Emotet malspam is back
Introduction
As already reported, malicious spam (malspam) pushing Emotet is back approximately 3 and 1/2 months after it disappeared. Today's diary reviews infection traffic from Tuesday, 2019-09-17.
Emotet's disappearance
After May 2019, I stopped finding any new examples of malspam pushing Emotet. As early as 2019-06-09, someone reported the command and control (C2) infrastructure for Emotet had gone silent. The C2 infrastructure was active again as early as 2019-08-22, which led to several reports that Emotet was back. However, no malspam was reported until Monday 2019-09-16. Since then, Emotet activity levels are back to what we saw before the 3 and 1/2 month break.
A new Emotet malspam example
Recent examples of Emotet malspam I found all use German language message text. Like before, this malspam uses attached Word documents, or it uses links to download Word documents. These Word documents have malicious macros designed to infect a vulnerable Windows host with Emotet.
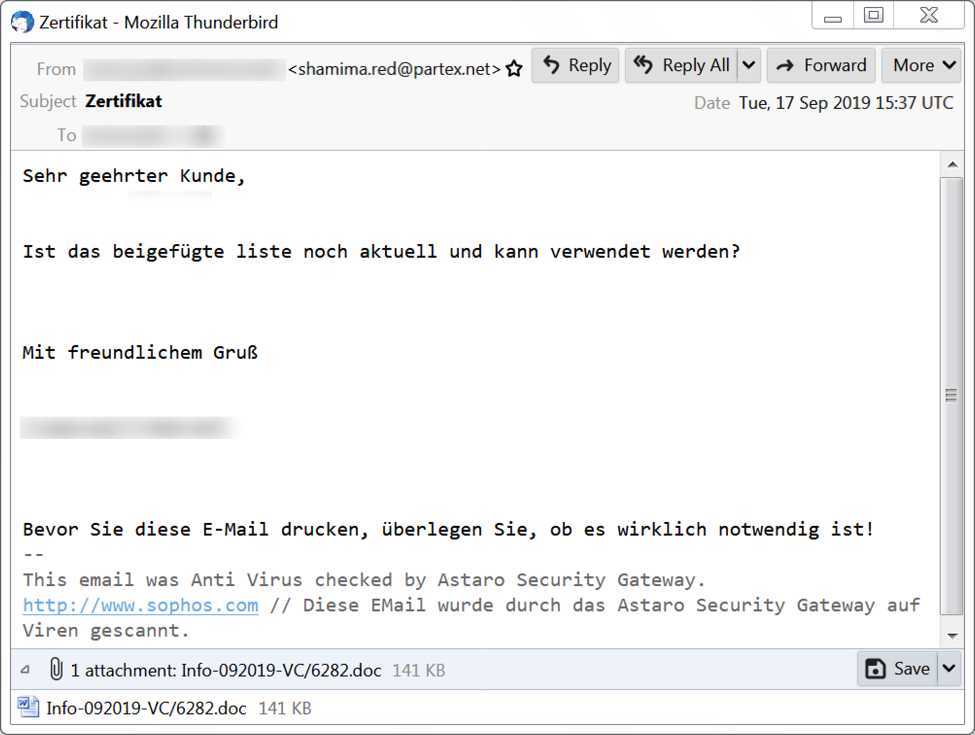
Shown above: Screenshot of Emotet malspam from Tuesday 2019-09-17.

Shown above: The attached Word document with macros for Emotet.
Infection traffic
Traffic for this Emotet infection was typical for what we saw before the 3 and 1/2 month break. Emotet acts as a distributor for other malware, and in this case I saw Trickbot traffic after the initial Emotet infection.
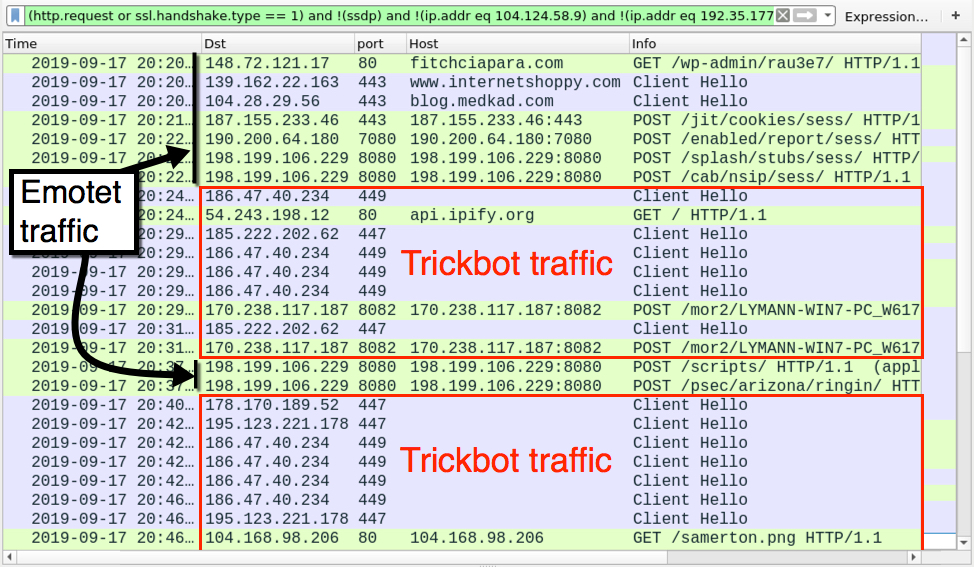
Shown above: Traffic from the infection filtered in Wireshark.
Forensics on the infected Windows host
I saw the same type of artifacts on my infected Windows host that I'd seen in recent Emotet and/or Trickbot infections. See the images below for details.
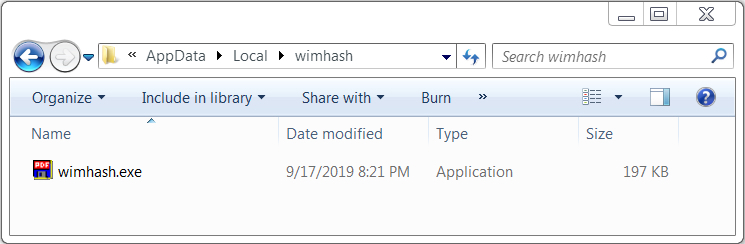
Shown above: Emotet from the infected Windows host.
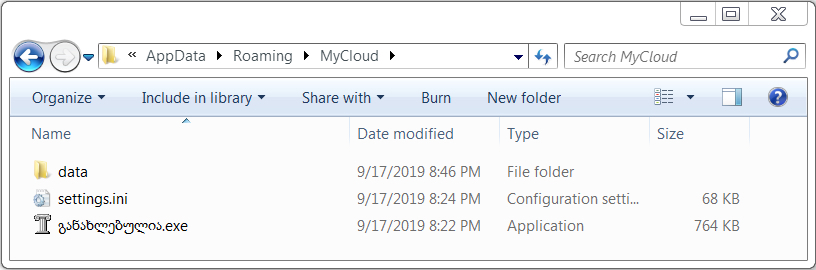
Shown above: Trickbot on the infected Windows host.

Shown above: Trickbot modules on the infected Windows host.

Shown above: Persistence mechanisms for Emotet and Trickbot on the infected host.
Indicators of Compromise (IoCs)
URLs caused by the Word macro to retrieve an Emotet EXE:
- 148.72.121[.]17 port 80 - fitchciapara[.]com - GET /wp-admin/rau3e7/
- 139.162.22[.]163 port 443 (HTTPS) - www.internetshoppy[.]com - GET /wp-includes/971426/
- 104.28.29[.]56 port 443 (HTTPS) - blog.medkad[.]com - GET /wp-admin/e9684/
- 107.180.0[.]193 port 80 - www.sirijayareddypsychologist[.]com - GET /roawk/0kwsol940/
- 205.144.171[.]168 port 80 - komatireddy[.]net - GET /wp-content/911968/
Post-infection traffic caused by Emotet:
- 187.155.233[.]46 port 443 - 187.155.233[.]46:443 - POST /jit/cookies/sess/
- 190.200.64[.]180 port 7080 - 190.200.64[.]180:7080 - POST /enabled/report/sess/
- 198.199.106[.]229 port 8080 - 198.199.106[.]229:8080 - POST /splash/stubs/sess/
- 198.199.106[.]229 port 8080 - 198.199.106[.]229:8080 - POST /cab/nsip/sess/
- 198.199.106[.]229 port 8080 - 198.199.106[.]229:8080 - POST /scripts/
- 198.199.106[.]229 port 8080 - 198.199.106[.]229:8080 - POST /psec/arizona/ringin/
- 79.127.57[.]42 port 80 - attempted TCP connections, but no response from the server
- 181.81.143[.]108 port 80 - attempted TCP connections, but no response from the server
- 66.228.32[.]31 port 443 - attempted TCP connections, but no response from the server
- 198.50.170[.]27 port 8080 - attempted TCP connections, but no response from the server
- 216.98.148[.]157 port 8080 - attempted TCP connections, but no response from the server
Post-infection traffic caused by Trickbot:
- 186.47.40[.]234 port 449 - HTTPS/SSL/TLS traffic
- port 80 - api.ipify[.]org - GET /
- 185.222.202[.]62 port 447 - HTTPS/SSL/TLS traffic
- 178.170.189[.]52 port 447 - HTTPS/SSL/TLS traffic
- 195.123.221[.]178 port 447 - HTTPS/SSL/TLS traffic
- 170.238.117[.]187 port 8082 - 170.238.117[.]187:8082 - POST /mor2/[hostname]_[Windows version].[hex string]/90
- 170.238.117[.]187 port 8082 - 170.238.117[.]187:8082 - POST /mor2/[hostname]_[Windows version].[hex string]/81
- 104.168.98[.]206 port 80 - 104.168.98[.]206 - GET /samerton.png
- 104.168.98[.]206 port 80 - 104.168.98[.]206 - GET /tablone.png
- 195.123.238[.]83 port 447 - attempted TCP connections, but no response from the server
- 108.170.40[.]34 port 447 - attempted TCP connections, but no response from the server
- 194.5.250[.]79 port 447 - attempted TCP connections, but no response from the server
- 66.55.71[.]15 port 447 - attempted TCP connections, but no response from the server
- 195.123.238[.]110 port 447 - attempted TCP connections, but no response from the server
Files from the infected Windows host:
SHA256 hash: 34d2b83245696fa1dd24ef9ed4b33ef9172e9f6e274928628bd24c1de0763b47
- File size: 143,970 bytes
- File name: Info-092019-VC_6282.doc
- File description: Attachment from malspam--Word doc with macro for Emotet
SHA256 hash: de51c2bdcadf6ed9d159cdeb222af834144732da27e6f70e3d03019c57e221be
- File size: 76,288 bytes
- File location: hxxps://blog.medkad[.]com/wp-admin/e9684/
- File location: C:\Users\[username]\979.exe
- File location: C:\Users\[username]\AppData\Local\[random name]\[same random name].exe
- File description: Initial Emotet EXE retrieved by Word macro
SHA256 hash: b47d3146bf26d007cfbbb3a8527ae60885f265ed24e2a33ab3caad66f20e7683
- File size: 201,728 bytes
- File location: C:\Users\[username]\AppData\Local\[random name]\[same random name].exe
- File description: Updated Emotet EXE after initial infection
SHA256 hash: 571e071e1cf7151cabda294c7a41c72b541b7e17231a18ce815eed8e1b4dbaab
- File size: 782,336 bytes
- File location: C:\M9Y7o6OLANbw.exe
- File location: C:\ProgramData\[Georgian characters].exe
- File location: C:\Users\[username]\AppData\Roaming\MyCloud\[Georgian characters].exe
- File description: Trickbot (gtag: mor2) retrieved by Emotet-infected Windows host
Final Words
Pcap and malware from this infection can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments