Malspam pushing Quasar RAT
Introduction
Quasar is a publicly-available Remote Access Tool (RAT) for Windows hosts. Here is a link to the Github page for Quasar RAT. This RAT is occasionally distributed as malware through malicious spam (malspam). On Tuesday 2019-09-24 I found malspam with malware based on Quasar RAT. Today's diary reviews the infection activity.
The email
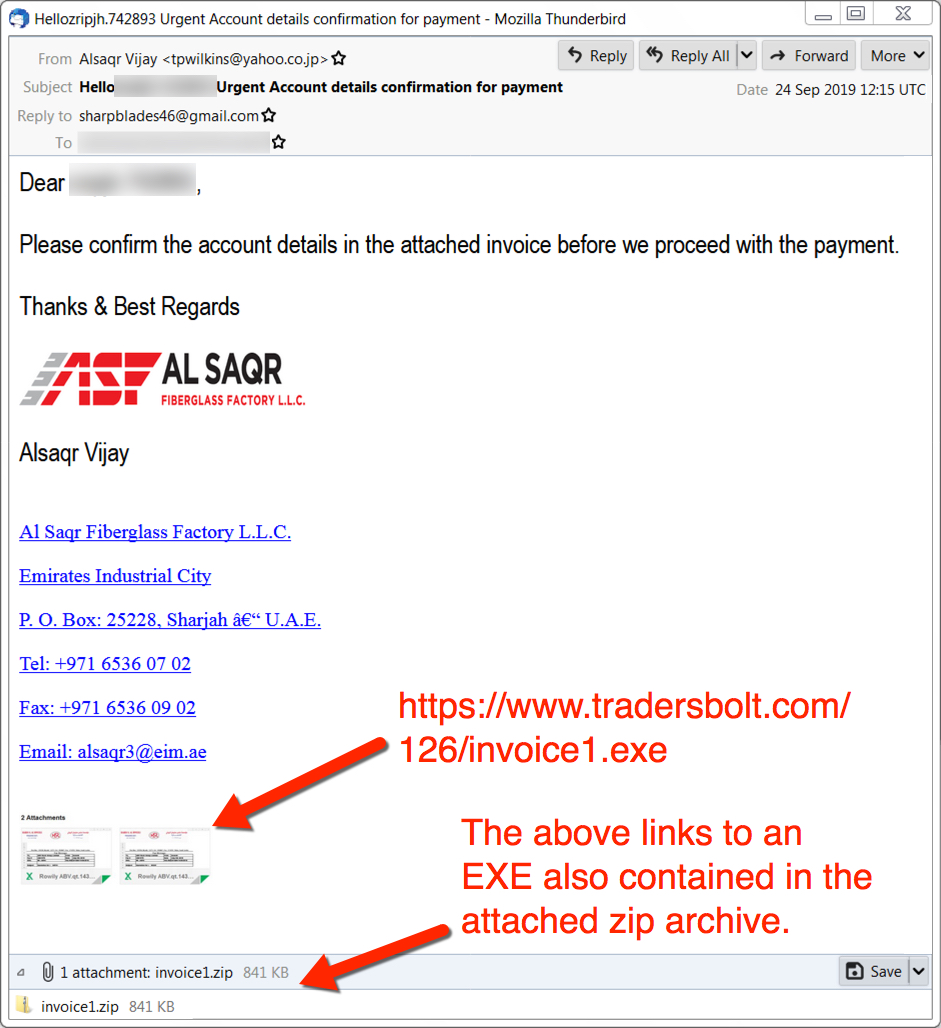
Shown above: Screenshot of the email.
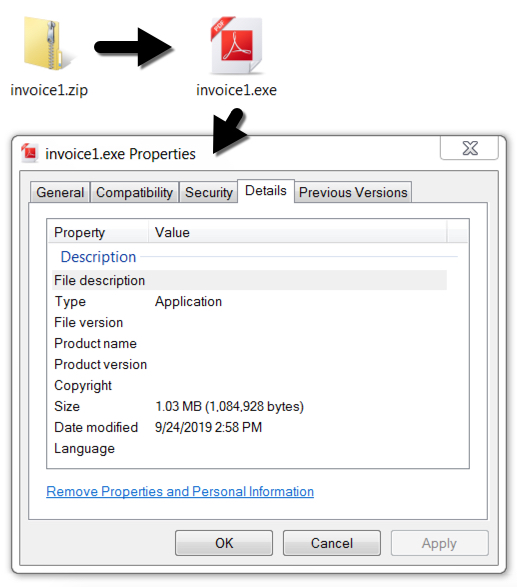
Shown above: The attachment and extracted Windows executable for Quasar RAT.
Infection traffic
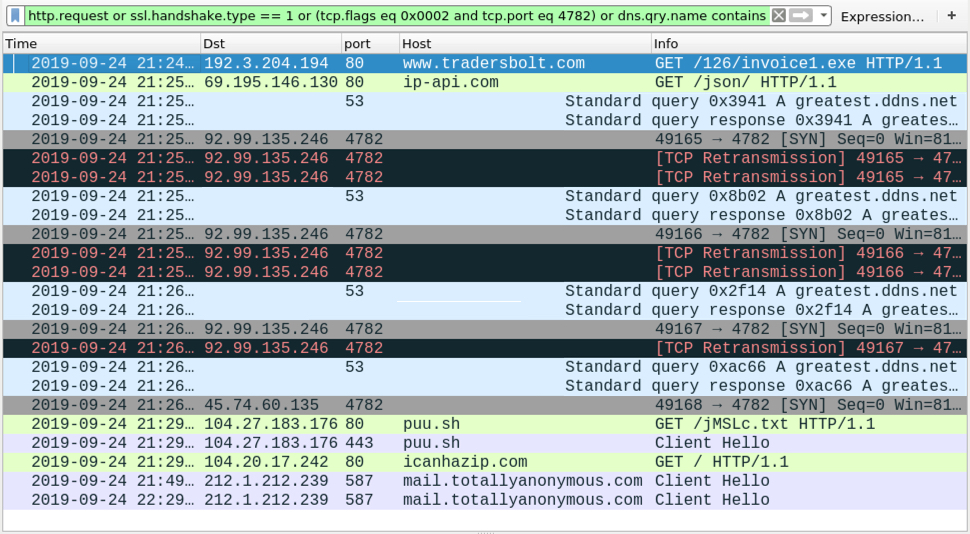
Shown above: Screenshot of the infection traffic filtered in Wireshark.
Post-infection forensics
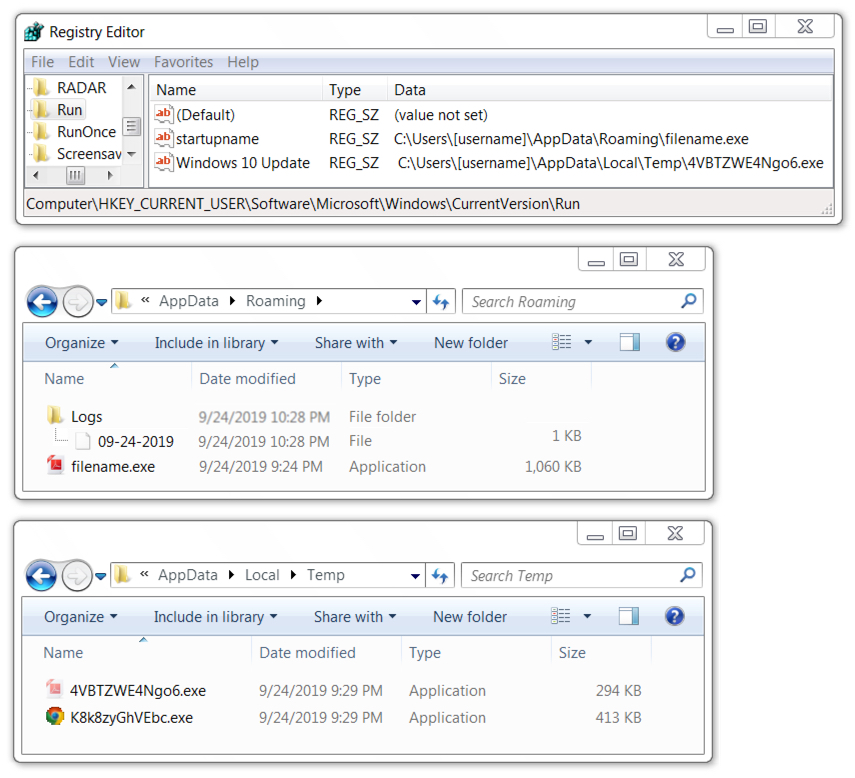
Shown above: Quasar RAT artifacts on the infected Windows host
Indicators of Compromise (IOCs)
The following infection traffic was seen on my infected lab host:
- 192.3.204[.]194 port 442 - www.tradersbolt[.]com - GET /126/invoice1.exe
- port 80 - ip-api[.]com - GET /json/ - IP address check (not inherently malicious)
- 92.99.135[.]246 port 4782 - greatest.ddns[.]net - attempted TCP connections but no response
- 45.74.60[.]135 port 4782 - greatest.ddns[.]net - Quasar RAT C2 traffic
- port 80 - puu[.]sh - GET /jMSLc.txt
- port 443 - puu[.]sh - HTTPS traffic
- port 80 - icanhazip[.]com - GET / - IP address check (not inherently malicious)
- port 587 - mail.totallyanonymous[.]com - Encrypted SMTP traffic from Quasar RAT-infected host
The following items are malware associated with this infection:
SHA256 hash: abc980ebd2463ff522ff090914cc21d02915f643f385ee0ea0af23d51a18e47f
- File size: 861,270 bytes
- File name: invoice1.zip
- File description: Zip attachment from malspam
SHA256 hash: edcbbb59405b2bb97269ed5db32a15b57154221adb9504ff828ee367953cccc1
- File size: 1,084,928 bytes
- File name: invoice1.exe
- File location: hxxps://www.tradersbolt[.]com/126/invoice1.exe
- File location: C:\Users\[username]\AppData\Roaming\filename.exe
- File description: Quasar RAT EXE extracted from zip attachment or retreived from link in the malspam
SHA256 hash: 065ac3f23800921135b1794706aca86ab59c94ab463c5c17a4d3535bf9aab828
- File size: 300,544 bytes
- File location: C:\Users\[username]\AppData\Local\Temp\4VBTZWE4Ngo6.exe
- File description: File created when Quasar RAT EXE was executed (1 of 2)
SHA256 hash: 389863b056fa0c3d4ebf130103445bc56769824f1e6cecea9c950744b80752b0
- File size: 422,139 bytes
- File location: C:\Users\[username]\AppData\Local\Temp\K8k8zyGhVEbc.exe
- File description: File created when Quasar RAT EXE was executed (2 of 2)
Final words
The email, a pcap of the infection traffic, and the associated malware is available here.
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments