More malspam using password-protected Word docs
Introduction
This diary reviews an example of malicious spam (malspam) using password-protected Word documents to distribute Nymaim on Tuesday 2018-10-30.
Background: Since March 2013, I've documented several examples of malspam using password-protected Word documents to distribute malware. Previously, this malspam pushed various families of ransomware. In August 2018, this malspam switched to pushing Neutrino malware. By September 2018, this campaign started pushing Nymaim.
Last week on 2018-10-26, this campaign briefly switched to pushing GlobeImposter ransomware, but this week it's back to pushing Nymaim.
A list of my posts about this malspam (ISC diaries or posts from malware-traffic-analysis.net) follows:
2018-03-14 - Malspam with password-protected Word docs pushes Sigma ransomware
2018-04-20 - Malspam with password-protected Word docs pushes GlobeImposter ransomware
2018-05-09 - Malspam with password-protected Word docs pushes Sigma ransomware
2018-06-04 - Malspam with password-protected Word docs pushes Gandcrab ransomware
2018-07-23 - Malspam with password-protected Word docs pushes AZORult then Hermes ransomware
2018-07-27 - Malspam with password-protected Word docs pushes Hermes ransomware
2018-08-15 - More malspam pushing password-protected Word docs for AZORult and Hermes ransomware
2018-08-21 - More malspam with password-protected Word docs, now pushing Neutrino
2018-09-06 - Malspam with password-protected Word docs pushes AZORult then Neutrino
2018-09-17 - Quick post: Malspam with password-protected Word docs pushes Nymaim
2018-09-21 - Malspam with password-protected Word docs still pushing Nymaim
2018-09-28 - More malspam with password-protected Word docs pushing Nymaim
2018-10-26 - Malspam with password-protected Word docs now pushing GlobeImposter ransomware
Now let's review my most recent infection from Tuesday evening on 2018-10-30.
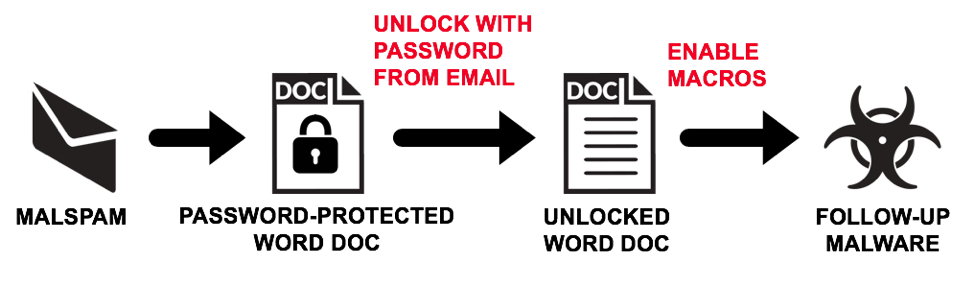
Shown above: Flow chart for infections from this malspam campaign.
Emails
The emails all have spoofed sending addresses, and recent messages are either resume-themed or invoice-themed. The most recent emails I've seen are invoice-themed with invoice.doc as the file attachment. These emails are currently sent from servers residing in the 176.119.6.0/24 block of IP addresses. This block appears to be administered by MultiDC, a hosting company based in the Ukraine. Passwords for the attached Word documents have been 1234 for several weeks now.
