Angler Exploit Kit - Recent Traffic Patterns
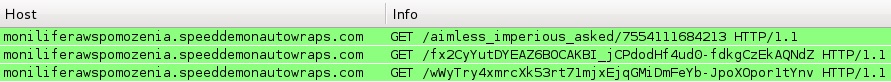
Angler exploit kit (EK) has changed URL patterns (again) during the past month. I infected a Windows host so we can take a closer look. Let's see what Angler has been up to. First, here are the Angler EK URL patterns noted in traffic from an infected host:
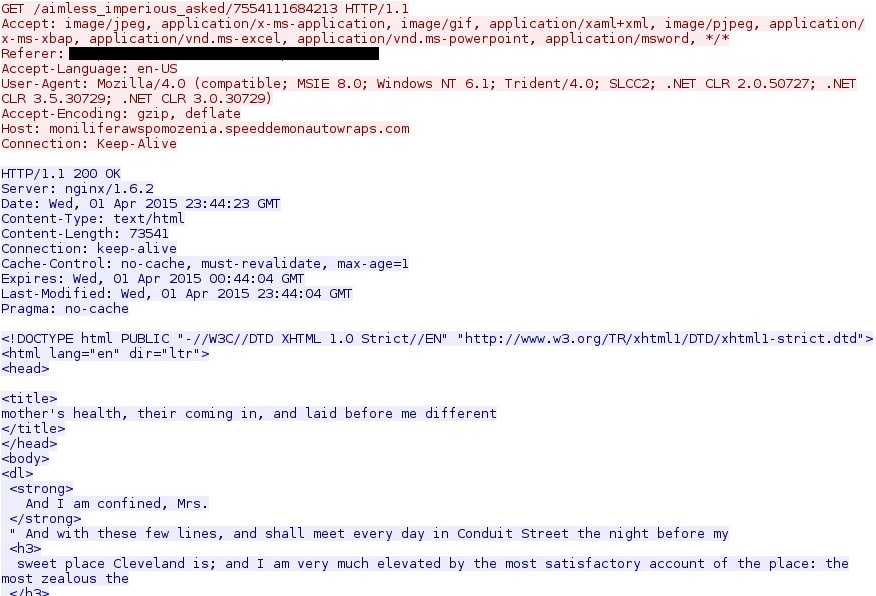
The domains and URLs change frequently, and I saw several different URL patterns while using different Windows hosts to get a full infection chain. Below is an image of the landing page URL:
Further down in the HTML, you can see some of the obfuscated code designed to set off an infection chain of events.
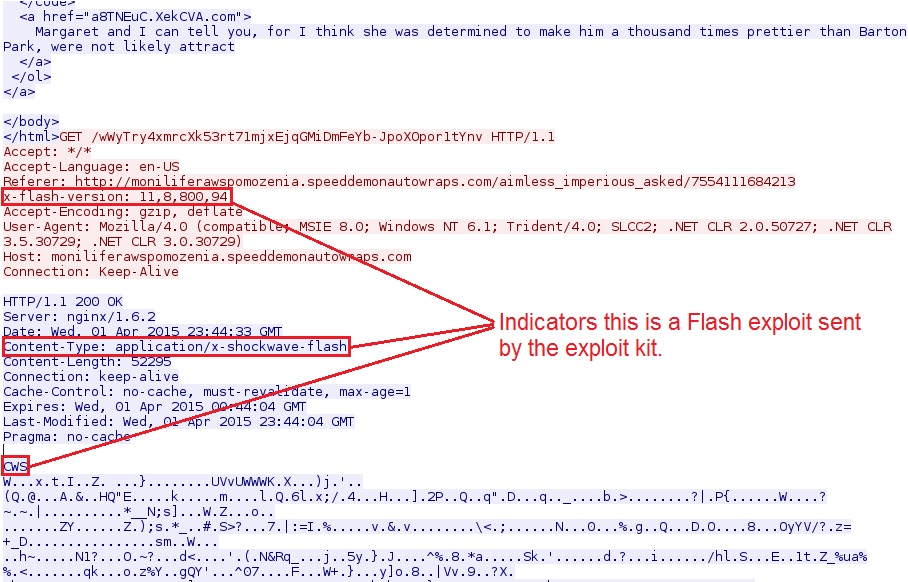
Next, Angler EK sends a Flash exploit:
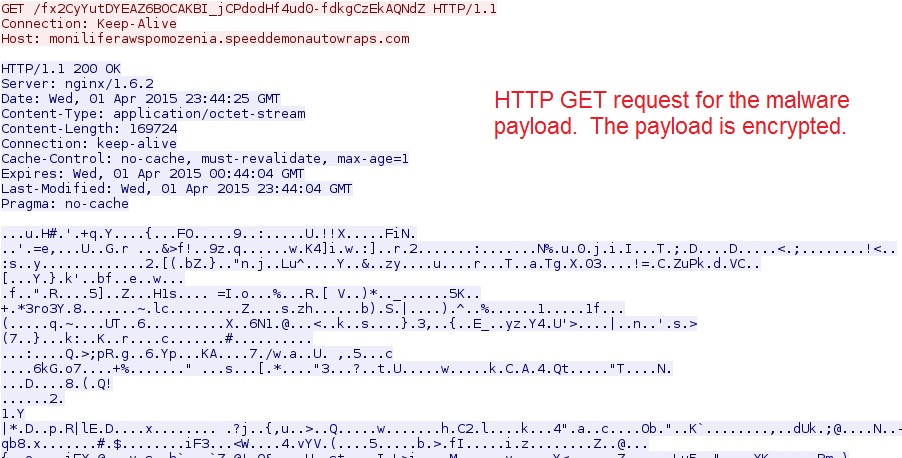
And finally, we have the HTTP GET request Angler EK used to send the malware payload:
The malware payload is encrypted. As early as August 2014, Angler EK has been using a “file-less” infection method, so it won’t write this payload to the disk [1].
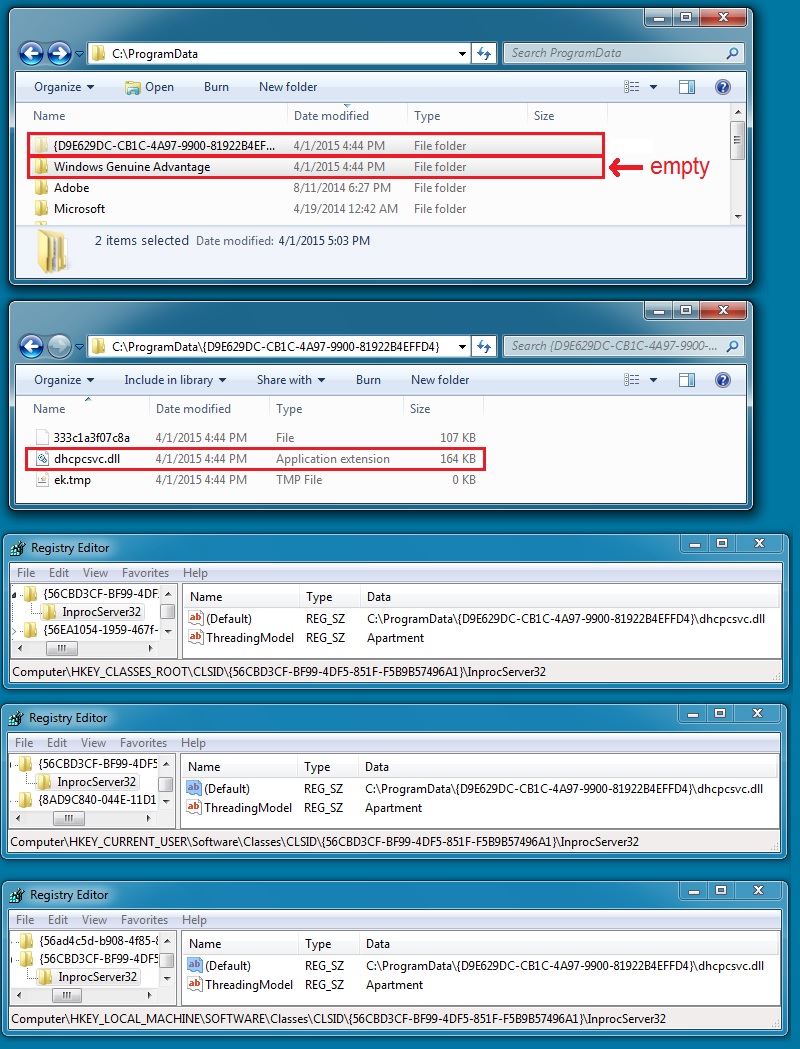
However, artifacts are left behind after the infection. Why? The infected host needs to keep the malware persistent on the system after a reboot. Below are some of the files, directories, and registry keys used to keep the malware persistent on this infected host:
The persistent malware is usually named after a legitimate system file, in this case: dhcpcsv.dll
You can find a copy of this malicious file at: https://malwr.com/analysis/ZjIxOTViNjM2N2YzNGQ1YWI1NzNlYjkzZjI0ZTEyMjQ/
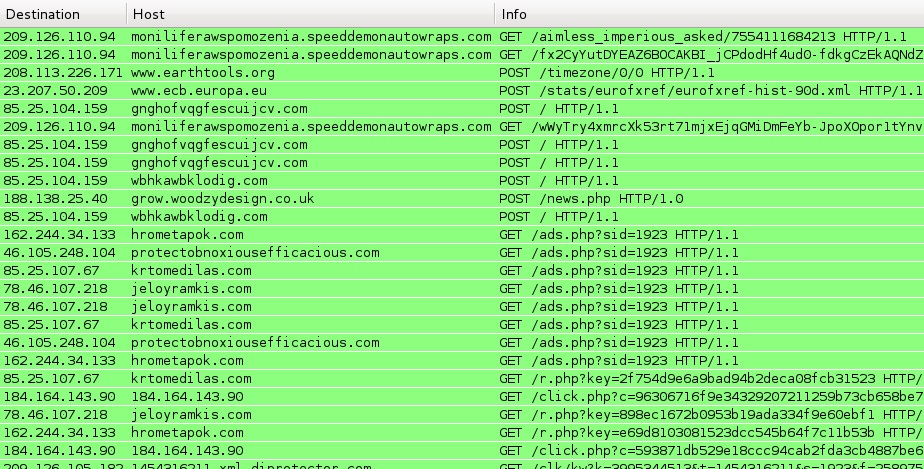
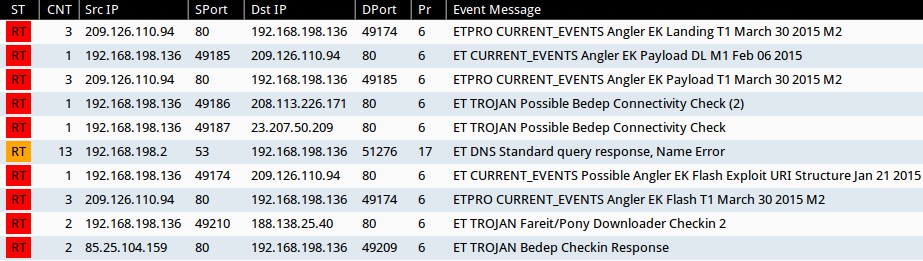
What about traffic from the infected host? Below is a screenshot of the Angler EK and post-infection traffic from Wireshark:
Using Security Onion to monitor the infection traffic, you’ll find alerts typical for Angler EK followed by Bedep. Microsoft has an entry in the company’s threat encyclopedia that describes Bedep, and it matches the patterns seen during today’s infection traffic [2].
I have a similar example of this Angler/Bedep traffic from 2015-04-01 available at: http://malware-traffic-analysis.net/2015/04/01/index.html
Keep monitoring your networks. Compromised websites are everywhere, and this type of traffic happens more often than you think!
---
Brad Duncan, Security Researcher at Rackspace
Blog: www.malware-traffic-analysis.net - Twitter: @malware_traffic
References:
[1] http://malware.dontneedcoffee.com/2014/08/angler-ek-now-capable-of-fileless.html
[2] http://www.microsoft.com/security/portal/threat/encyclopedia/entry.aspx?Name=Win32/Bedep#tab=2


Comments