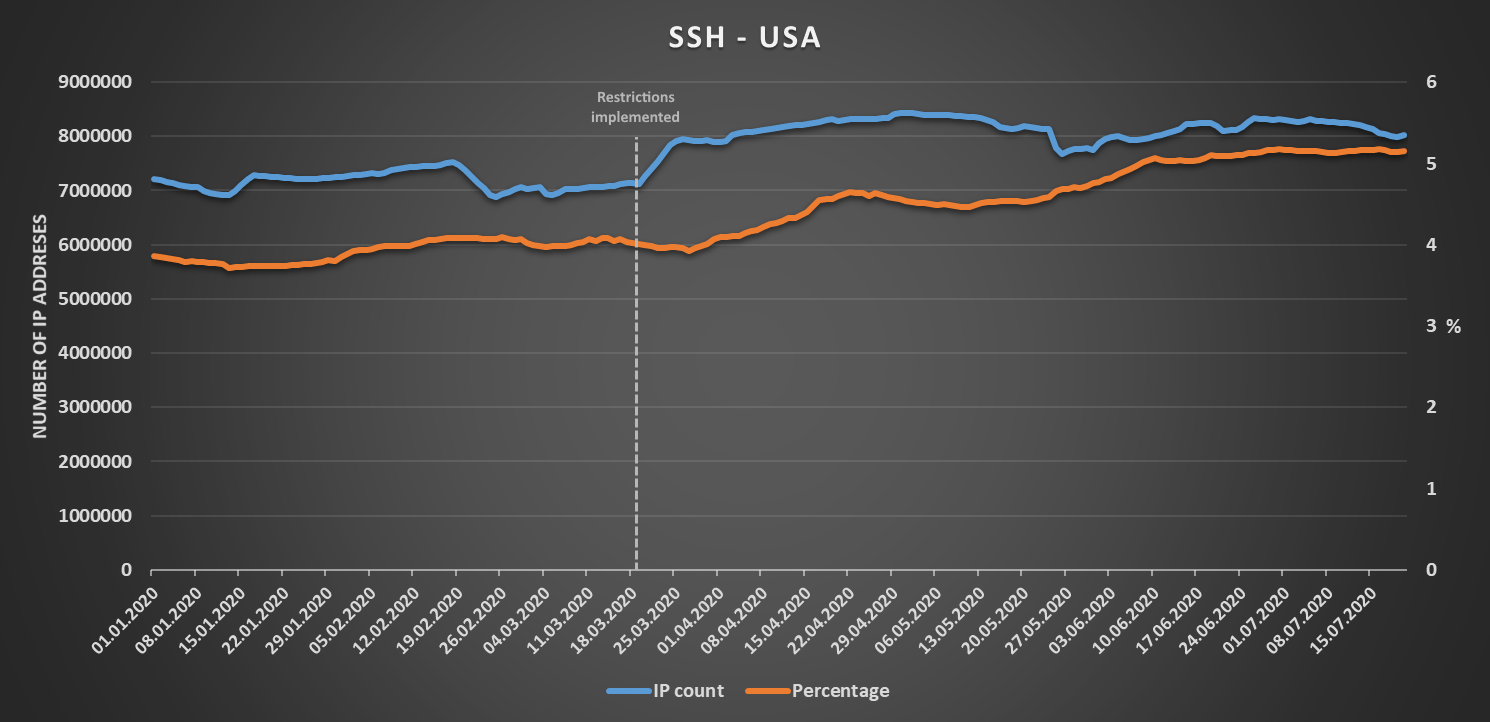
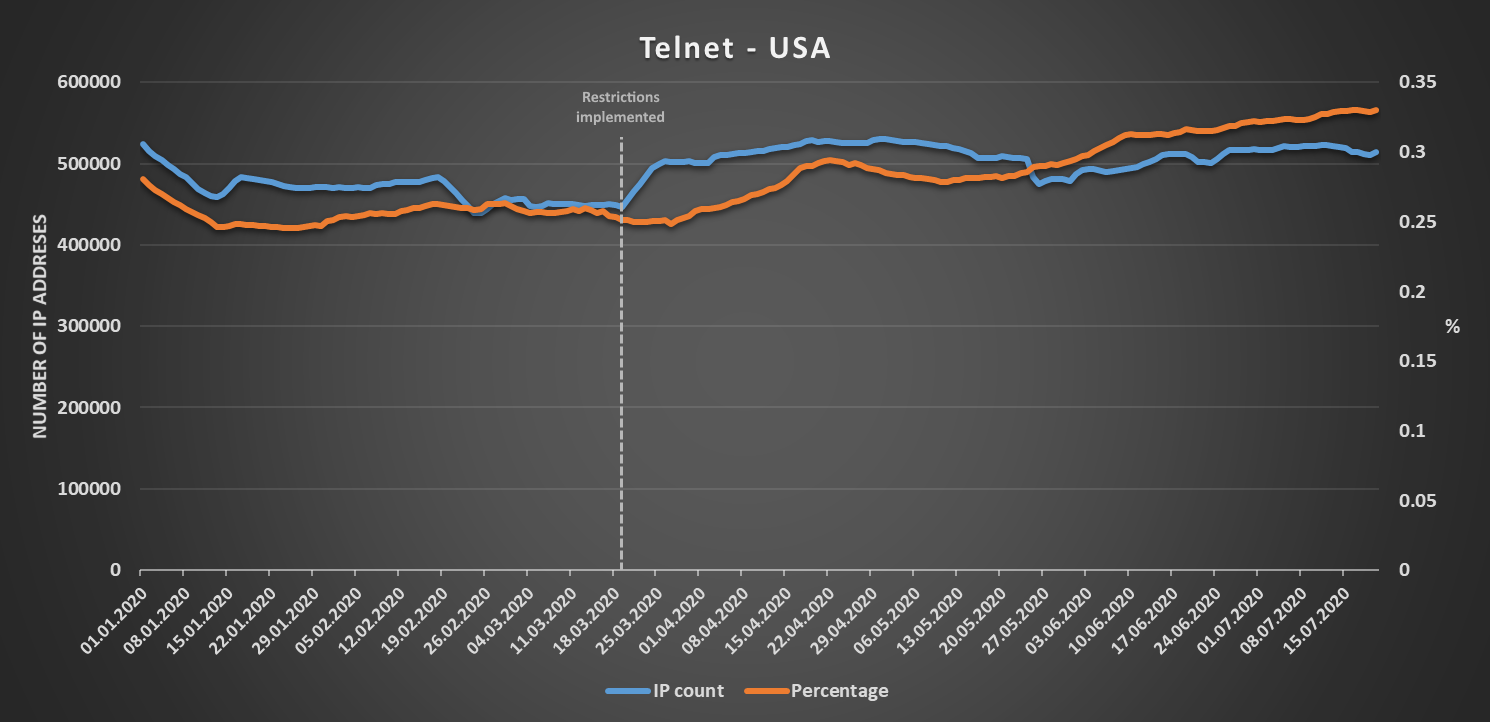
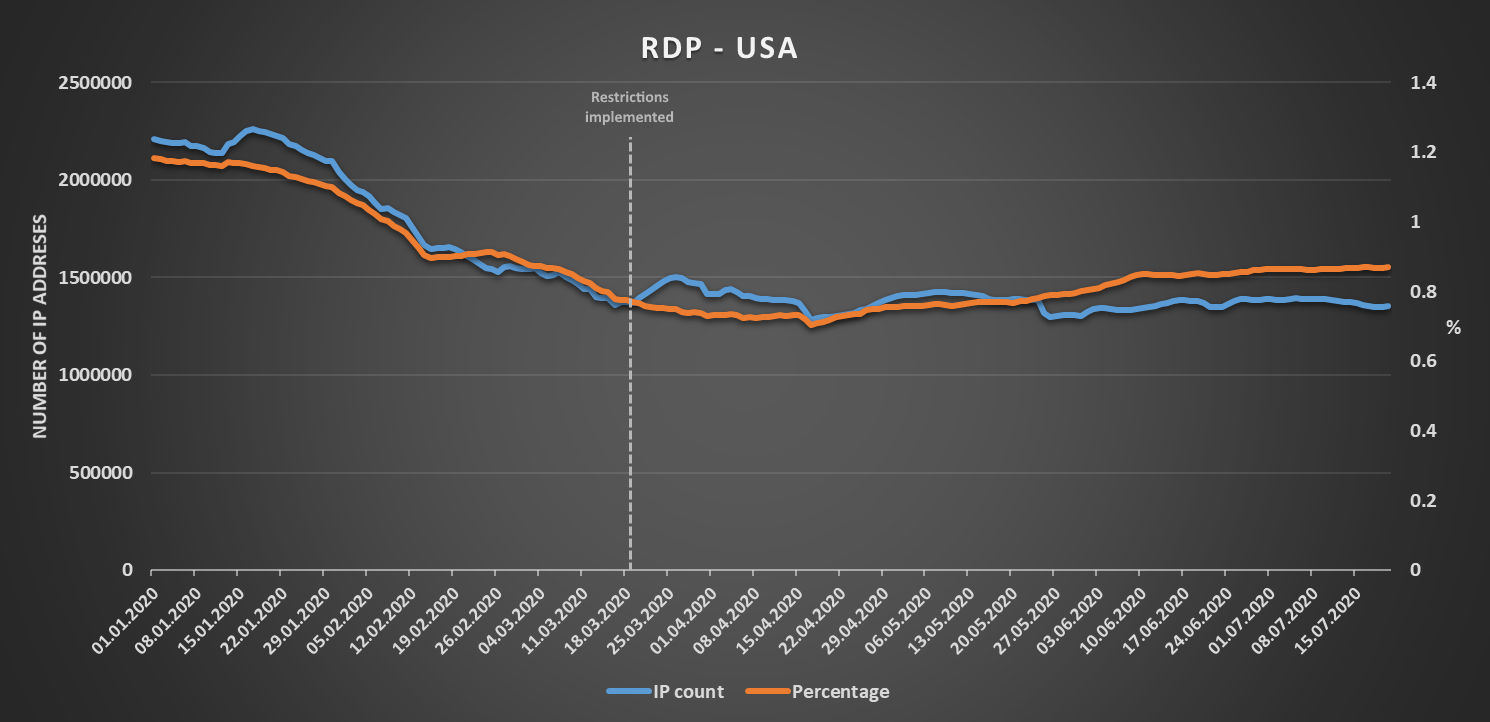
As we may see, the regional trends don’t necessarily always follow the global ones and may sometimes even be a bit counterintuitive...
[1] https://untrustednetwork.net/en/2020/04/02/open-ports-in-the-time-of-corona/
[2] https://blog.shodan.io/trends-in-internet-exposure/



Comments