Suspicious GET Request: Do You Know What This Is?
Reader Vinnie noticed following suspicious GET request directed at his web server:
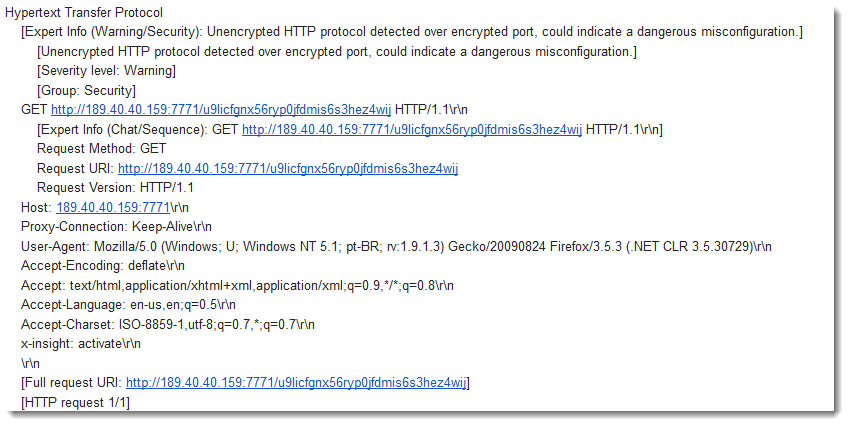
My first idea was an attempt to abuse his web server as a proxy, or log SPAM.
Vinnie executed this request (hxxp://189[.]40[.]40[.]159:7771/u9licfgnx56ryp0jfdmis6s3hez4wij), and got text back:
171886eb9748eb13fc7548e018bf5b70jA0ECQMCkTJtXpMYj4b00ukBAU2wE+cAc+fGlL16GWLH6RAVc2yShs37UlBBj2cDX3s7FLGSshr...
I was able to make some sense of this: the first 32 characters are hexadecimal digits, and the rest is BASE64. That BASE64 string decodes to binary data that starts with the magic header for "GPG symmetrically encrypted data (AES256 cipher)": "8C 0D 04 09 03 02".
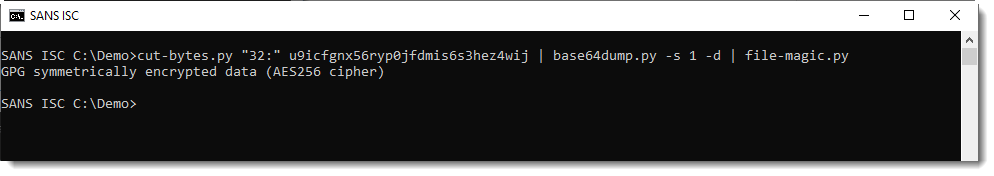
The data has a high entropy:
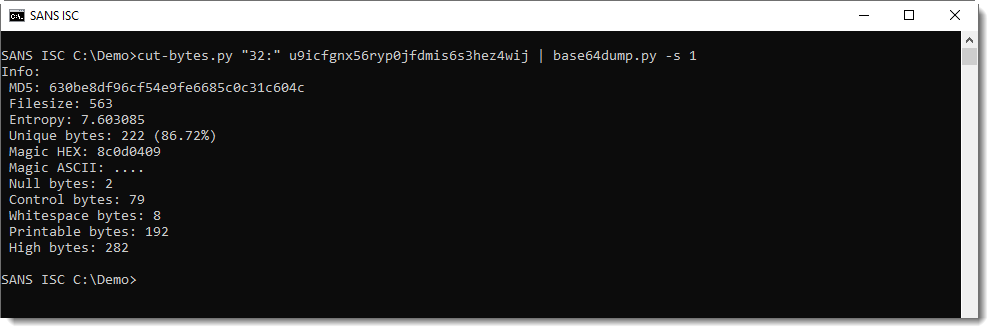
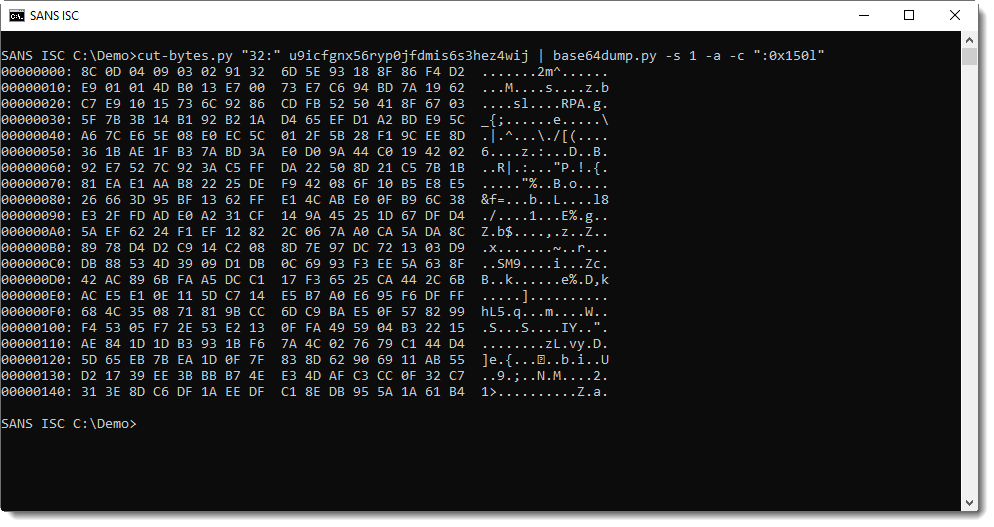
That's as far as I got.
We don't know if the server replying with this data is under the control of the attacker, or not. It could be an "innocent bystander".
Do you have any idea what this might be about, or what the data is? Please post a comment!
We're not asking to interact with this server, there's no need. We want to know if you have ideas about the request type or returned data. Should you still decide to interact with this server, be careful. We don't recommend it, we don't know what this server is or does. Don't do anything that might be considered hostile and don't do anything illegal.
If you want a second example of data, take a look at Shodan's report: https://www.shodan.io/host/189.40.40.159
Please post a comment, thanks!
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com



Comments