Port 0 DDOS
Following on the stories of amplification DDOS attacks using Chargen, and stories of "booters" via Brian Kreb's, I am watching with interest the increase in port 0 amplification DDOS attacks.
Typically these are relatively short duration, 15 to 30 minute, attacks aimed at a residential IP address and my speculation is that these are targeted at "booting" participants in RPG games. On the networks I have access to these are usually in the 300 Mbps to 2.0 Gbps range. The volume would most certainly be very debilitating for the target, and sometimes their neighbors, but for the most part doesn't cause overall problems for the network. The sources are very diverse.
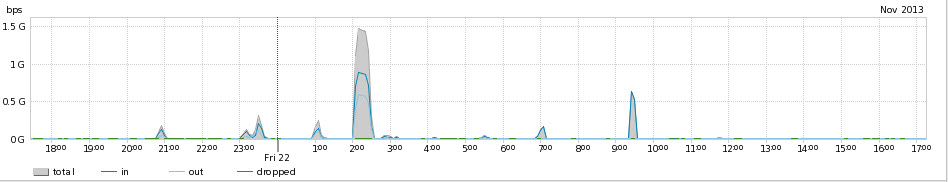
Unfortunately I do not have an ability to get packets of any of these attacks, but I am questioning whether this traffic is actually destined for port 0 or if it is actually fragmentation attacks that are being interpreted as source port 0 traffic.
Jim Macleod at lovemytool.com does an excellent job of describing what I am suspecting.
If anyone has packets available from one of these attacks, I would love to review them.
-- Rick Wanner MSISE - rwanner at isc dot sans dot edu - http://namedeplume.blogspot.com/ - Twitter:namedeplume (Protected)
Apple not updating OS X Mountain Lion?
Larry Seltzer over at ZDNet has noticed that since the release of OS X Mavericks that Apple has stopped updating OS X Mountain Lion. Although Apple is not forthcoming with the reasons for this, it appears this is a departure from past behavior.
-- Rick Wanner MSISE - rwanner at isc dot sans dot edu - http://namedeplume.blogspot.com/ - Twitter:namedeplume (Protected)
Tales of Password Reuse
As a security practitioner I try really hard to drink the Kool-Aid, in other words practice what I preach. I have been a strong advocate, for well over a decade, of avoiding password reuse. There is one consolation I personally made to password reuse. For years I used one "throwaway" password for services where I didn't care about the account. You know those annoying sites that make you sign up just to access some mundane capability. In my case, my throwaway password is still a high quality password, but it is used on literally dozens of sites where there is no data of value, like Adobe. After the Adobe breach I changed my throwaway password on as many sites as I could remember using it at, and developed a better methodology for passwords on these sites (i.e. no more reuse).
Apparently I missed one. Yesterday I got an email from Evernote telling me that I had used the same password at Evernote that I had used at Adobe. The Evernote account probably got my throwaway password before I realized the value of the Evernote service. I now use Evernote nearly every day from my mobile devices; where I don't get prompted for the credentials; but never log into it over the web, so I didn't remember what the password was set to.
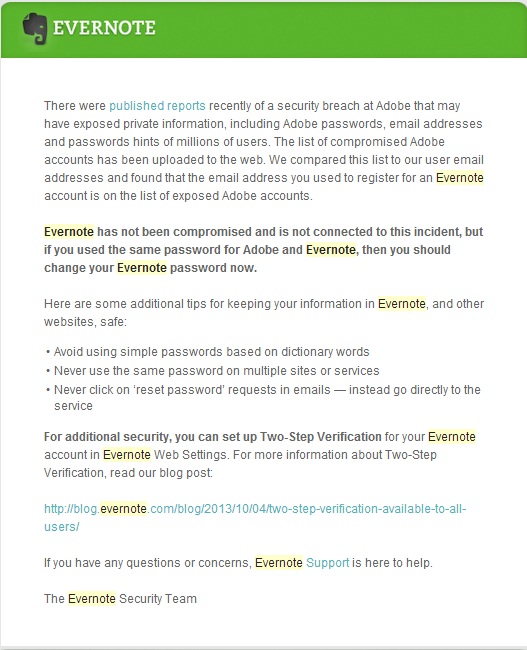
Needless to say I quickly changed my Evernote password and enabled Evernote's two-step authentication.
Shortly later an ISC reader forwarded a The Register article about a brute force authentication attack against github. While there aren't a lot of technical details in the article, this attack is interesting because it is a relatively slow attack from over 40,000 IP addresses, obviously designed to reduce the likelihood of any anti-brute-forcing controls kicking in.
"These addresses were used to slowly brute force weak passwords or passwords used on multiple sites. We are working on additional rate-limiting measures to address this". Suggesting that this was not your typical brute force employing obvious userids and incredibly inane passwords, but a targeted attack against password reuse.
The article also goes on to lament; "It strikes us that GitHub's recent bout of probing may stem from crackers using the 38 million user details that were sucked out of Adobe recently to check for duplicate logins on other sites."
Guess I will be looking at all my passwords again, including the ones used by my mobile devices!
-- Rick Wanner - rwanner at isc dot sans dot edu - http://namedeplume.blogspot.com/ - Twitter:namedeplume (Protected)


Comments