Job application-themed malspam pushes ZLoader
Introduction
Last week, I published a diary about ZLoader malware spread through Polish malspam. Today's diary reviews more ZLoader spread through a different malspam campaign. Two interesting points about this campaign:
- The campaign uses password-protected XLS files, so they are not usually detected as malware on their own without the password.
- The URL for the initial ZLoader URL is geo-fenced. Although the emails and XLS files were in English, I could not get an infection from an IP address within the United States. I was able to successfully infect a lab host by going through a Canadian IP address.
- The Registry update to keep ZLoader persistent didn't happen until after I rebooted my infected lab host. I forgot to check if it would happen when I merely signed out and signed back in through the same user account.
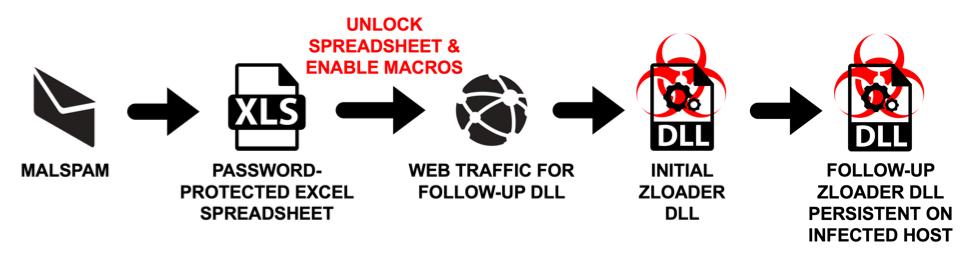
Shown above: Flow chart for this infection chain.
Images from the infection
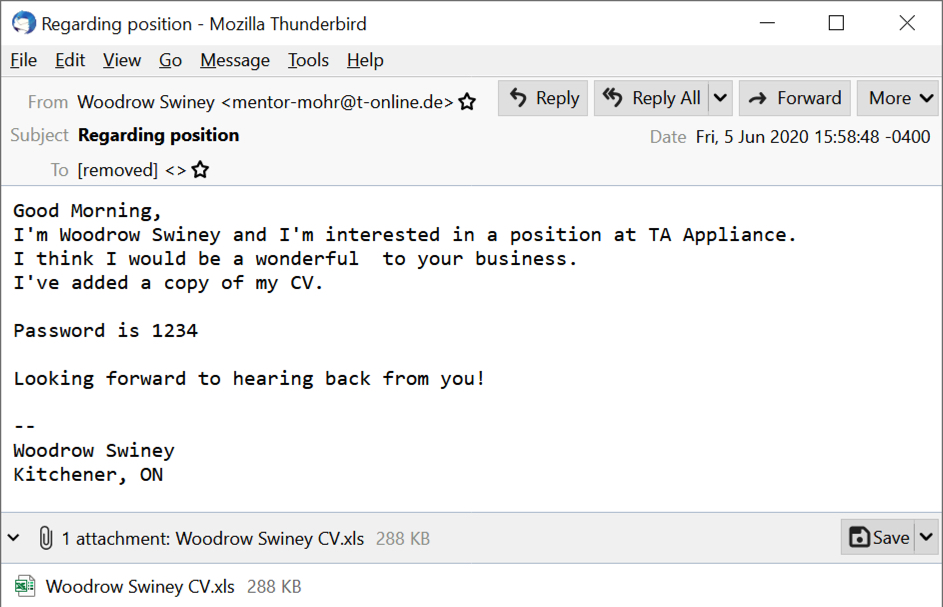
Shown above: Screenshot of an email from this campaign.
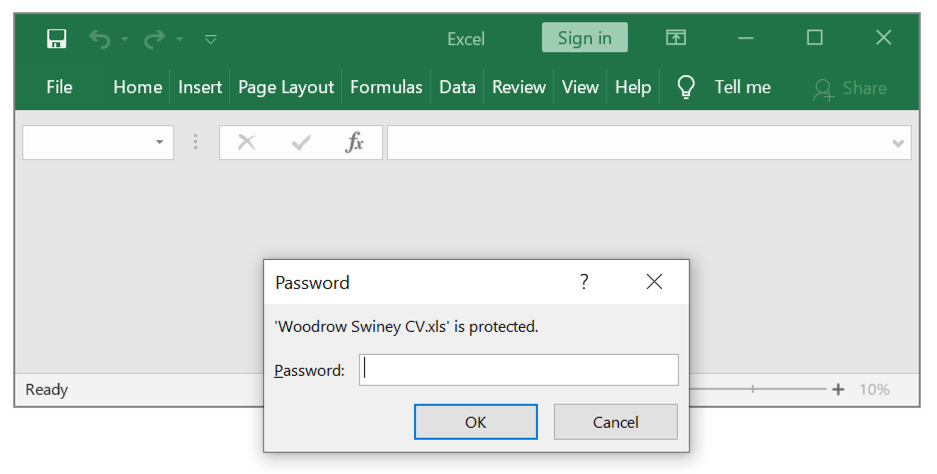
Shown above: You need the password from the email to unlock and open the XLS file.
