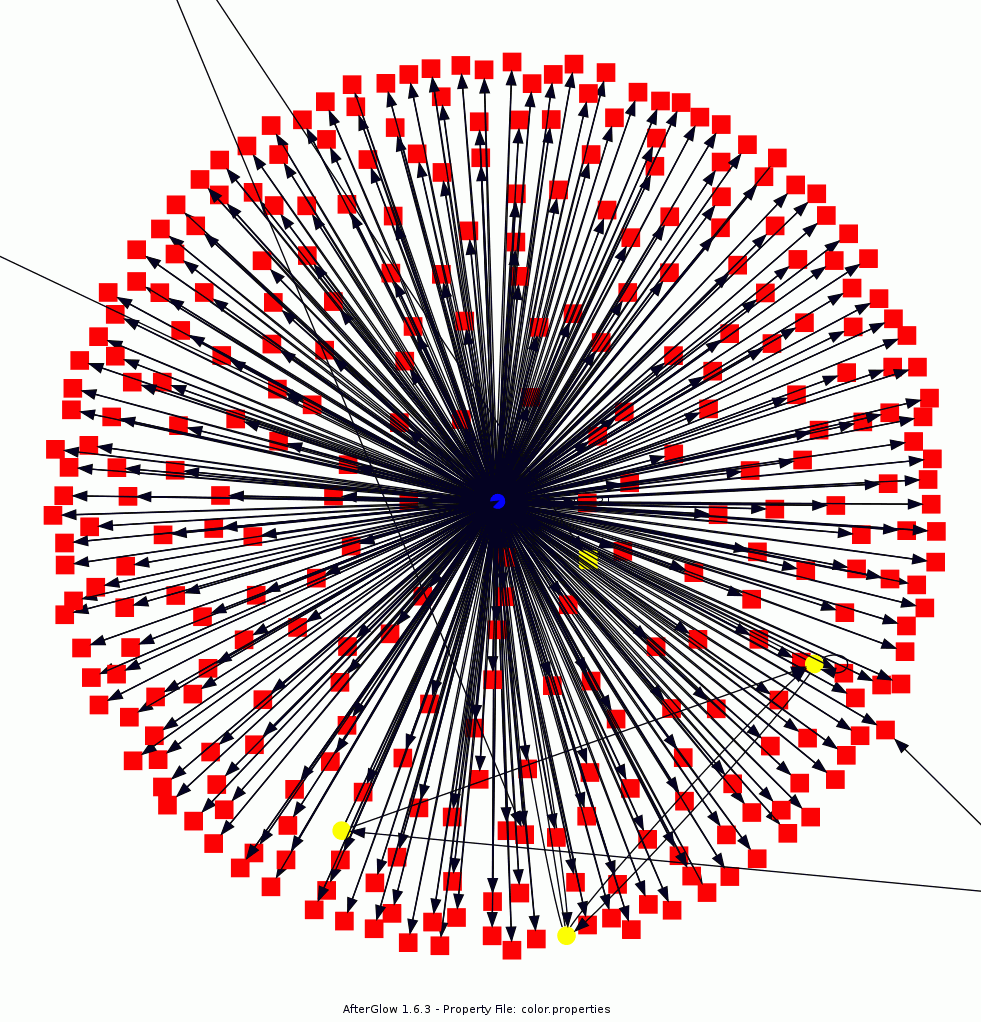
Celebrating 4th of July With a Malware PCAP Visualization
It's been exactly five years since the ISC Diary discussed the Storm botnet and fireworks.exe. What better way to celebrate America's birthday with another fireworks-like visualization. Much has changed in five years, including malware techniques, and the venerable AfterGlow visualization tool set, but some things remain consistent. Malware still sucks, sometimes it's really chatty, and when it is, the resulting PCAP can be rendered as a great picture. Raffy Marty's AfterGlow now includes a cloud version (like I said, much has changed in five years), but I rolled this graphic with a ZeroAccess sample and AfterGlow with Argus on an Ubuntu VM. An excellent analysis of this sample is provided by Contagio, so I'll spare you the details. Using the PCAP provided in that post, I executed argus -r zeroaccess.pcap -w - | ra -r - -nn -s saddr daddr -c, | perl afterglow.pl -c color.properties | neato -Tgif -o zeroaccess.gif. To simplify textually, the blue dot in the middle is our hapless victim system and the red nodes are all the evil minions it's conversing with.
With the utmost respect, and sincere apologies to the Honorable Mr. Lincoln: We here highly resolve that these samples shall not have been analyzed in vain — that this Diary, under the World Wide Web, shall promote a new birth of security — and that an Internet of the people, by the people, for the people, shall not perish from the earth.
Happy 4th of July!!


Comments