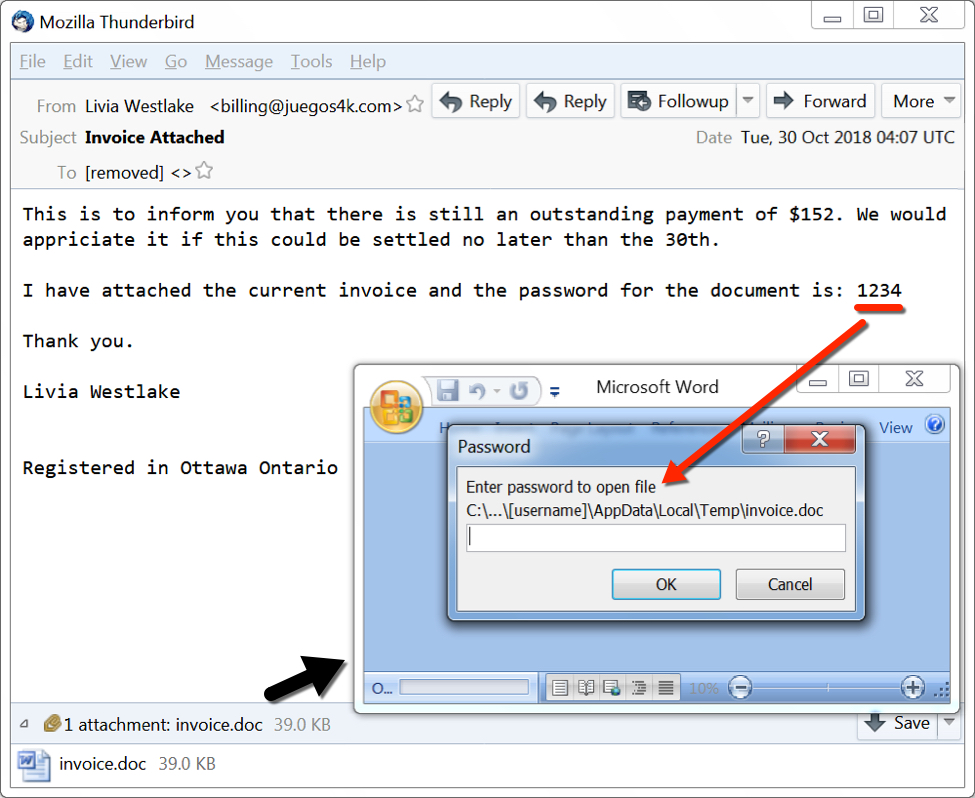
Shown above: An example of malspam from this campaign.
After a victim unlocks the password-protected Word document, it shows a message asking readers to enable macros. Macros on this Word document will download and install malware on a vulnerable Windows host.
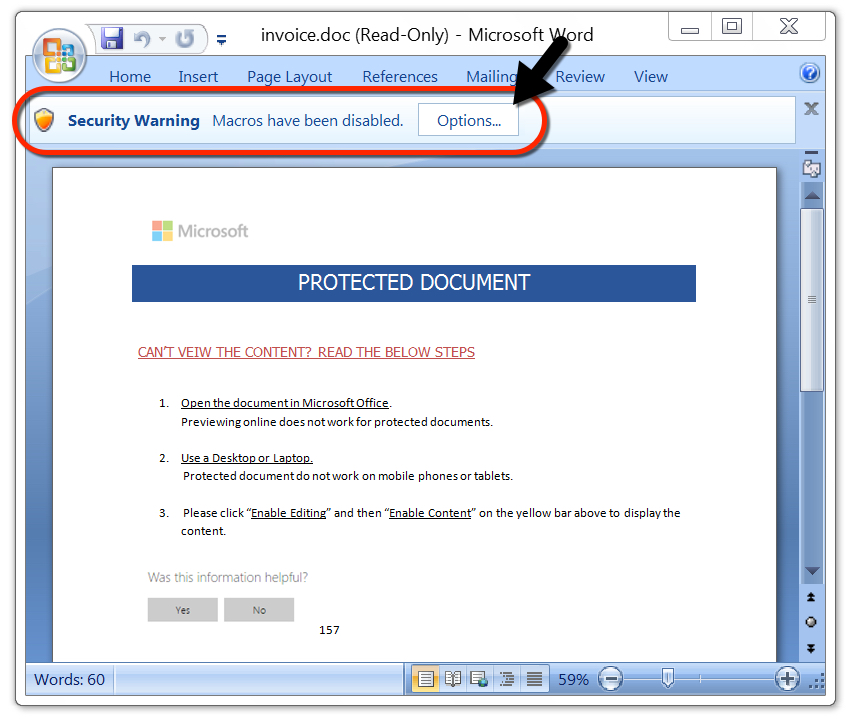
Shown above: An unlocked Word document waiting for its victim to enable macros.
Malware from an infected host
The Word macro retrieved a Windows executable from 209.141.60.230 and saved it to the user's AppData\Local\Temp directory as qwerty2.exe. In this case, qwerty2.exe was Nymaim. The malware deleted itself after follow-up Nymaim executables were installed and made persistent on the infected Windows host.
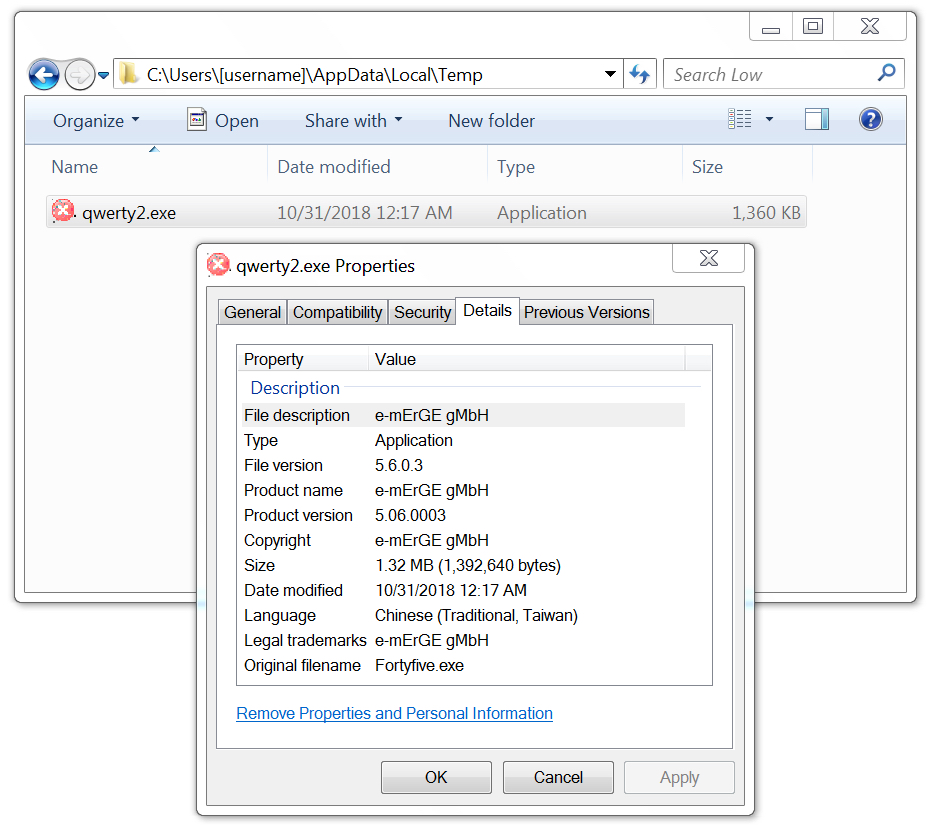
Shown above: Initial Nymaim executable that deleted itself after the infection.
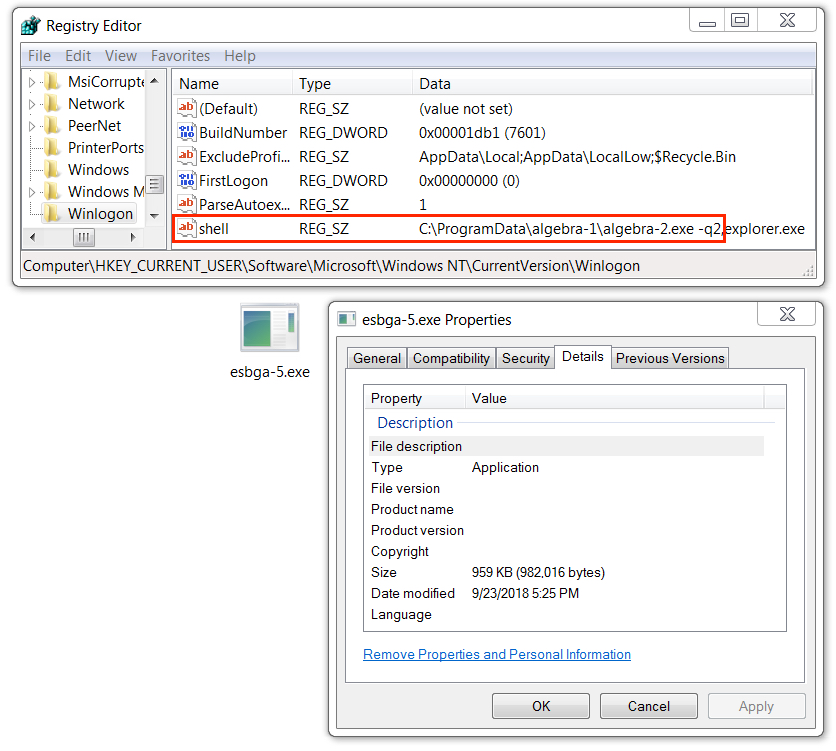
Shown above: Follow-up Nymaim executable (1 of 3) made persistent through the Windows registry.
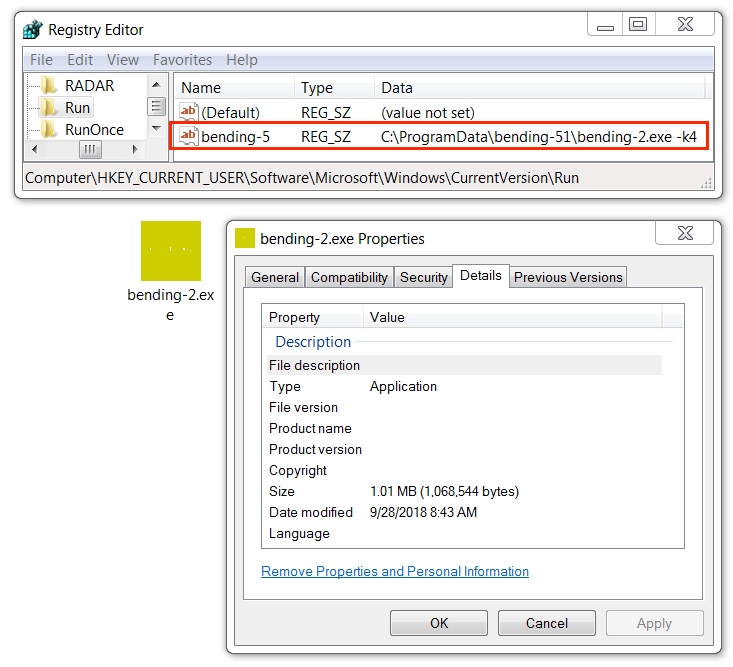
Shown above: Follow-up Nymaim executable (2 of 3) also persistent through the Windows registry.
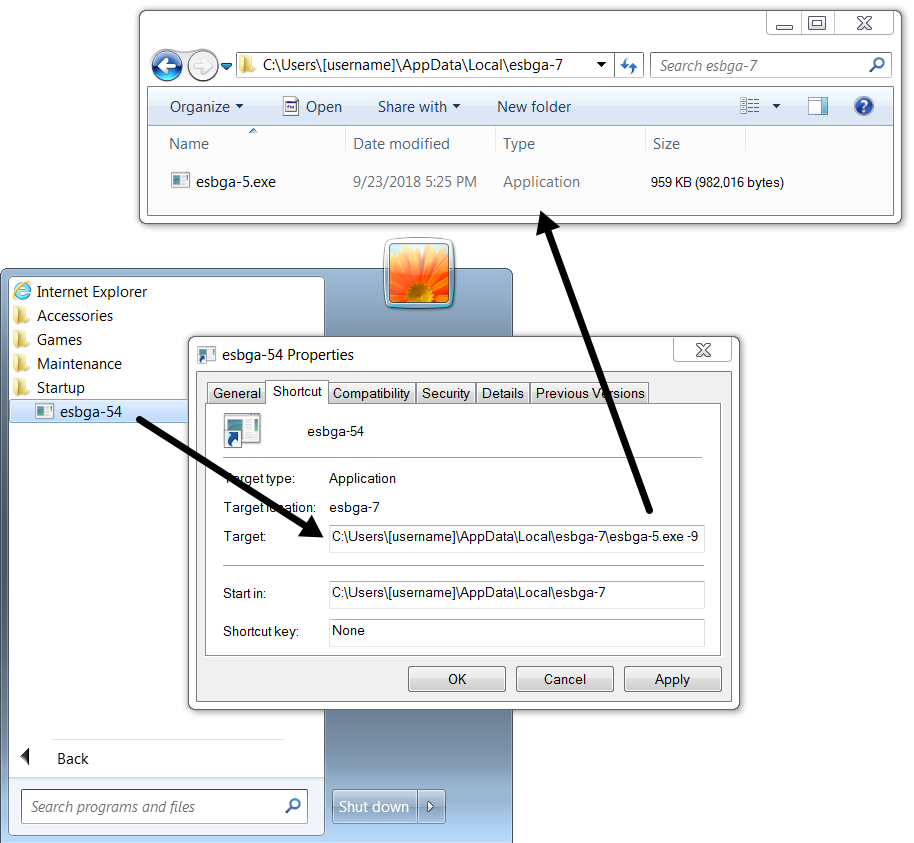
Shown above: Follow-up Nymaim executable (3 of 3) persistent through a shortcut in the Windows Startup folder.
Network traffic
Network traffic was typical for Nymaim infections I've recently seen. This malware spoofs legitimate domains carfax.com and zepter.com but uses different IP addresses based on DNS queries for other domains.
Nymaim uses Google DNS to query IP addresses on actual malicious domains. In most cases, IP addresses from those DNS queries are not directly used by the infected host for spoofed traffic to carfax.com and zepter.com. Ultimately, info returned by these Google DNS queries is used by Nymaim to calculate or determine the actual IP addresses used in its post-infection traffic. People should understand that Carfax and Zepter are not involved with this activity.
Of note, the infected Windows host also made DNS queries through Google DNS for google.com and microsoft.com.
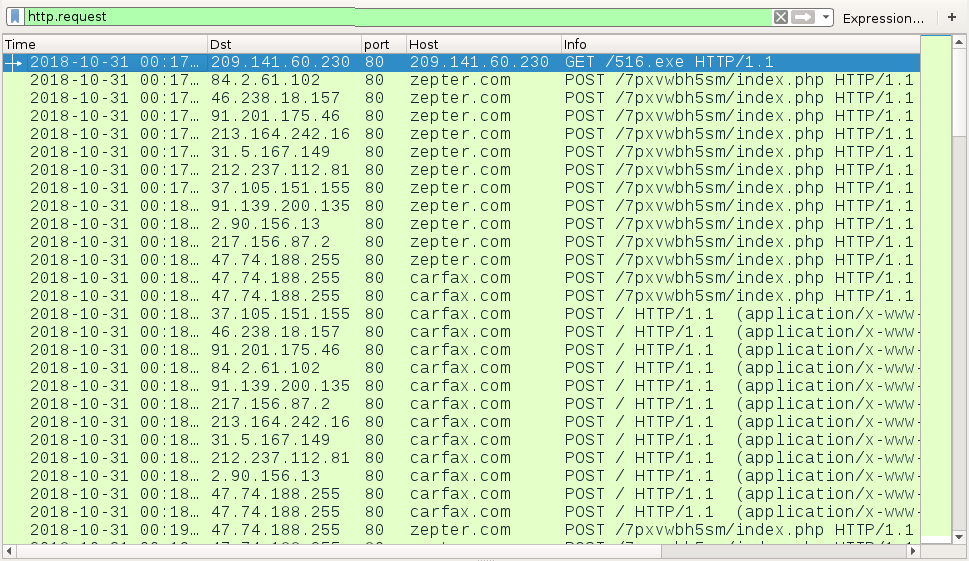
Shown above: HTTP traffic from the infection filtered in Wireshark.

Shown above: DNS traffic used by Nymaim to determine IP addresses used for spoofed traffic to carfax.com and zepter.com.
Indicators
Data on 10 malspam examples from 2018-10-27 through 2018-10-30:
- Received: from tonnocraft.com ([176.119.6.30])
- Received: from theductbusters.com ([176.119.6.45])
- Received: from kafadaroto.com ([176.119.6.162])
- Received: from parkinsonalberta.com ([176.119.6.113])
- Received: from theultimateadventurecentre.com ([176.119.6.37])
- Received: from font8.com ([176.119.6.233])
- Received: from getadsb.com ([176.119.6.220])
- Received: from madisonchevrolets.com ([176.119.6.150])
- Received: from fatalvr.com ([176.119.6.238])
- Received: from juegos4k.com ([176.119.6.165])
- From: Lavera Muck =?UTF-8?B?wqA=?= <noreply@tonnocraft.com>
- From: Kasey Rohloff =?UTF-8?B?wqA=?= <support@theductbusters.com>
- From: Doyle Bruce =?UTF-8?B?wqA=?= <mail@kafadaroto.com>
- From: Tamekia Ly =?UTF-8?B?wqA=?= <support@parkinsonalberta.com>
- From: Livia Westlake =?UTF-8?B?wqA=?= <help@theultimateadventurecentre.com>
- From: Mozelle Kalinowski =?UTF-8?B?wqA=?= <admin@font8.com>
- From: Arminda Fortson =?UTF-8?B?wqA=?= <noreply@getadsb.com>
- From: Alona Mcferren =?UTF-8?B?wqA=?= <admin@madisonchevrolets.com>
- From: Shona Dyck =?UTF-8?B?wqA=?= <sale@fatalvr.com>
- From: Livia Westlake =?UTF-8?B?wqA=?= <billing@juegos4k.com>
- Subject: Job
- Subject: application
- Subject: Regarding Job
- Subject: Hiring
- Subject: application
- Subject: Invoice Attached
- Subject: Invoice Attached
- Subject: Invoice Attached
- Subject: Invoice Attached
- Subject: Invoice Attached
- Attachment name: Lavera Muck Resume.doc
- Attachment name: Kasey Rohloff Resume.doc
- Attachment name: Doyle Bruce Resume.doc
- Attachment name: Tamekia Ly Resume.doc
- Attachment name: Livia Westlake Resume.doc
- Attachment name: invoice.doc
- Attachment name: invoice.doc
- Attachment name: invoice.doc
- Attachment name: invoice.doc
- Attachment name: invoice.doc
SHA256 hashes for the attached Word documents:
- 1a58bf2f30081aa41132131d2b31d8874fbfb31d23984d85b3292e8f74184e4e
- 2292617913ede3a9bb6917da9fec937318faefe03eb42c4c4cdd11f2890cf956
- 52a8247b00ce01f1069187395288fa0ee152ee4f845470f29a72097d54a3fe75
- 5567cddd66b5d37889e453fc392d594869479f0b65ef06c5829a03c56540136f
- 7984b53c53c6ae3ebf030503eafcdd406a1d1bb35a9aa6ac0a8c3be555f9aee1
- 83a29f4783027c4311978142488d07fb289d0576dca3c908fe65a7ab67d79c17
- a40814b438b7439a9e6540560a12d7ad3e24915fe37c3d267f0804b51d71022a
- d4a6fefa461a99e4ddebc3dc1fb4615bad399e46c9dac114702d4d7c5c774dd6
- d4ed432b7e0d6ebdc3b3aca4250566332100cd7c1980b28dbf6a69785b601797
- f46e5104862a86b971f3df6f162492efbda47c104230f2a5bebee4e0cd3f0793
Malware on the infected Windows host:
SHA256 hash: 45e387b429e6883f12c777b6b7be1c1239dc34115d882bce98afc80e7ad4b2b6
- File size: 1,392,640 bytes
- File type: PE32 executable (GUI) Intel 80386, for MS Windows
- File location: C:\Users\[username]\AppData\Local\Temp\qwerty2.exe
- Persistence mechanism: none (deletes itself after running)
- File description: Initial Nymaim executable downloaded by Word macro
SHA256 hash: 11b0c2732e0bcbfb6d7bbf37180344ec0b1eafd58d73fe65278b69cfb981daf1
- File size: 982,016 bytes
- File type: PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows
- File location: C:\ProgramData\algebra-1\algebra-2.exe
- Persistence mechanism: Windows Registry entry
- Entry: HKCU\Software\Microsoft\Windows NT\CurrentVersion\Winlogon - shell
- Command: C:\ProgramData\algebra-1\algebra-2.exe -q2
- File description: Nymaim malware persistent on the infected Windows host (1 of 3)
SHA256 hash: 524f22a1582a03defca57913e6a55d5989c4fc1330163efce284ec5eced983ca
- File size: 1,068,544 bytes
- File type: PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows
- File location: C:\ProgramData\bending-51\bending-2.exe
- Persistence mechanism: Windows Registry entry
- Entry: HKCU\Software\Microsoft\Windows\CurrentVersion\Run - bending-5
- Command: C:\ProgramData\bending-51\bending-2.exe -k4
- File description: Nymaim malware persistent on the infected Windows host (2 of 3)
SHA256 hash: 8d10d226e723dd9ad8993e4710d5913078d83bae6870b61aa70bafaefbe70c49
- File size: 982,016 bytes
- File type: PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows
- File location: C:\Users\[username]\AppData\Local\esbga-7\esbga-5.exe
- Persistence mechanism: Windows shortcut in the Startup folder
- Command: C:\Users\[username]\AppData\Local\esbga-7\esbga-5.exe -9
- File description: Nymaim malware persistent on the infected Windows host (3 of 3)
Traffic from an infected Windows host:
- 209.141.60.230 port 80 - 209.141.60.230 - GET /516.exe
- 2.90.156.13 port 80 - zepter.com - POST /7pxvwbh5sm/index.php
- 2.90.156.13 port 80 - carfax.com - POST /
- 31.5.167.149 port 80 - zepter.com - POST /7pxvwbh5sm/index.php
- 31.5.167.149 port 80 - carfax.com - POST /
- 37.105.151.155 port 80 - zepter.com - POST /7pxvwbh5sm/index.php
- 37.105.151.155 port 80 - carfax.com - POST /
- 46.238.18.157 port 80 - zepter.com - POST /7pxvwbh5sm/index.php
- 46.238.18.157 port 80 - carfax.com - POST /
- 47.74.188.255 port 80 - carfax.com - POST /7pxvwbh5sm/index.php
- 47.74.188.255 port 80 - zepter.com - POST /7pxvwbh5sm/index.php
- 47.74.188.255 port 80 - carfax.com - POST /
- 84.2.61.102 port 80 - zepter.com - POST /7pxvwbh5sm/index.php
- 84.2.61.102 port 80 - carfax.com - POST /
- 91.139.200.135 port 80 - zepter.com - POST /7pxvwbh5sm/index.php
- 91.139.200.135 port 80 - carfax.com - POST /
- 91.201.175.46 port 80 - zepter.com - POST /7pxvwbh5sm/index.php
- 91.201.175.46 port 80 - carfax.com - POST /
- 212.237.112.81 port 80 - zepter.com - POST /7pxvwbh5sm/index.php
- 212.237.112.81 port 80 - carfax.com - POST /
- 213.164.242.16 port 80 - zepter.com - POST /7pxvwbh5sm/index.php
- 213.164.242.16 port 80 - carfax.com - POST /
- 217.156.87.2 port 80 - zepter.com - POST /7pxvwbh5sm/index.php
- 217.156.87.2 port 80 - carfax.com - POST /
- DNS query to Google DNS for: microsoft.com
- DNS query to Google DNS for: google.com
- DNS query to Google DNS for: shetyiosnf.com
- DNS query to Google DNS for: deligvsiogsd.com
Final words
Email examples, pcap, and malware associated with today's diary can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments