Fake AV Bingo
Can you guess which domains the crooks behind the Fake Anti-Virus Scam are going to use next ? Well, neither can we. But for several weeks now, they are hosting a lot of their bad stuff out of 91.213.29.66, geo-located in lovely Russia (where else?).
A passive DNS collector like BFK/RUS-CERT can help to turn this IP address back into the domain names currently in use. Here's an excerpt from the resulting list, all in all 165 domains of badness.
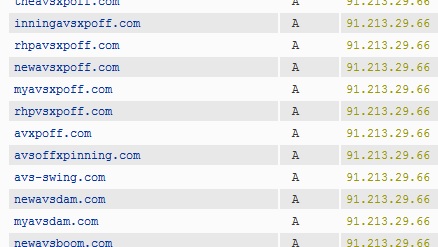
Several of these domains were "found" by our readers via the poisoned Google image searches that we reported earlier this month, and also via malicious advertisements embedded in perfectly benign web pages.
If you Apple Mac users now feel all safe, think again! As we mentioned earlier, Fake AV has made its appearance on Macs, where naive automatic download-and-run default settings in browsers still are common, and where "MacDefender" and its expected numerous successors and variants are likely to become as "successful" for the bad guys as their Windows version has been for years.
Fake AV Bingo? The only winning move is not to play.


Comments