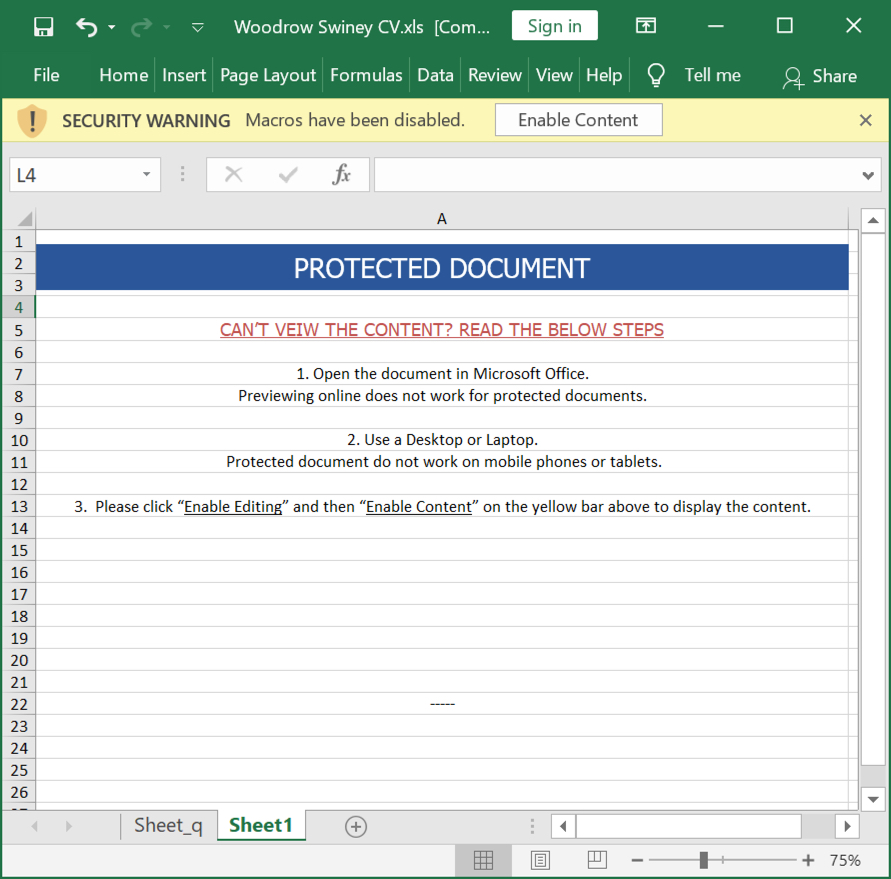
Shown above: Screenshot of the XLS file after it's unlocked.
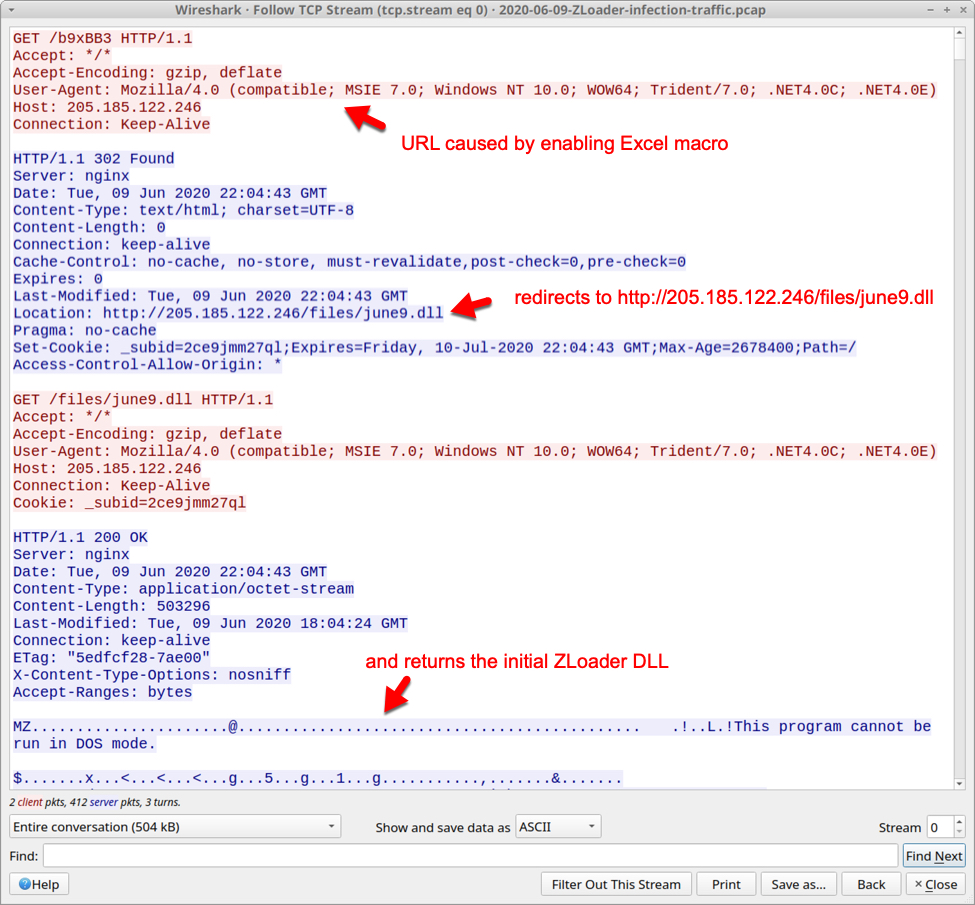
Shown above: Traffic seen for the ZLoader DLL after enabling macros on the unlocked XLS file.
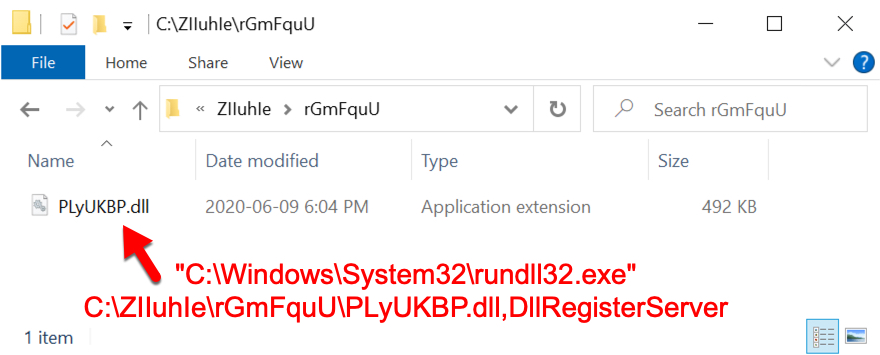
Shown above: The initial ZLoader DLL as it was first saved to my infected Windows host.
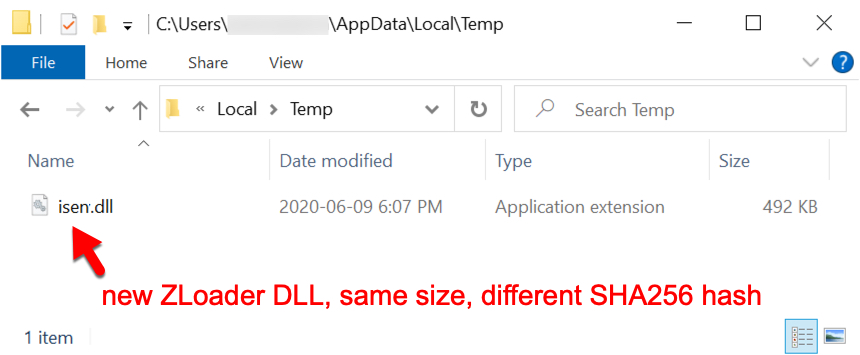
Shown above: Three minutes later, I saw a new ZLoader DLL the same size as the old one with a different SHA256 file hash.
