New Campaign Using Old Equation Editor Vulnerability
Yesterday, I found a phishing sample that looked interesting:
From: sales@tjzxchem[.]com To: me Subject: RE: Re: Proforma Invoice INV 075 2018-19 ’08 Reply-To: exports.sonyaceramics@gmail[.]com Dear Respected Sir, Please find the proforma invoice attached. Kindly check and confirm. Material will be dispatched with 5-7 working days. Regards, Armit Thakkar Head Sales Development Technovinyl Polymers India Ltd. Filix 901 -C1, 9th Floor, Opp. Asian Paints, L.B.S.Road, Bhandup (W), Mumbai - 400 078, India Mob: +91-9322266143 Ph: +91-22-61721888
There was an attached document "INV 075 2018-19.xlsx" (SHA256: abbdd98106284eb83582fa08e3452cf43e22edde9e86ffb8e9386c8e97440624) with a score of 28/60 on VT[1]. When I opened the document, it presented a nice picture asking the victim to disable the default Office security feature:
But I also received an error message from Office about an application that could not be opened. Excel tried to spawn a new process:
EQNEDT32.EXE -Embedding
Google this and you will discover that the “Equation Editor” is an Office tool that helps to write cool equations:
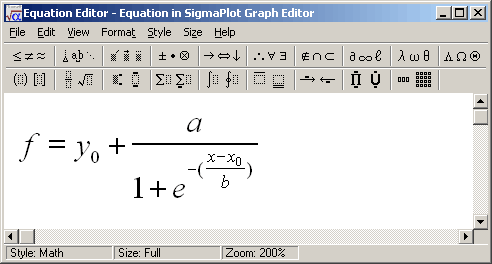
This tool is very useful for mathematicians or engineers who must add complex equations in their documents but who install this in a malware analysis sandbox? This is a nice way to evade automated analysis. Once my sandbox fixed and the Equation Editor installed, I re-opened the document and, immediately, the Equation Editor was launched. It downloaded and executed the following payload:
http://216.170.114.195/klonnx.exe
(SHA256: 7fe5f06d04390dd22e1065491c43c33dbebd03400826897c814db8d10469a8eb - VT score: 41/69).
Once executed, the malware copies itself into %APPDATA%\Roaming\svhost\svhost.exe
It schedules a task via schtasks.exe:
schtasks.exe /create /sc MINUTE /tn svhost.exe /MO 1 /tr "C:\Users\admin\AppData\Roaming\svhost\svhost.exe\
But also creates a shortcut in: %APPDATA%\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\svhost.exe.url:
[InternetShortcut] URL=file:///C:/Users/admin/AppData/Roaming/svhost/svhost.exe
The malware is a Razy trojan and it phones home to datalogsbackups[.]hopto[.]org (91.192.100.20) to port 2233.
The vulnerability exploited by this campaign is not new. It abuses the CVE-2017-11882 present in eqnedt32.exe[2].
[1] https://www.virustotal.com/#/file/abbdd98106284eb83582fa08e3452cf43e22edde9e86ffb8e9386c8e97440624/detection
[2] https://borncity.com/win/2017/11/28/hacker-are-misusing-cve-2017-11882-in-office-eqnedt32-exe/
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
"OG" Tools Remain Valuable
For vendors, the cybersecurity landscape is a nice place to make a very lucrative business. New solutions and tools are released every day and promise you to easily detect malicious activities on your networks. And it's a recurring story. Once they have been implemented by many customers, vendors come back again with new version flagged as “2.0”, “NG” or “Next Generation”. Is it really useful or just a hype? I won’t start the debate but keep in mind that good old tools and protocols remain still very valuable today.
I was contacted by a company which had a security incident. Apparently, they suffer from an ongoing data leak and customers’ information are leaked to the competition. If you are working in this field and you need to investigate quickly, you probably already faced the following situation. I visited them and started to grab details about the infrastructure, the architecture and the key point: logs or any kind of data that could help to spot the source of the leak. You realise quickly that nothing or only a low amount of information is available. A good point, they had a bunch of logs extracted from the local resolver. Based on the DNS queries performed by the hosts, we were able to spot a compromised one. But not all of them were using the local resolver (yes, it was possible to use any public DNS) and some hosts might communicate directly with IP addresses…
My next question to them was: "Do you know the NetFfow protocol?”. No, they did not. NetFlow[1] is a very old protocol developed by Cisco in 1996(!). At the origin, it was developed for accounting reasons when the Internet was slow and subscription plans based on the amount of traffic you used (I’m feeling old now). A Cisco router/switch which has NetFlow enable (called an exporter) send UDP packets to a Netflow collector with the following details (resumed):
- timestamp (flow start)
- duration
- protocol
- source IP /port
- destination IP / port
- number of packets
- number of bytes
This information is very useful to spot malicious activity! Once you started to collect Netflow data you can easily generate stats like:
- Top speakers on the network
- Top destinations
- Top protocols (based on the port)
- Hosts talking to suspicious hosts (ex: located in a country where you don’t have business thanks to the GeoIP)
- Hosts talking a regular interval with a low amount of traffic (typically systems phoning home to their C2)
- Hosts starting to talk at night
- And many more...
Compared to a full packet capture, you won't see the traffic payload but the amount of data is very low and you don't need a very powerful computer to process them.
To collect NetFlow data, you just have to install a collector (nfdump[2] is the most known)
# apt-get install nfdump # vi /etc/default/nfdump (change the value of nfcapd_start to “yes”) # service nfdump start
Now, connect to your Cisco device and enable NetFlow:
Router(config)# ip flow-export <collector> <port>
The default port is 9996 and <collector> is the IP/FQDN of the server running the nfcapd daemon. Now, have a look at the nfdump command to extract interesting stats from the captured data. Note that many tools are able to digest NetFlow data. Logstash from the ELK stack is a good example[3]. This setup can be deployed in a few minutes and will give you a nice visibility of your network traffic to quickly spot a malicious behaviour.
Conclusion: "Old Generation" tools remain valuable when you need to investigate security incidents.
[1] https://www.cisco.com/c/en/us/products/ios-nx-os-software/ios-netflow/index.html
[2] https://github.com/phaag/nfdump
[3] https://www.elastic.co/guide/en/logstash/current/netflow-module.html
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key


Comments