Guest Diary: Dylan Johnson - A week in the life of some Perimeter Firewalls
[Guest Diary: Dylan Johnson BSc.CISSP] [A week in the life of some Perimeter Firewalls]
I hope the title of this blog doesn’t appear a dry and dull topic because a week in the life of an Internet facing firewall is anything but dull.
This is just a short blog detailing an interesting piece of research aimed at promoting situational awareness in relation to the threat from the internet.
Perimeter firewalls are the main barriers protecting you from the Internet, should these be misconfigured either maliciously or accidentally, what would you be exposed too?
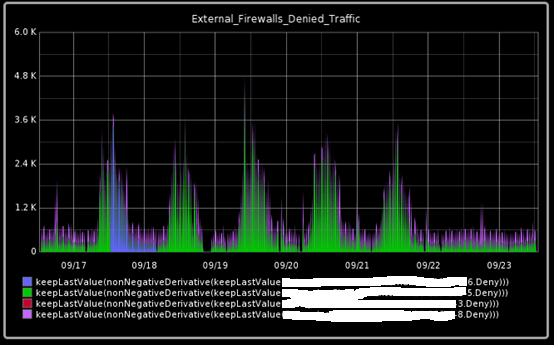
Graph 1 below shows the amount of dropped traffic (Axis-Y) against time (Axis-X). You can see at peak periods the number of dropped connections is 3.6k over a 30 minute period.
Graph 1
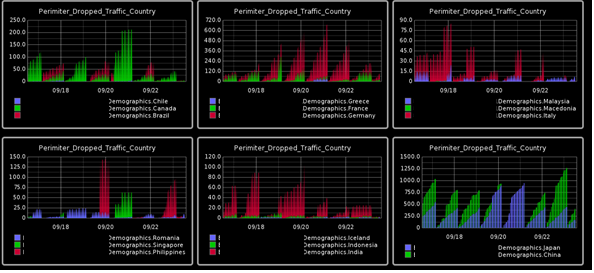
The summary graphs below drill into more of the detail present in the audit data from the firewalls and present this in the same format as graph 1 however the different colors highlight the traffics country of origin.
If you look at the bottom right graph you can see traffic from China with a peak drop rate of 1250 connections every 30 minutes. Also notice the erratic trends within the graph, bottom right.
Graph 2
So as you can see firewalls are constantly busy fighting off a constant slew of malicious traffic. A lot of the traffic dropped may be reconnaissance or to make an analogy someone checking the quality of your locks, windows and doors, however they can still post via the letter box!
To explain the firewall letter box analogy, firewalls wouldn’t be much use if they blocked absolutely everything, if that was the case why would we even need a network connection to the internet at all? Perimeter firewalls need to pass certain types of traffic to applications, its then up to the applications to deal with the traffic profile we saw previously in graph 2 i.e all that traffic from China and the other countries.
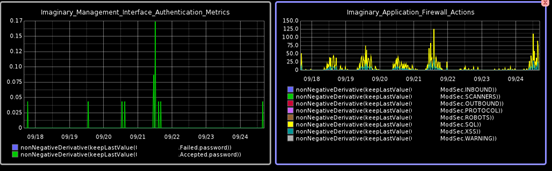
Graph 3 below shows actions taken by an application firewall as you can see there is a constant slew of SQLi (SQL Injection) and XSS (Cross Site Scripting) attacks. These attacks reach the webserver perhaps because there is no security control upstream capable of understanding and dealing with Layer 7 or Application Layer traffic. A traditional firewall operates at layers 3(Network Layer) and layers 4(Transport Layer) they are often oblivious to what is happening at layer 7 they only care about getting the traffic to its intended destination.
Graph 3
So as you can see you are indeed connected to the global internet and are being probed by traffic from the four corners of the known world, from Amsterdam to Zimbabwe.
The purpose of this blog was to demonstrate that you may be in a quiet and relatively tranquil part of the world but you are connected to a network that remains mainly un-policed and carry’s a very real and persistent threat as I hope you can see from the data and explanation presented in this blog. Make sure you understand the threat, monitor it and ensure you have controls in place to keep it out.
Post suggestions or comments in the section below or send us any questions or comments in the contact form on https://isc.sans.edu/contact.html#contact-form
--
Adam Swanger, Web Developer (GWEB, GWAPT)
Internet Storm Center https://isc.sans.edu


Comments