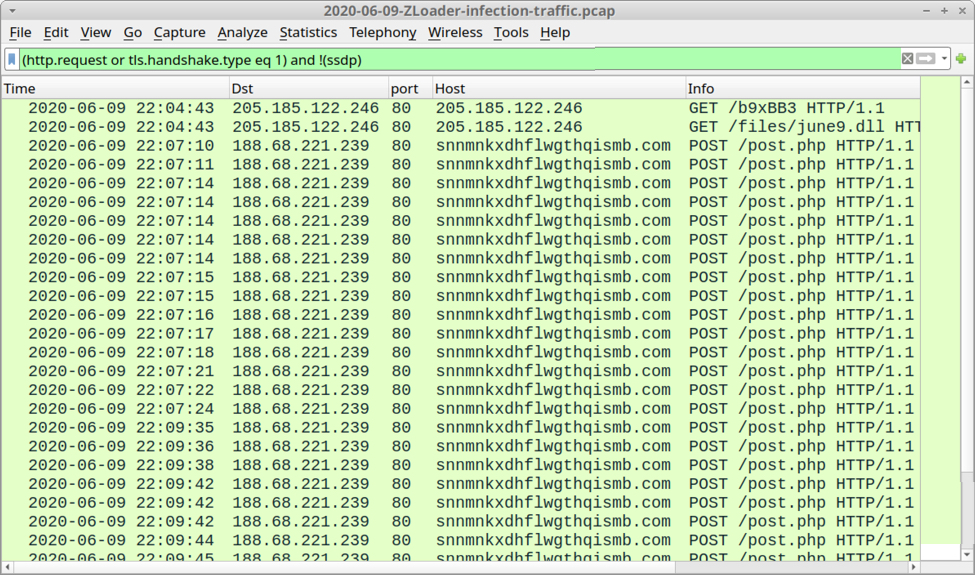
Shown above: Traffic from the infection filtered in Wireshark.
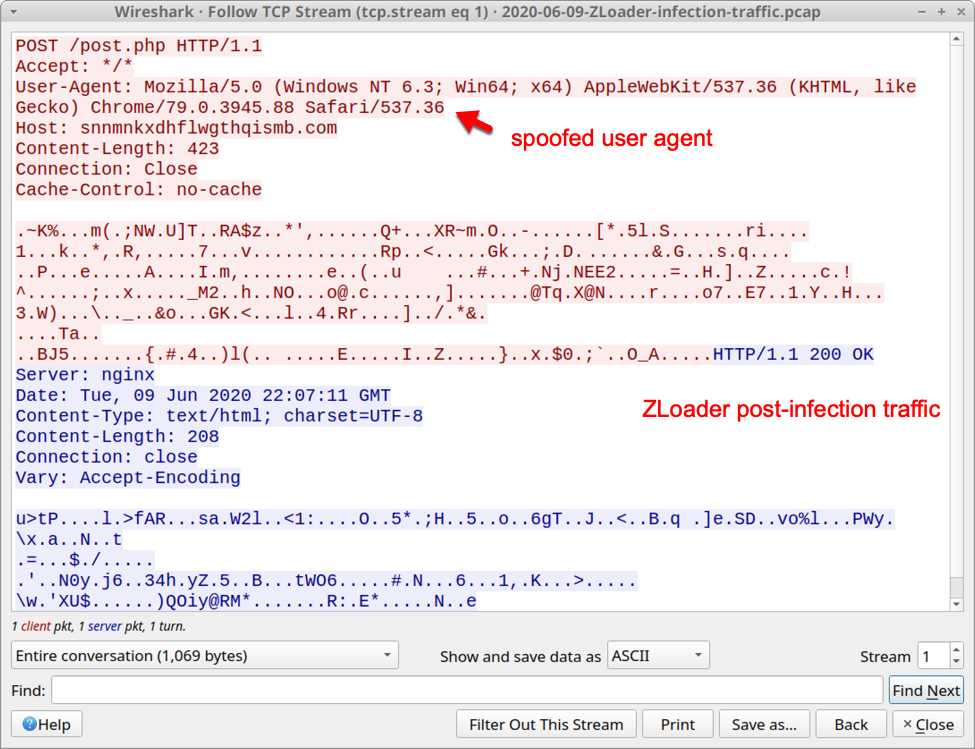
Shown above: TCP stream with an example of ZLoader post-infection traffic.
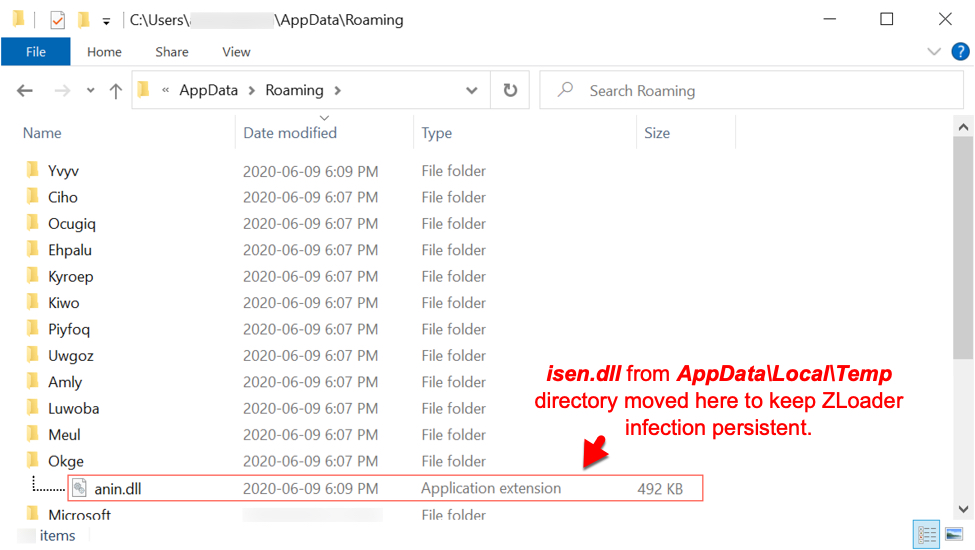
Shown above: ZLoader on the infected Windows host. Other folders in the AppData\Roaming directory created during this infection often had decoy files consisting of random binary data.
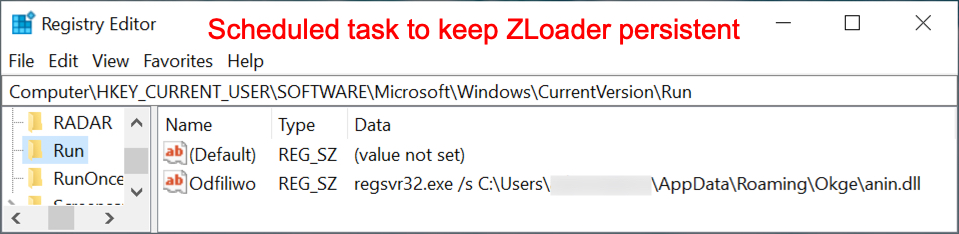
Shown above: Registry update to keep ZLoader persistent. The registry update didn't happen until after I rebooted my infected Windows host.
Indicators of Compromise (IoCs)
SHA256 hashes for password-protected XLS files (password: 1234)
- f4decddf7c66722424bc08001f76f96c7f5fffd00cecdecc6b192f1a48b0c41d
- 3d5c6bf7bca7714b1466c0a088a5dbe1a4684ec1d9142cb310d8c64688ce9fa4
- 4c250eca51e80b116d93fd7aec9764e6856244b048a050959275aa90b7d6ad6d
- d98e1ceeb9dc9c097bc3d1e14893c344657f67431e9b955833c1adbd85986493
- c5319187fae5cf975654cbdf041dd8fe5993e4ca9034bf517be82a2d16a0cd4c
- 6de3645643318c34d97b2106ce9dd34ce41cb0c11e6f2f2788916abfdef70ea2
- e0df76e2a4b60fd7eeebb57337e8a91f66c2d88a9750d30a3ce5e162d3f9436f
Malware retrieved from an infected Windows 10 host:
SHA256 hash: 0829886e0ca34a32fa545e0a53d7a2208d963b7b826a14aefde94d9ff4f549e5
- File size: 503,296 bytes
- File location: hxxp://205.185.122[.]246/files/june9.dll
- File location: C:\ZIIuhIe\rGmFquU\PLyUKBP.dll
- File description: Initial DLL file for ZLoader retrieved by Word macro
- Run method: rundll32.exe PLyUKBP.dll,DllRegisterServer
SHA256 hash: aa8fc19f16e4e185f6464d2e18ec7731c235d2b0d364f76965cf5967d5eef613
- File size: 503,296 bytes
- File location: C:\Users\[username]\AppData\Local\Temp]isen.dll
- File location: C:\Users\[username]\AppData\Roaming\Okge\anin.dll
- File description: Follow-up DLL for ZLoader persistent on the infected Win10 host
- Run method: regsvr32.exe /s anin.dll
Traffic from an infected Windows 10 host:
- 205.185.122[.]246 port 80 - 205.185.122[.]246 - GET /b9xBB3
- 205.185.122[.]246 port 80 - 205.185.122[.]246 - GET /files/june9.dll
- 188.68.221[.]239 port 80 - snnmnkxdhflwgthqismb[.]com - POST /post.php
Final words
As always, these types of infections are not very effective against fully-patched and up-to-date computers running the latest version of Microsoft Windows. The default virus & threat protection settings should stop these samples of ZLoader from infecting a Windows 10 host. Real-time protection and Tamper Protection are designed to prevent such activity.
And as I mentioned last week, malware authors continually adjust their malware in an attempt to escape detection. With the low cost of distribution through email, and with poor security practices among potential victims, campaigns pushing ZLoader and other malware will likely remain cost-effective.
Pcap and malware samples for today's diary can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments