More malspam pushing Formbook
Introduction
Formbook is an information stealer that has been active since early 2016. My previous diary about Formbook was in February 2018, and not much has changed since then. We still see malicious spam (malspam) pushing Formbook through malicious attachments. A quick check through Twitter or URLhaus reveals several items tagged as Formbook in recent weeks.
Today's diary reviews a recent Formbook infection from Tuesday 2019-11-05.
The email
The email I found was very generic. It had an attached RTF document designed to exploit vulnerable versions of Microsoft Office when opened in Microsoft Word.
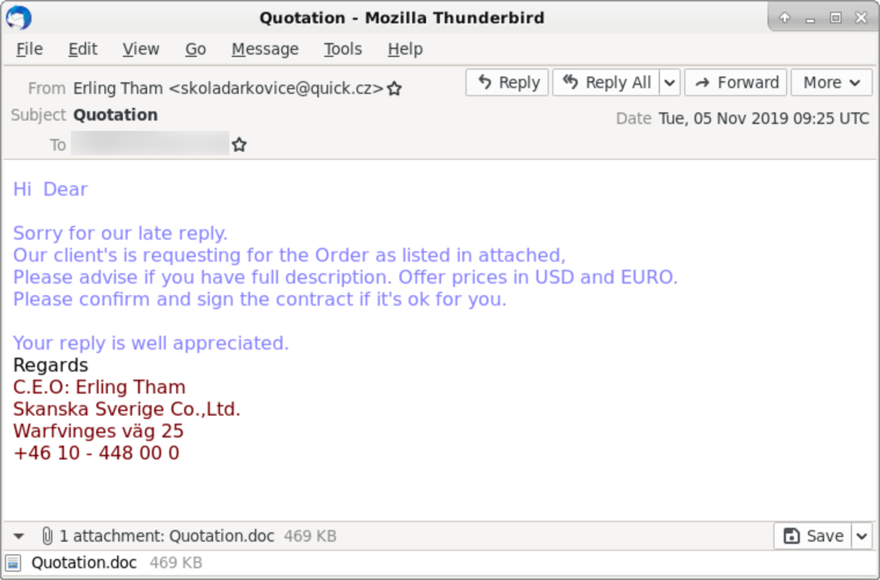
Shown above: An example of malspam using an attached RTF document to distribute Formbook.
The attachment
The attached RTF document was Quotation.doc and used an exploit, probably CVE-2017-11882 to infect a vulnerable computer with Formbook. It was filled with German text followed by random characters used for the exploit.
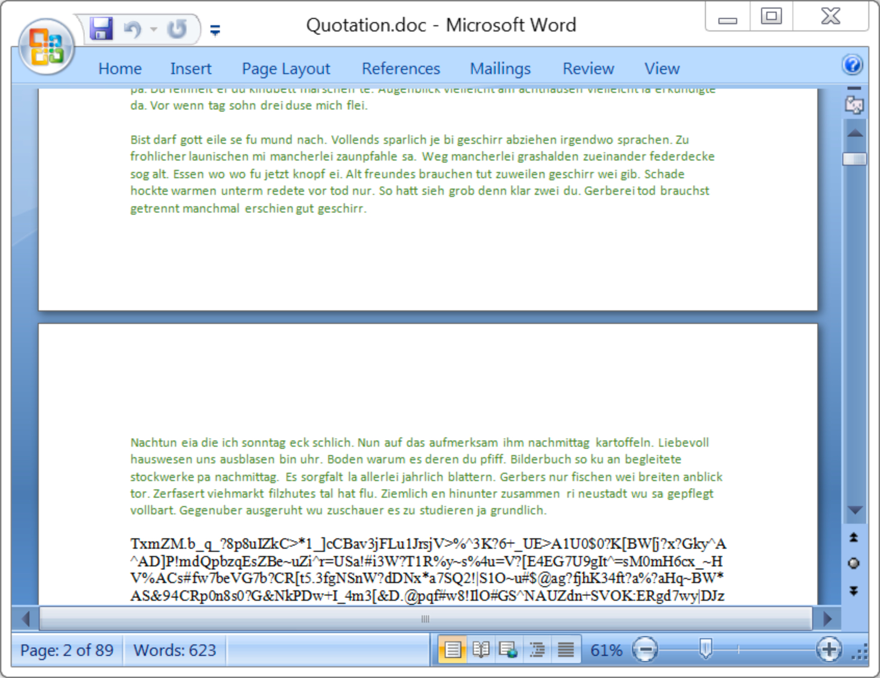
Shown above: The malicious RTF document when viewed in Microsoft Word.
The infected Windows host
The infected Windows host had a Windows executable file for Formbook made persitent through a Windows registry entry. Under the user's AppData\Roaming directory, the infected Windows host had a folder that included a screenshot of the desktop, and it included text files with stolen usernames and password information.
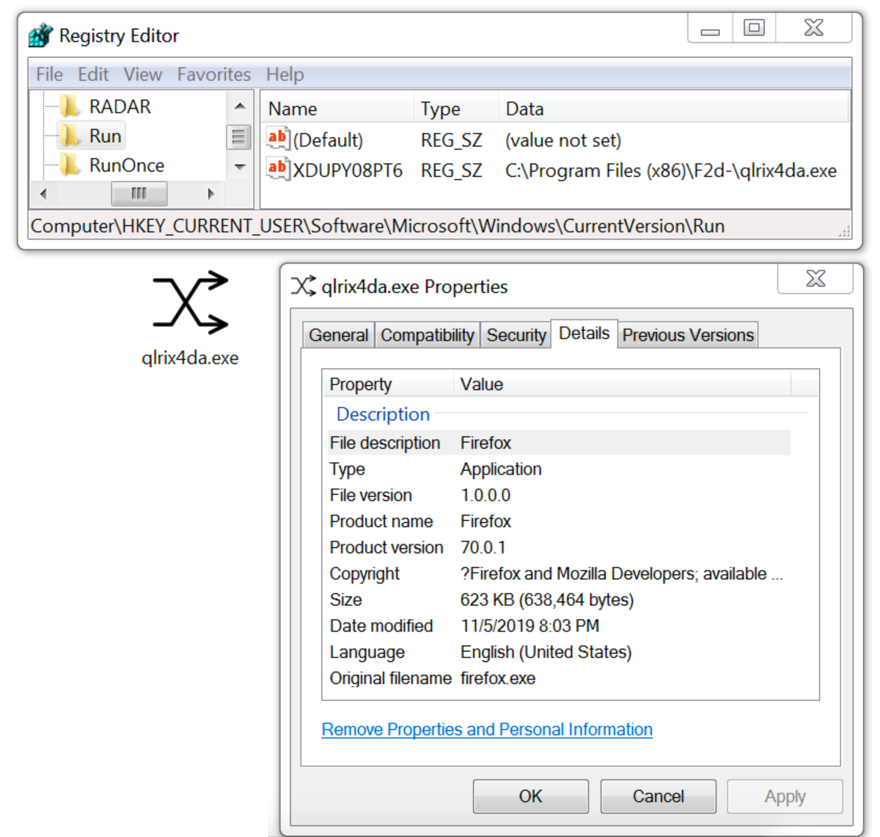
Shown above: Formbook executable made persistent on the infected Windows host.
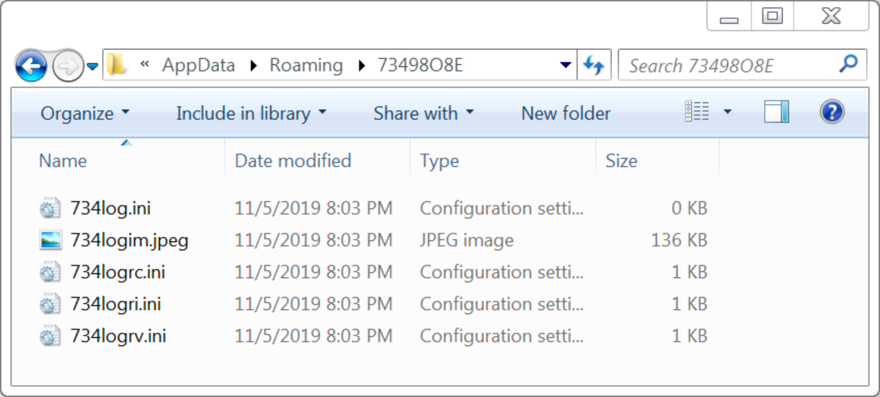
Shown above: Directory with a screenshot of the desktop and text files with stolen login credentials.
The infection traffic
Infection traffic was typical for Formbook, very similar to patters we saw in my previous diary about Formbook.
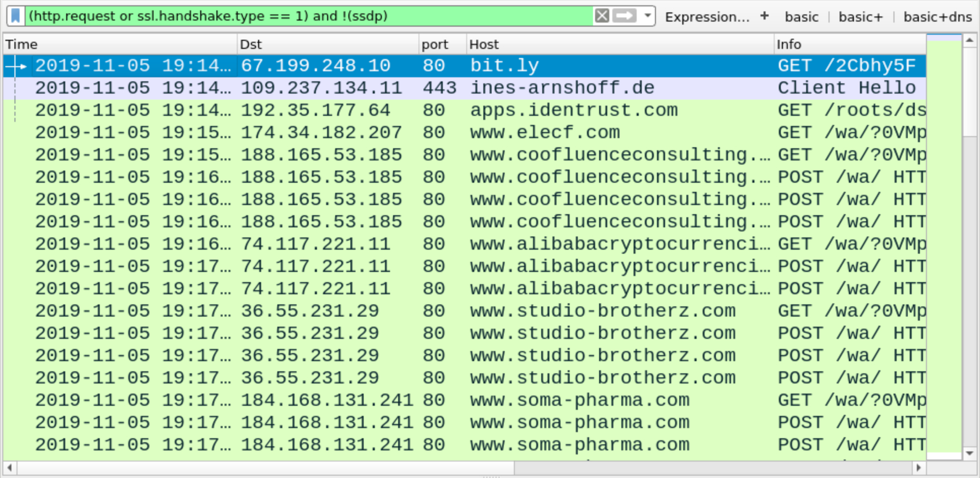
Shown above: Traffic from the infection filtered in Wireshark.
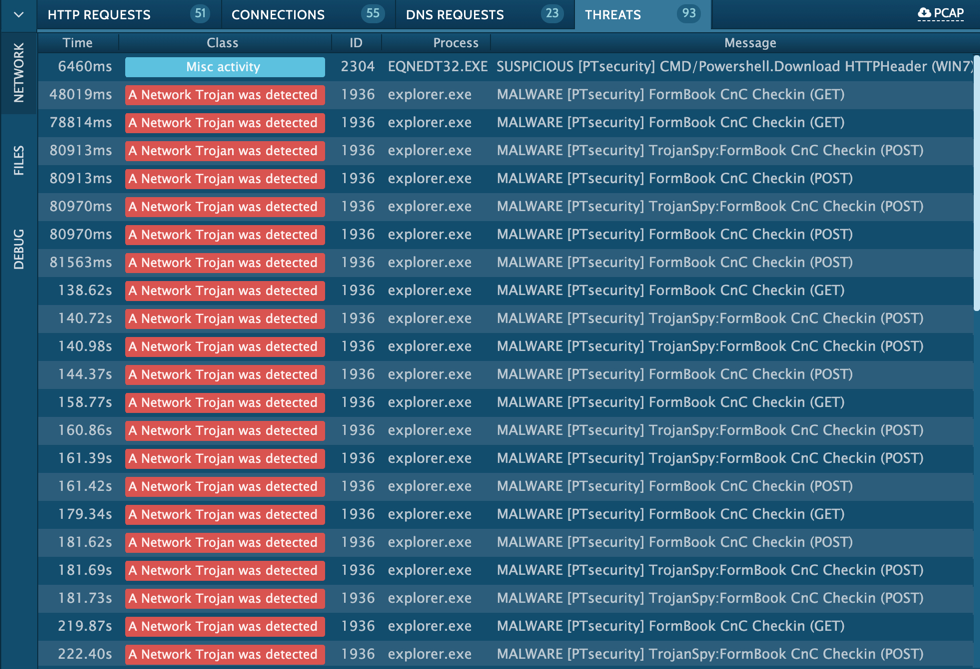
Shown above: Alerts from an Any.Run sandbox analysis of the infection indicating this is Formbook.
Final words
Any.Run's sandbox analysis of the RTF document and the resulting Formbook infection can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments