H went down.
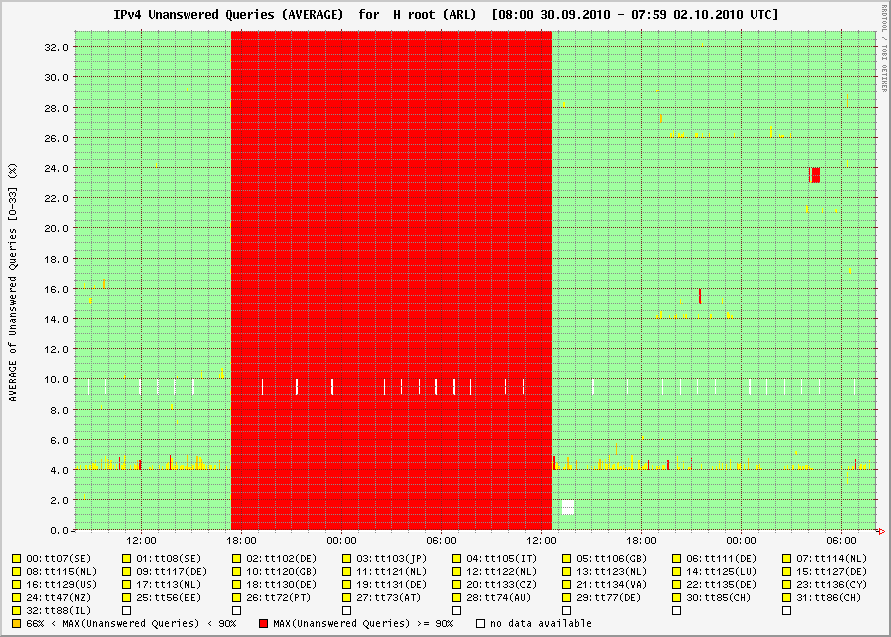
Well the bad news is the H root servers were not available for over 18 hours. The good news is that practically nobody noticed. As it turns out a fiber cut and poor weather took out access to this cluster of root DNS servers. https://lists.dns-oarc.net/pipermail/dns-operations/2010-October/006142.html shows the explanation for the outage. While the outage had no direct impact on Internet users, it does point out the necessity of proper design for redundancy. Graph of the H availability:
Cheers,
Adrien de Beaupré
Intru-shun.ca Inc.
Cyber Security Awareness Month - Day 3 - Recognizing phishing and online scams
On day 3 of Cyber Security Awareness Month 2010 the topic is Recognizing phishing and online scams. Which is an interesting discussion. For example, would phishers still bother if no one clicked and freely entered their credit card and personal information? Would 419 scammers bother if no one responded to their messages? Since there is a profit motive behind the miscreants actions if there were a diminishing return, or the actual possibility or prosecution, would we continue to see so many of their emails and web sites? Philosophical questions aside, in oder to reduce the harm of scammer and phishers the people receiving the bait need to be able to recognize the messages as such and not respond or click.
Don't click or respond to the following:
- If it sounds too good to be true, it is.
- If the message does not appear authentic, it probably isn't.
- Do the content of the message appear in search engine results?
- If you hover your mouse over the link does your browser or security software silently scream at you?
- Seeing silly typos, formatting, or grammatical errors a professional would not make.
- If the message asks you to send your information to them, rather than the other way around.
- If you don't have an account with the company supposedly sending the email!
Here are some useful links:
- http://www.microsoft.com/protect/fraud/phishing/symptoms.aspx
- http://www.us-cert.gov/reading_room/emailscams_0905.pdf
- http://www.gongol.com/howto/recognizephishing/
- http://www.surfnetkids.com/safety/how_to_recognize_phishing-21760.htm
This is just a start, please send in your suggestions on ways to avoid falling for scammers by recognizing the signs.
Update: Leigh sent in the following quiz to assist in detecting phishing/scams:
http://www.ballarat.edu.au/aasp/is/ict/security/security_challenge.shtml
Cheers,
Adrien de Beaupré
Intru-shun.ca Inc.
Canada's Cyber Security Strategy released today
Public Safety Canada released their version of a Cyber Security Strategy today. My first impression is that the document is a good start, albeit a bit late. It does demonstrate that the government is trying to show leadership in this area, which is a good thing. What the strategy document lacks is the pragmatic plan and specific steps required to implement it. The document will also serve as the report card for Canadians to evaluate the progress of the various departments that currently handle aspects of cyber security within the levels of government. Particularly Public Safety. In twelve months from now all of the items in their strategy should be reality. Each of the three primary areas the strategy covers are equally important in the long term, and require a significant investment in time, funding, cooperation, partnerships, and leadership. Government systems, applications, and networks must be secured. New better partnerships must be created with all stakeholders in the private and public sectors. The public have the right to expect both guidance and assistance in securing their home computers and identities.
I believe that this truly underscores the need for a national CIRT/CERT in Canada, an organization that can help Canada meet these requirements and follow the steps as laid out in the strategy, as unfortunately it does not currently exist.
It is a step in the right direction, however many more are required.
The strategy is outlined here:
http://www.publicsafety.gc.ca/prg/em/cbr/ccss-scc-eng.aspx
Tell us what you think, or comment below!
Cheers,
Adrien de Beaupré, Handler, SANS Internet Storm Center
Senior IT Security Consultant
Intru-shun.ca Inc.


Comments