Joomla (and WordPress) Bulk Exploit Going on
We've gotten some reports and discussion around many Joomla (and some WordPress) sites exploited and hosting IFRAMES pointing to bad places. We'll get to the downloaded in a second, but the interesting thing to note is that it doesn't seem to be a scanner exploiting one vulnerability but some tool that's basically firing a bunch of Joomla and Wordpress exploits at a given server and hoping something hits. We'd like PCAPs or weblogs if you're seeing something similar in your environment. Right now it seems the biggest pain is around Joomla users, particularly with extensions which greatly increase the vulnerability footprint and the one thing helping WordPress is the really nice feature of 1-button upgrades (and upgrades which don't tend to break your website).
The IFRAMES seem to have rapidly changing FQDN's that it is using but the common element is /nightend.cgi?8. Two of the bad IPs that seem to be frequent offenders are 78.157.192.72 and 108.174.52.38. Ultimately it pulls FakeAV software to do it's badness.
Mediation is your typical advice, make sure all your software is up-to-date and kept that way on a regular basis.
If you have weblogs (particularly verbose ones), I would be interested in seeing them. The tool being used is of interest to me.
--
John Bambenek
bambenek \at\ gmail /dot/ com
Bambenek Consulting
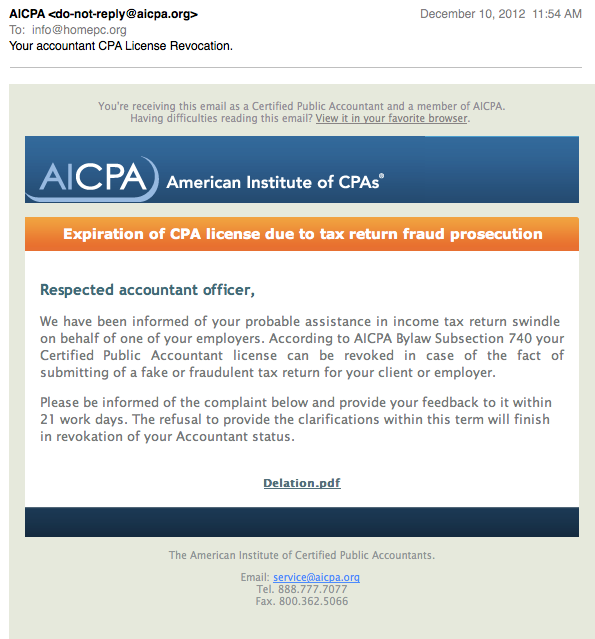
Your CPA License has not been revoked
I have been seeing some e-mails hitting my spam traps today, warning me of my revoked CPA license. No, I am not a CPA. But the e-mails are reasonably well done, so I do think some CPAs may fall for them. At least they got the graphics nice and pretty, but the text could be better worded.
The only clickable link is the "Delation.pdf" (maye that should be deletion?). Upon clicking the link, we are send on the usual malware redirect loop:
The first stop is
httx://tesorogroup. com/components/com_ag_google_analytics2/taxfraudalert.html
It includes javascript and meta tag redirects to
httx://eaglepointecondo. co/ detects /denouncement-reports.php
which will test our browser for vulnerable plugins and try to run a java applet. Looks all very "standard". You may want to check your DNS server logs for anybody resolving tesorogroup.com or eaglepointecondo.co . The two host currently resolve to 64.15.152.49 and 59.57.247.185 respectively.
Wepawet does a nice job analysing the obfuscated javascript:
http://wepawet.iseclab.org/view.php?hash=c390cd570069882395e24b7a30abbe64&t=1355160668&type=js
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter


Comments