Quick and dirty generic listener
From time to time, we see spikes on some odd port in our data and we want to figure out what the bad guys are trying to do. Even just capturing the first packet or two of data can help us figure out what they are looking for, even if we don't initially give the proper response to capture the entire exploit. Sometimes, we can get lucky and the whole exploit is a single packet (yes, I remember SQL Slammer very well). It seems like everyone has their favorite way to capture the traffic, but they all seem to have weaknesses. So, I figured I'd ask you, our loyal readers, for your favorites and any pros and cons to your favorite method. Do you put up a netcat listener (in a loop, so it continues to listen after the first connection attempt)? Do you use socat? Do you have a favorite perl or python (or bash or powershell) script? In my Truman-based automated malware analysis environment, I simply redirected every port to my IRC server perl script, but that isn't appropriate if we're actually facing the internet. So, let me know what you think.
---------------
Jim Clausing, GIAC GSE #26
jclausing --at-- isc [dot] sans (dot) edu
I'll be teaching FOR610: Reverse-Engineering Malware in Columbia, MD in June (https://www.sans.org/community/event/for610-columbia-jun-2017)
and in Ottawa, ON in Sep (https://www.sans.org/community/event/for610-ottawa-sep-2017)
Microsoft Patch Tuesday, or is that "Patch Next Tuesday"? - Flash Player RCE patched today
Microsoft released the patch for MS017-005 today, to patch a remote code execution vulnerability in Windows 8.1, Windows Server 2012, Windows Server 2012 R2, Windows RT 8.1, Windows 10, and Windows Server 2016. The MS Bulletin is posted here: https://technet.microsoft.com/en-us/library/security/MS17-005, but is not yet posted on the main feed (https://technet.microsoft.com/en-us/security/bulletins.aspx)
The matching Adobe technote is APSB17-04, found here: https://helpx.adobe.com/security/products/flash-player/apsb17-04.html
This is a remote code execution issue, so it's a definite "PATCH NOW" issue.
** Update: the Microsoft feed has caught up now with the patch release, https://technet.microsoft.com/en-us/security/bulletins.aspx is now correct.
===============
Rob VandenBrink
Compugen
2 Apple Updates Today as Well - GarageBand and Logic Pro X
GarageBand 10.1.6 is released today, fixing an arbitrary code execution bug in Yosemite 10.10 and later (CVE-2017-2374)
There's also second patch for Logic Pro X 10.3.1. Unfortunately, it's got the text for the Garageband patch in it's notes, so it's not clear what is fixed in this update.
As always, all Apple security patches are hosted here: https://support.apple.com/kb/HT201222
===============
Rob VandenBrink
Compugen
Investigating Off-Premise Wireless Behaviour (or, "I Know What You Connected To")
Last week, I was working with a client on a web-filtering solution, using one of their organization's laptops. We happened to notice the long-long-LONG list of SSIDs that were on this machine, may of them open SSIDs. The host we were looking at had the default "dlink" and "linksys" SSIDs as auto-connect, so not a great situation. Coincidentally, this was the same day Xavier posted his diary about collecting this same information (the ssid list) from live machines (https://isc.sans.edu/forums/diary/How+was+your+stay+at+the+Hotel+La+Playa/22069/). It really seems like people still have a pathological need to connect up to free WiFi.
I got to thinking about how to collect this information in an Active Directory domain using PowerShell. It's quite easy for Windows 10, but not so much for Windows 7 clients. For the "older environment" case, I ended up falling back to:
netsh wlan show profiles to get the list of wireless profiles
netsh wlan show profiles name=PROFILENAME to get the details for the profile "PROFILENAME"
Combine that up with psexec (because psexec *always* works - well, almost always), and some text manipulation, and you have the code below.
Yes, I do know that this could have been done by pulling everything out of the registry, but in this case perfect is the enemy of "done" - I had a few clients who wanted this done quickly, and this approach got it done in that "quickly" time frame.
The resulting script will list all wireless profiles across an AD domain. I did have a "test connection" line in there, but enough organizations have ping disabled now that I took that out.
How to use this information? For most organizations, this is a chance to do some outreach, some end-user education about safer computing. In most cases, this means that we recommend that they tether to their phone rather than connect to random free SSIDs.
In a more security conscious environment, say if it's a bank or if clearances are involved, what this can be used for is as a simple audit. In higher security shops, it's more common to see Group Policy be used to say "only this short list of SSIDs are permitted", where the list is the organizations' "real" wireless networks, as well as (in some cases) a pre-configured cell phone "tethered" network.
As always, let us know how this code works out. There are a few errors I'm still trying to suppress, and it can take quite a long time to run this, but the clients that I've used this with have gotten good use out of the information.
The code (recommend PowerShell 4.0 or better):
$nodenets = @()
$domainmembers = get-adcomputer -filter *
foreach ($node in $domainmembers) {
$netlist = iex ("./psexec /accepteula \\"+$node.name +" netsh wlan show profiles") 2>./a | Select-String -Pattern ": "
if(($netlist -like "*was not found*") -or ($netlist.length -eq 0)) { write-host "No Wireless on host " $node.name }
else {
write-host "Assessing Wireless on host " $node.name
foreach ($net in $netlist) {
[console]::write(".")
$netprf = ($net -split(": "))[1]
$cmd = "./psexec /accepteula \\"+$node.name +" netsh wlan show profiles name="+ "`'"+$netprf+"`'"
$netparmlist = iex $cmd 2>./a
$netparmlist2 = $netparmlist | select-string -pattern ": " | select-string -pattern "Applied" -NotMatch | select-string -pattern "Profile" -NotMatch
$x = New-Object psobject
$x | add-member -membertype NoteProperty -name "Node" -Value $node.name
foreach($parm in $netparmlist2) {
$t1 = $parm -split ": "
$x | add-member –membertype NoteProperty –name ($t1[0].trim(" ")) –Value ($t1[1]) ;
}
$nodenets += $x
}
}
}
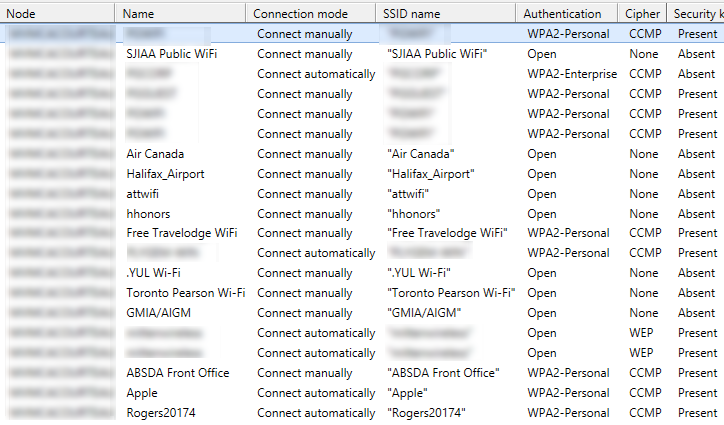
$nodenets | select Node, Name, "Connection Mode", "SSID Name", Authentication, Cipher, "Security Key" | Out-GridView
(watch for updates over the next few days at https://github.com/robvandenbrink/opw )
The output (you could just as easily output to CSV for use in Excel):
===============
Rob VandenBrink
Compugen



Comments